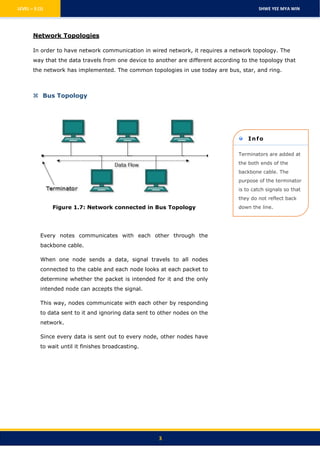
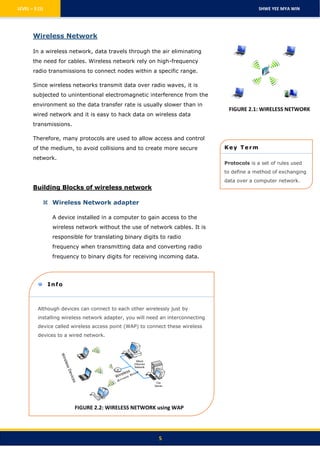
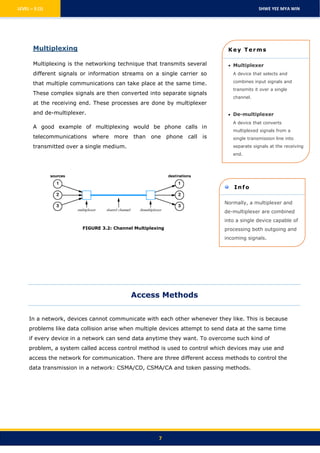
There are several key aspects to how computer networks allow communication between devices:
1) Networks can be classified by their size as local, wide area, or metropolitan area networks, and connect devices using either wired or wireless technologies.
2) For data to be exchanged, networks rely on protocols and network services like packet switching to efficiently transmit information between devices.
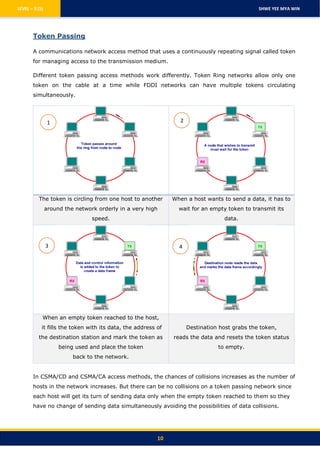
3) Access control methods such as CSMA/CD, CSMA/CA, and token passing are used to manage communication on the network and prevent collisions between transmitting devices.