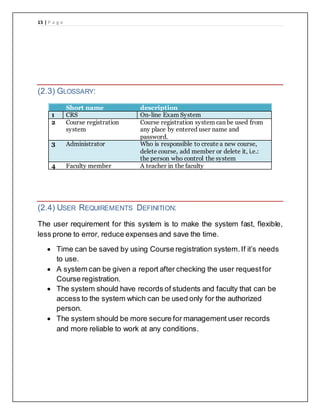
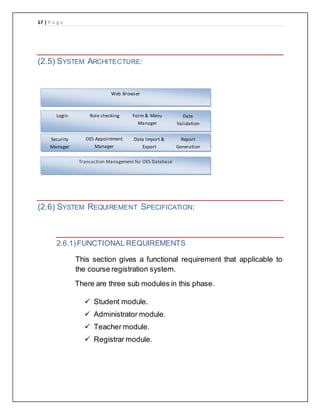
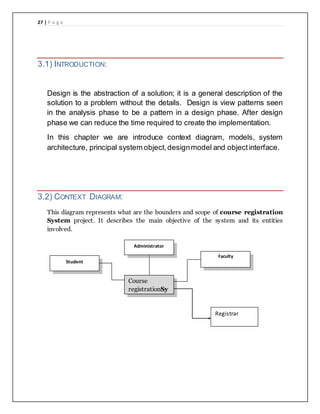
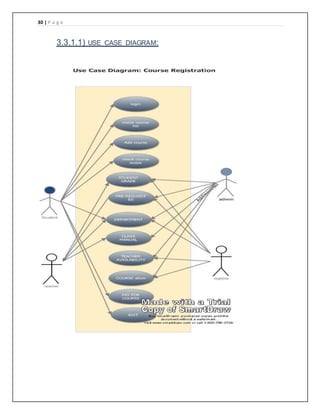
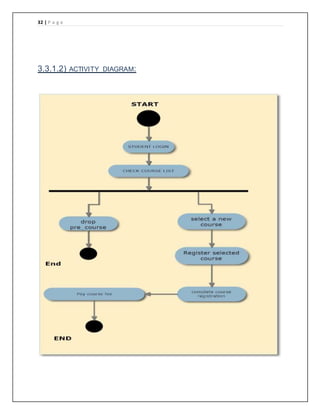
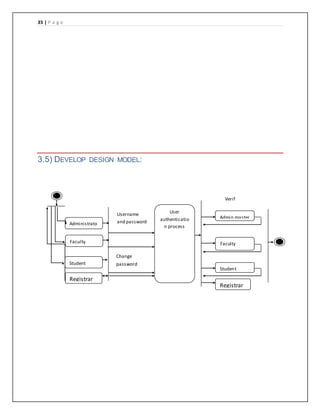
The document provides details of a course registration system project for a university. It includes a project plan with objectives to create an online system to replace the manual paper-based registration currently used. It outlines requirements for the system including functional requirements for student, administrator, teacher and registrar modules. Non-functional requirements around performance, safety and security are also specified. The project will follow a waterfall model for development.