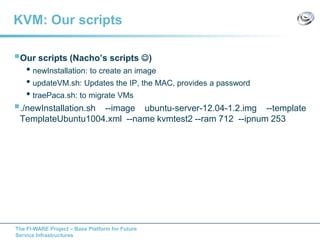
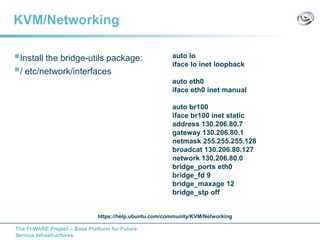
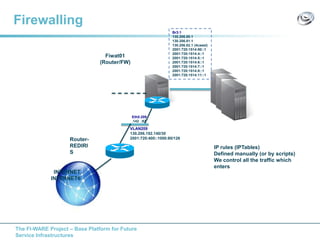
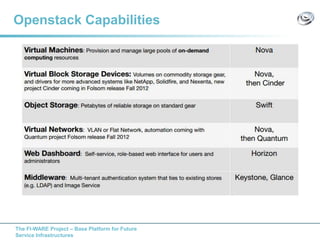
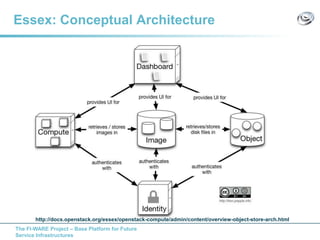
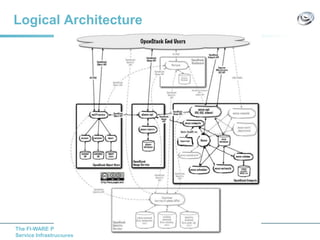
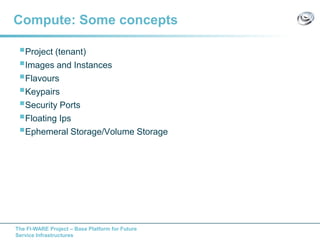
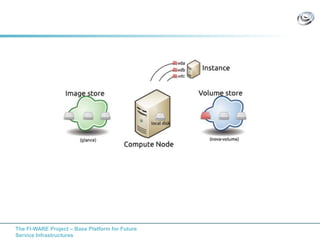
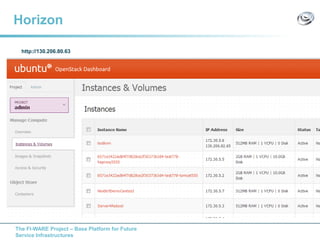
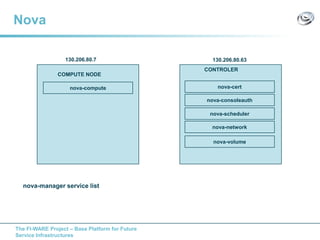
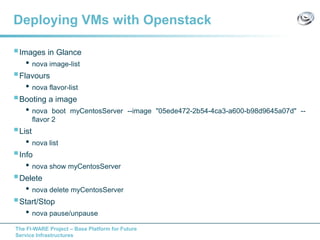
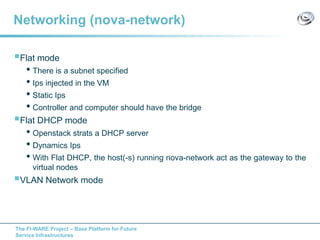
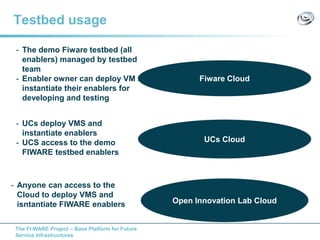
The document discusses setting up a FIWARE testbed using OpenStack for infrastructure as a service (IaaS). It describes installing OpenStack components like Nova, Glance, Horizon on servers to deploy virtual machines from images and manage them. Key OpenStack concepts are explained like projects, flavors, images, networking. Steps are provided to launch VMs, assign IPs, security groups. Future plans include adding more FIWARE components and improving the OpenStack installation. The testbed is intended for FIWARE enablers, UCs and open innovation projects to instantiate and test enablers in a cloud environment.