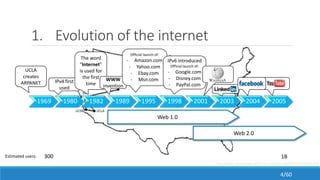
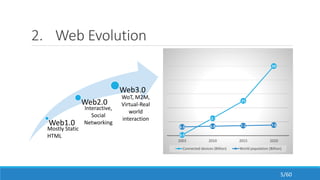
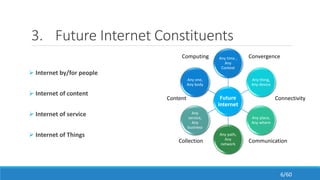
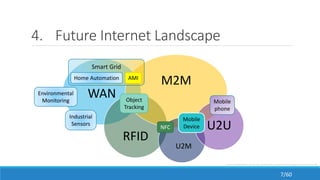
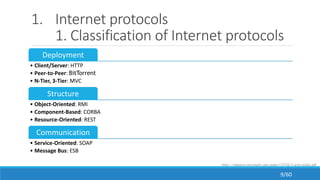
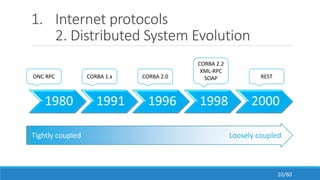
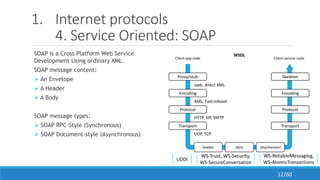
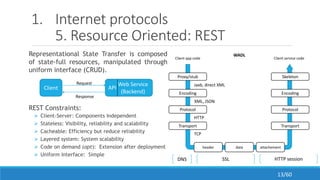
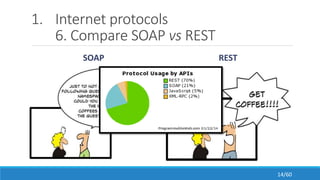
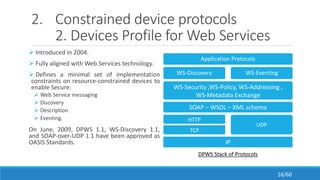
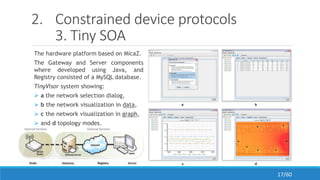
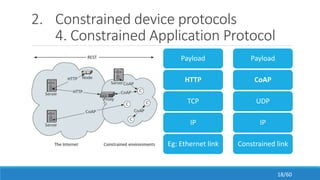
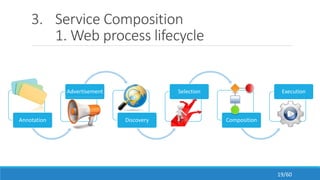
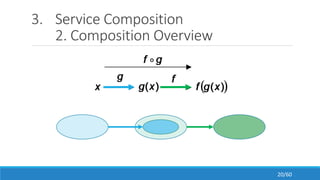
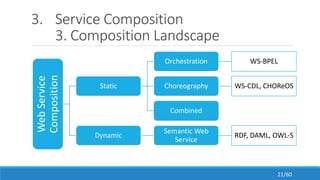
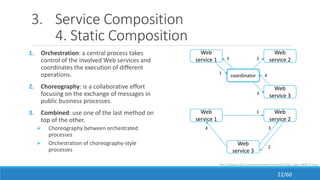
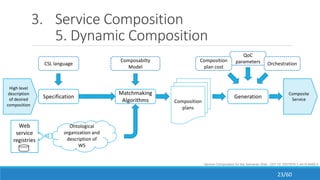
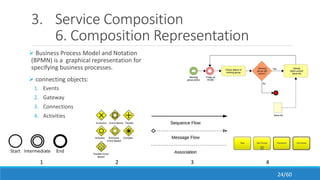
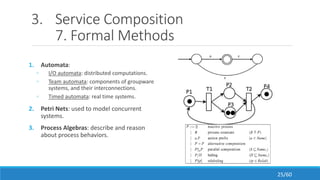
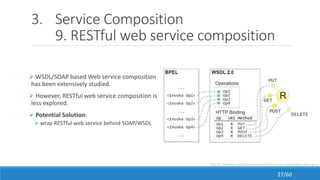
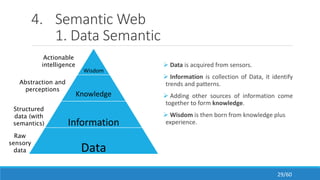
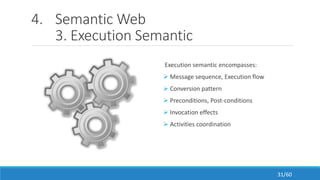
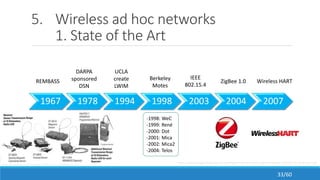
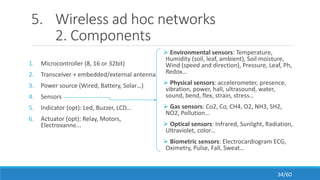
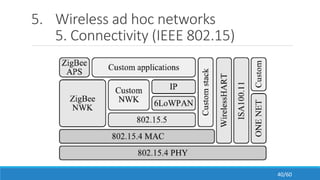
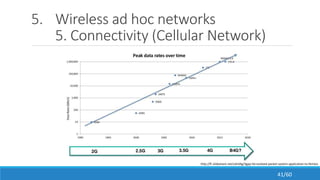
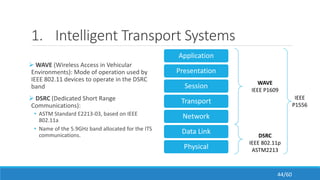
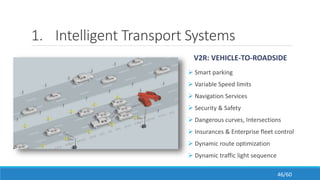
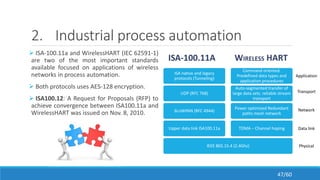
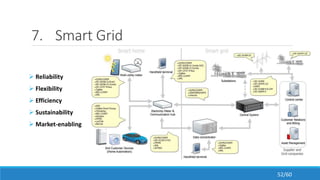
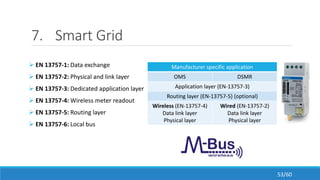
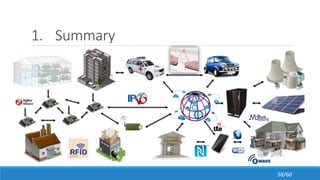
The document discusses the evolution, technologies, applications, and challenges of the future internet, highlighting the transition from Web 1.0 to Web 3.0 along with various internet protocols like SOAP and REST. It examines components like the Internet of Things and service compositions, alongside applications across sectors such as intelligent transport systems and healthcare. Challenges in the future internet are also outlined, including the integration of diverse technologies and ensuring secure and efficient connectivity.