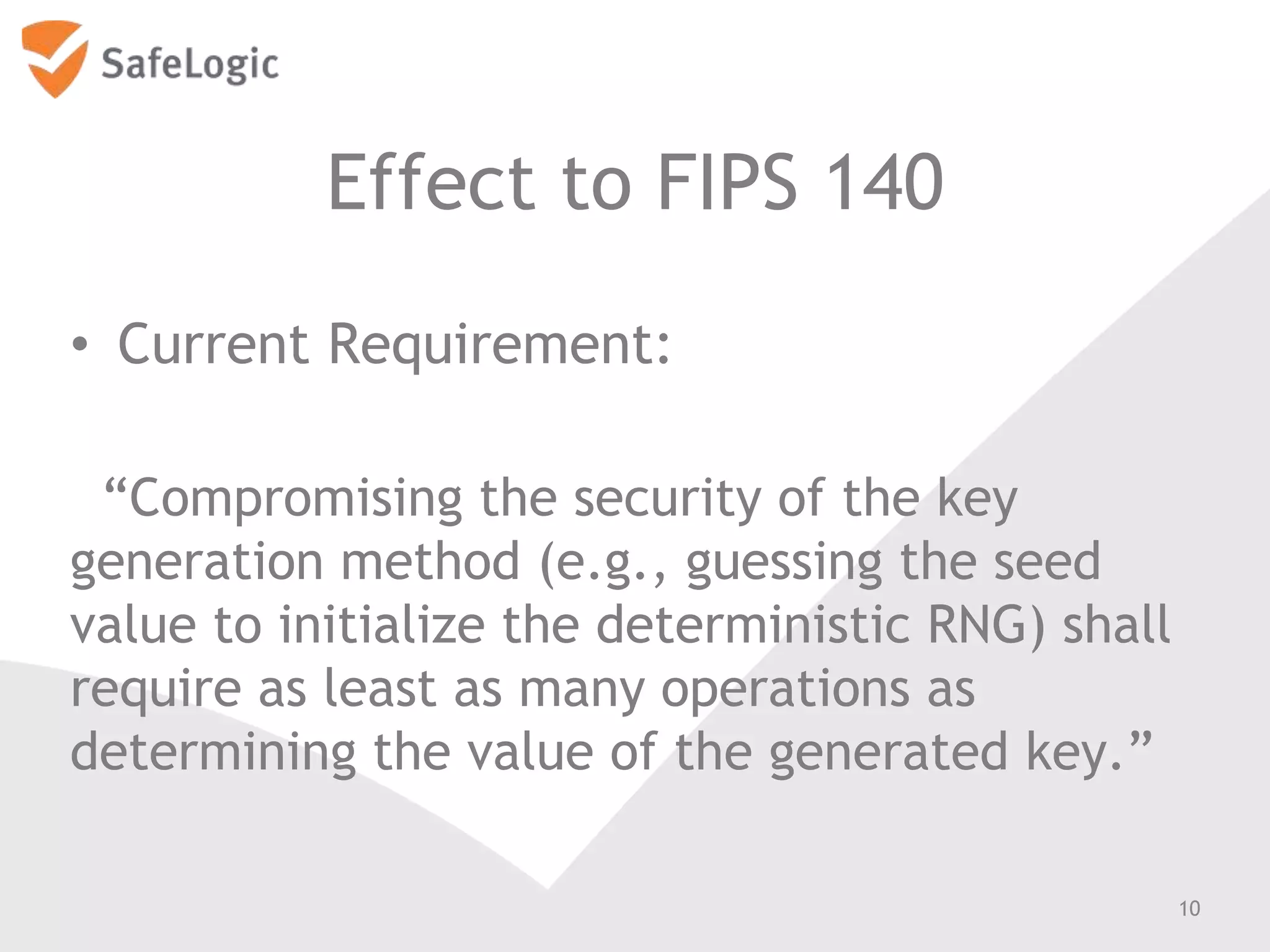
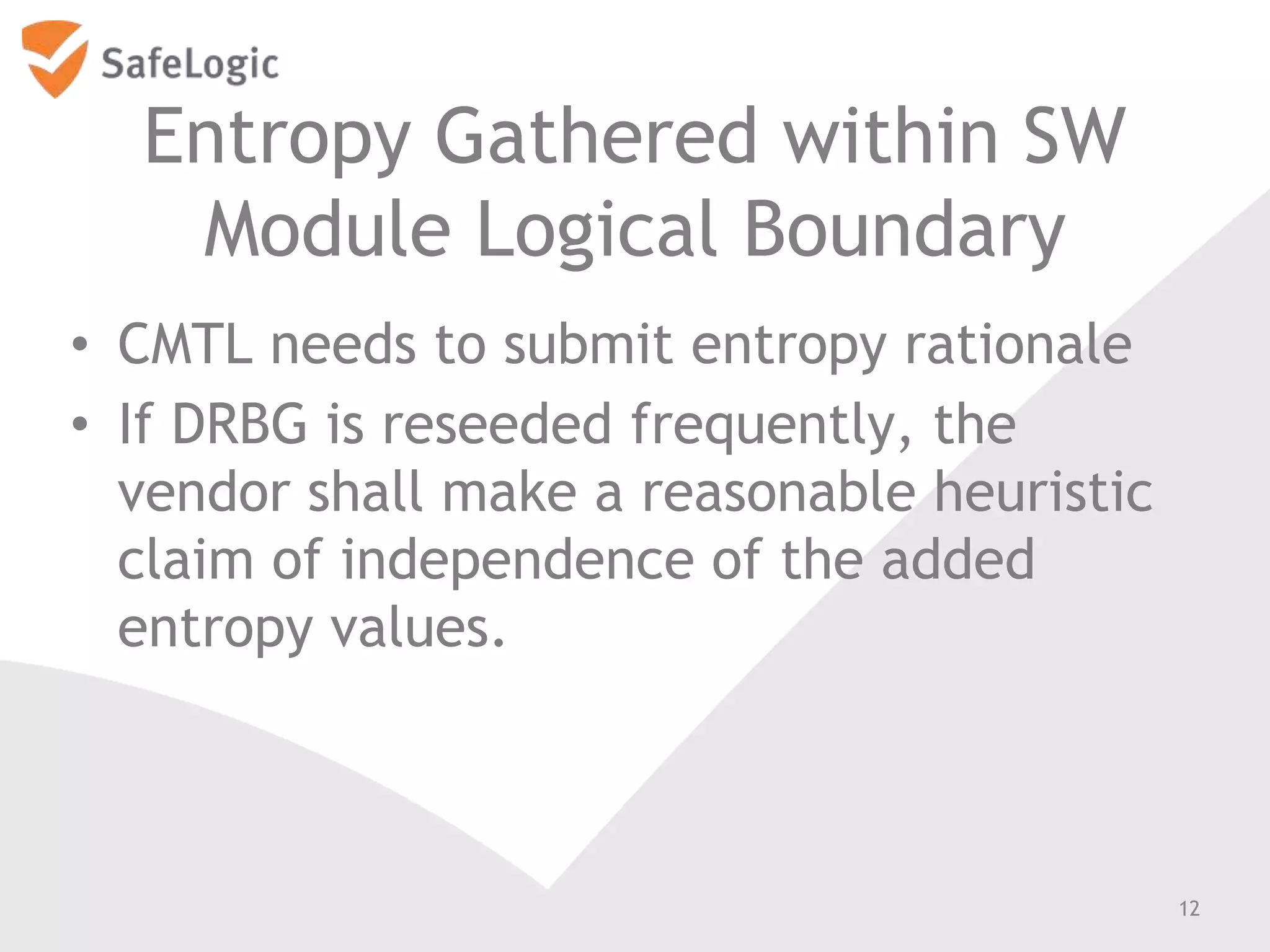
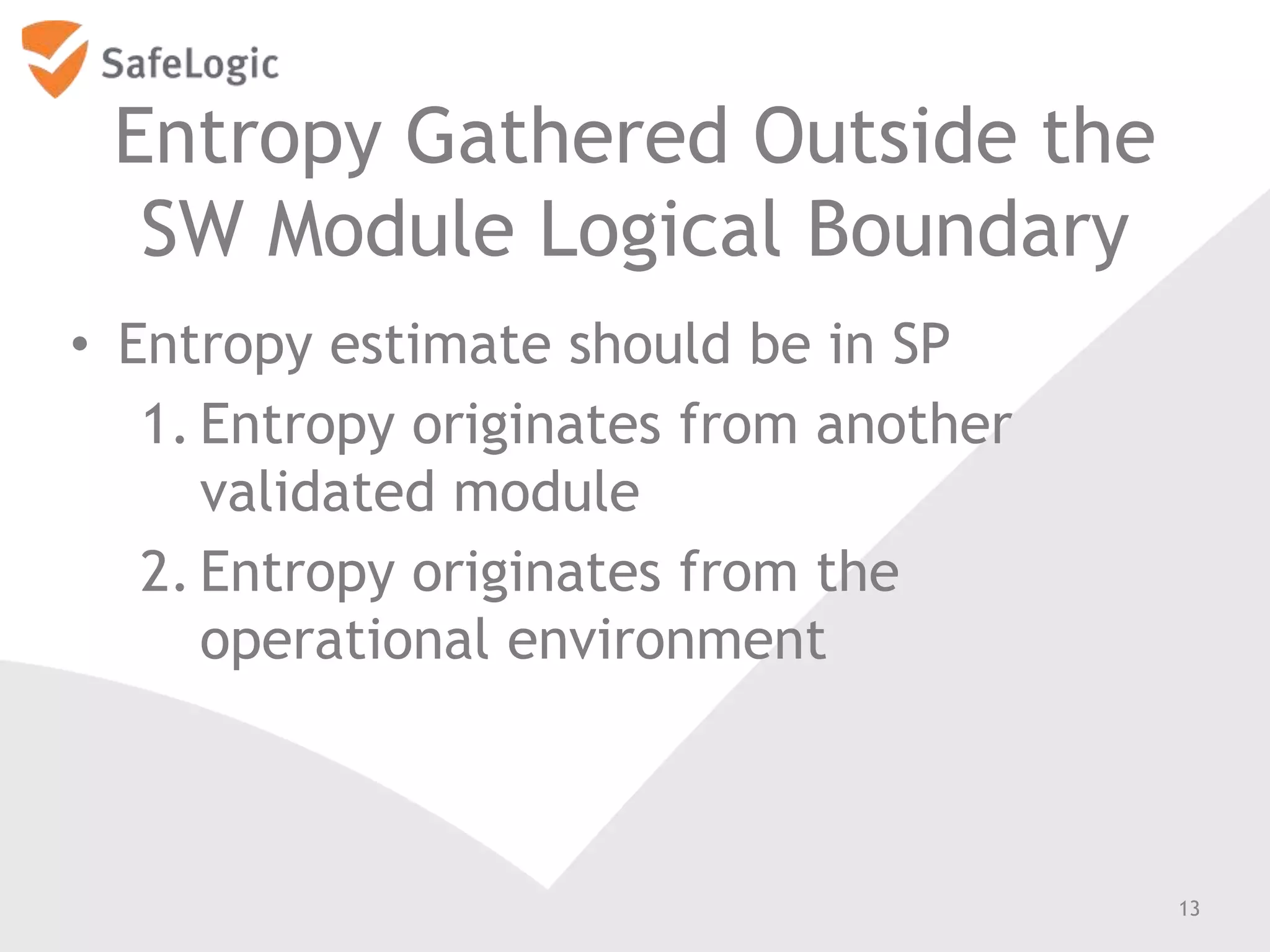
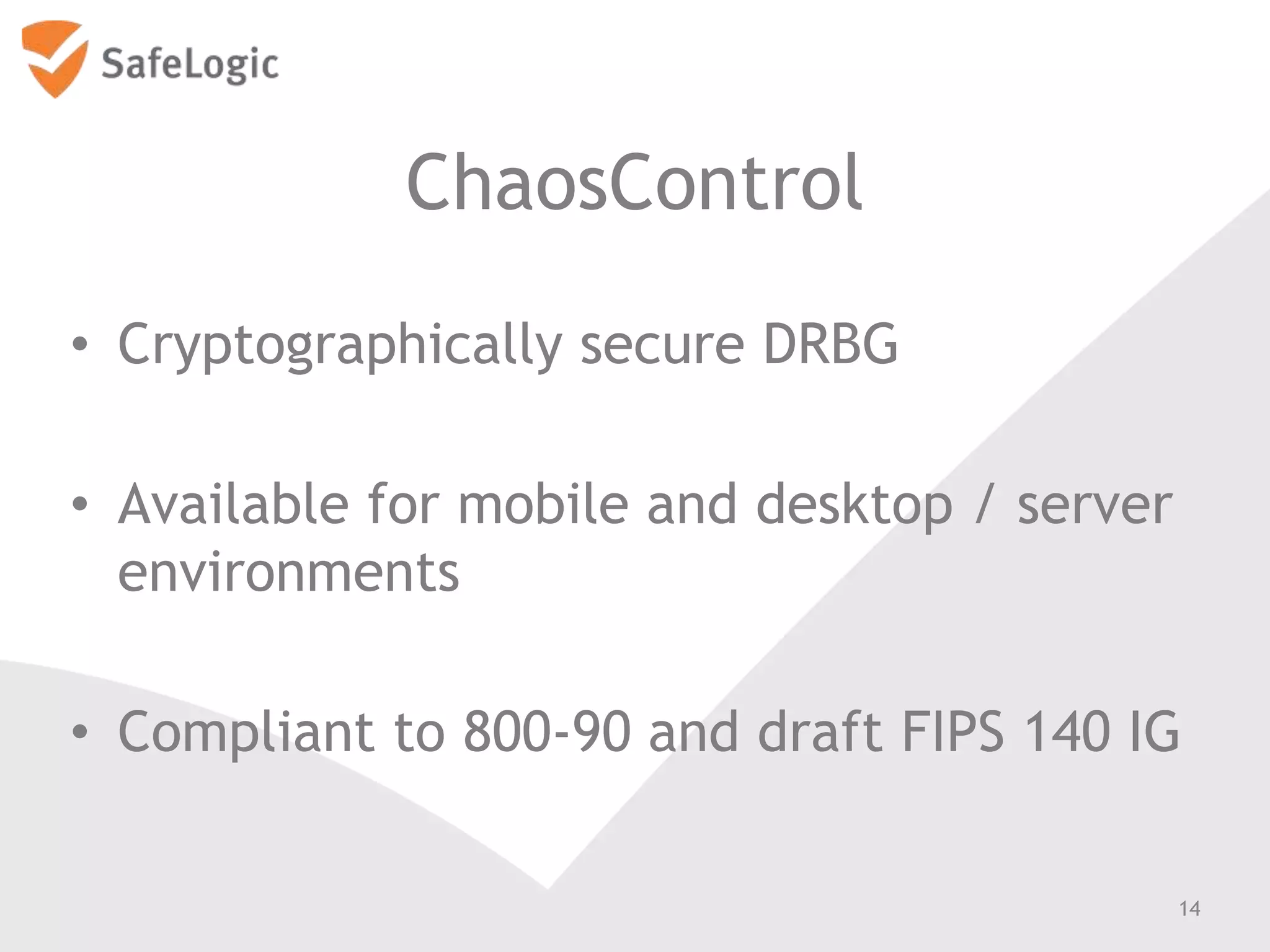
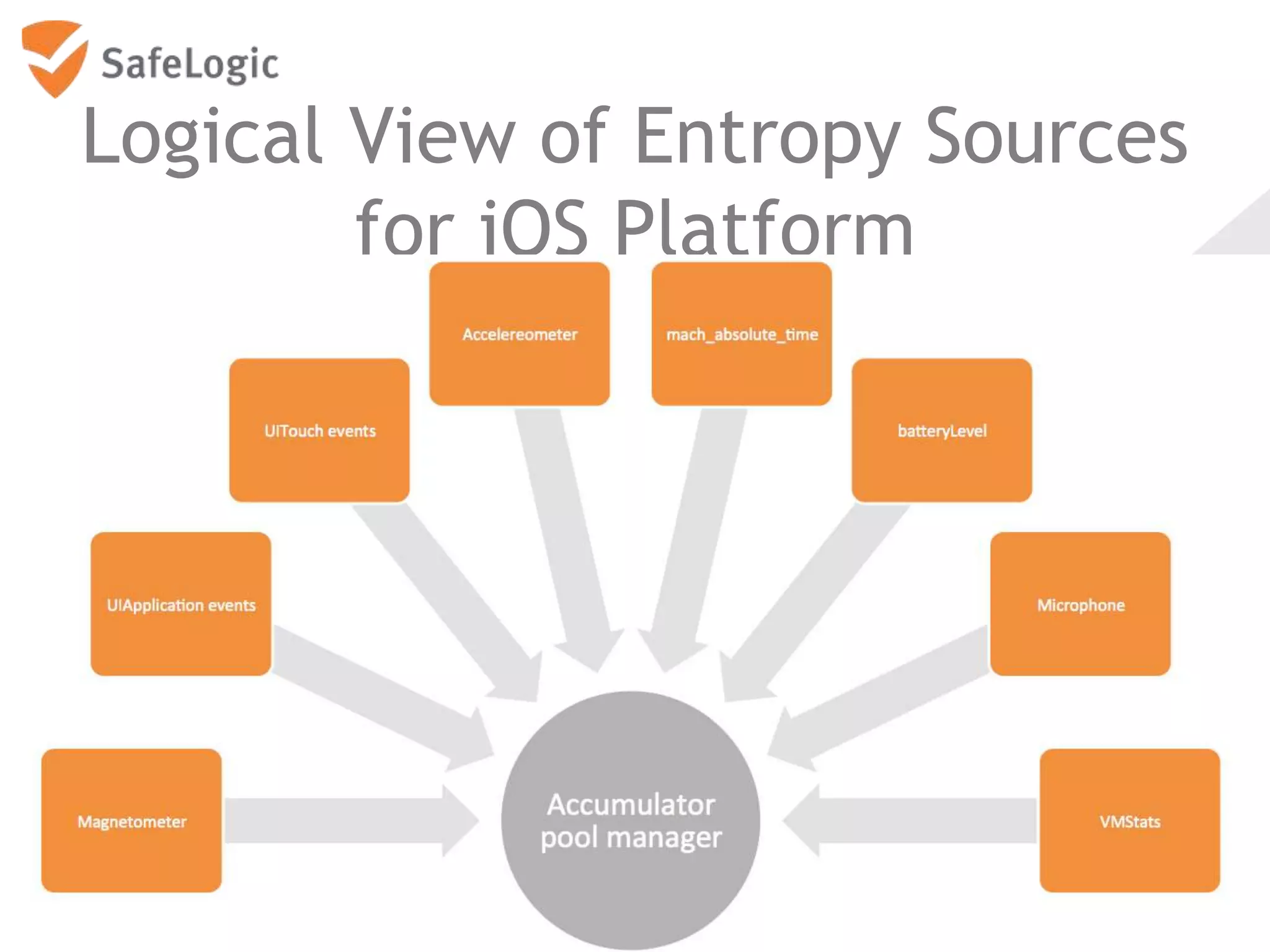
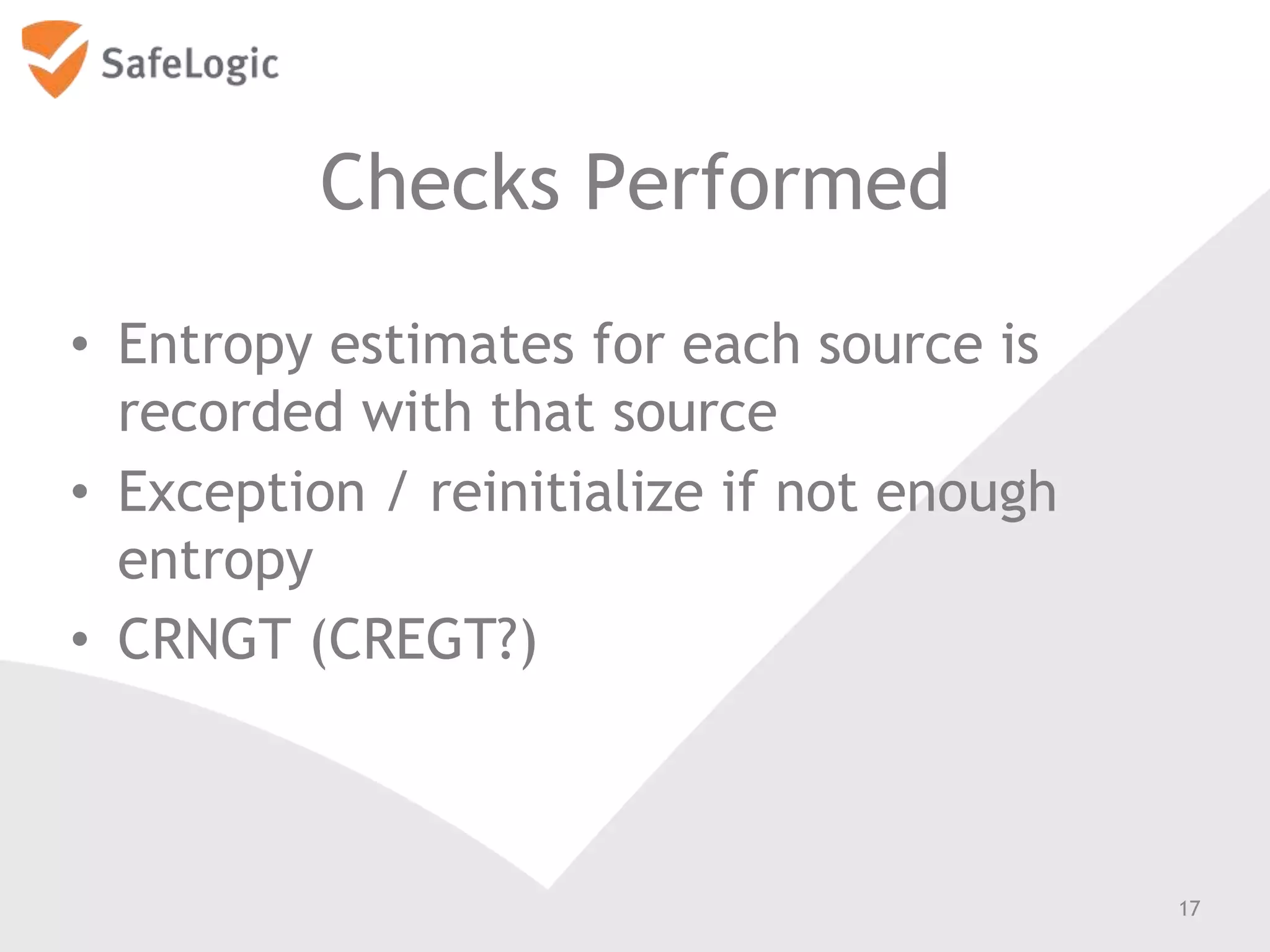
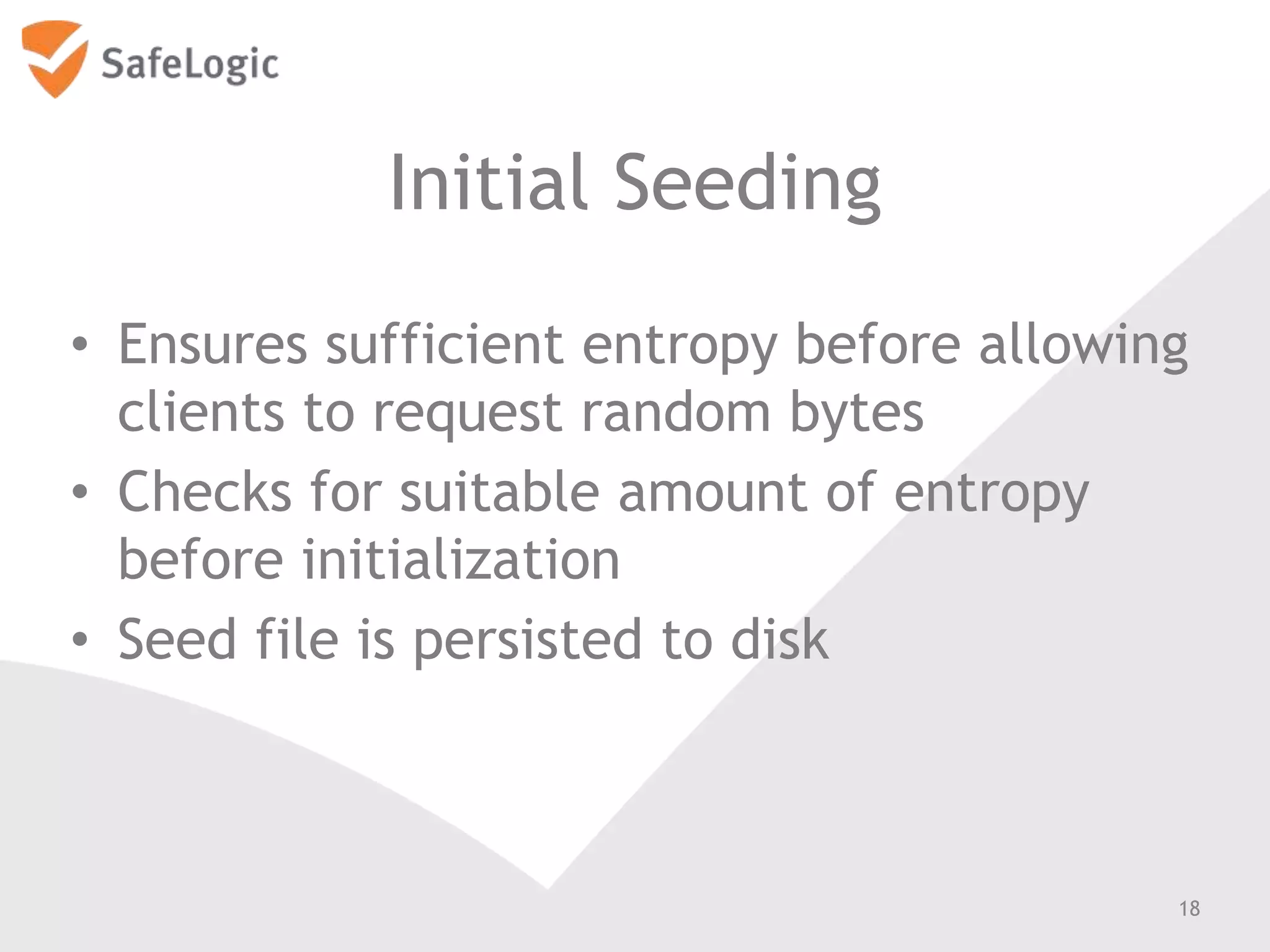
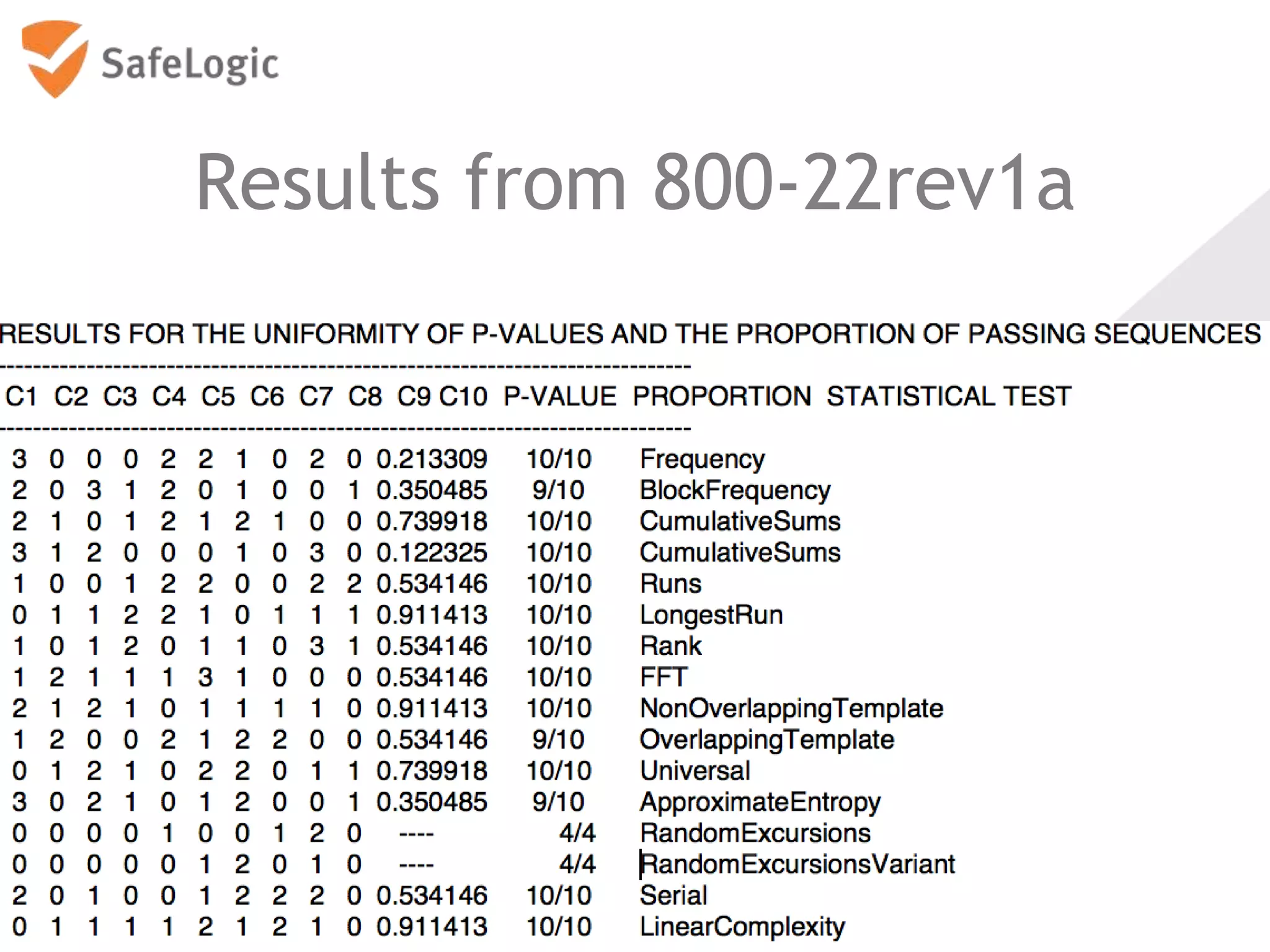
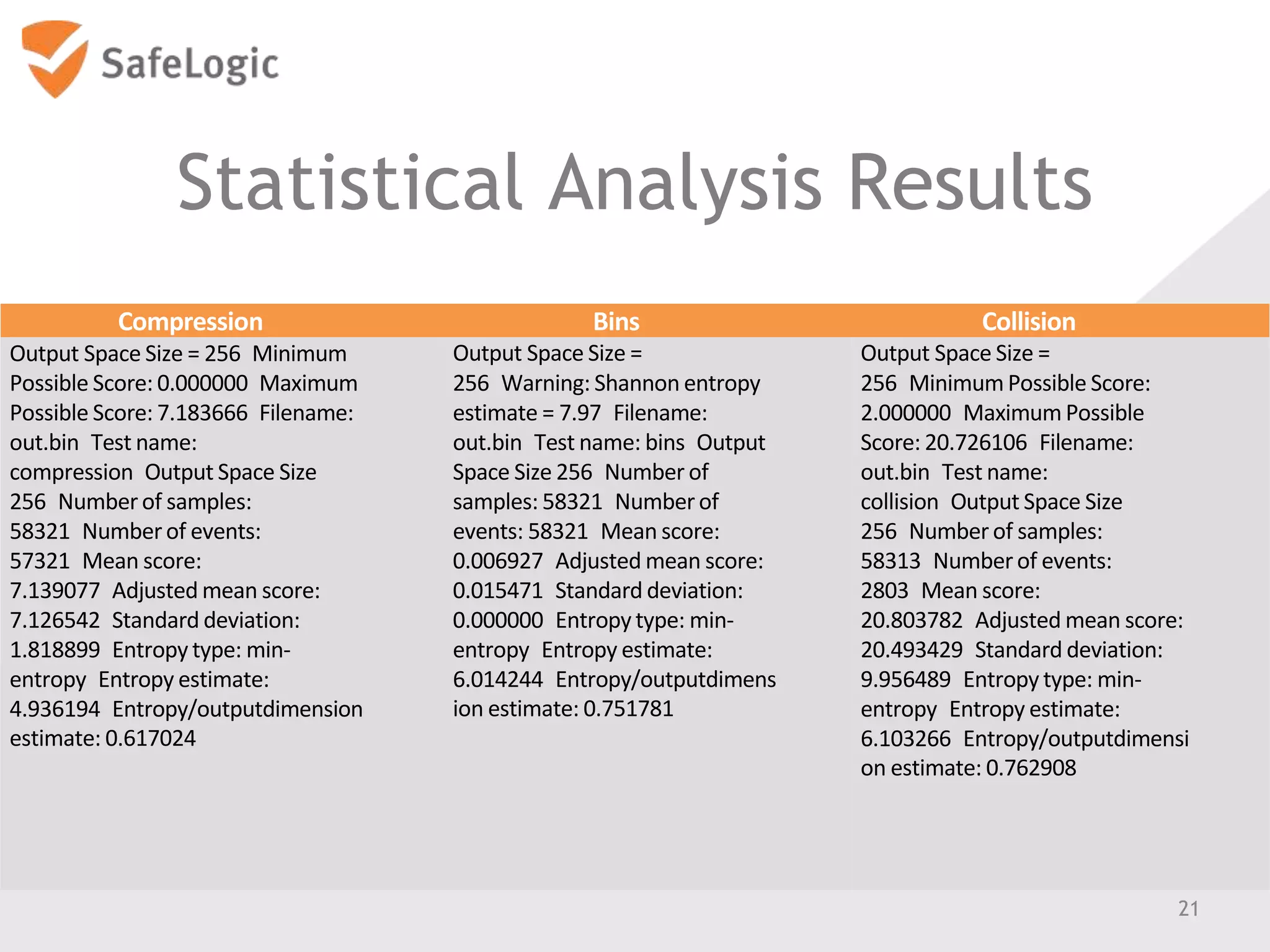
The document discusses entropy in the context of cryptography, highlighting its significance in generating random bits and ensuring secure authentication protocols. It reviews various NIST standards and requirements for entropy sources and the challenges of generating truly random data on computers. Additionally, the document introduces a product called ChaosControl, which aims to provide a compliant solution for random bit generation.