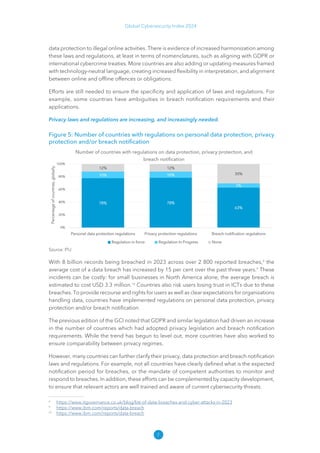
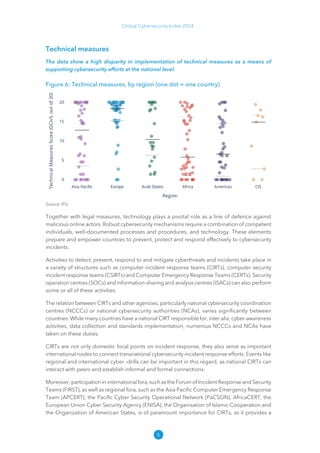
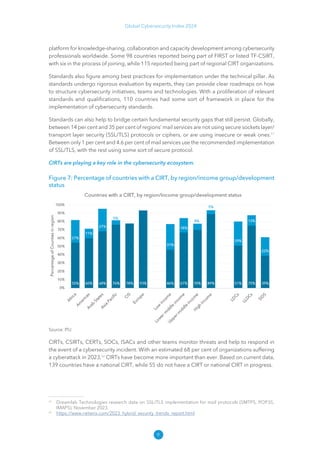
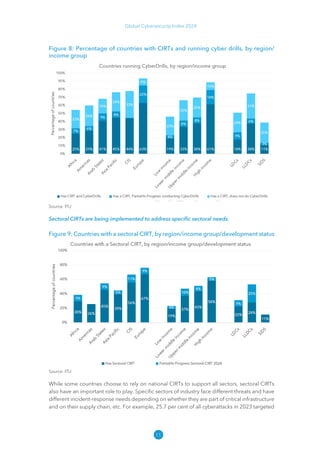
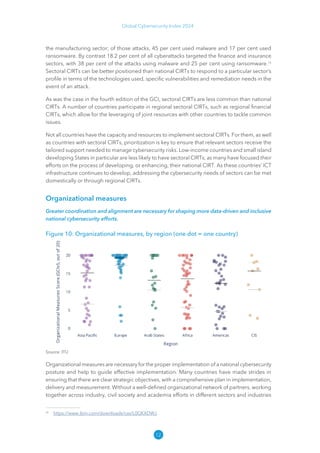
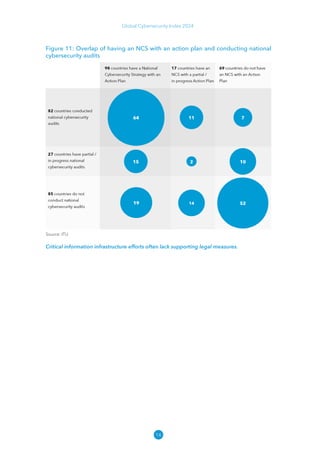
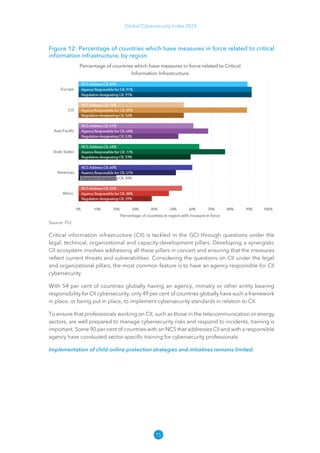
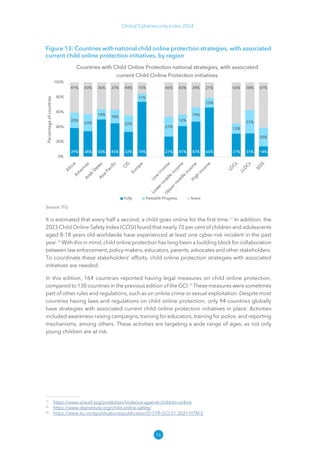
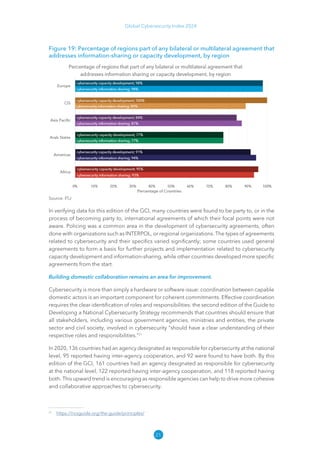
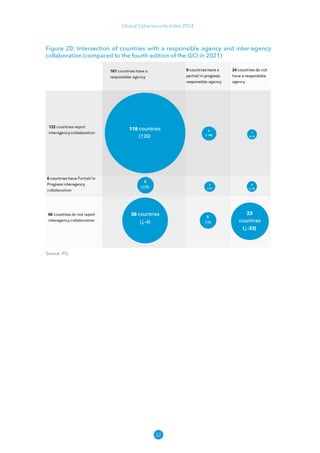
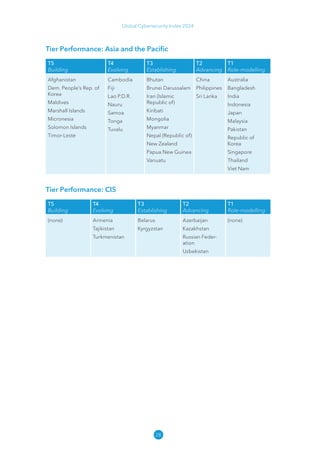
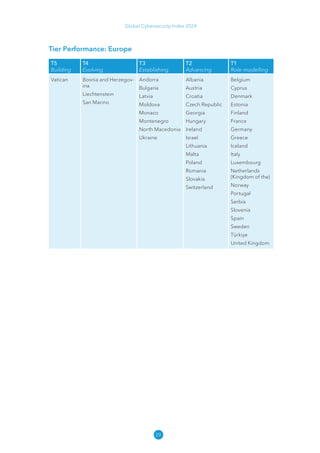
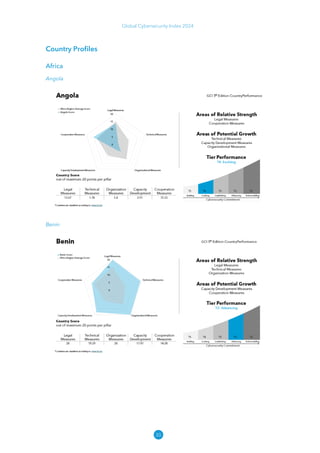
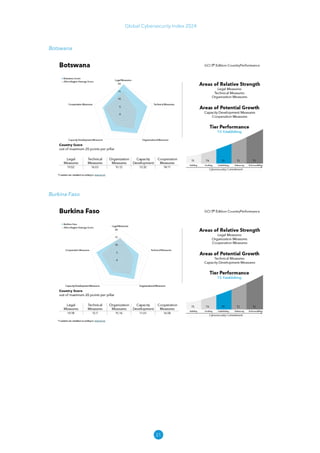
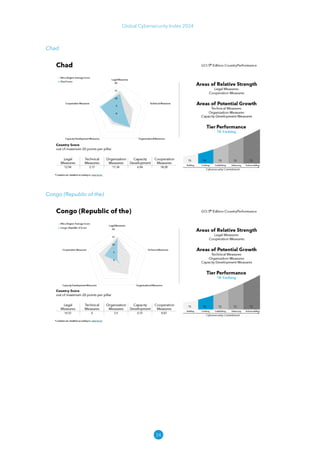
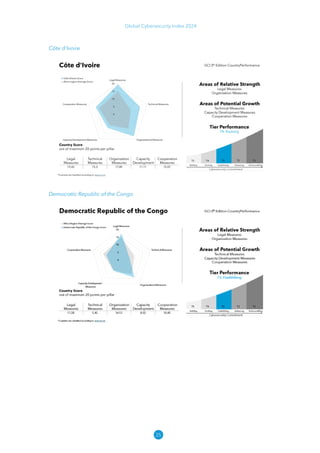
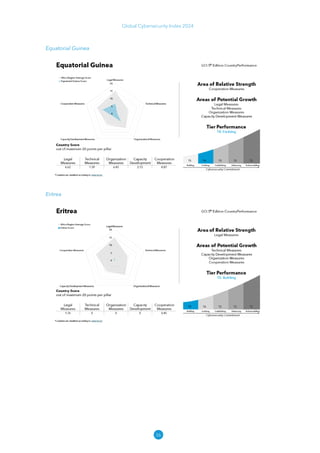
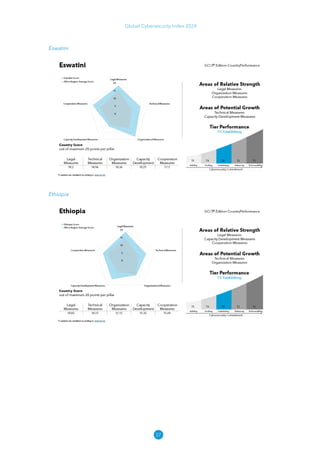
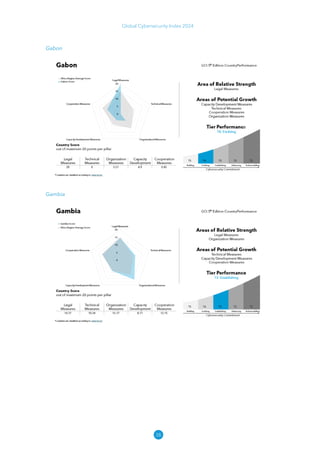
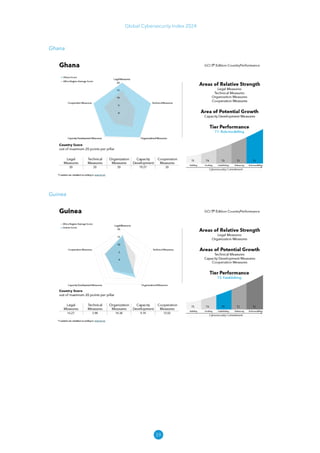
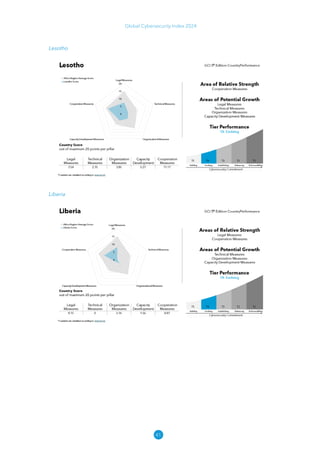
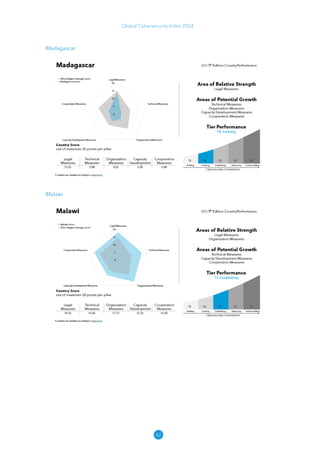
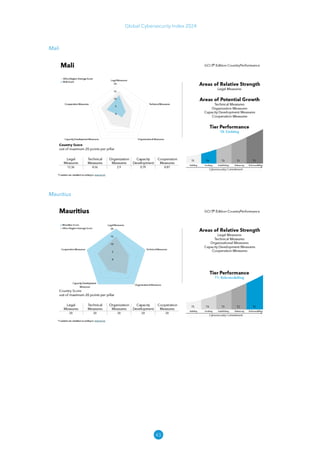
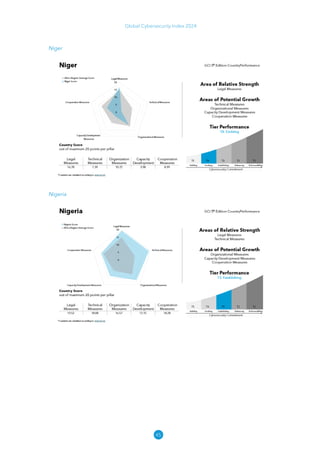
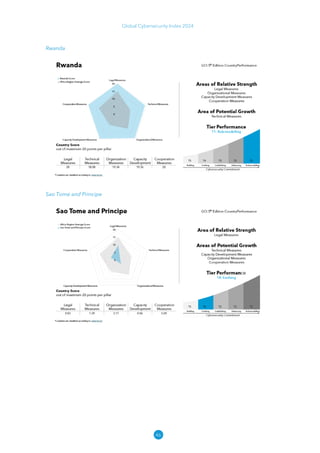
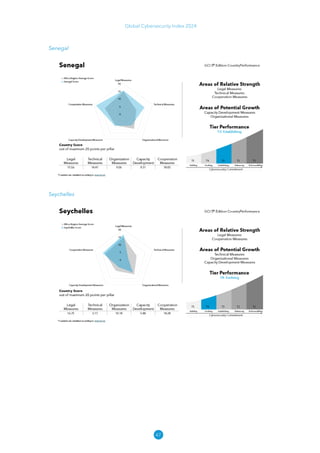
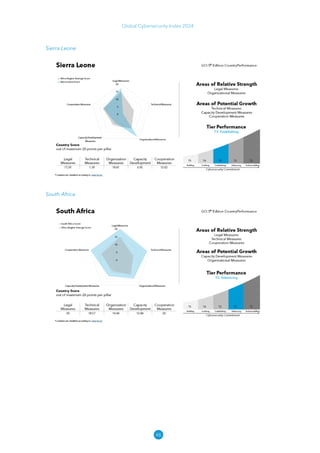
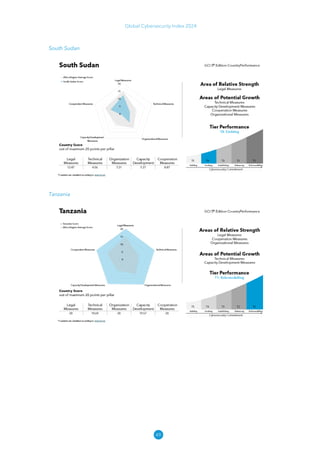
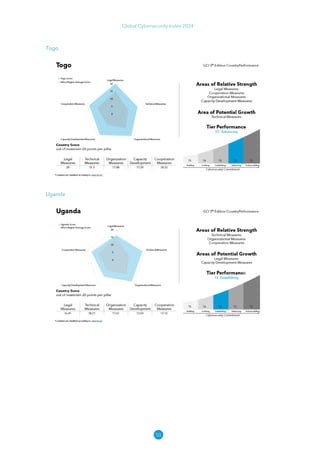
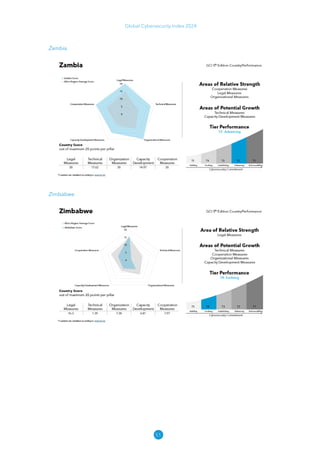
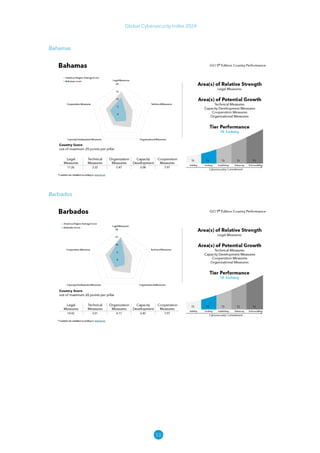
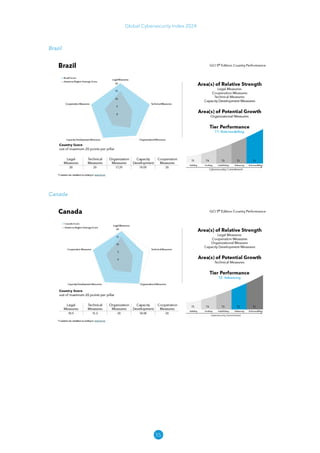
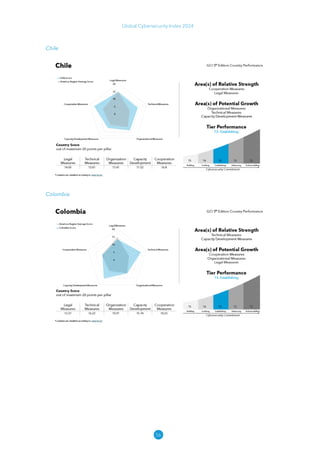
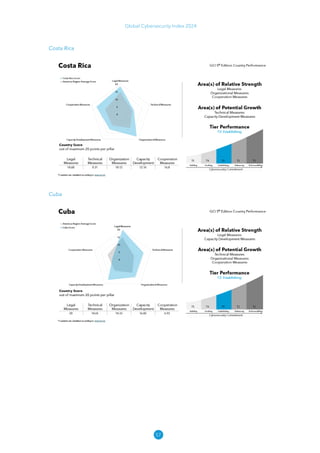
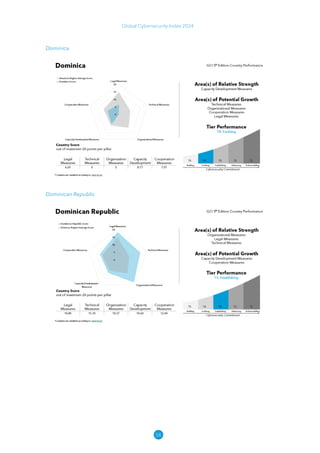
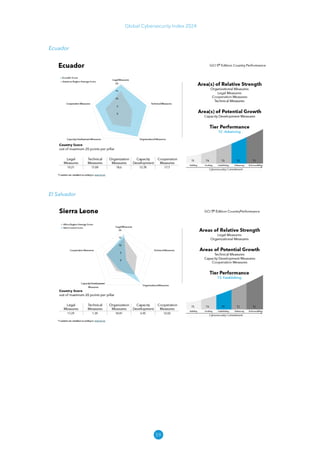
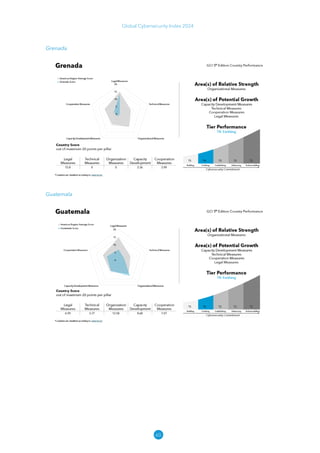
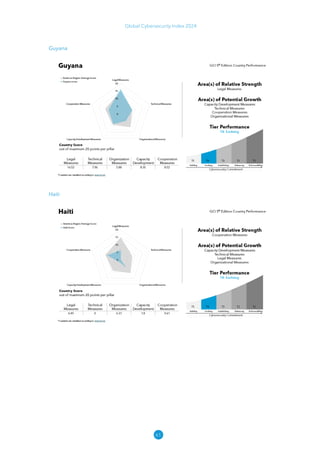
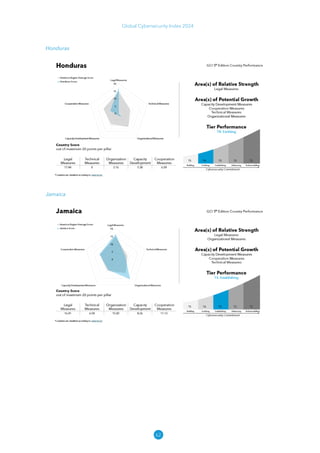
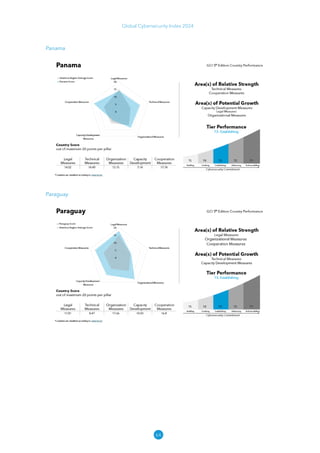
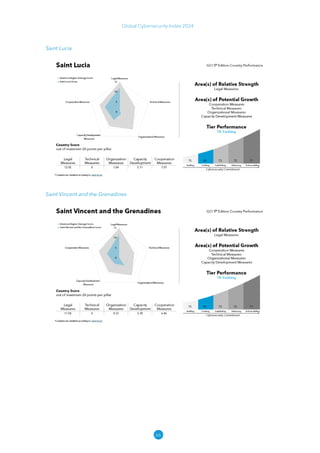
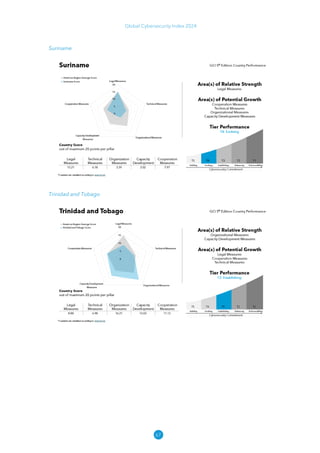
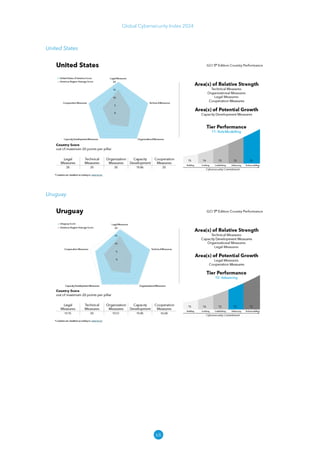
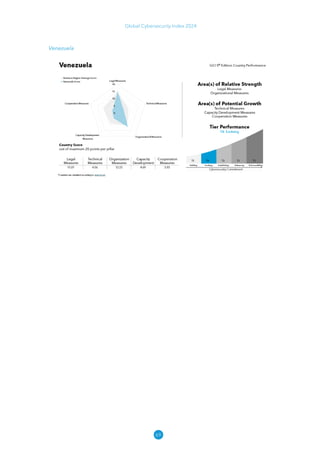
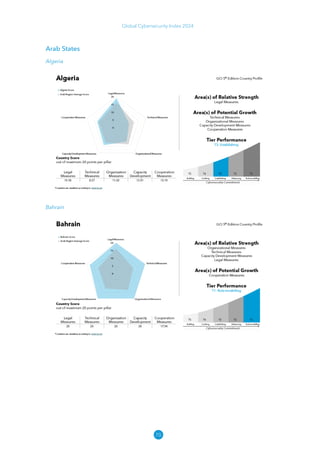
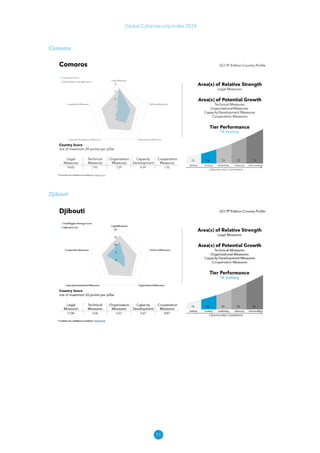
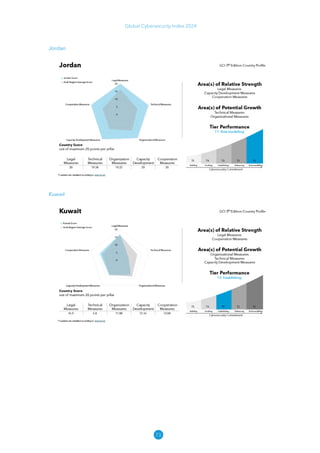
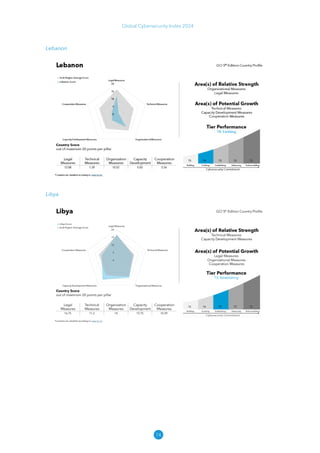
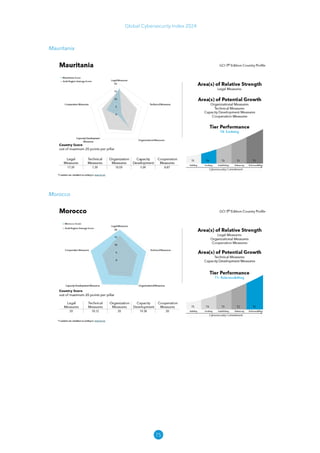
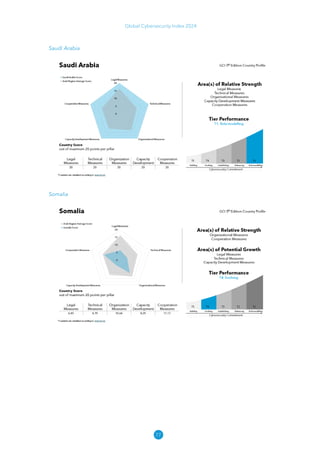
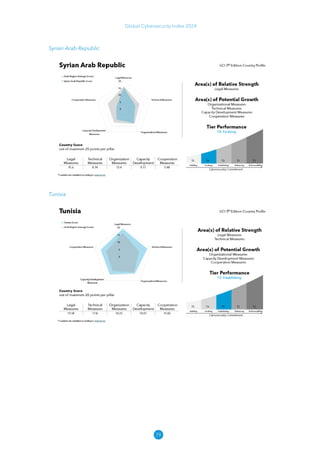
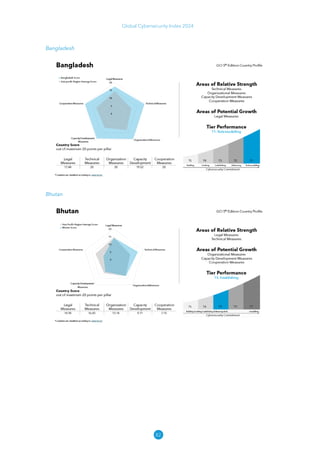
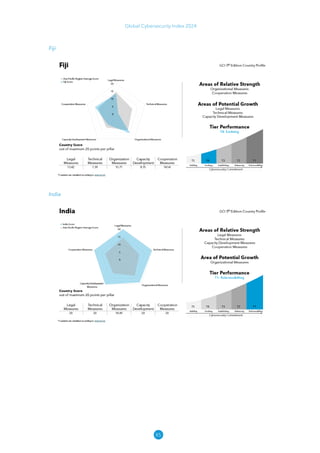
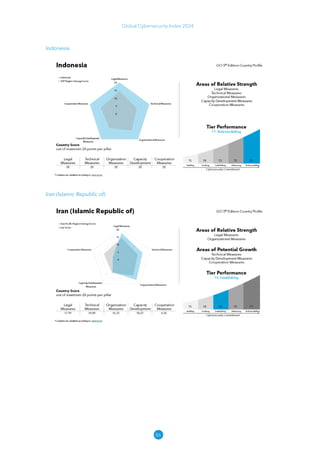
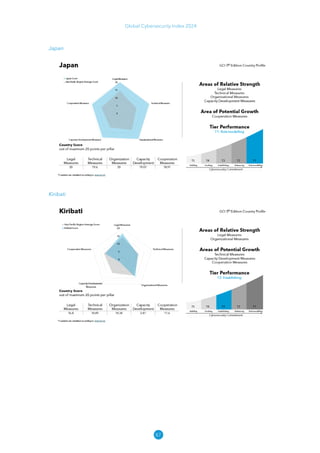
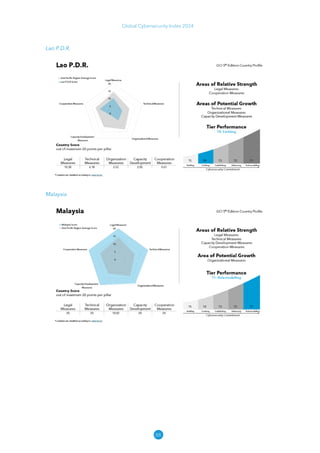
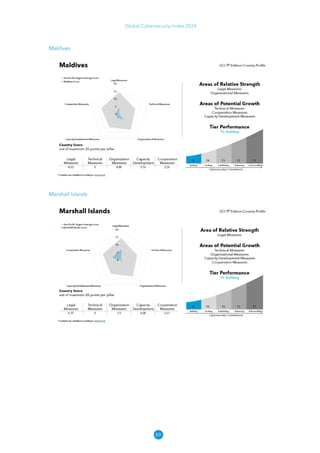
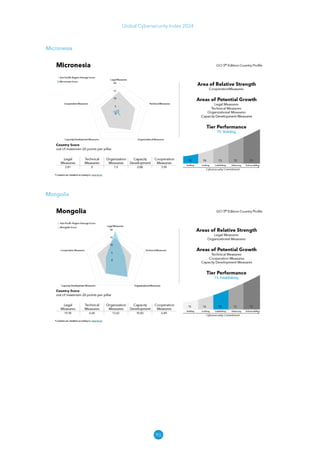
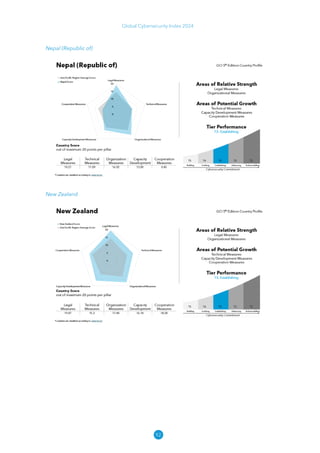
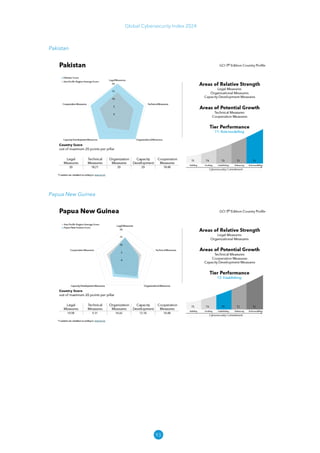
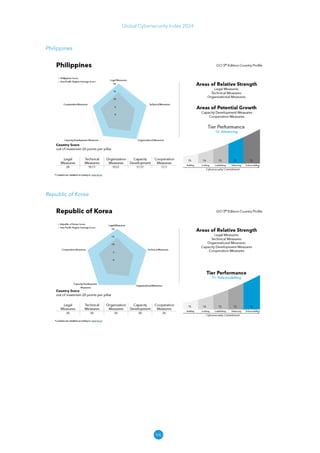
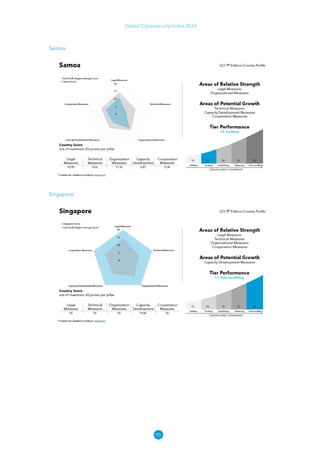
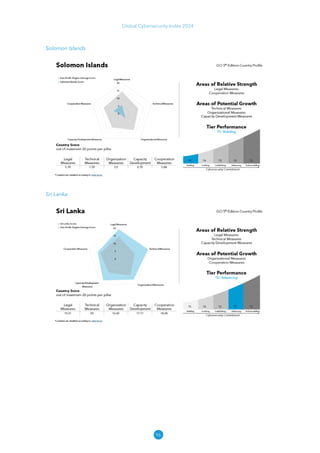
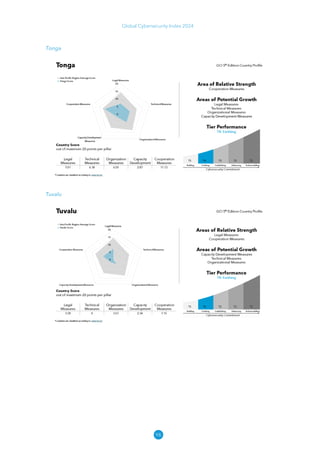
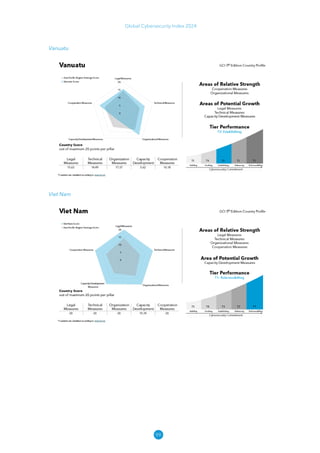
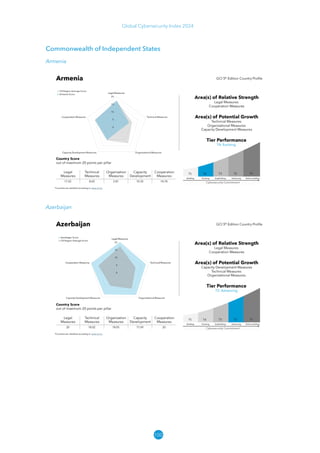
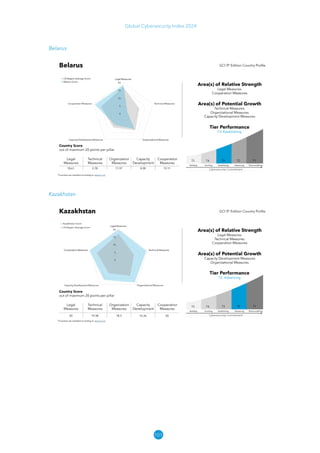
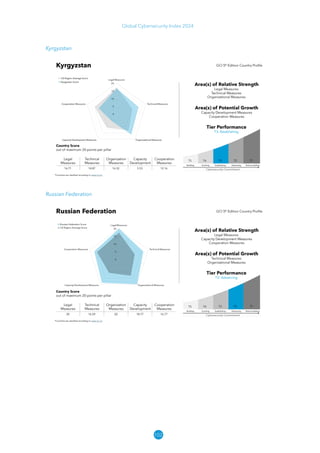
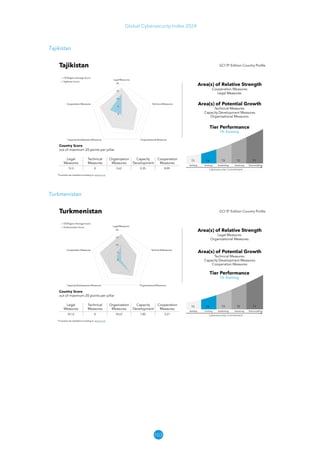
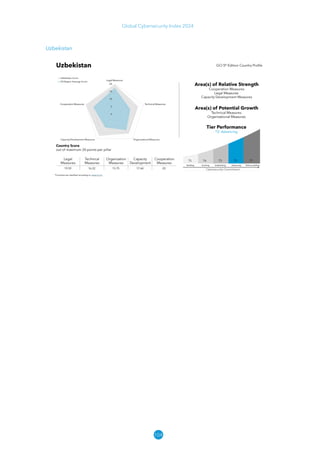
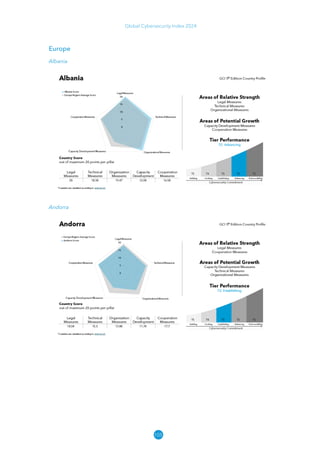
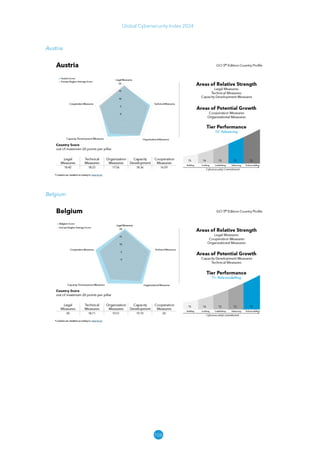
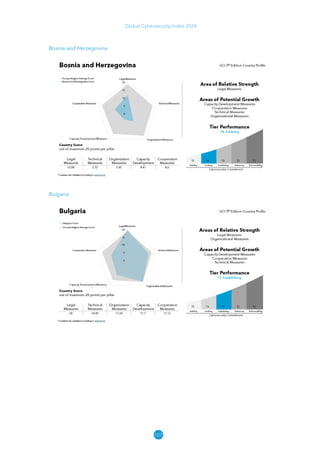
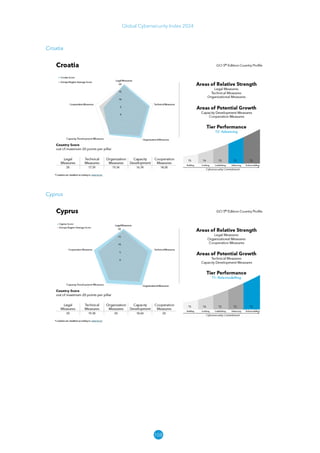
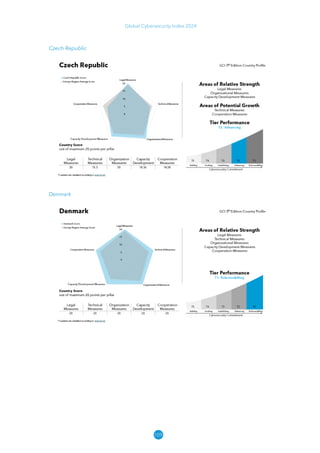
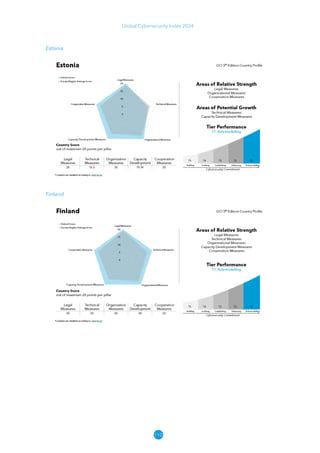
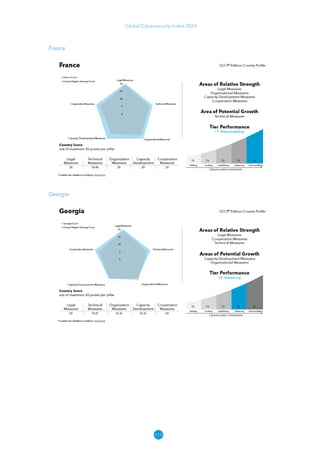
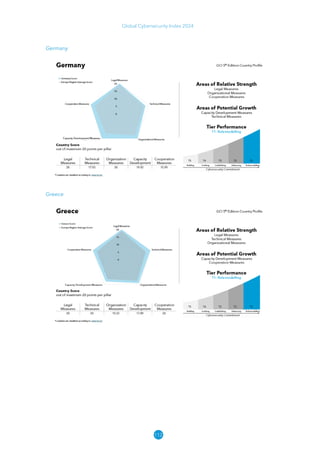
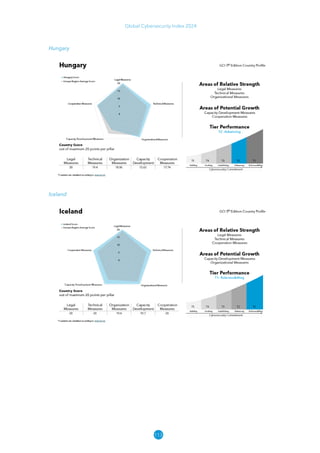
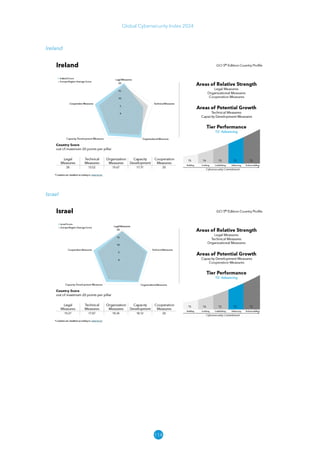
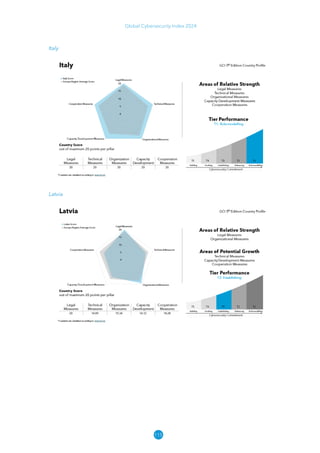
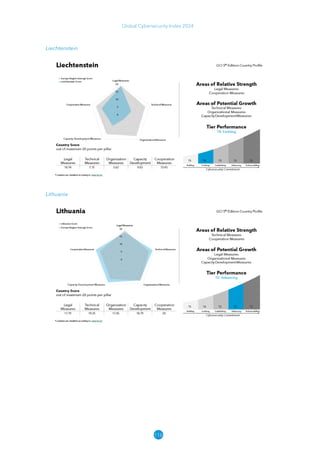
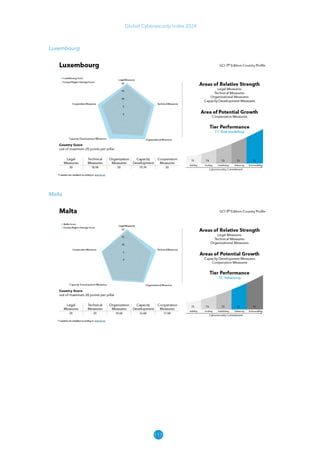
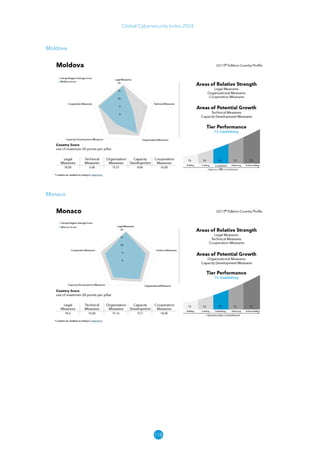
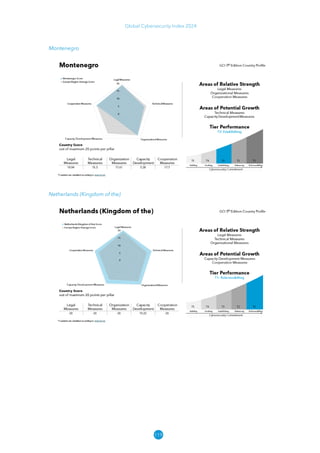
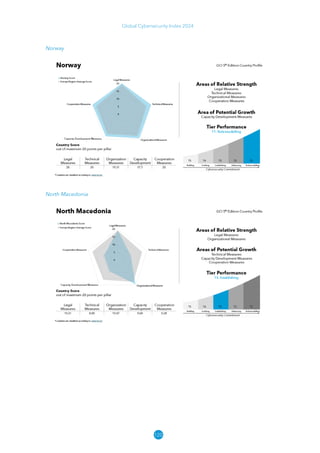
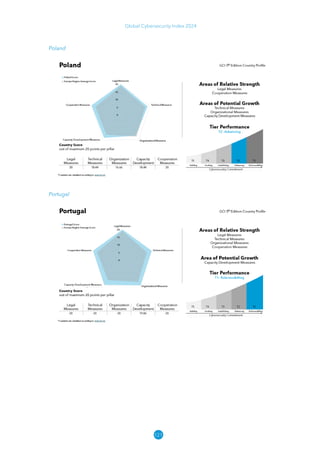
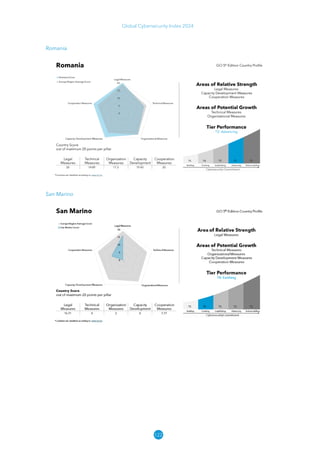
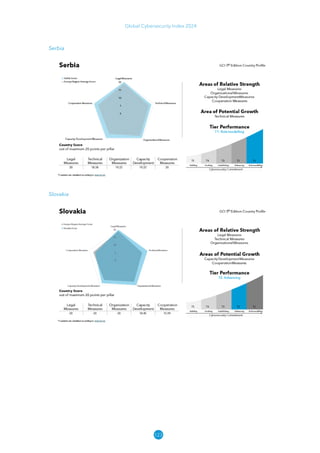
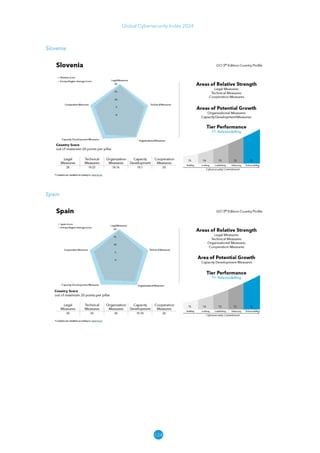
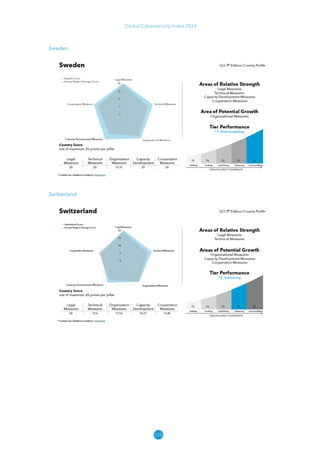
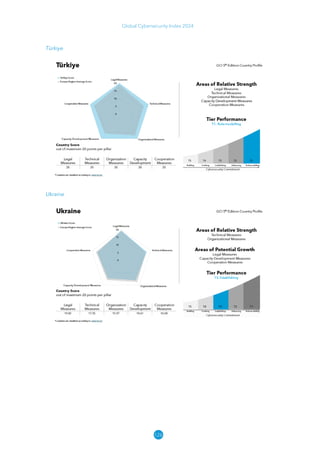
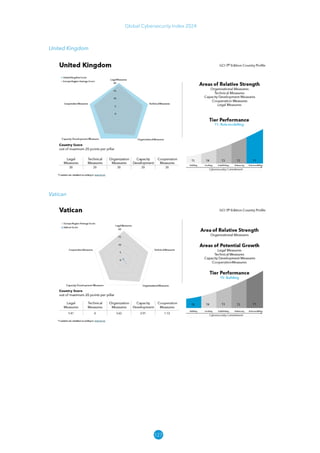
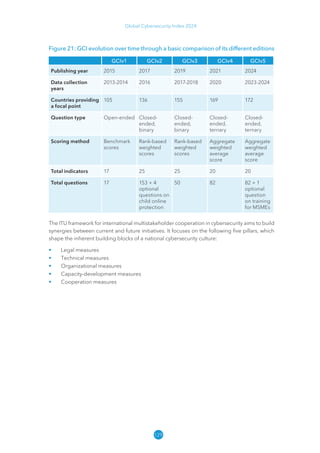
The Global Cybersecurity Index 2024, published by the International Telecommunication Union, assesses countries' cybersecurity commitments across five pillars: legal, technical, organizational, capacity development, and cooperation. This edition highlights record engagement from 194 countries, with an average overall score of 65.7 out of 100, showing a 27% improvement since 2021 in national cybersecurity efforts. It emphasizes the importance of implementing high-quality activities to ensure the effectiveness of cybersecurity initiatives, particularly in addressing the needs of vulnerable populations.