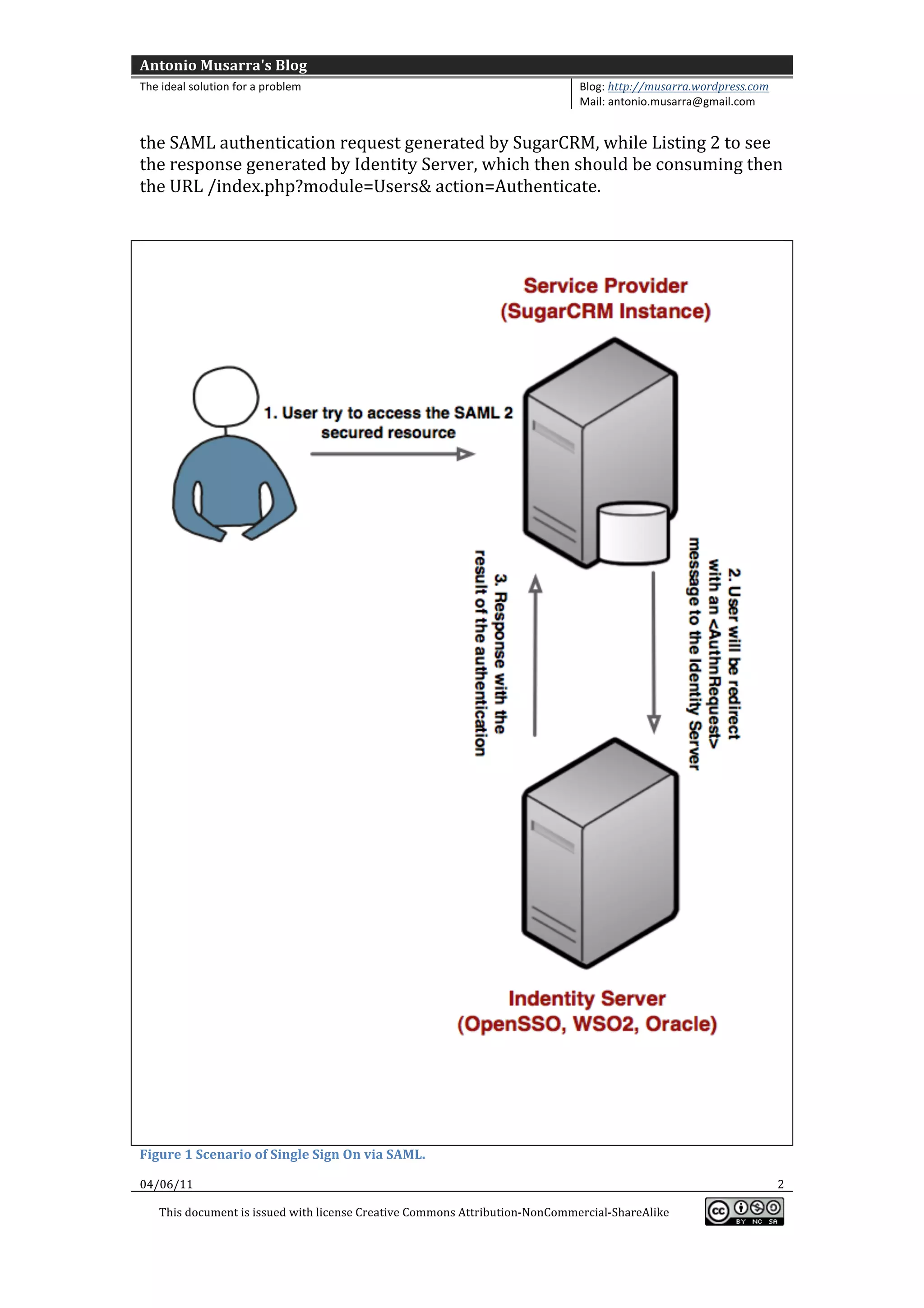
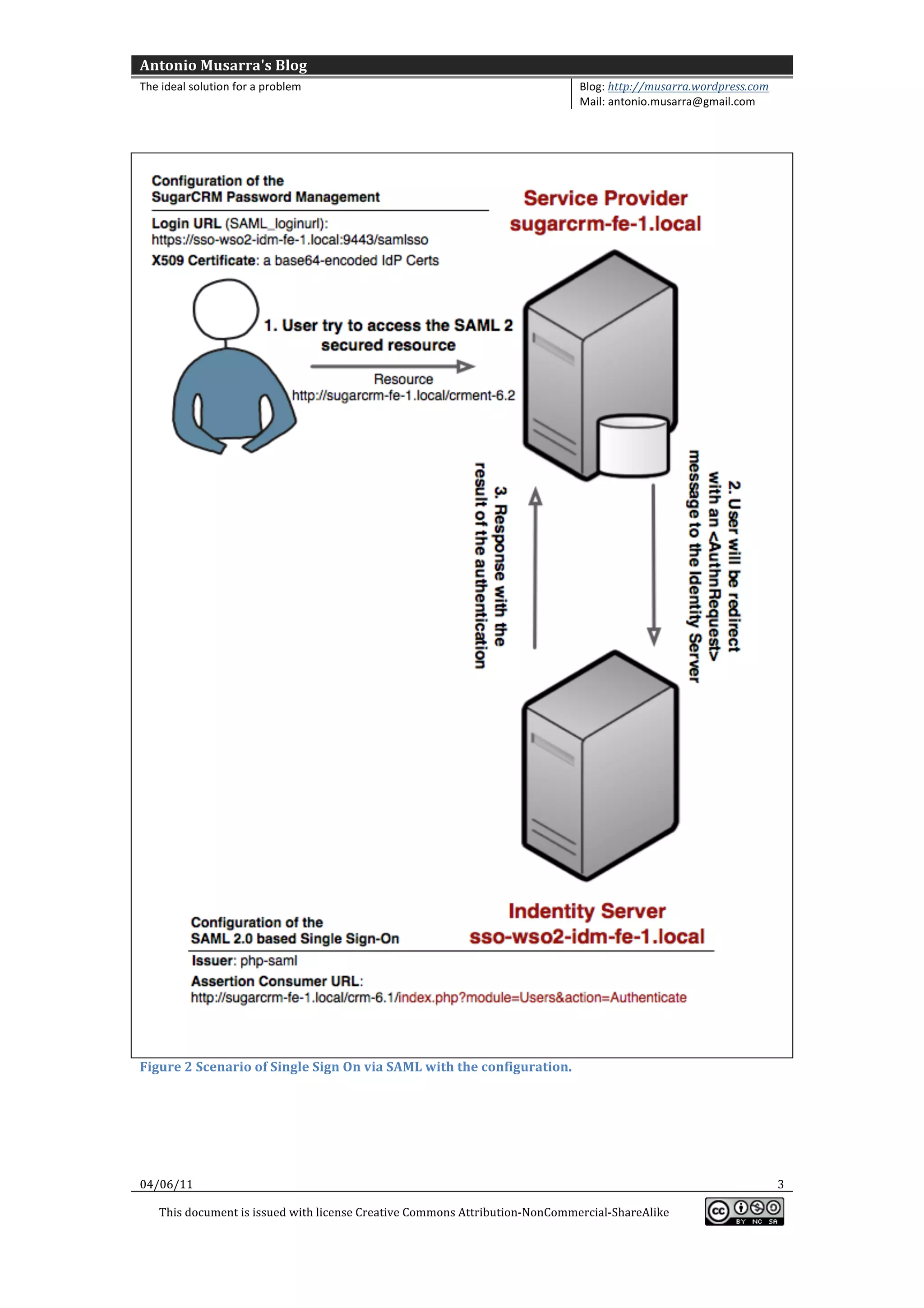
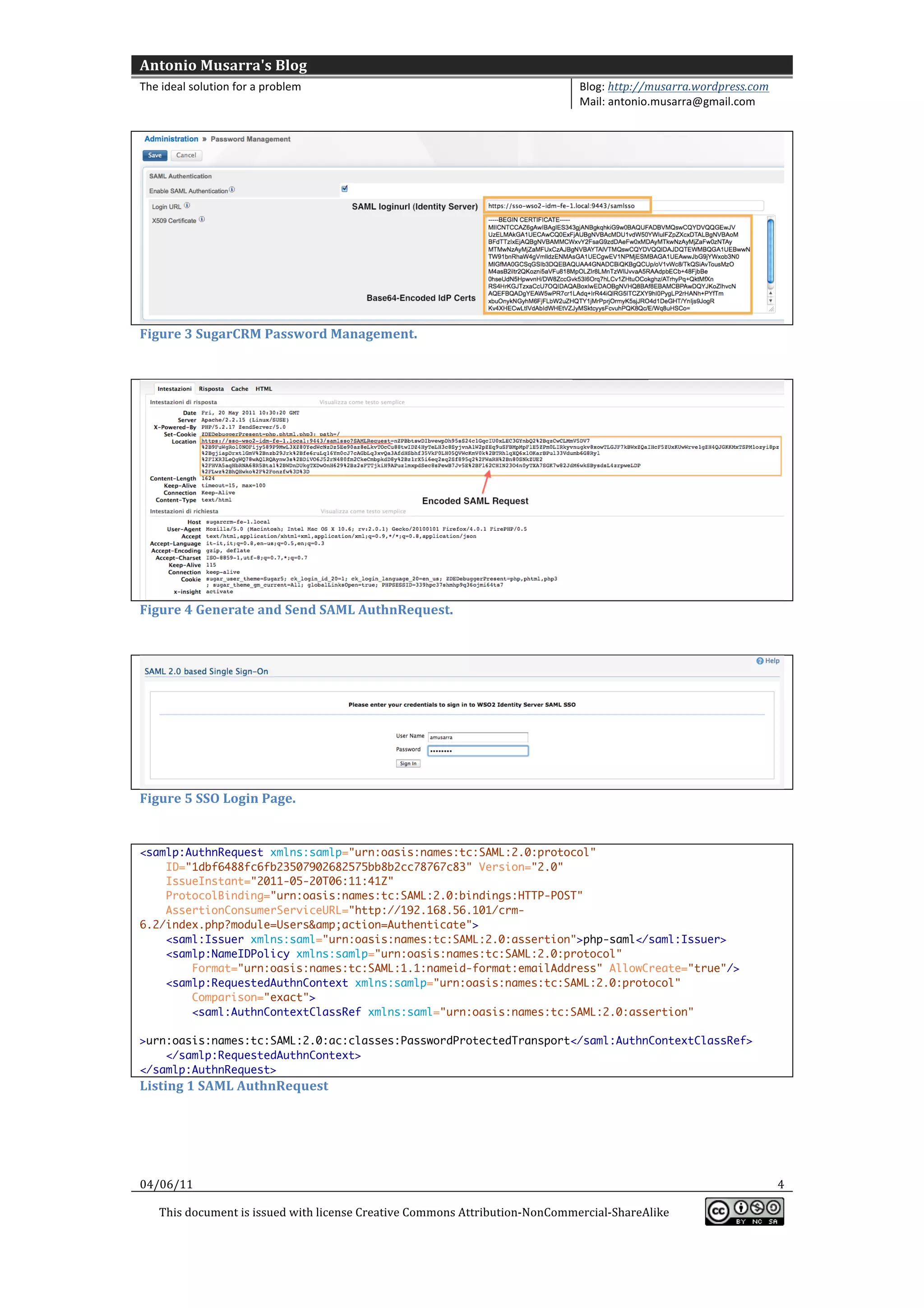
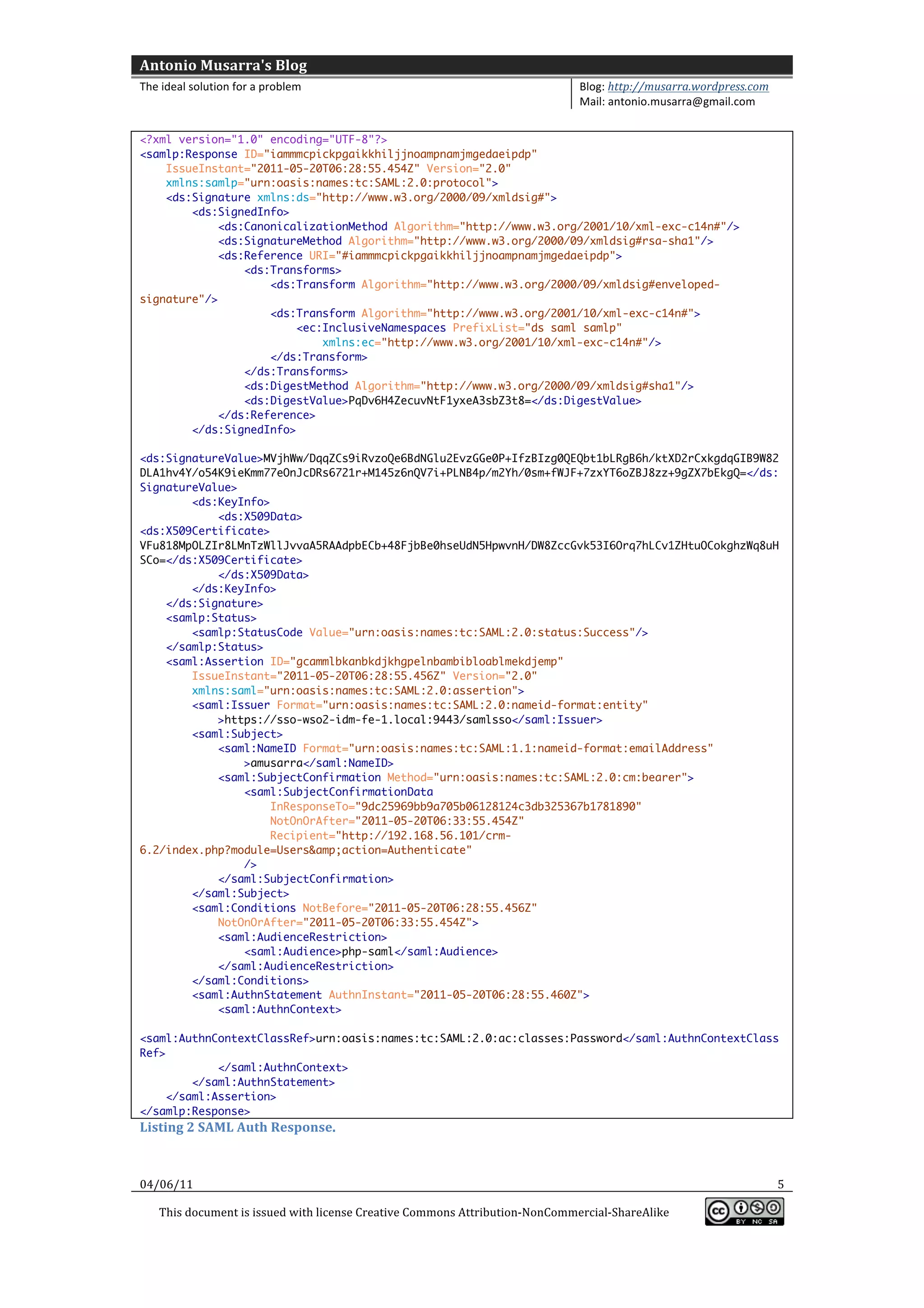
This document provides information and configuration steps for setting up single sign-on (SSO) via SAML between SugarCRM and an identity provider. It includes details on the SAML authentication request generated by SugarCRM and the response from the identity provider. Code snippets and diagrams are included to illustrate the SSO process and configuration parameters.