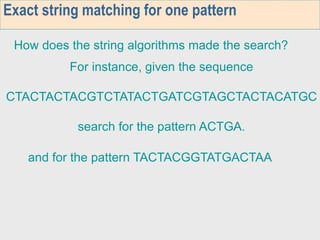
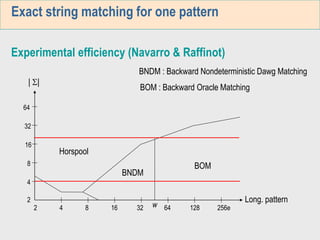
The document discusses algorithms for exact string matching in bioinformatics. It covers:
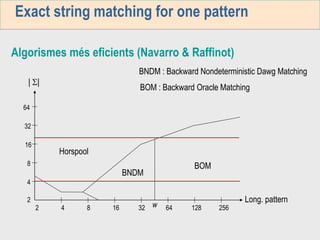
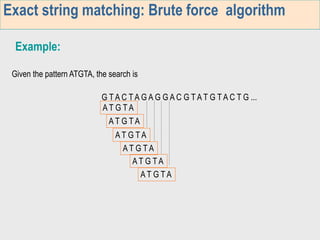
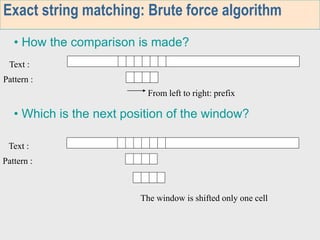
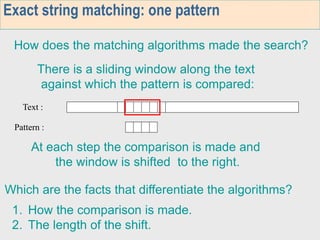
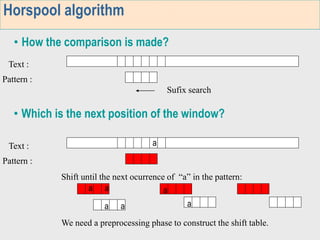
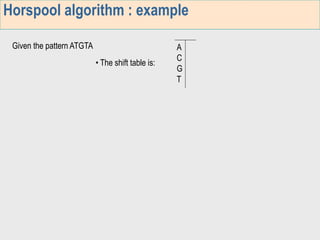
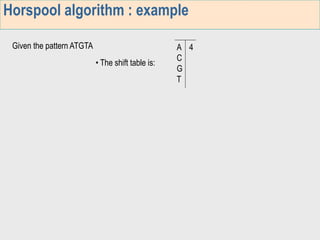
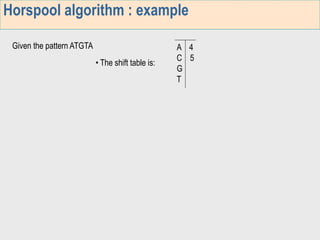
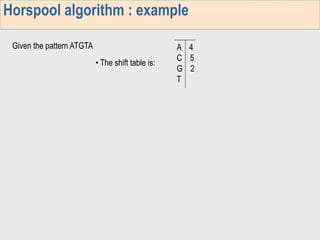
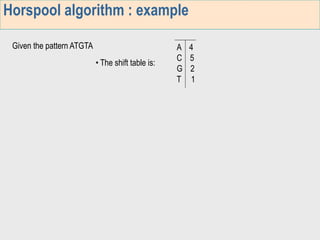
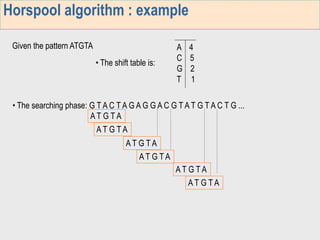
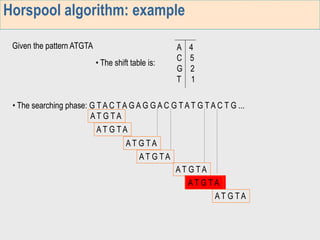
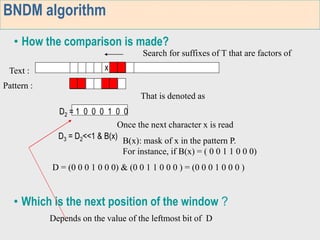
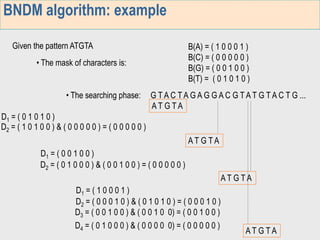
1. The first week focuses on algorithms for exact string matching of a single pattern, including brute force, Horspool's, and BNDM algorithms.
2. The second week covers approximate search and alignment of short sequences.
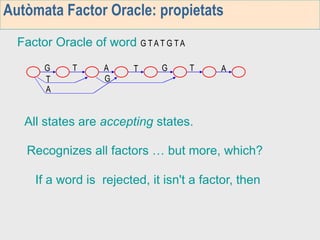
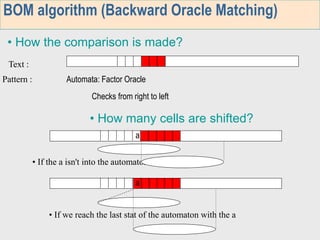
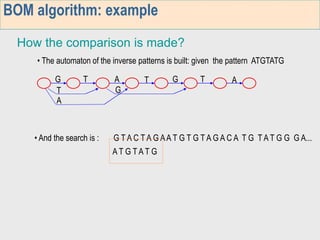
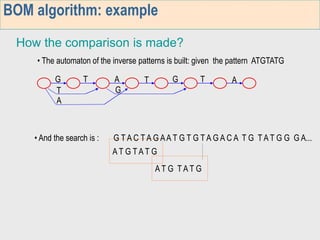
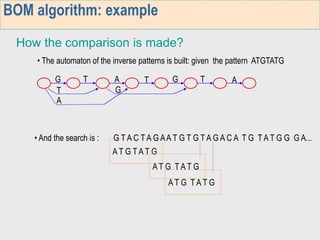
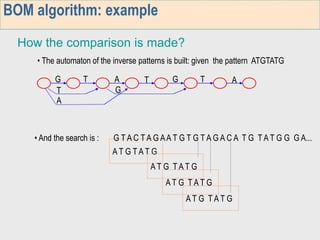
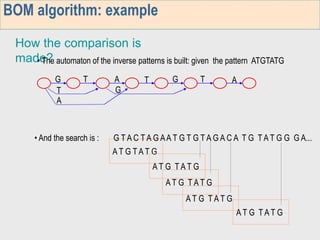
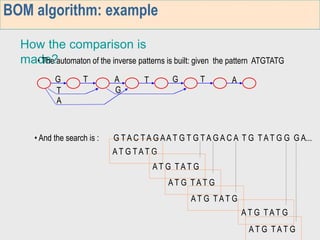
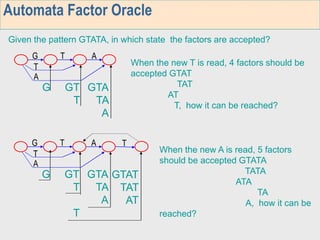
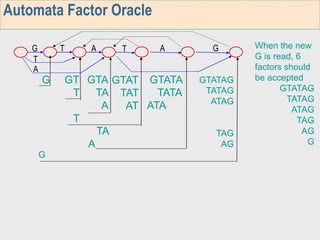
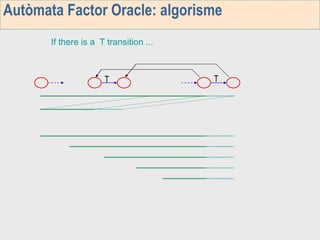
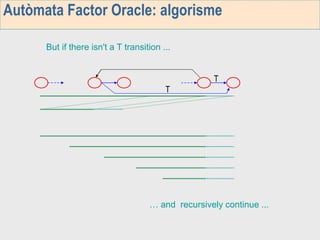
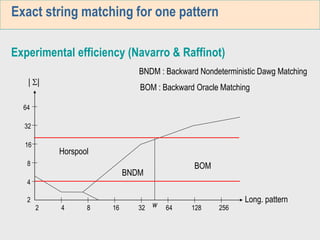
3. The third week deals with searching long sequences. It also discusses building factor automata and the BOM algorithm which uses these automata to match patterns from right to left.



![Extended string matching
• Classes of characters: when in some DNA files or patterns there are
new characters as N or R that means N={A,C,G,T} and R={G,A}.
• Bounded length gaps: we find pattern as ATx(2,3)TA where x(2,3)
means any 2 or 3 characters.
• Optional characters: we find pattern as AC?ACT?T?A where C?
means that C may or may not appear in the text.
• Wild cards: we find pattern as AT*TA where * means an arbitrary long
string.
• Repeatable characters: we find pattern as AT[TA]*AT where [TA]*
means that TA can appear zero or more times..](https://image.slidesharecdn.com/14-15-2-ads-sessio1-240227061549-2626d36a/85/Horspool-Algorithm-in-Design-and-Analysis-of-Algorithms-in-VTU-23-320.jpg)