Gdpr encryption and tokenization
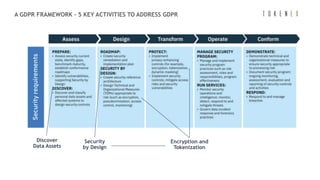
- 1. Encryption and Tokenization 1Source: The IBM GDRP framework Discover Data Assets Security by Design A GDPR FRAMEWORK - 5 KEY ACTIVITIES TO ADDRESS GDPR
- 2. 2 2Source: Forrester 2017 BEST PRACTICE - FIND AND PROTECT YOUR SENSITIVE DATA
- 3. Field Real Data Tokenized / Pseudonymized Name Joe Smith csu wusoj Address 100 Main Street, Pleasantville, CA 476 srta coetse, cysieondusbak, CA Date of Birth 12/25/1966 01/02/1966 Telephone 760-278-3389 760-389-2289 E-Mail Address joe.smith@surferdude.org eoe.nwuer@beusorpdqo.org SSN 076-39-2778 076-28-3390 CC Number 3678 2289 3907 3378 3846 2290 3371 3378 Business URL www.surferdude.com www.sheyinctao.com Fingerprint Encrypted Photo Encrypted X-Ray Encrypted Healthcare / Financial Services Dr. visits, prescriptions, hospital stays and discharges, clinical, billing, etc. Financial Services Consumer Products and activities Protection methods can be equally applied to the actual data, but not needed with de-identification 3Source: Customer Case Study DATA DE-IDENTIFICATION / ANONYMIZATION
- 4. 4 4Source: Gartner ENCRYPTION & TOKENIZATION LEVELS
- 5. 5 5Source: Gartner Less Secure More Secure ENCRYPTION AND TOKENIZATION BEST PRACTICES
- 6. Tokens Tokens PII Tokens Tokens • Protecting Personally Identifiable Information (PII), including names, addresses, phone, email, policy and account numbers • Compliance with EU Cross Border Data Protection Laws • Utilizing Data Tokenization, and centralized policy, key management, auditing, and reporting 6 6Source: International Customer Case Study PROTECT PII DATA CROSS BORDER - BEST PRACTICES
- 7. *: Underlying sensitive value (USV) Source: ANSI X9 7 ANSI X9 - CURRENT TOKENIZATION STANDARD
- 8. • Format-preserving encryption (FPE) is useful in situations where fixed-format data, such as Primary account numbers Social Security numbers, must be protected. • FPE will limit changes to existing communication protocols, database schemata or application code. 8Source: Accredited Standards Committee ANSI X9 2018 ANSI X9 STANDARD FOR FORMAT PRESERVING ENCRYPTION
- 9. Quantum computers will be able to instantly break the encryption of sensitive data protected by today's strongest security, warns the head of IBM Research. This could happen in a little more than five years because of advances in quantum computer technologies. Encryption and Tokenization today are effective means to protect a data subject's PII per the GDPR regulation, and that they will not be soon due to the enhancements in Quantum computing. 9Source: IBM and ZDNet STANDARD ENCRYPTION AND TOKENIZATION ARE EFFECTIVE TO MEET GDPR
- 10. 10Source: THALES at RSA Conference 2018 Quantum Cryptanalysis is effectively “breaking cryptology with quantum computers” THIS IS A BIG THREAT! If our cryptography is broken, then everything breaks! Glover’s algorithm Given a functioning Universal Quantum Computer, Glover’s algorithm weakens the currently assumed strength of symmetric algorithms like AES Shor’s algorithm Given a functioning Universal Quantum Computer, Shor’s algorithm weakens the currently assumed strength of symmetric algorithms like RSA, ECC QUANTUM CRYPTANALYSIS
- 11. Quantum cryptography allows communication that is guaranteed to be secure, thanks to the laws of physics. And it is becoming increasingly important. Physicists have long known that quantum computers will be able to break almost all other types of cryptography. Since these devices are becoming more capable, the writing is on the wall for conventional encryption. 11Source: MIT University CHINESE SATELLITES USING QUANTUM ENCRYPTION
- 12. 12Source: Thales Quantum Cryptography is effectively “doing cryptography with quantum computers” There are several potential techniques One thing that is well established is Quantum Key Distribution • This has almost nothing to do with Quantum Computing • Transmit keys from one place to another as quantum state in photons • Relies on the quantum mechanical phenomenon that you cannot observe a photon without disturbing its state • Theoretically extremely secure, but suffers practical issues Famously recently used by China in satellites QUANTUM CRYPTOGRAPHY
- 13. 13Source: scmp.com/news/china/economy The mission can provide unbreakable secret communications channels, in principle, using the laws of quantum science. Is China winning the race with the US to develop quantum computers? Chinese funding to research the next generation in computing may be dwarfing American efforts, according to US experts. IS CHINA WINNING THE RACE?
- 14. Quantum key distribution (QKD), which is the process of using quantum communication to establish a shared key between two parties (Alice and Bob, for example) without a third party (Eve) learning anything about that key, even if Eve can eavesdrop on all communication between Alice and Bob. If Eve tries to learn information about the key being established, key establishment will fail causing Alice and Bob to notice. Once the key is established, it is then typically used for encrypted communication using classical techniques. 1414Source: C. H. Bennett and G. Brassard: Quantum cryptography: Public key distribution What is Quantum Key Distribution? HOW IS QUANTUM KEY CRYPTOGRAPHY DIFFERENT?
- 15. 15 15Source: The RSAC 2018 Conference Zulfikar Ramzan, Ph.D. Chief Technology Officer, RSA Moderator Whitfield Diffie Cryptographer and Security Expert, Cryptomathic Paul Kocher Security Researcher, Independent Moxie Marlinspike Founder, Signal Ronald Rivest MIT Institute Professor, MIT Adi Shamir Borman Professor of Computer Science, The Weizmann Institute, Israel The three inventors, which the RSA patent is named after, are Ronald Rivest, Adi Shamir, and Leonard Adleman. *: Matthew Rosenfield, known as Moxie Marlinspike, is an American computer security researcher, * THE RSAC 2018 CRYPTOGRAPHERS PANEL
- 16. Lattice-based cryptography is the generic term for constructions of cryptographic primitives that involve lattices, either in the construction itself or in the security proof. Lattice-based constructions are currently important candidates for post- quantum cryptography. Unlike more widely used and known public-key schemes such as the RSA, Diffie-Hellman or Elliptic-Curve cryptosystems. 16Source: RSAC 2018 Will Lattice-based cryptography to replace RSA, ECC and D-H? LATTICE-BASED CRYPTOLOGY
- 17. 17 ISO/IEC 27002 Security Controls ISO/IEC 27001 ISO/IEC 27005 Risk Management ISO/IEC 29134 Privacy Impact ISO/IEC 27018 PII in Cloud ISO/IEC 29101 Privacy by Design ISO/IEC 29100 Privacy for Cloud ISO/IEC 17788 Definitions ISO/IEC 27000 series – ITSEC Management A company that has implemented ISO 27001 has already done at least half the job of achieving GDPR compliance Source: itgovernance.co.uk Information technology - Security techniques - Code of practice for protection of personally identifiable information (PII) in public clouds acting as PII processors International Organization for Standardization ISO 27001 HALF THE JOB OF ACHIEVING GDPR COMPLIANCE
- 18. • Methods a quantum computer could use to break encryption and how these attacks will specifically affect the different cryptographic methods used today • Updates on the work being done by NIST to identify quantum safe algorithms • Guidance for financial services organizations to mitigate quantum computing risk • Next steps that X9, as a standards body, needs to take over the next few years to prepare for the post-quantum world 18Source: MIT University and ANXI X9 NIST and ANSI X9 Defining Quantum Safe Encryption Algorithms PREPARE FOR THE POST QUANTUM WORLD
- 19. 19 GDPR and TokenEx If you are a data controller who has a valid reason--other than consent from the data subject--for the processing of his or her personal data “for a purpose other than that for which the personal data have been collected”, Article 6(4)(e) obligates you to use “appropriate safeguards, which may include encryption or pseudonymization. The TokenEx platform enables you to pseudonymize personal data within your environment, by replacing it with tokens, and storing the personal data in an encrypted TokenEx cloud token vault. The GDPR requires “data protection by design and by default.” Article 25(1) specifically obligates controllers to “…implement appropriate technical and organizational measures, such as pseudonymization.” The TokenEx platform enables you to pseudonymize personal data within your environment, replacing it with tokens, and storing the data in an encrypted TokenEx cloud token vault. The pseudonymized data will likely present a lower risk, thus possibly reducing the number of additional security measures required to meet this obligation. Using a cloud-based tokenization provider like TokenEx to pseudonymize direct identifiers in the personal data your controls is a clear indication that you are considering data protection by design and striving to implement technical measures appropriate to the risk. Article 32(1) obligates controllers as well as processors to “implement appropriate technical and organizational measures to ensure a level of security appropriate to the risk,” including pseudonymization of personal data. The TokenEx platform enables you to pseudonymize personal data within your environment, replacing it with tokens, and storing the data in an encrypted TokenEx cloud token vault. The pseudonymized data will likely present a lower risk, thus possibly reducing the number of additional security measures required to meet this obligation. TokenEx: “Tokenization” GDPR Article 6(4)e): “Encryption” TokenEx: “Tokenization and Encryption” GDPR Article 25(1): “Data Protection by Design” Article 25(1): “Encryption” GDPR Article 32(1) “Pseudonymization of Personal Data” TokenEx: “Pseudonymize Personal Data” KEY ACTIVITIES TO ADDRESS GDPR Source: https://tokenex.com/gdpr
Editor's Notes
- A framework for GDPR readiness GDPR compliance is complex, because the regulation itself is complex. It outlines obligations for data holders that can affect all parts of a business, from data collection to customer communication practices. However, GDPR is also open-ended: it doesn’t tell you in detail how to meet those obligations, or that any given technological approach will suffice. That’s why IBM has developed a straightforward approach to help simplify the ways you think about conformance. The IBM GDPR framework offers an actionable five-phase approach to GDPR readiness, which recognizes that readiness is a continuum: every organization will have a unique place on the journey to readiness. In Phase 1, you assess your situation. You figure out which of the data you collect and store is covered by GDPR regulations, and then you plot a course to discover it. Phase 2 is where you design your approach. You need to come up with a solid plan for data collection, use and storage. And you need to develop an architecture and strategy that will balance risks and business objectives. Your goal in Phase 3 is to transform your practices, understanding that the data you deem valuable to your organization is equally valuable to the people it represents. This is where you need to develop a sustainable privacy compliance program, implement security and governance controls (TOMs — Technical and Organizational Measures) and potentially appoint a Data Protection Officer. By the time you get to Phase 4, you’re ready to operate your program. Now you’re continually inspecting your data, monitoring personal data access, testing your security, using privacy and security by design principles and purging unneeded data. And Phase 5 — the final phase — is where you’re ready to conform with the necessary GDPR requirements. Now you’re fulfilling data subject requests for access, correction, erasure and transfer. You’re also prepared for audits with documentation of your activities and ready to inform regulators and data subjects in the event of a data breach.
- De-identification or Anonymization can be a cost effective approach to protect data
- Tokenization not just for PCI. Use Case: Protect PII Data Cross Border. Achieve Compliance while moving, outsourcing, data, EVEN between countries. Data residency issue solved. Example: A major bank performed a consolidation of all European operational data sources. This meant protecting Personally Identifiable Information (PII) in compliance with the EU Cross Border Data Protection Laws. In addition, they required access to Austrian and German customer data to be restricted to only people in each respective country. CHALLENGES The primary challenge was to protect PII – names and addresses, phone and email, policy and account numbers, birth dates, etc. – to the satisfaction of EU Cross Border Data Security requirements. This included incoming source data from various European banking entities, and existing data within those systems, which would be consolidated at the Italian HQ. RESULT Complete policy-enforced de-identification of sensitive data across all bank entities End-to-end data protection from geographically distributed bank entities to HQ All existing data secured at a granular level Achieved targeted compliance with EU Cross Border Data Security laws, Datenschutzgesetz 2000 - DSG 2000 in Austria, and Bundesdatenschutzgesetz in Germany Implemented country-specific data access restrictions Extremely high throughput of data Source
- X9 defines new standard for encryption of financial services data 09 May 2018 | 2189 views | 0Source: X9Today the Accredited Standards Committee X9 Inc. (X9) announced the publication of a new standard that defines requirements for using a particular method of preserving formatting in the encryption of financial services data. The standard, X9.124-2 Symmetric Key Cryptography For the Financial Services Industry -- Format Preserving Encryption - Part 2: Key Stream with Counter Mode, is now available for purchase from the ANSI Store. The X9.124 standard defines a collection of format-preserving encryption methods for financial services. Format-preserving encryption (FPE) is useful in situations where fixed-format data, such as primary account numbers or Social Security numbers, must be encrypted, but there is a requirement to limit changes to existing communication protocols, database schemata or application code. Encryption has historically been an expensive technique to deploy in real-world systems because of the need to alter the operation of existing systems and applications. The benefit of FPE techniques is that encryption can be added to existing systems in such a way that system modifications are kept to a minimum. Often, substantial savings can be realized because database schemas and financial applications can run with encrypted data without needing modification or replacement. X9.124-2 defines requirements for using a particular approach - Key Stream with Counter Mode -- to specify a set of algorithms that securely encrypts formatted data and retains that format in the resulting ciphertext. Format-preserving encryption Counter Mode is a particularly simple and efficient mechanism for maintaining data format while also safeguarding its security. IT equipment vendors, banks, and retailers are some of the sectors that will benefit from X9.124-2. "This new standard describes a straightforward method of preserving the format of important data while ensuring its security, leading to cost efficiencies in systems and processing throughout the industry," said ASC X9 Executive Director Steve Stevens. "The new format-preserving encryption standard offers an additional encryption method to security professionals in search of a solution to efficiently protect data and privacy in a digital world," said Eric Le Saint, distinguished engineer, Visa, and chairman, X9F1 Working Group. "The development of the new standard is the result of hard work by many dedicated contributors from the X9F1 working group, to whom we are grateful."
- ISO 27001 and the GDPR - IT Governance Source: itgovernance.co.uk/gdpr-and-iso-27001
- A framework for GDPR readiness GDPR compliance is complex, because the regulation itself is complex. It outlines obligations for data holders that can affect all parts of a business, from data collection to customer communication practices. However, GDPR is also open-ended: it doesn’t tell you in detail how to meet those obligations, or that any given technological approach will suffice. That’s why IBM has developed a straightforward approach to help simplify the ways you think about conformance. The IBM GDPR framework offers an actionable five-phase approach to GDPR readiness, which recognizes that readiness is a continuum: every organization will have a unique place on the journey to readiness. In Phase 1, you assess your situation. You figure out which of the data you collect and store is covered by GDPR regulations, and then you plot a course to discover it. Phase 2 is where you design your approach. You need to come up with a solid plan for data collection, use and storage. And you need to develop an architecture and strategy that will balance risks and business objectives. Your goal in Phase 3 is to transform your practices, understanding that the data you deem valuable to your organization is equally valuable to the people it represents. This is where you need to develop a sustainable privacy compliance program, implement security and governance controls (TOMs — Technical and Organizational Measures) and potentially appoint a Data Protection Officer. By the time you get to Phase 4, you’re ready to operate your program. Now you’re continually inspecting your data, monitoring personal data access, testing your security, using privacy and security by design principles and purging unneeded data. And Phase 5 — the final phase — is where you’re ready to conform with the necessary GDPR requirements. Now you’re fulfilling data subject requests for access, correction, erasure and transfer. You’re also prepared for audits with documentation of your activities and ready to inform regulators and data subjects in the event of a data breach.
