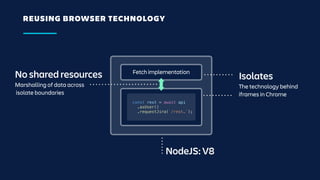
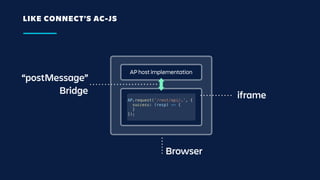
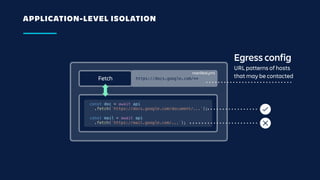
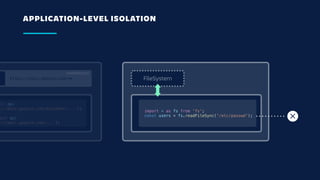
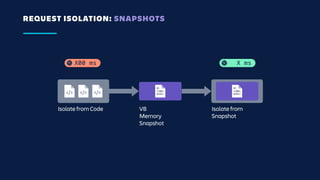
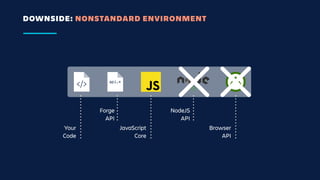
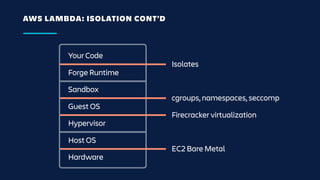
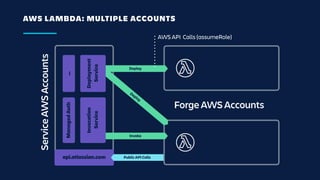
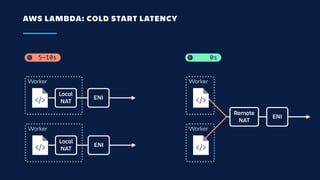
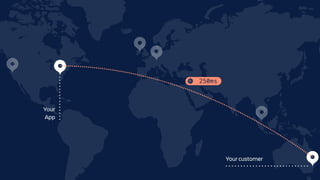
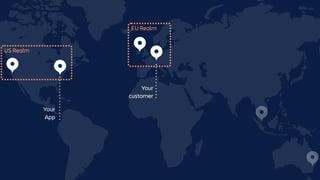
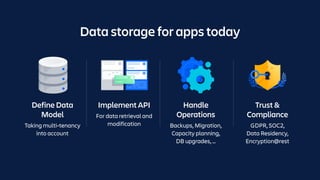
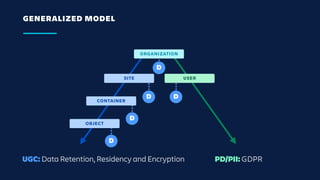
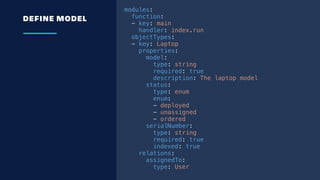
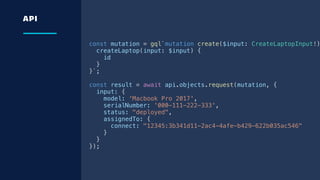
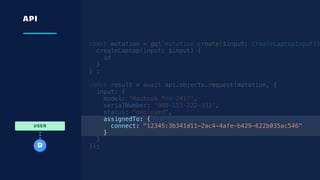
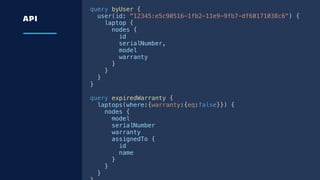
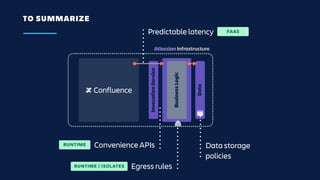
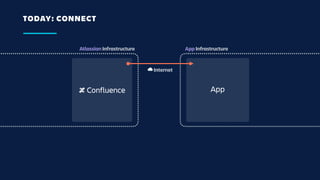
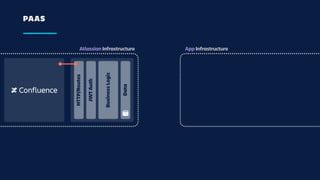
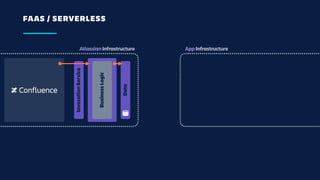
The document details an overview of Atlassian's managed authentication and isolation model using AWS Lambda, highlighting security enhancements and user experience improvements. It outlines key components such as data management, runtime isolation, and the infrastructure for app development, while ensuring compliance with standards like GDPR. The document also discusses practical implementation scenarios and the benefits of reduced latency and predictable behavior for users.


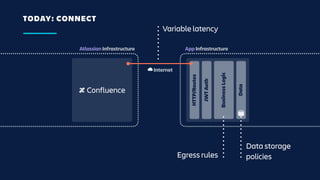
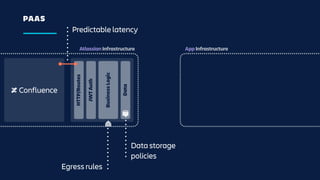
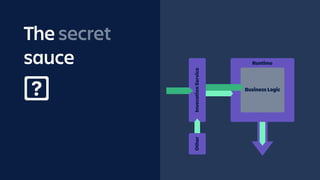




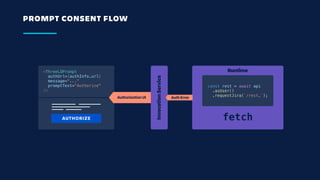
![UNDER THE HOOD
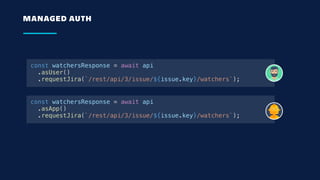
const rest = await api
.asUser()
.requestJira(`/rest…`);
Runtime
InvocationService
{
"issue": {
"key": "ATL-2019"
},
"context": {
"cloudId": "1a5dab50-7544-…f310",
"accountId": "12345:3b341d…c546"
}
}
Managed
Auth
{
"tokens": [
{
"accountId": "12345:3b341d…c546",
"token": "<secret>",
"service": "api.atlassian.com"
}
]
}
fetch
GET https://api.atlassian.com
/ex/jira/{cloudId}/rest/api/3/..
Authorization: Bearer {token}](https://image.slidesharecdn.com/1650-1730forgestreule-191030004437/85/Forge-Under-the-Hood-14-320.jpg)
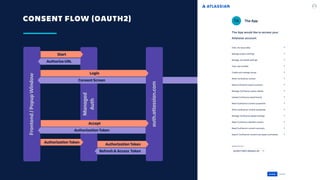
![AFTER CONSENT FLOW
const rest = await api
.asUser()
.requestJira(`/rest…`);
Runtime
InvocationService
{
"issue": {
"key": "ATL-2019"
},
"context": {
"cloudId": "1a5dab50-7544-…f310",
"accountId": "12345:3b341d…c546"
}
}
Managed
Auth
{
"tokens": [
{
"accountId": "12345:3b341d…c546",
"token": "<access token>",
"service": "api.atlassian.com"
}
]
}
fetch
GET https://api.atlassian.com
/ex/jira/{cloudId}/rest/api/3/..
Authorization: Bearer {token}](https://image.slidesharecdn.com/1650-1730forgestreule-191030004437/85/Forge-Under-the-Hood-17-320.jpg)