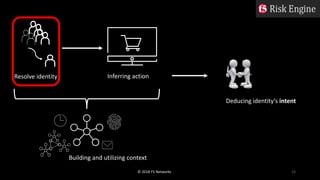
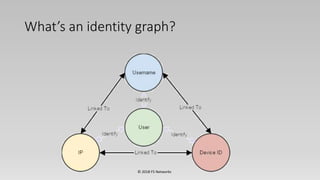
The document discusses identity resolution in cyber defense, focusing on the challenges of identifying and authenticating users across multiple devices while addressing issues like identity theft and false positives. It outlines a proposed solution utilizing machine learning and behavioral analysis to infer user intent and create a more secure environment. The presentation covers technical aspects such as risk engines, identity graphs, and the combination of various data sources to enhance identity verification processes.