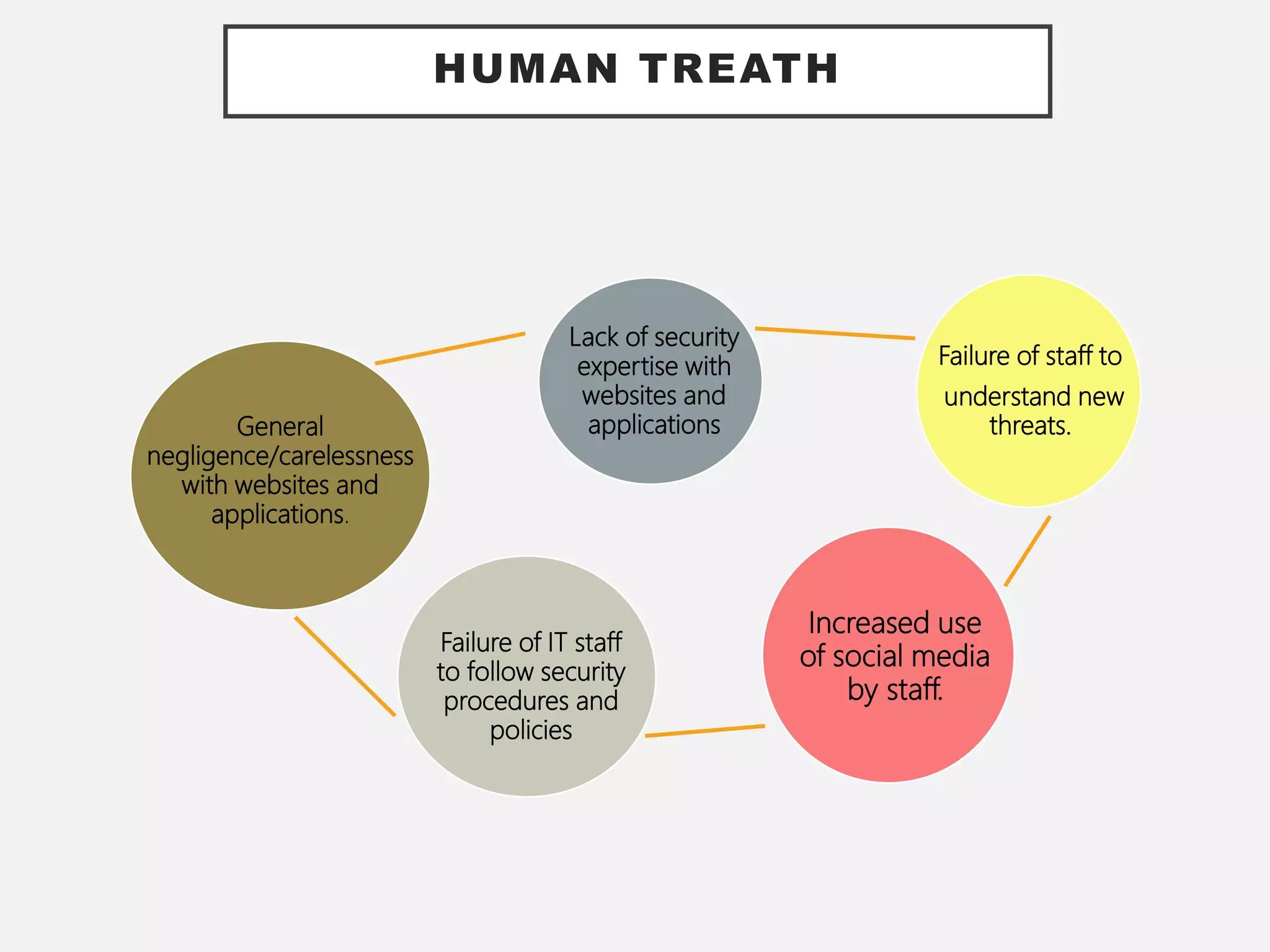
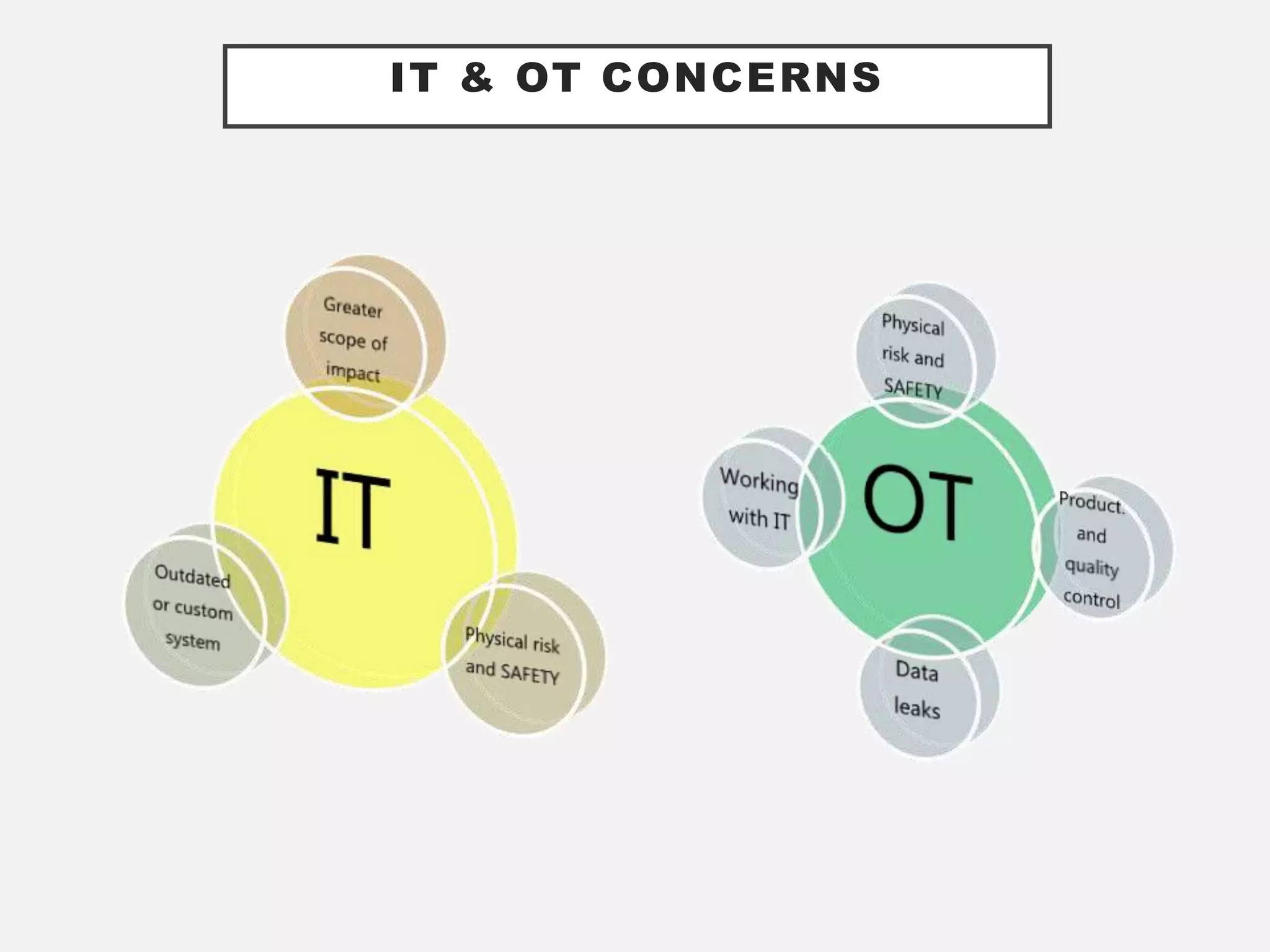
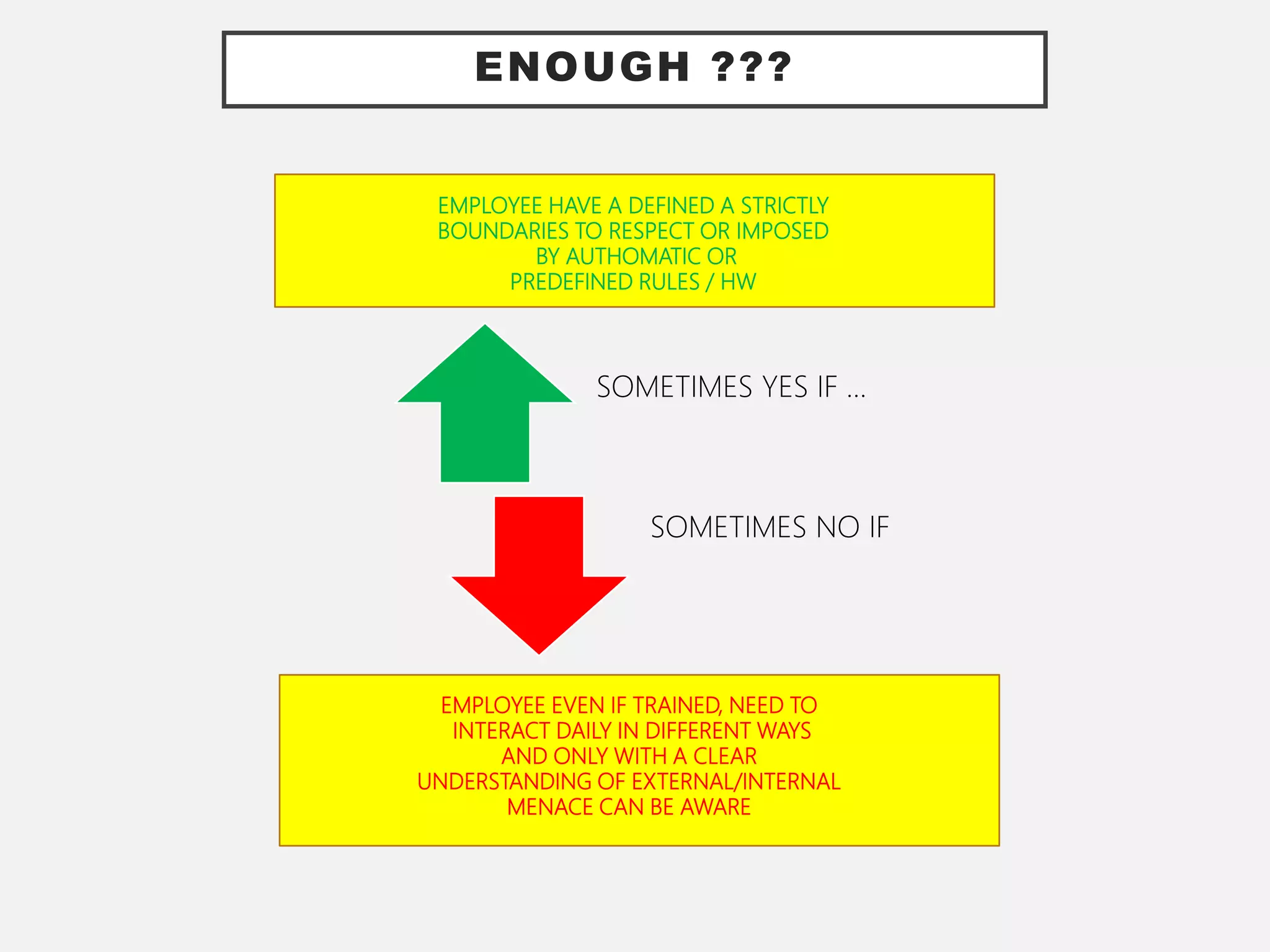
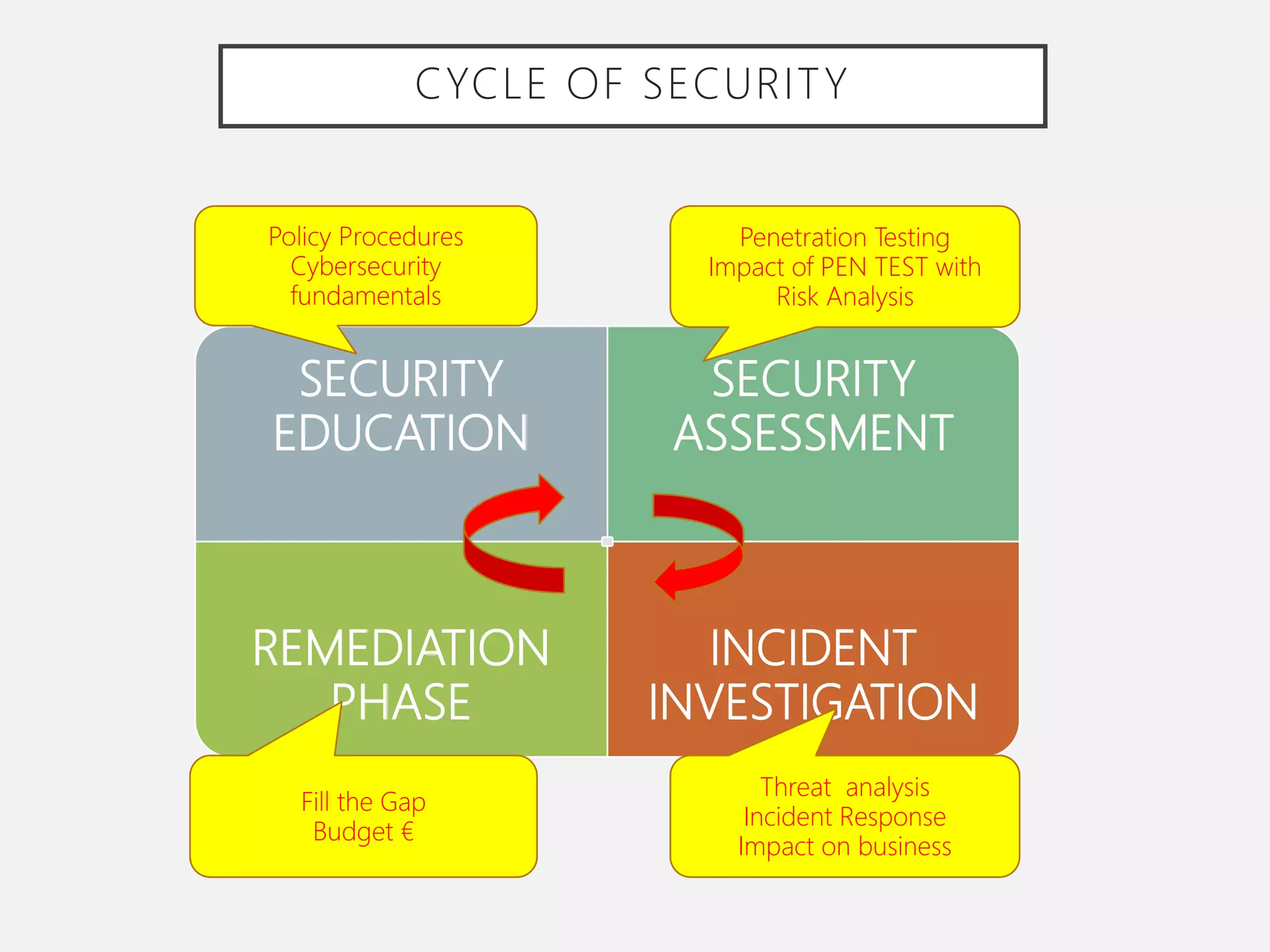
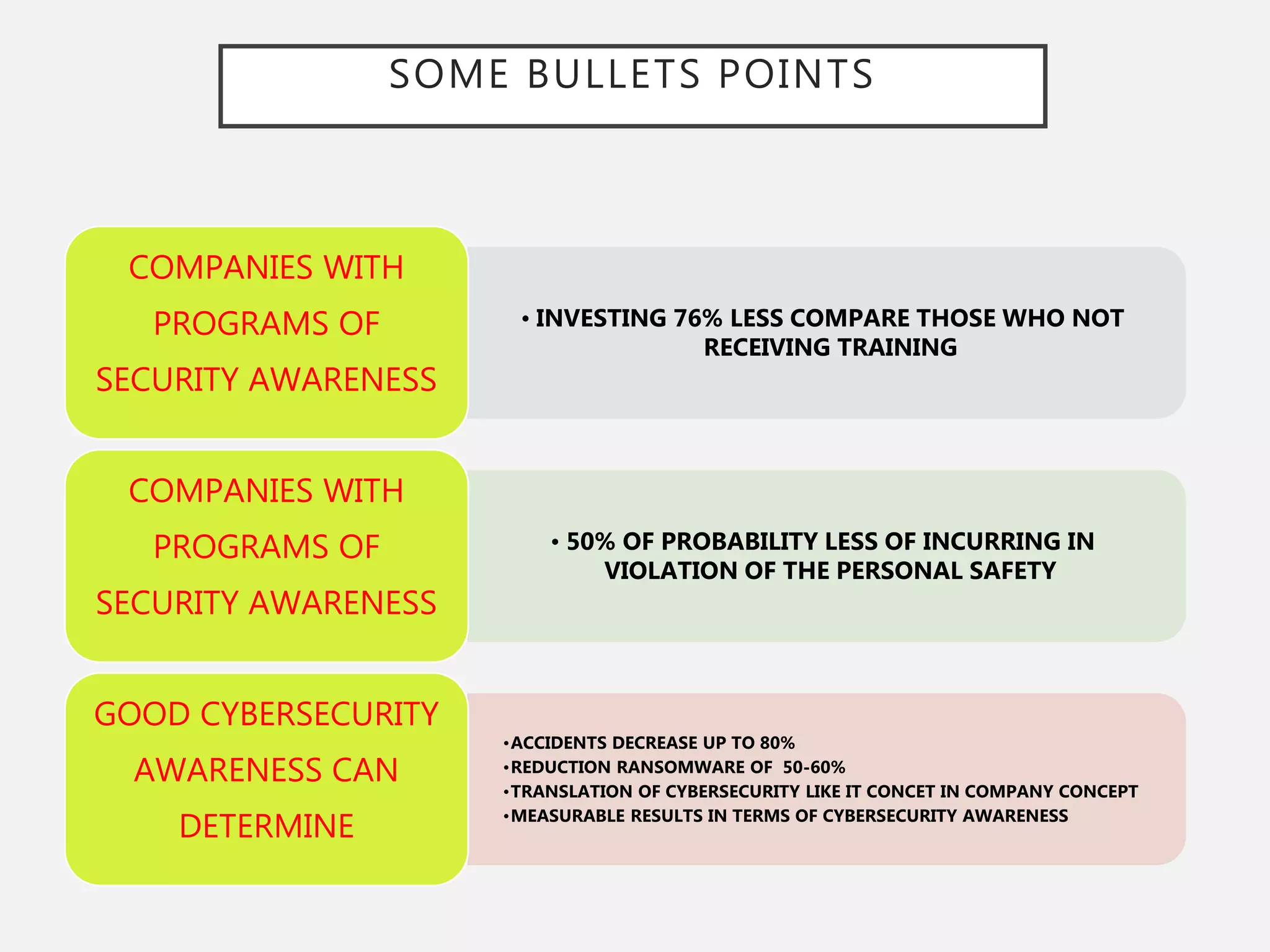
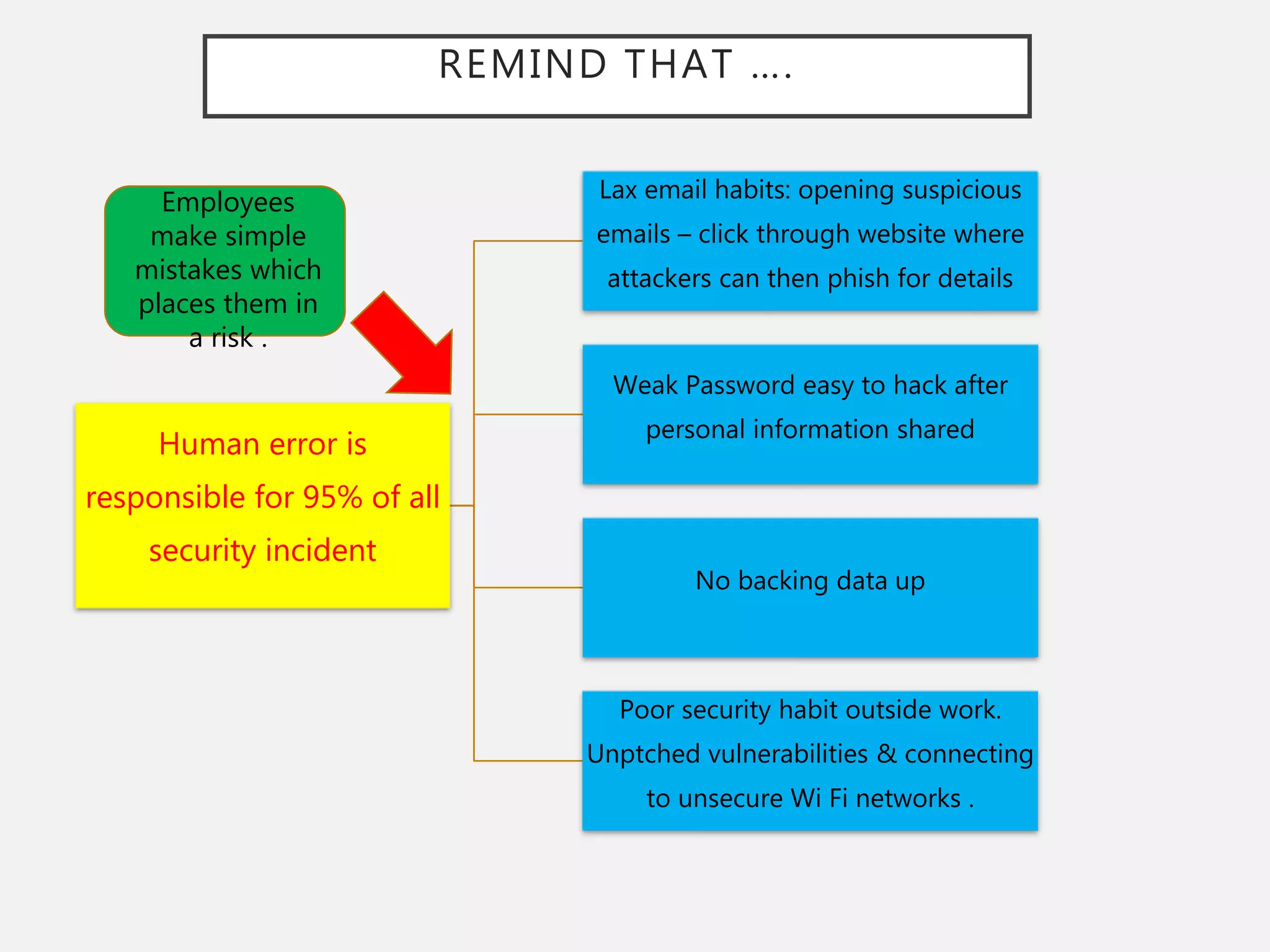
The document discusses the convergence of Information Technology (IT) and Operational Technology (OT), emphasizing the need for improved alignment and shared standards to enhance cybersecurity and reduce risks in various industries. Human factors are highlighted as a significant concern in security incidents, with human error accounting for 95% of incidents, thus underscoring the importance of training and awareness programs. The role of CIOs is evolving to lead the exploitation of business assets across both IT and OT systems, promoting a holistic approach to security management.