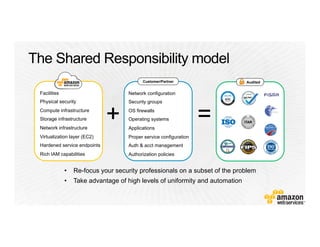
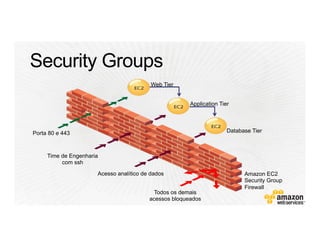
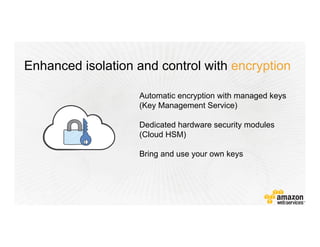
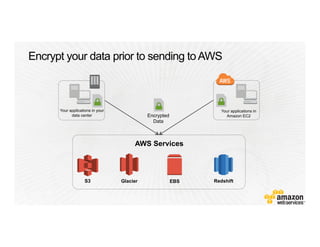
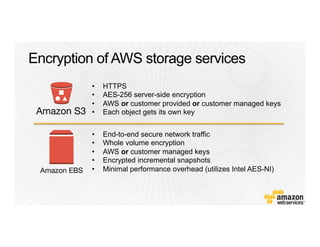
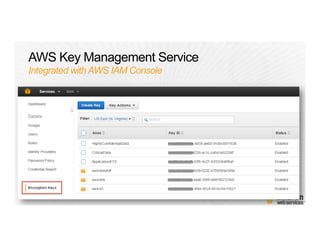
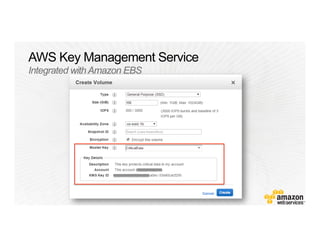
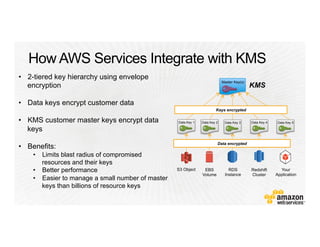
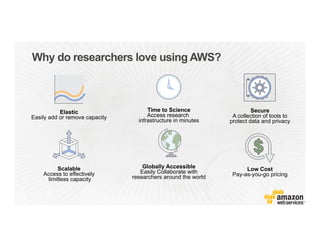
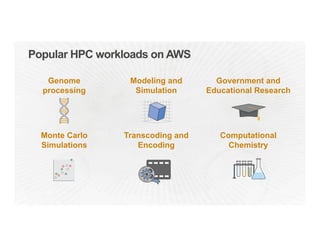
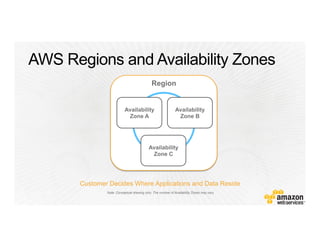
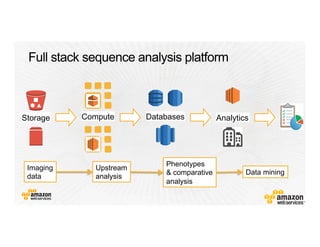
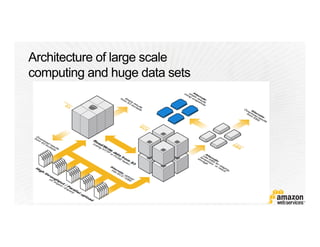
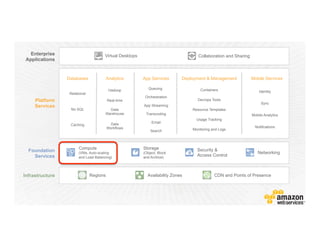
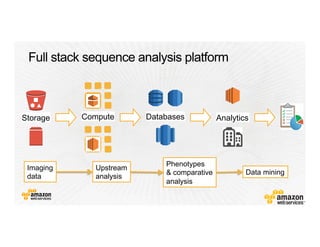
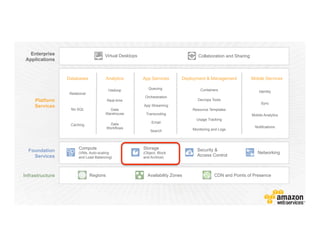
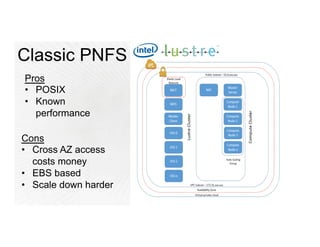
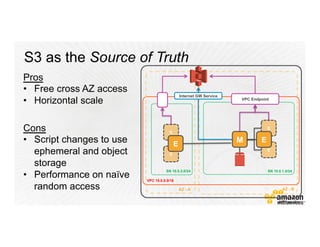
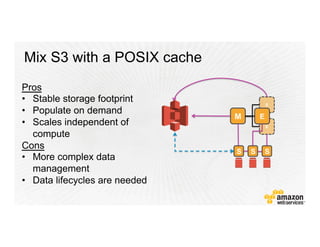
This document provides an overview of Amazon Web Services (AWS) and its capabilities. It describes AWS's global consumer and seller businesses as well as its cloud infrastructure business. It then discusses why researchers love using AWS due to benefits like time to science, global accessibility, low costs, security, and elasticity. Popular high-performance computing workloads on AWS are also listed.
















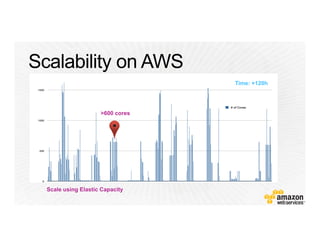




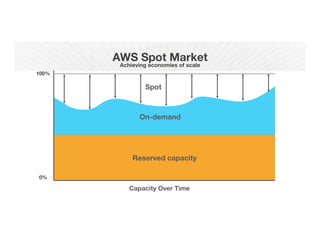
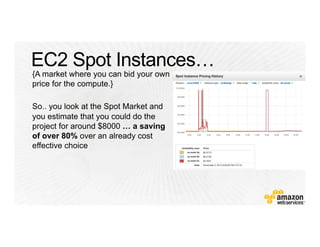
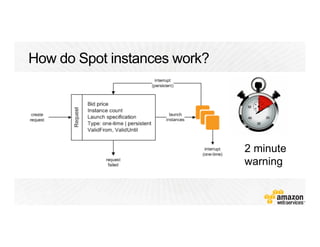














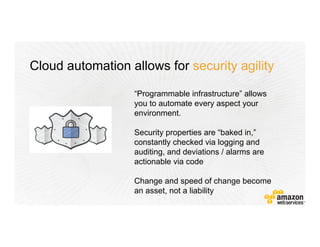
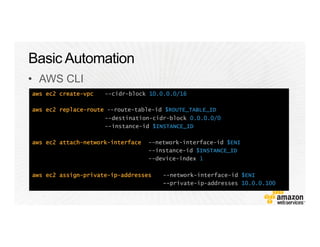


!["Resources" : {
"VPC" : {
"Type" : "AWS::EC2::VPC",
"Properties" : {
"CidrBlock" : “10.0.0.0/16”,
"Tags" : [ { "Key" : “Name", "Value" : “VPCName“ } ]
}
},
"PublicSubnet" : {
"Type" : "AWS::EC2::Subnet",
"Properties" : {
"VpcId" : { "Ref" : "VPC" },
"CidrBlock" : “10.0.1.0/24”,
"Tags" : [ { "Key" : "Network", "Value" : "Public" } ]
}
}
• AWS CloudFormation](https://image.slidesharecdn.com/hpctechnicalworkshoppublic-150605134743-lva1-app6892/85/HPC-in-AWS-Technical-Workshop-71-320.jpg)