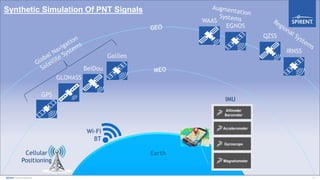
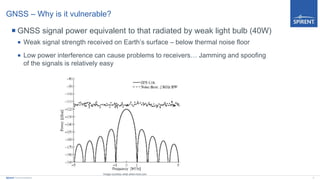
The document discusses vulnerabilities of Global Navigation Satellite Systems (GNSS), particularly GPS, highlighting issues of jamming and spoofing that have resulted in documented real-world incidents affecting transportation and maritime operations. It emphasizes the ease with which GNSS signals can be disrupted and the cybersecurity implications of such vulnerabilities. The author calls for greater awareness and proactive measures in managing GNSS security to mitigate risks associated with these navigational technologies.


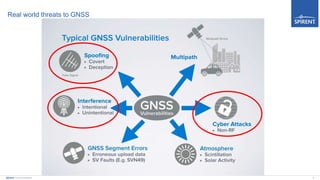
![GPS jamming – real world reports
• 2018: ICAO publish investigation of multiple reports of GPS interference on approach to
Runway 24 at Manila International Airport, More than 50 reports in the 2nd quarter of 2016
• Loss of on-board GNSS functionality
• [GPS-L INVALID] and/or [GPS-R INVALID] messages appear
• Decrease in navigation performance leading to RNP alert
• Loss of Autoland and ADS-B capability
• 2018: Multiple maritime incidents reported in the Eastern Mediterranean Sea. The nature
of the incident is reported to be GPS interference. Five vessels and one aircraft operating
between Cyprus and Port Said, Egypt have reported GPS disruptions/interference
occurring over extended periods and resulting in either inaccurate positions or no position
• 2015: Multiple outbound vessels from a non-U.S. port lost GPS signal reception. Impacts
included loss of collision avoidance capabilities on the radar display.
• 2014: US Coast Guard reported that U.S. port (East Coast ) suffered a seven-hour GPS
signal disruption that crippled operations at one berth - Port cranes were disabled.
Significant delays to port operations ensued
• 2014: FBI aware of 46 reported incidents of luxury car theft where the thieves placed one
or more GPS jammers in cargo containers with stolen automobiles.
• 2014: Cargo thieves in North Florida used GPS jammers to steal a refrigerated trailer
containing a temperature controlled shipment](https://image.slidesharecdn.com/gpsbehavingbadlylightningtalk-180803081418/85/Gps-behaving-badly-Guy-Busenel-7-320.jpg)