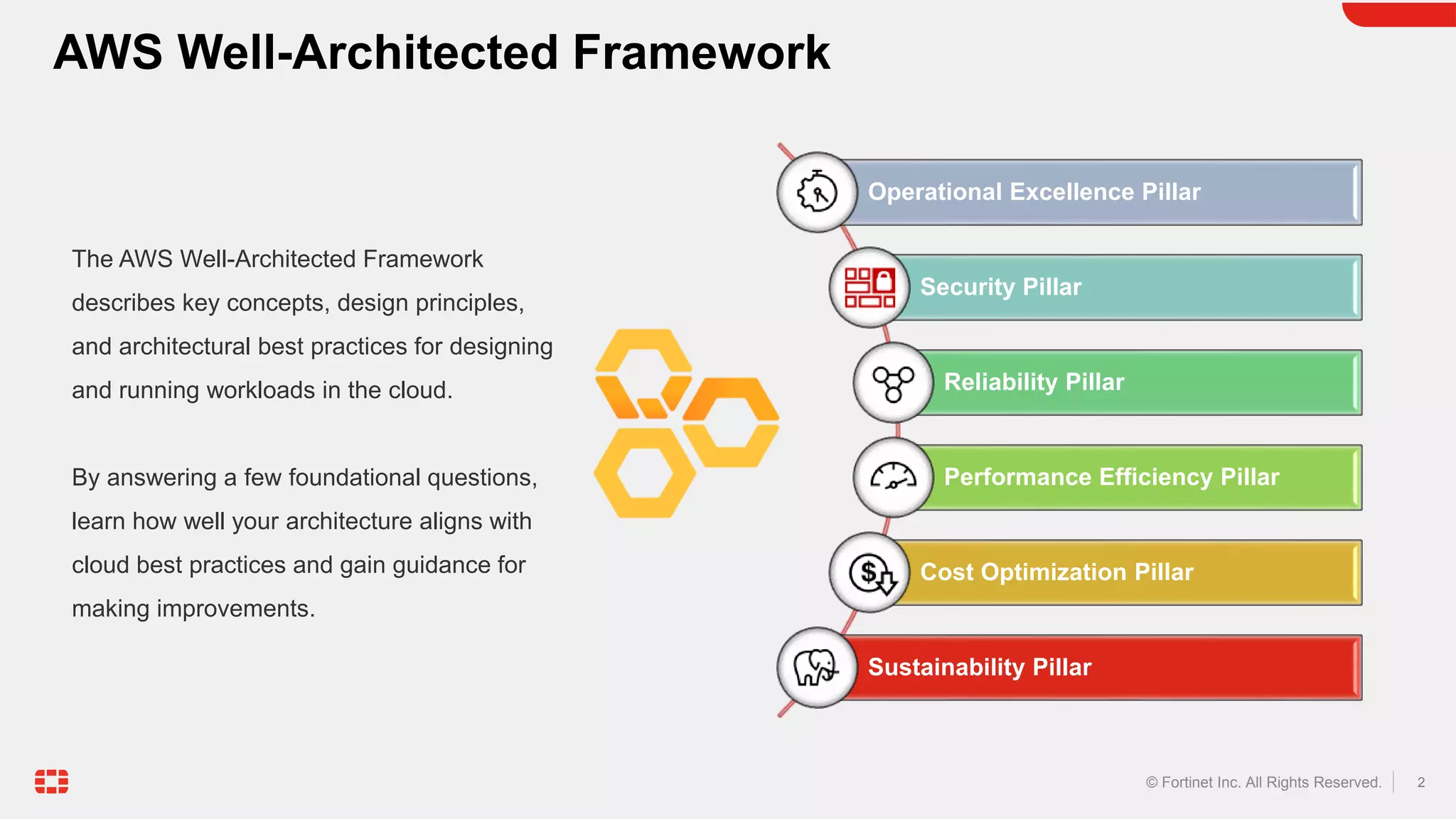
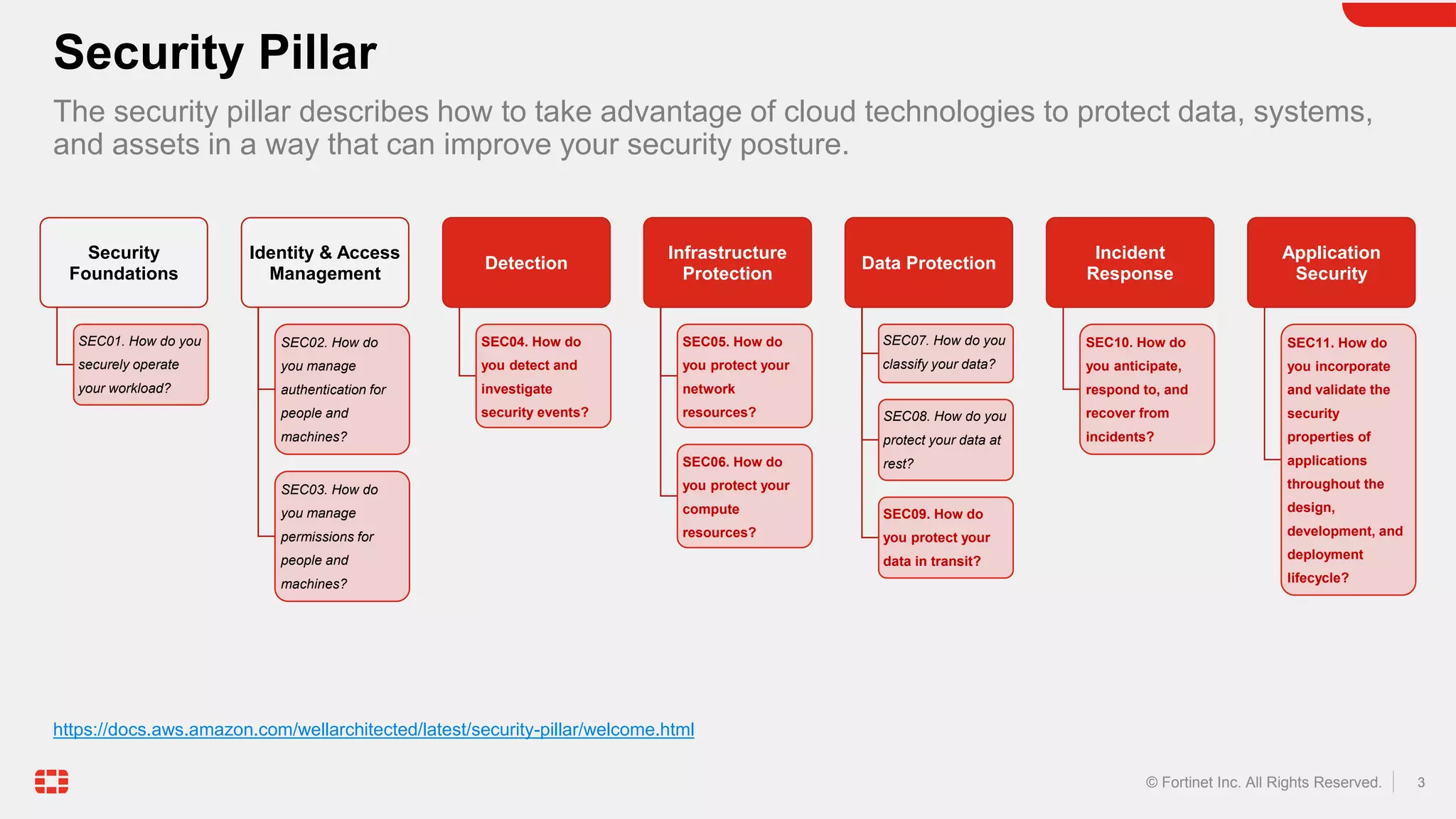
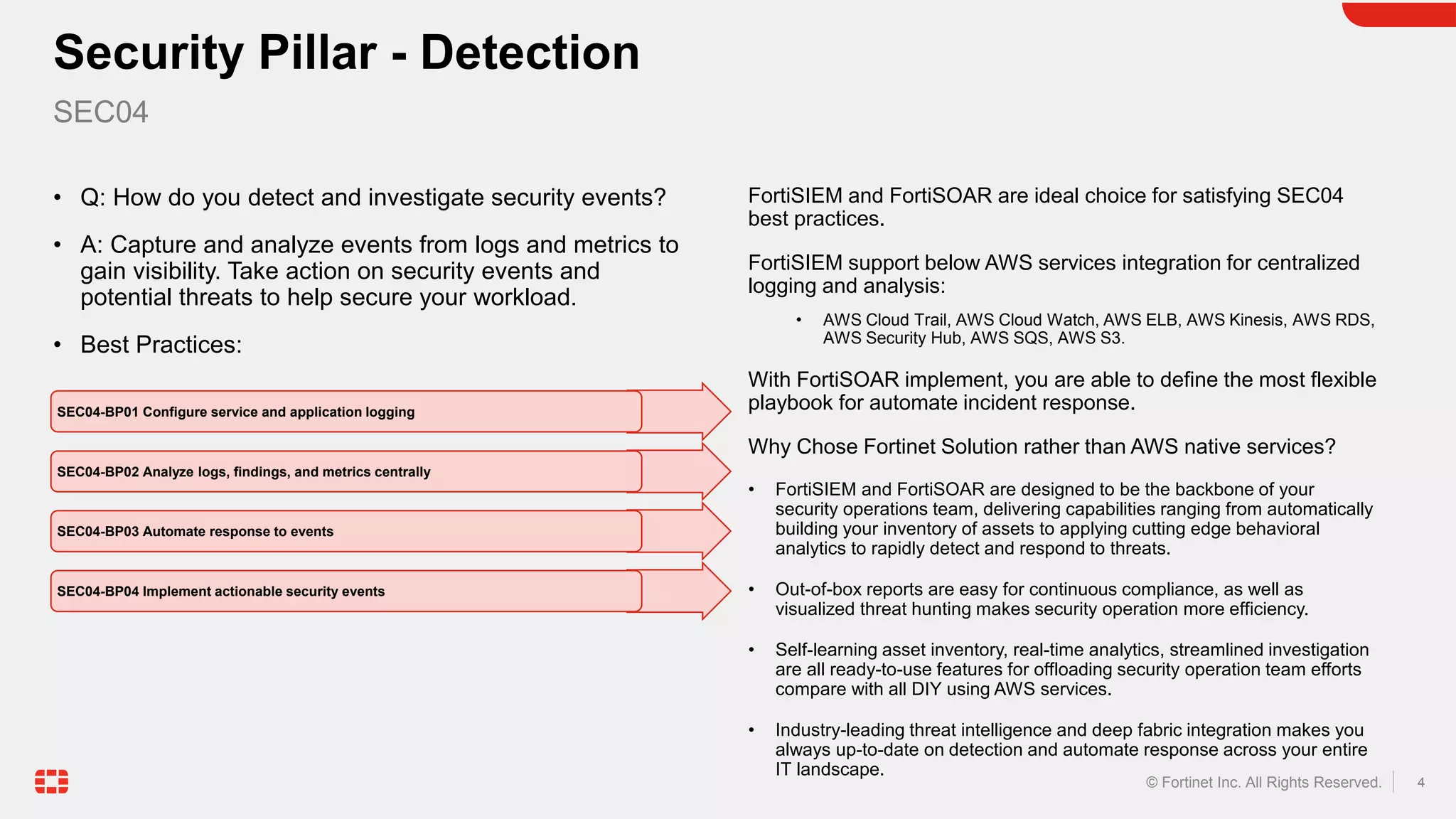
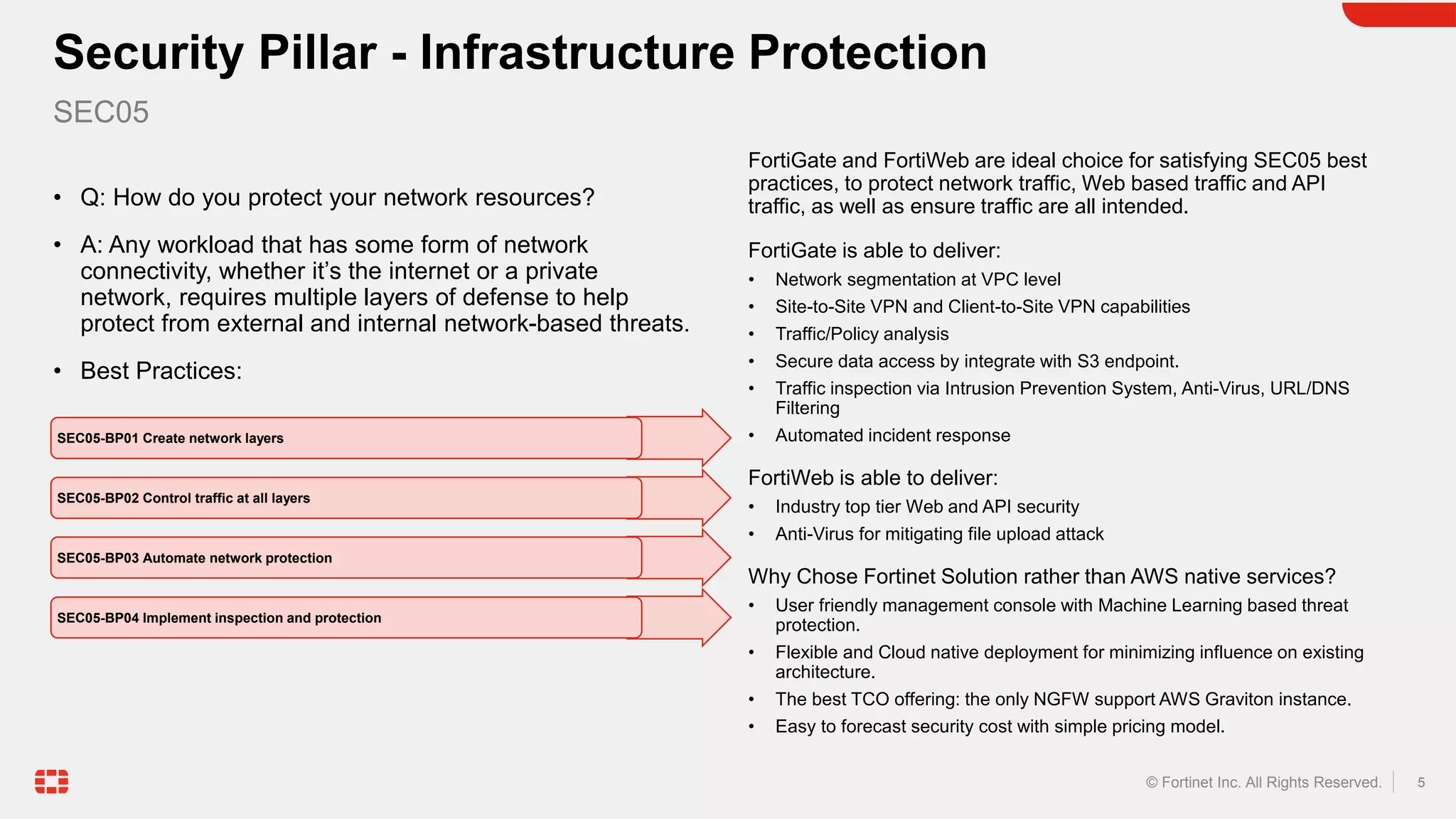
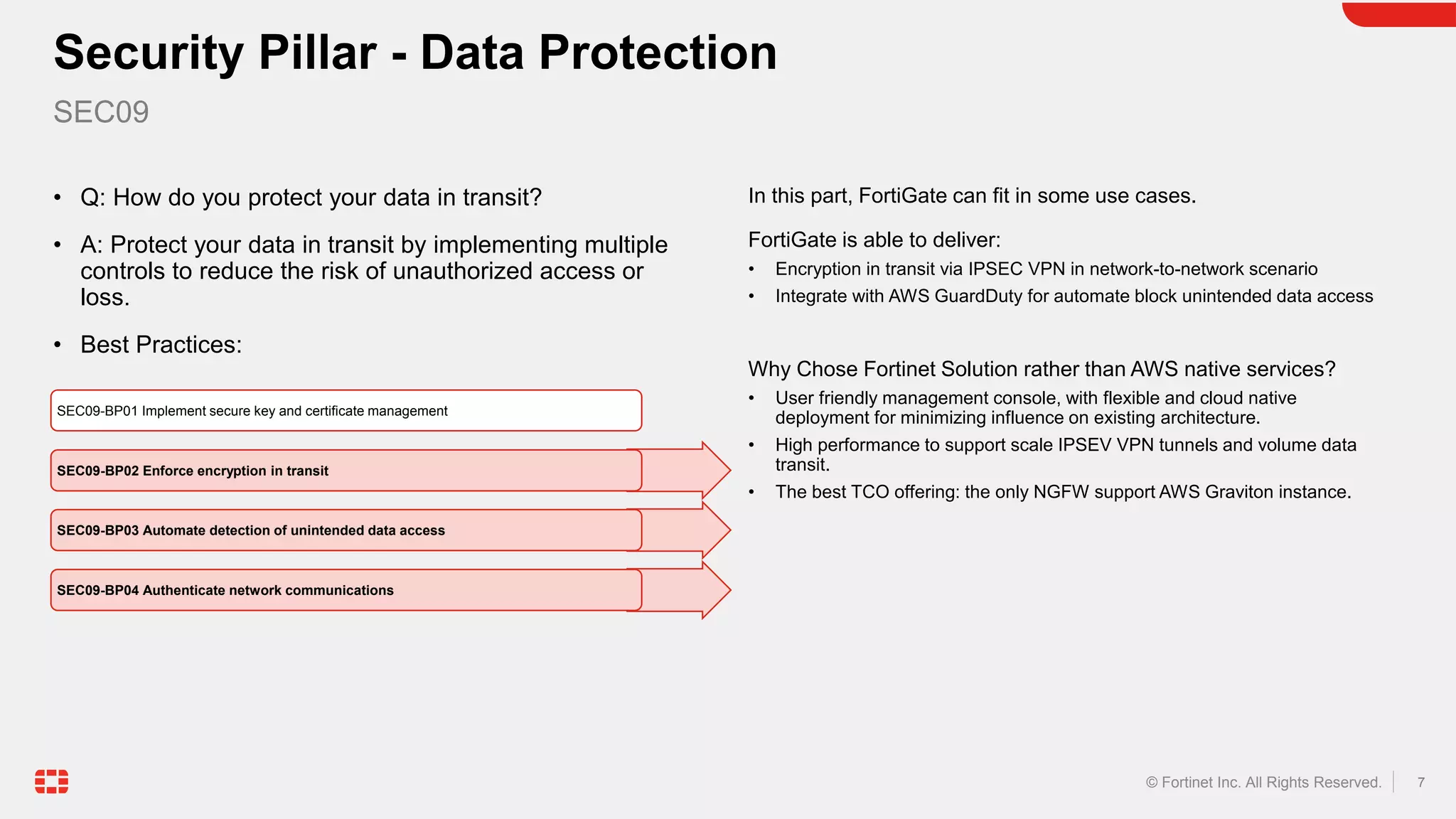
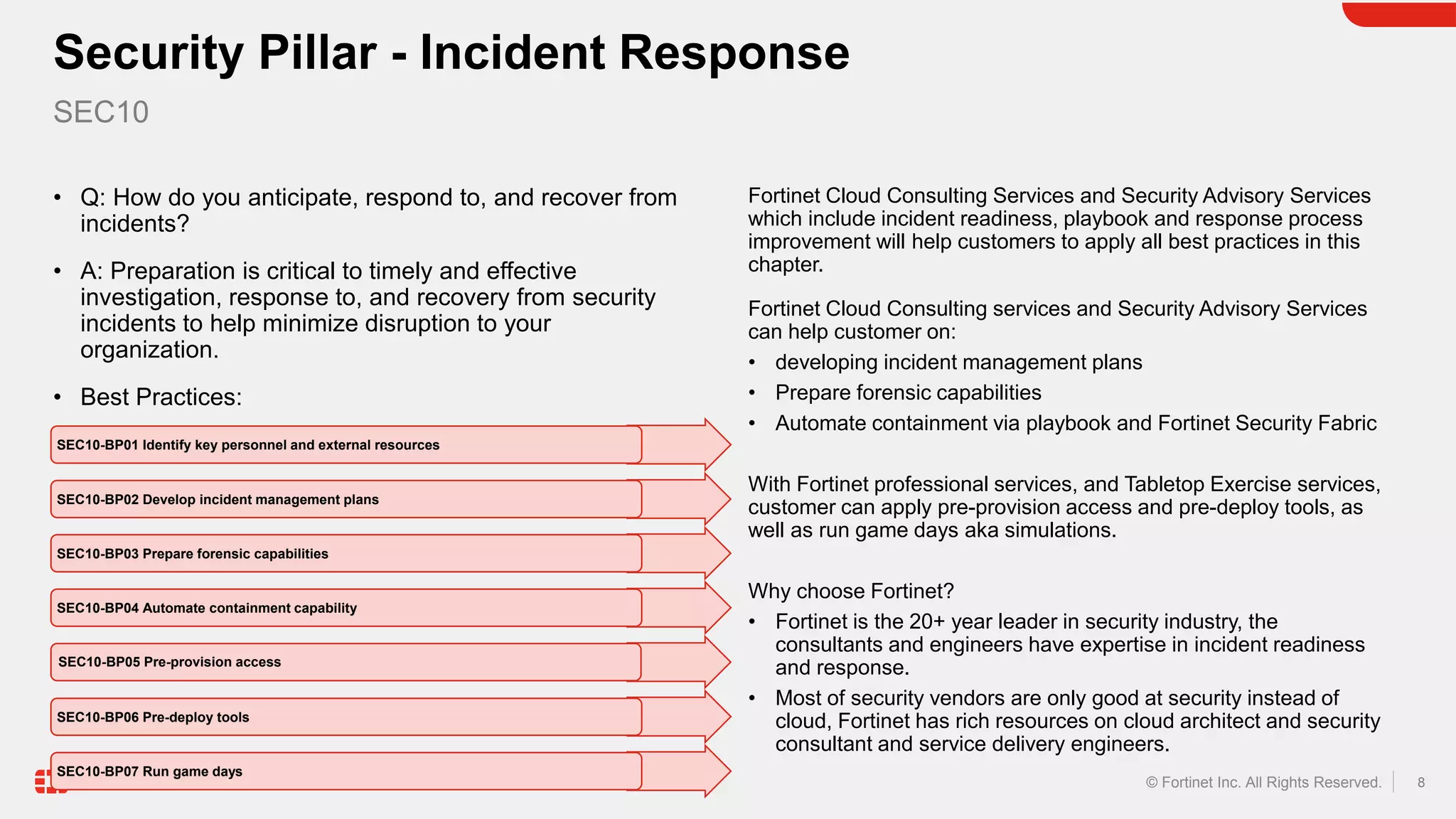
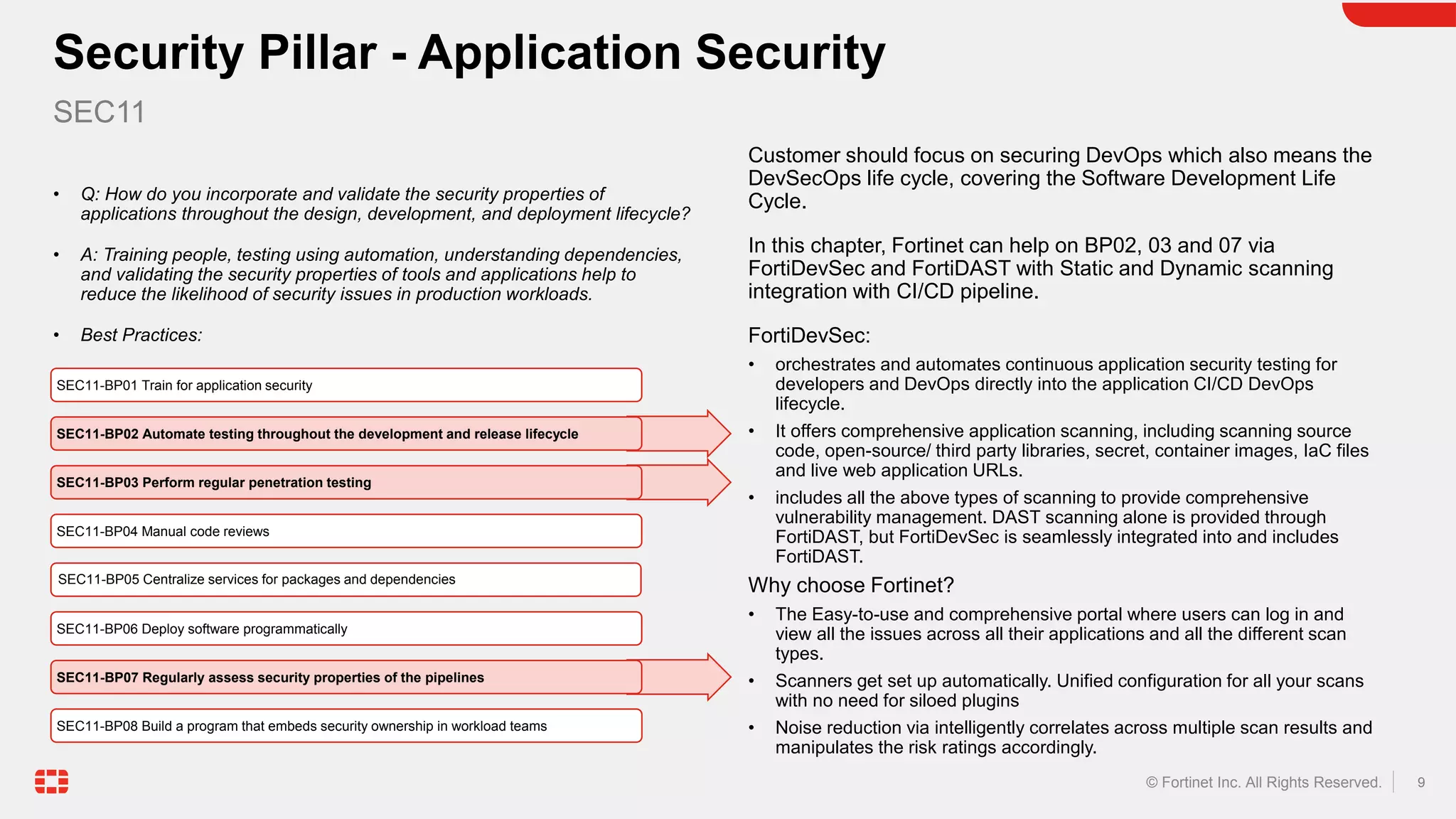
The document discusses the AWS Well-Architected Framework and how it describes best practices for designing workloads in the cloud across various pillars including security. It then provides answers to several questions relating to implementing security best practices for detecting and investigating security events, protecting network resources, protecting compute resources, protecting data in transit, anticipating and responding to security incidents, and incorporating security in the application development lifecycle. For each question, it recommends relevant Fortinet security solutions that align with AWS security best practices and provides reasons for choosing Fortinet over native AWS services.