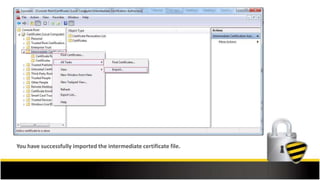
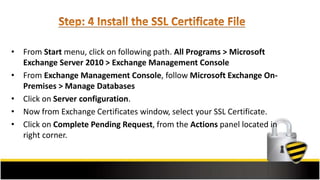
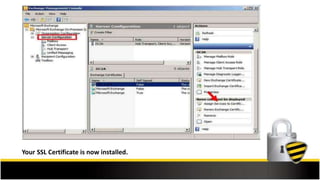
This document outlines the steps to install an SSL certificate on Microsoft Exchange Server 2010, beginning with pre-installation preparations such as purchasing an SSL certificate and generating a CSR. It provides detailed guidance on importing the intermediate certificate, completing the SSL certificate request, and assigning services to the certificate through the Exchange Management Console. Additional resources for support and SSL tools are also included.