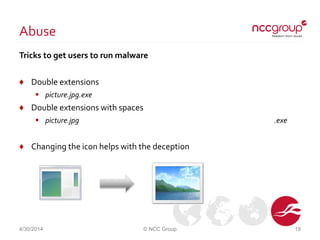
The document discusses the issue of certain Windows file extensions being hidden regardless of user settings, which poses security risks by potentially allowing malicious code execution. It details the registry values associated with hidden file extensions, specifically targeting Microsoft Access and shortcut files, and highlights how these could be exploited. The conclusion emphasizes the need for caution when interacting with files that may have hidden extensions to avoid running malware.













![Digging deeper
♦ Look at subkeys too
C:>reg query HKCRAccess.Shortcut.Diagram.1 /s
HKEY_CLASSES_ROOTAccess.Shortcut.Diagram.1
(Default) REG_SZ Microsoft Access Diagram Shortcut
IsShortCut REG_SZ
NeverShowExt REG_SZ
…
HKEY_CLASSES_ROOTAccess.Shortcut.Diagram.1shellOpencommand
(Default) REG_SZ "C:Program FilesMicrosoft
OfficeOffice14MSACCESS.EXE" /NOSTARTUP /SHELLSYSTEM
[OpenDiagram "%1"]
…
4/30/2014 © NCC Group 16](https://image.slidesharecdn.com/hiddenext44cafe-140501040626-phpapp01/85/The-case-of-the-missing-file-extensions-16-320.jpg)

![Enumeration II
.appref-ms rundll32.exe dfshim.dll,ShOpenVerbShortcut %1|%2
.desklink
.glk C:PROGRA~1MIF5BA~1Office14GROOVE.EXE /grv: "%1"
.library-ms
.lnk
.mad "C:Program FilesMicrosoft OfficeOffice14MSACCESS.EXE" /NOSTARTUP /SHELLSYSTEM [OpenModule "%1"]
.maf "C:Program FilesMicrosoft OfficeOffice14MSACCESS.EXE" /NOSTARTUP /SHELLSYSTEM [OpenForm "%1"]
.mag "C:Program FilesMicrosoft OfficeOffice14MSACCESS.EXE" /NOSTARTUP /SHELLSYSTEM [OpenDiagram "%1"]
.mam "C:Program FilesMicrosoft OfficeOffice14MSACCESS.EXE" /NOSTARTUP /SHELLSYSTEM [ShellOpenMacro "%1"]
.mapimail
.maq C:PROGRA~1MIF5BA~1Office14MSACCESS.EXE /NOSTARTUP /SHELLSYSTEM [OpenQuery "%1"]
.mar "C:Program FilesMicrosoft OfficeOffice14MSACCESS.EXE" /NOSTARTUP /SHELLSYSTEM [OpenReport "%1", 2]
.mas "C:Program FilesMicrosoft OfficeOffice14MSACCESS.EXE" /NOSTARTUP /SHELLSYSTEM [OpenStoredProcedure "%1"]
.mat C:PROGRA~1MIF5BA~1Office14MSACCESS.EXE /NOSTARTUP /SHELLSYSTEM [OpenTable "%1"]
.mau "C:Program FilesMicrosoft OfficeOffice14MSACCESS.EXE" /SHELLSYSTEM [OpenFunction "%1"]
.mav "C:Program FilesMicrosoft OfficeOffice14MSACCESS.EXE" /NOSTARTUP /SHELLSYSTEM [OpenView "%1"]
.maw "C:Program FilesMicrosoft OfficeOffice14MSACCESS.EXE" /NOSTARTUP /SHELLSYSTEM [OpenDataAccessPage "%1"]
.mydocs
.pif "%1" %*
.scf C:Windowsexplorer.exe
.search-ms
.searchConnector-ms
.URL "C:WindowsSystem32rundll32.exe" "C:WindowsSystem32ieframe.dll",OpenURL %l
.website "C:Program FilesInternet Exploreriexplore.exe" -w "%l" %*
.zfsendtotarget
4/30/2014 © NCC Group 18](https://image.slidesharecdn.com/hiddenext44cafe-140501040626-phpapp01/85/The-case-of-the-missing-file-extensions-18-320.jpg)




![Internet shortcut example
♦ The following is an example readme.txt.url
Sends a user to NCC Group’s home page
Sets its icon to be the same as a text file
[{000214A0-0000-0000-C000-000000000046}]
Prop3=19,2
[InternetShortcut]
URL=http://www.nccgroup.com/
IDList=
HotKey=0
IconFile=C:WindowsSystem32shell32.dll
IconIndex=70
4/30/2014 © NCC Group 26](https://image.slidesharecdn.com/hiddenext44cafe-140501040626-phpapp01/85/The-case-of-the-missing-file-extensions-26-320.jpg)





