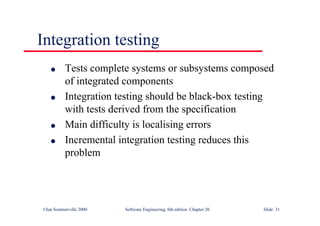
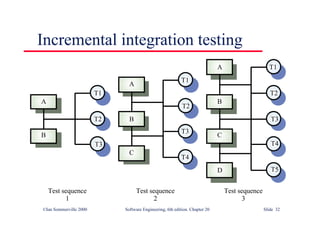
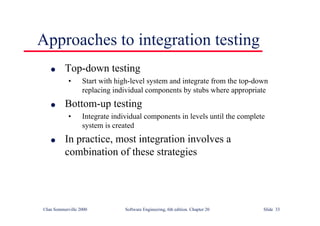
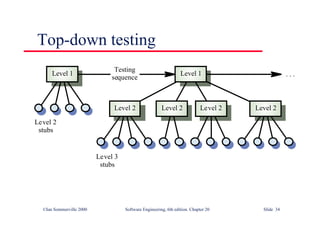
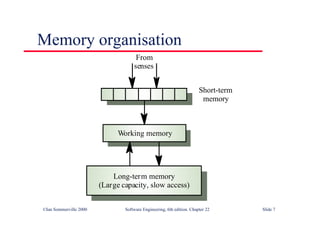
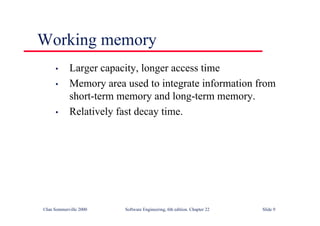
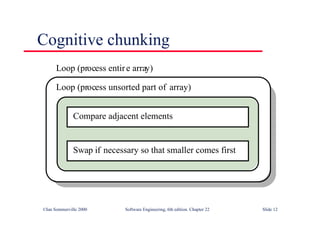
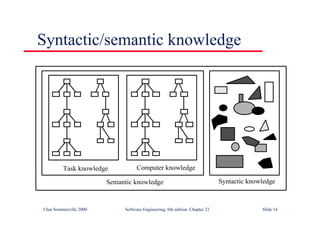
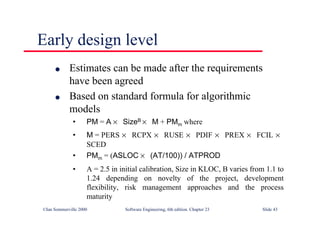
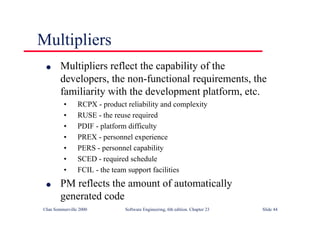
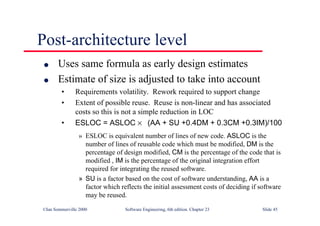
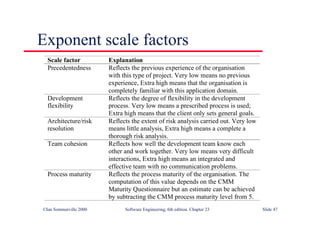
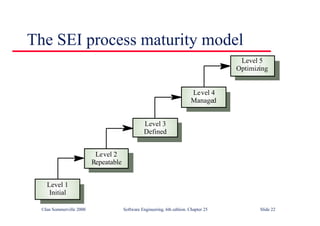
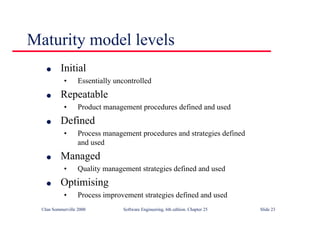
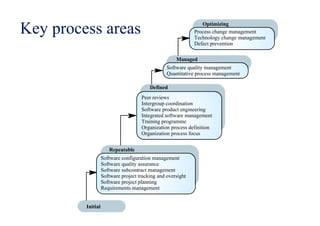
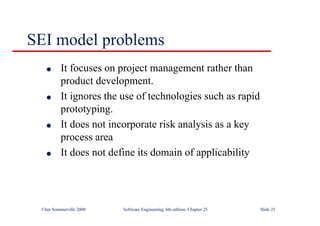
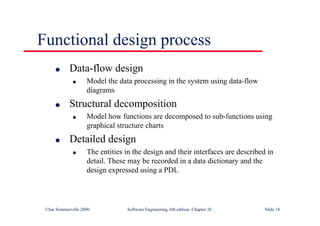
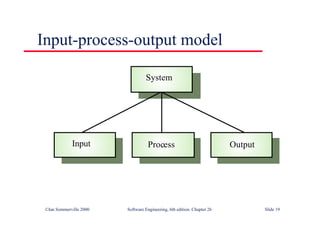
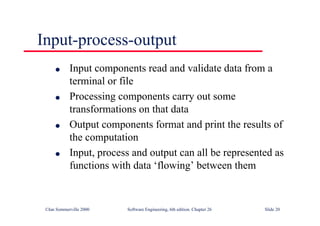
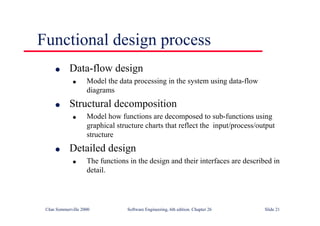
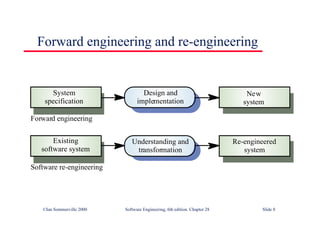
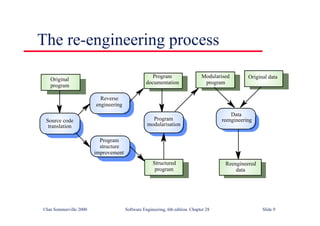
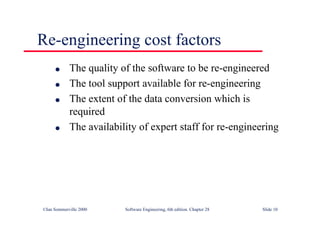
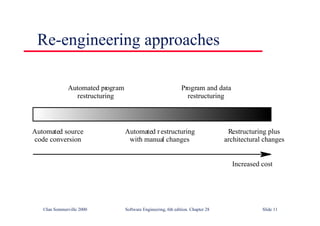
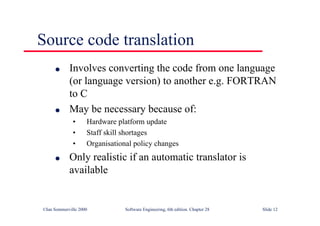
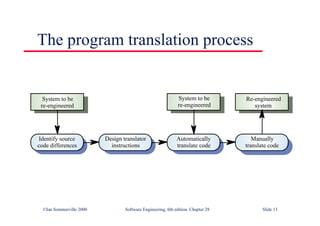
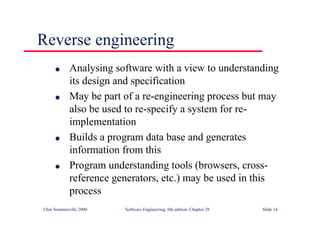
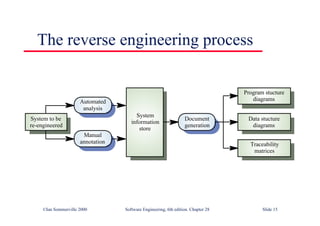
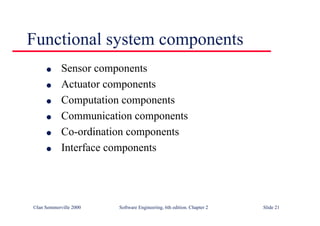
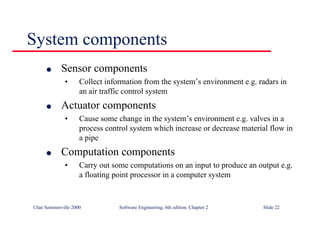
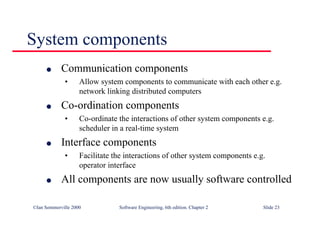
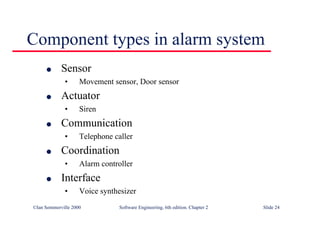
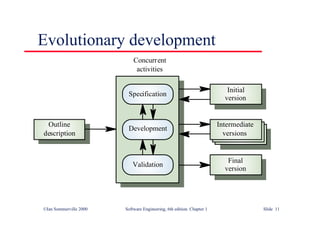
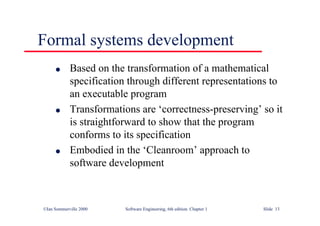
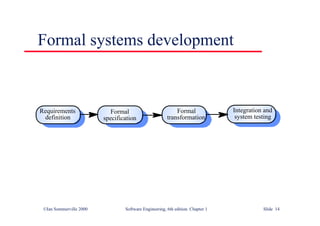
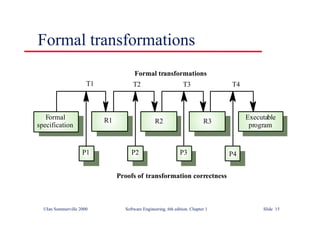
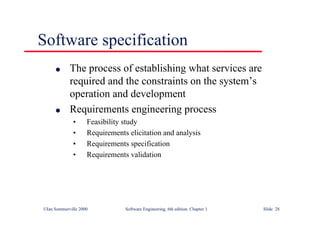
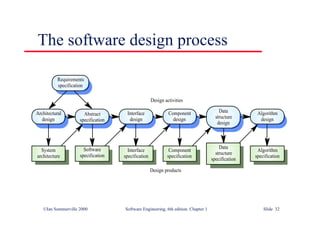
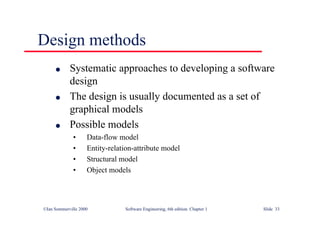
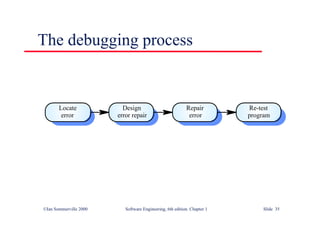
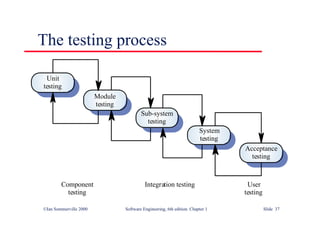
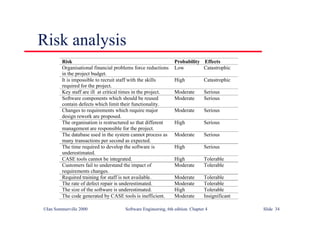
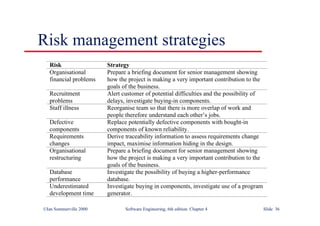
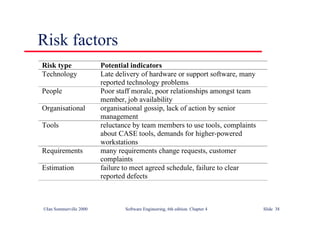
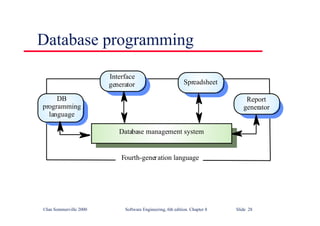
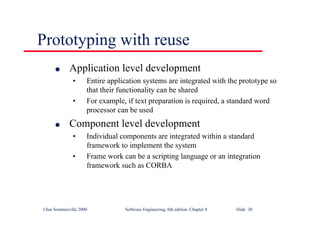
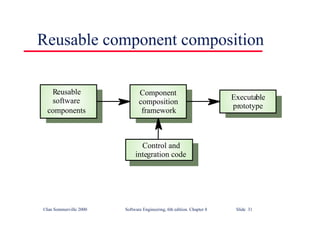
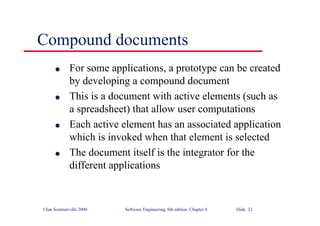
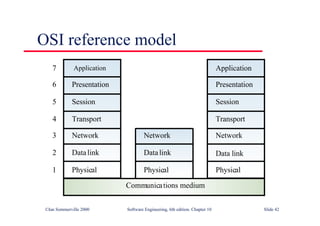
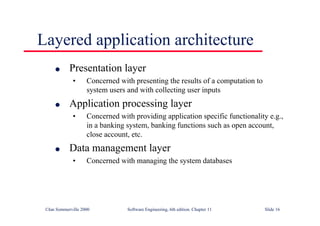
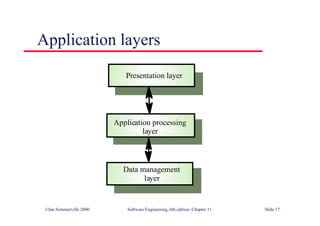
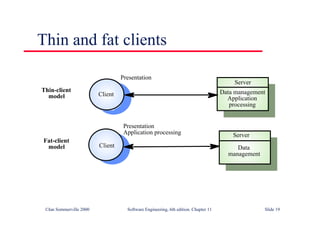
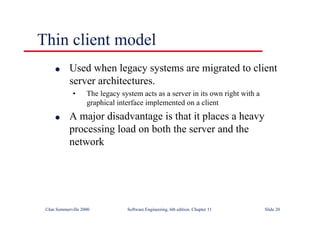
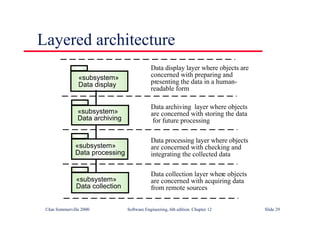
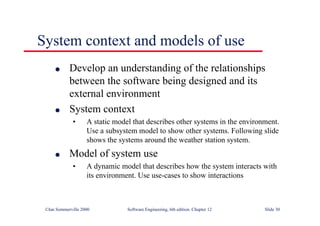
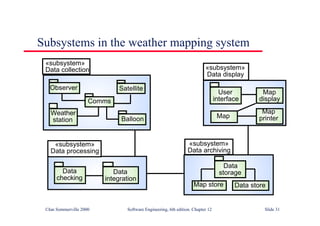
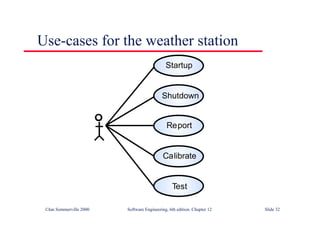
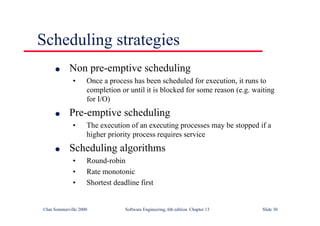
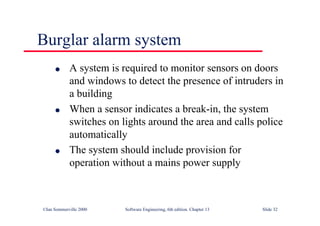
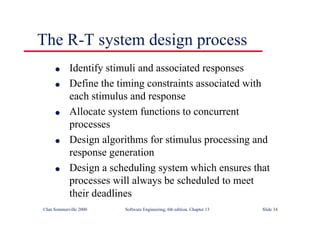
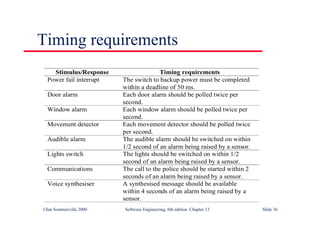
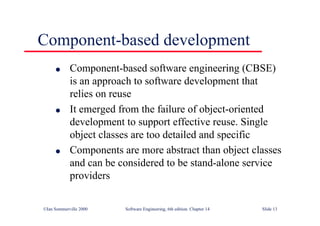
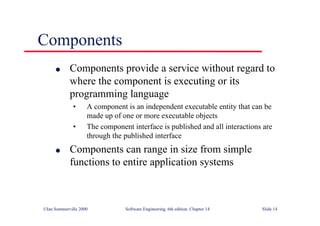
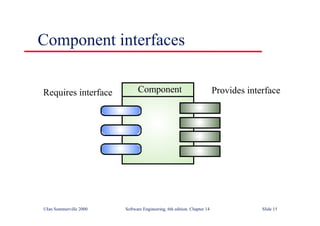
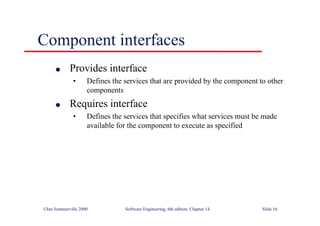
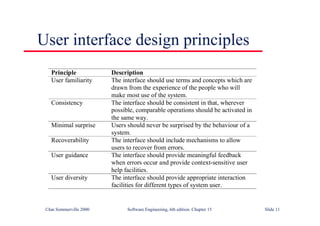
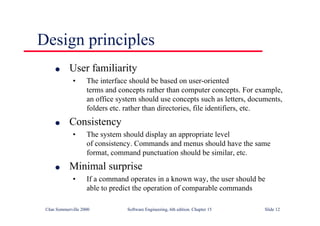
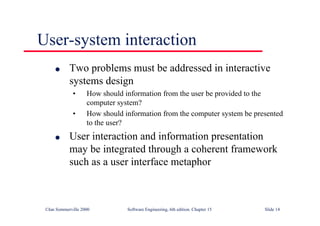
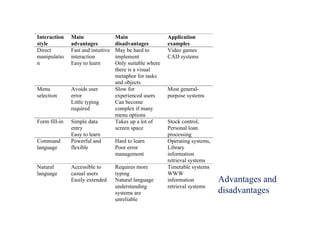
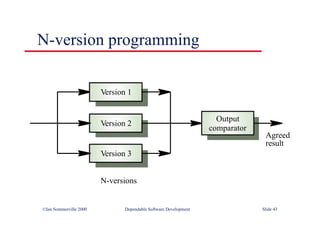
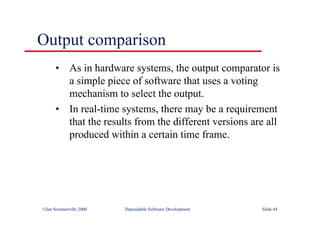
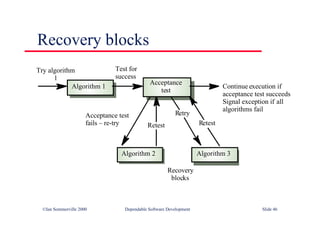
This document summarizes key points from Chapter 1 of Ian Sommerville's Software Engineering textbook. It introduces software engineering and explains that it is an engineering discipline concerned with all aspects of software production. It discusses professional responsibilities of software engineers and covers topics like what software is, differences between software engineering and computer science, software processes, costs of software engineering, and challenges facing the field. The document emphasizes that software engineers must consider ethical issues and stresses important concepts like reliability, maintainability, and usability of software.















































































































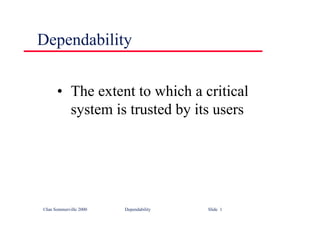
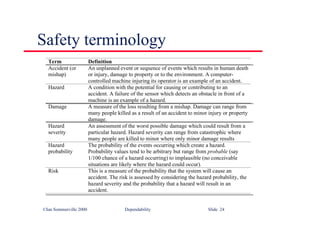
![©Ian Sommerville 2000 Software Engineering, 6th edition. Chapter 5 Slide 43
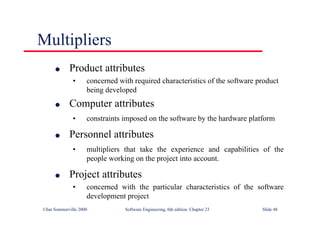
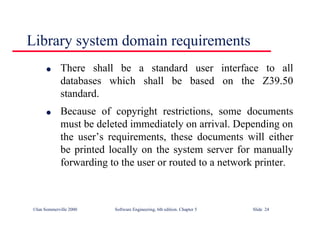
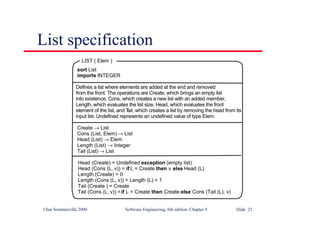
Part of an ATM specification
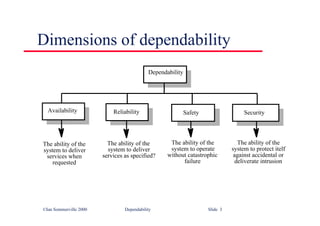
class ATM {
// declarations here
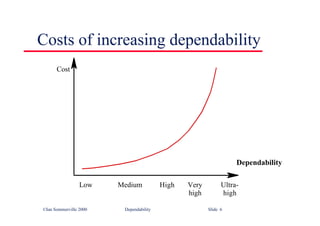
public static void main (String args[]) throws InvalidCard {
try {
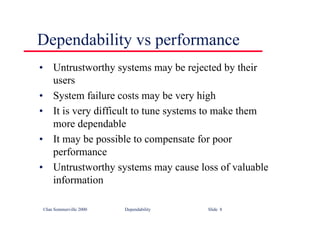
thisCard.read () ; // may throw InvalidCard exception
pin = KeyPad.readPin () ; attempts = 1 ;
while ( !thisCard.pin.equals (pin) & attempts < 4 )
{ pin = KeyPad.readPin () ; attempts = attempts + 1 ;
}
if (!thisCard.pin.equals (pin))
throw new InvalidCard ("Bad PIN");
thisBalance = thisCard.getBalance () ;
do { Screen.prompt (" Please select a service ") ;
service = Screen.touchKey () ;
switch (service) {
case Services.withdrawalWithReceipt:
receiptRequired = true ;](https://image.slidesharecdn.com/iansommervillesoftwareengineering6th-221129045124-a54bccb0/85/Ian_Sommerville_Software_Engineering_6th-pdf-210-320.jpg)





























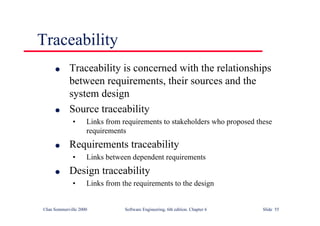
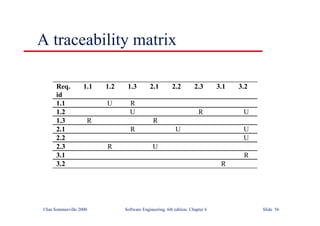






























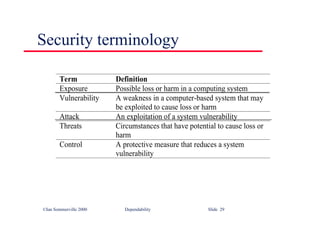
![©Ian Sommerville 2000 Software Engineering, 6th edition. Chapter 9 Slide 22
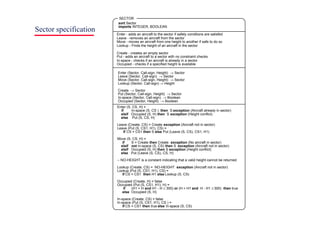
Recursion in specifications
l Operations are often specified recursively
l Tail (Cons (L, v)) = if L = Create then Create
else Cons (Tail (L), v)
• Cons ([5, 7], 9) = [5, 7, 9]
• Tail ([5, 7, 9]) = Tail (Cons ( [5, 7], 9)) =
• Cons (Tail ([5, 7]), 9) = Cons (Tail (Cons ([5], 7)), 9) =
• Cons (Cons (Tail ([5]), 7), 9) =
• Cons (Cons (Tail (Cons ([], 5)), 7), 9) =
• Cons (Cons ([Create], 7), 9) = Cons ([7], 9) = [7, 9]](https://image.slidesharecdn.com/iansommervillesoftwareengineering6th-221129045124-a54bccb0/85/Ian_Sommerville_Software_Engineering_6th-pdf-385-320.jpg)






















































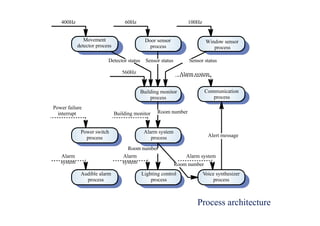



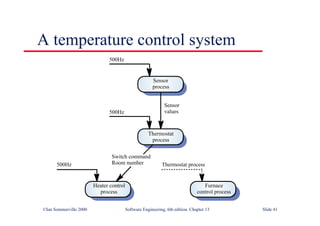
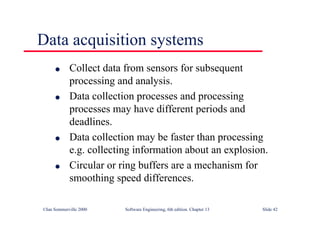
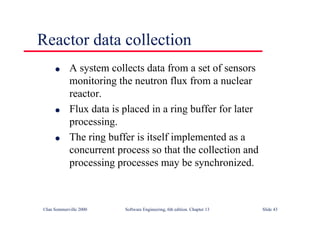
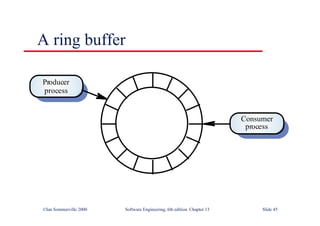

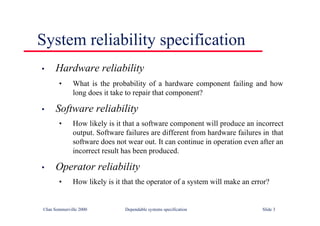
![Java implementation of a ring buffer 1
class CircularBuffer
{
int bufsize ;
SensorRecord [] store ;
int numberOfEntries = 0 ;
int front = 0, back = 0 ;
CircularBuffer (int n) {
bufsize = n ;
store = new SensorRecord [bufsize] ;
} // CircularBuffer
synchronized void put (SensorRecord rec ) throws InterruptedException
{
if ( numberOfEntries == bufsize)
wait () ;
store [back] = new SensorRecord (rec.sensorId, rec.sensorVal) ;
back = back + 1 ;
if (back == bufsize)
back = 0 ;
numberOfEntries = numberOfEntries + 1 ;
notify () ;
} // put](https://image.slidesharecdn.com/iansommervillesoftwareengineering6th-221129045124-a54bccb0/85/Ian_Sommerville_Software_Engineering_6th-pdf-593-320.jpg)
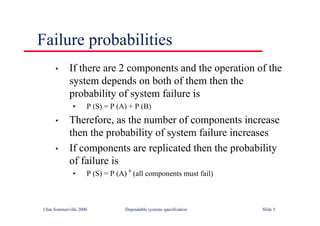
![Java implementation of a ring buffer 2
synchronized SensorRecord get () throws InterruptedException
{
SensorRecord result = new SensorRecord (-1, -1) ;
if (numberOfEntries == 0)
wait () ;
result = store [front] ;
front = front + 1 ;
if (front == bufsize)
front = 0 ;
numberOfEntries = numberOfEntries - 1 ;
notify () ;
return result ;
} // get
} // CircularBuffer](https://image.slidesharecdn.com/iansommervillesoftwareengineering6th-221129045124-a54bccb0/85/Ian_Sommerville_Software_Engineering_6th-pdf-594-320.jpg)












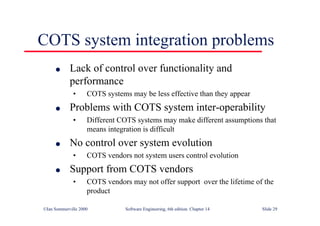



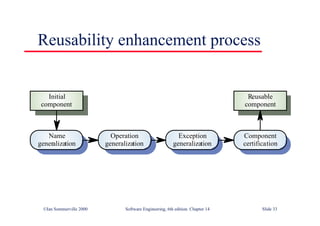

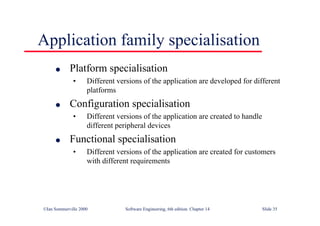
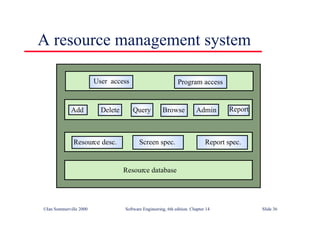




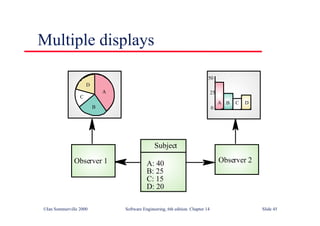

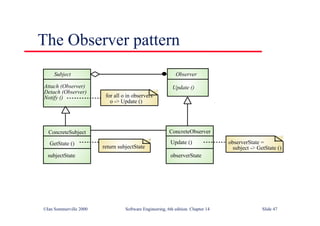










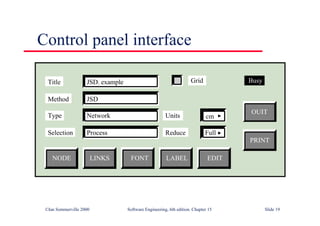


































































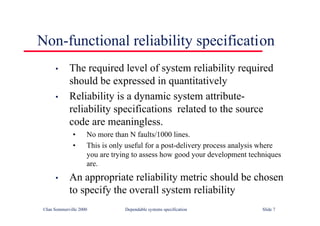

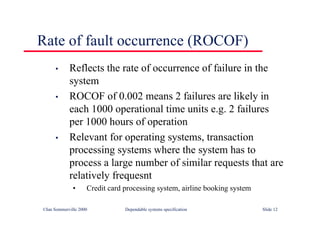
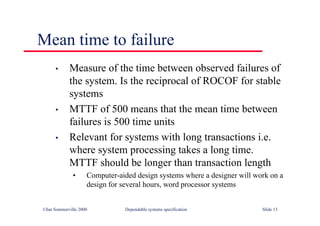


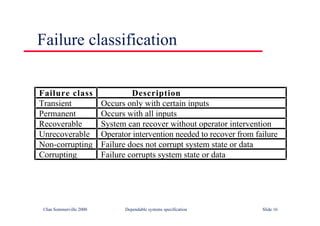

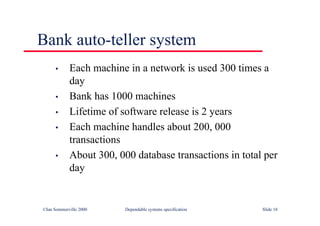



































![Java class with damage
assessment
class RobustArray {
// Checks that all the objects in an array of objects
// conform to some defined constraint
boolean [] checkState ;
CheckableObject [] theRobustArray ;
RobustArray (CheckableObject [] theArray)
{
checkState = new boolean [theArray.length] ;
theRobustArray = theArray ;
} //RobustArray
public void assessDamage () throws ArrayDamagedException
{
boolean hasBeenDamaged = false ;
for (int i= 0; i <this.theRobustArray.length ; i ++)
{
if (! theRobustArray [i].check ())
{
checkState [i] = true ;
hasBeenDamaged = true ;
}
else
checkState [i] = false ;
}
if (hasBeenDamaged)
throw new ArrayDamagedException () ;
} //assessDamage
} // RobustArray
©Ian Sommerville 2000 Dependable Software Development Slide 29](https://image.slidesharecdn.com/iansommervillesoftwareengineering6th-221129045124-a54bccb0/85/Ian_Sommerville_Software_Engineering_6th-pdf-840-320.jpg)




![Safe sort procedure (Java)
class SafeSort {
static void sort ( int [] intarray, int order ) throws SortError
{
int [] copy = new int [intarray.length];
// copy the input array
for (int i = 0; i < intarray.length ; i++)
copy [i] = intarray [i] ;
try {
Sort.bubblesort (intarray, intarray.length, order) ;
if (order == Sort.ascending)
for (int i = 0; i <= intarray.length-2 ; i++)
if (intarray [i] > intarray [i+1])
throw new SortError () ;
else
for (int i = 0; i <= intarray.length-2 ; i++)
if (intarray [i+1] > intarray [i])
throw new SortError () ;
} // try block
catch (SortError e )
{
for (int i = 0; i < intarray.length ; i++)
intarray [i] = copy [i] ;
throw new SortError ("Array not sorted") ;
} //catch
} // sort
} // SafeSort
©Ian Sommerville 2000 Dependable Software Development Slide 34](https://image.slidesharecdn.com/iansommervillesoftwareengineering6th-221129045124-a54bccb0/85/Ian_Sommerville_Software_Engineering_6th-pdf-845-320.jpg)


























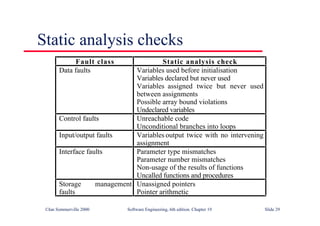
![LINT static analysis
138% more lint_ex.c
#include <stdio.h>
printarray (Anarray)
int Anarray;
{
printf(“%d”,Anarray);
}
main ()
{
int Anarray[5]; int i; char c;
printarray (Anarray, i, c);
printarray (Anarray) ;
}
139% cc lint_ex.c
140% lint lint_ex.c
lint_ex.c(10): warning: c may be used before set
lint_ex.c(10): warning: i may be used before set
printarray: variable # of args. lint_ex.c(4) :: lint_ex.c(10)
printarray, arg. 1 used inconsistently lint_ex.c(4) ::
lint_ex.c(10)
printarray, arg. 1 used inconsistently lint_ex.c(4) ::
lint_ex.c(11)
printf returns value which is always ignored](https://image.slidesharecdn.com/iansommervillesoftwareengineering6th-221129045124-a54bccb0/85/Ian_Sommerville_Software_Engineering_6th-pdf-895-320.jpg)


















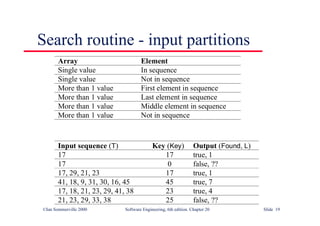

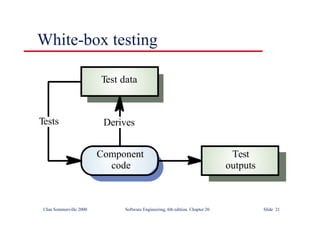
![Binary search (Java)
class BinSearch {
// This is an encapsulation of a binary search function that takes an array of
// ordered objects and a key and returns an object with 2 attributes namely
// index - the value of the array index
// found - a boolean indicating whether or not the key is in the array
// An object is returned because it is not possible in Java to pass basic types by
// reference to a function and so return two values
// the key is -1 if the element is not found
public static void search ( int key, int [] elemArray, Result r )
{
int bottom = 0 ;
int top = elemArray.length - 1 ;
int mid ;
r.found = false ; r.index = -1 ;
while ( bottom <= top )
{
mid = (top + bottom) / 2 ;
if (elemArray [mid] == key)
{
r.index = mid ;
r.found = true ;
return ;
} // if part
else
{
if (elemArray [mid] < key)
bottom = mid + 1 ;
else
top = mid - 1 ;
}
} //while loop
} // search
} //BinSearch](https://image.slidesharecdn.com/iansommervillesoftwareengineering6th-221129045124-a54bccb0/85/Ian_Sommerville_Software_Engineering_6th-pdf-927-320.jpg)

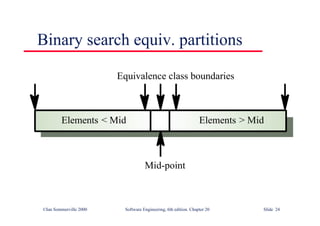
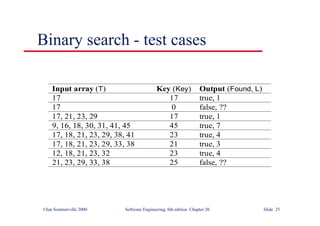
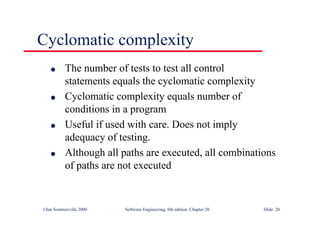
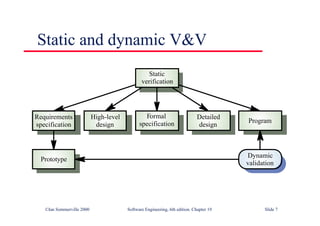
![Binary search flow graph
1
2
3
4
6
5
7
while bottom <= top
if (elemArray [mid] == key
(if (elemArray [mid]< key
8
9
bottom > top](https://image.slidesharecdn.com/iansommervillesoftwareengineering6th-221129045124-a54bccb0/85/Ian_Sommerville_Software_Engineering_6th-pdf-934-320.jpg)