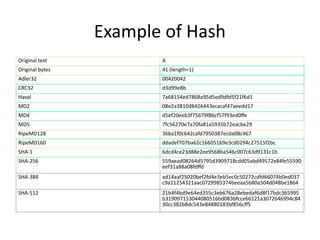
The document provides an overview of hash functions and digital signatures, detailing their definitions, properties, and applications in information security. Hash functions convert inputs into fixed-size strings ensuring data integrity, while digital signatures verify authenticity and prevent tampering using public key cryptography. Both are essential for secure communication and data protection in various applications including email, legal documents, and cryptocurrency.