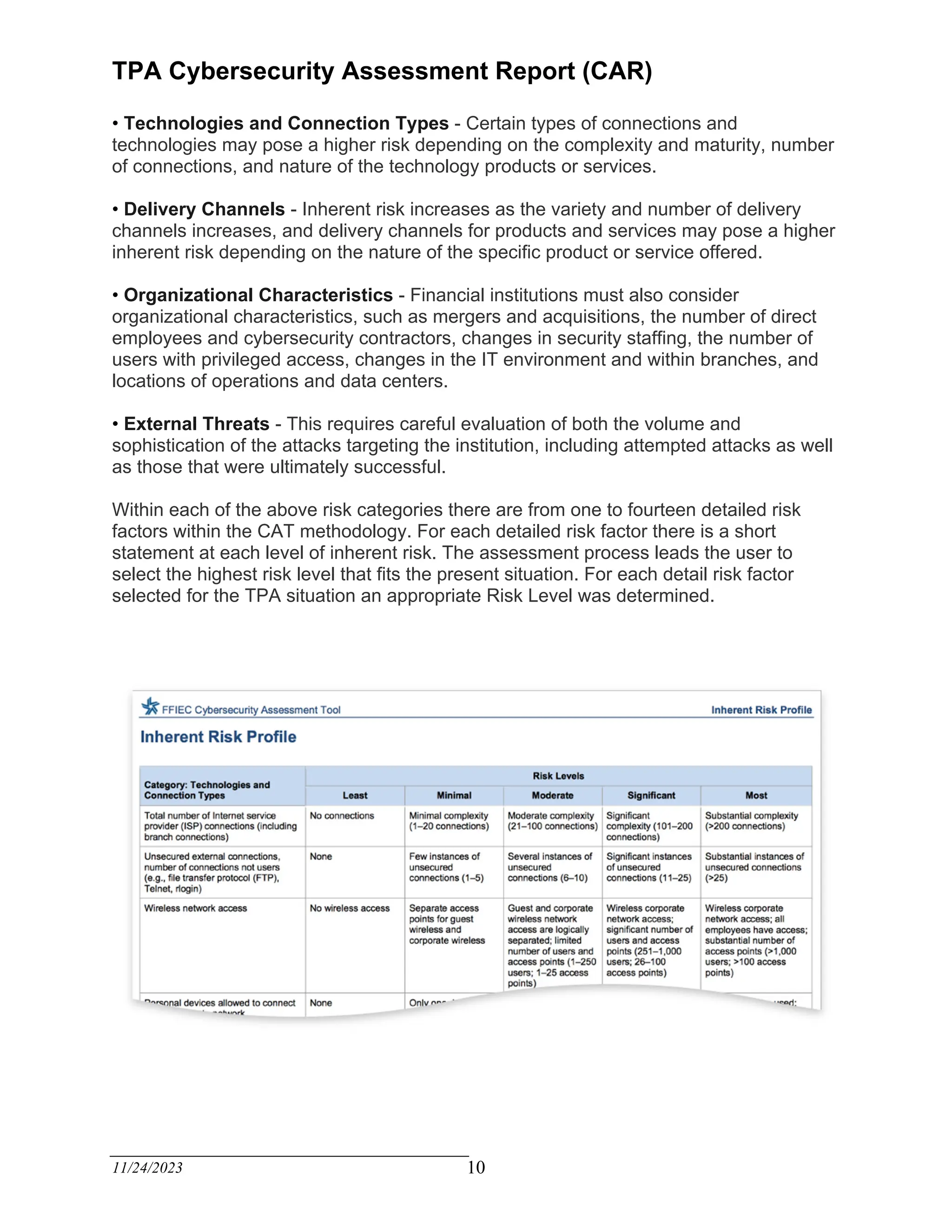
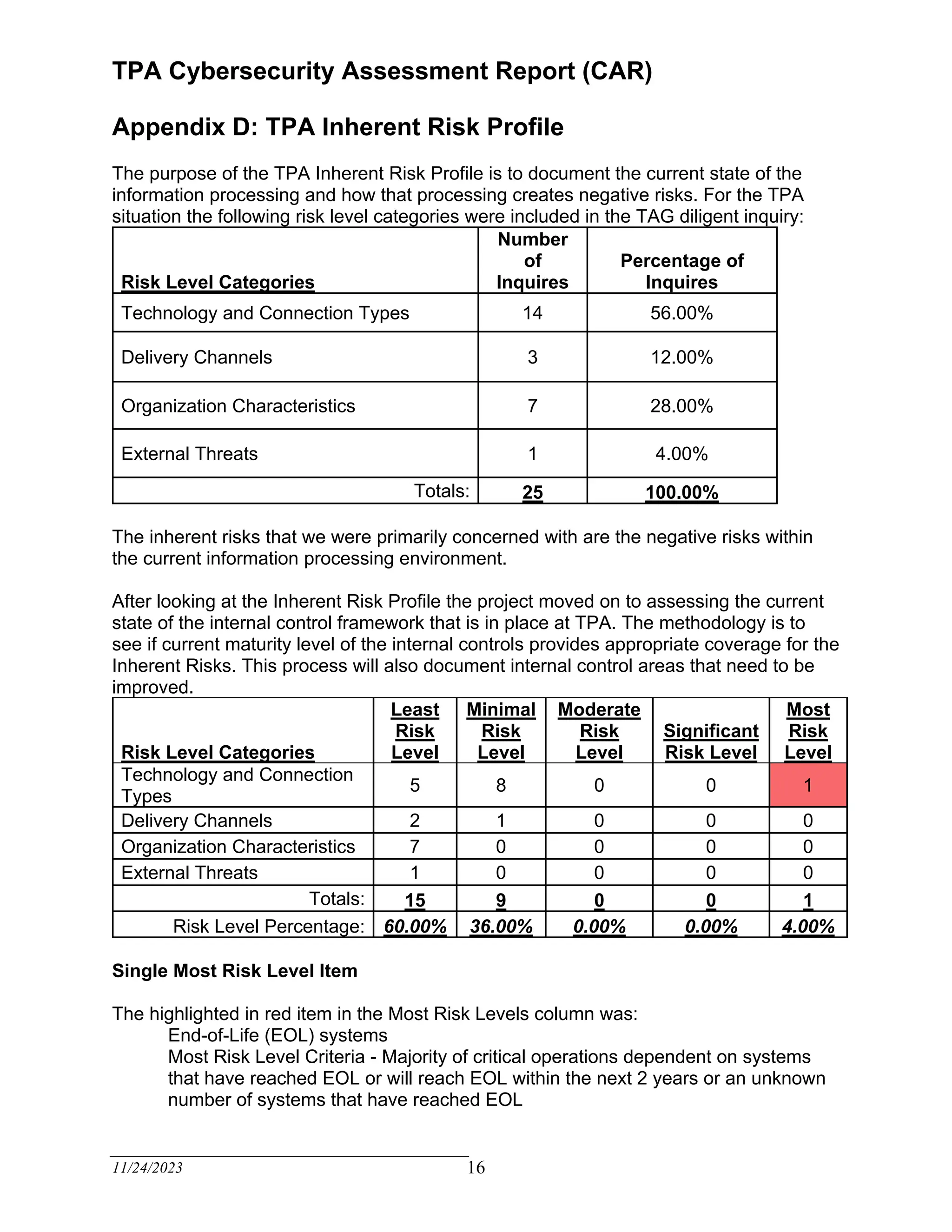
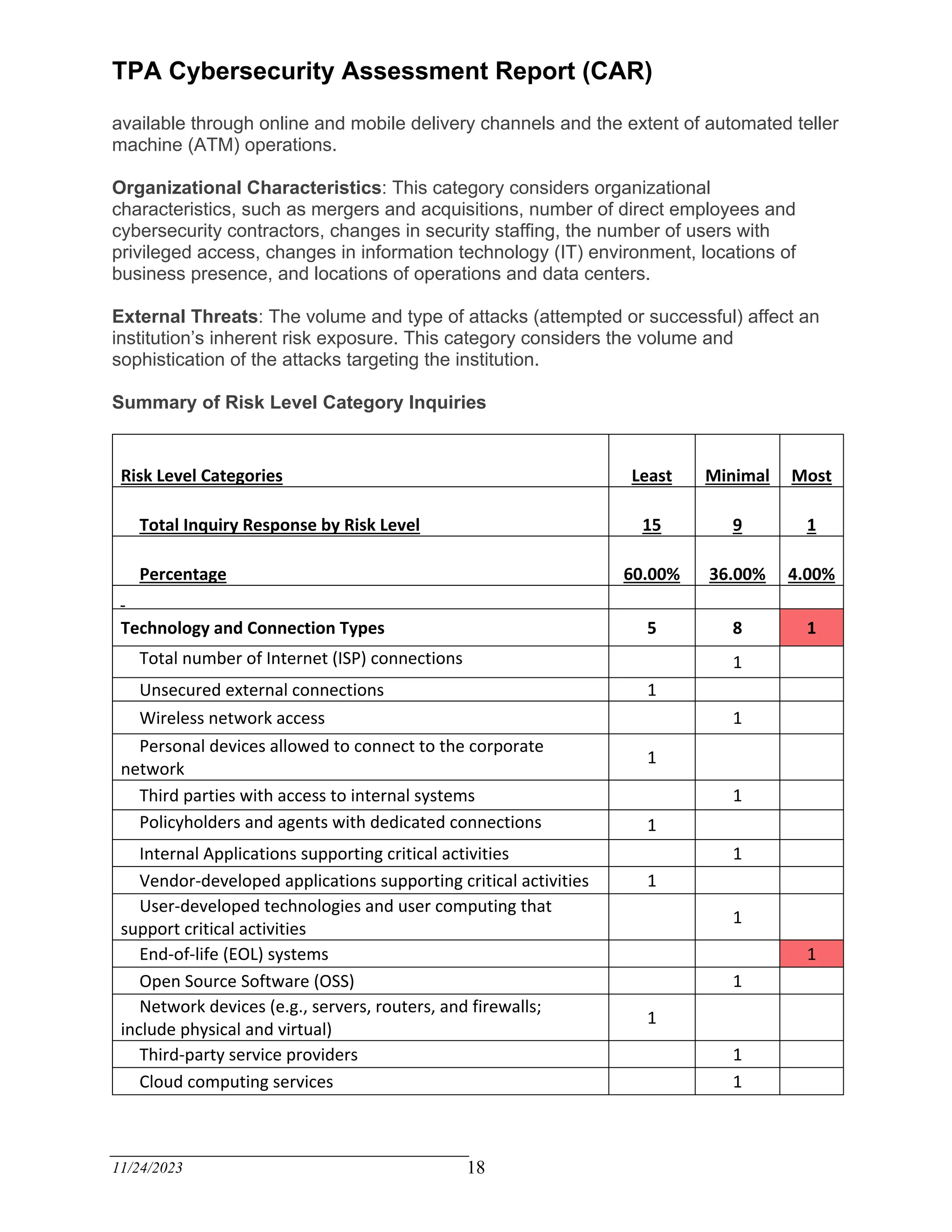
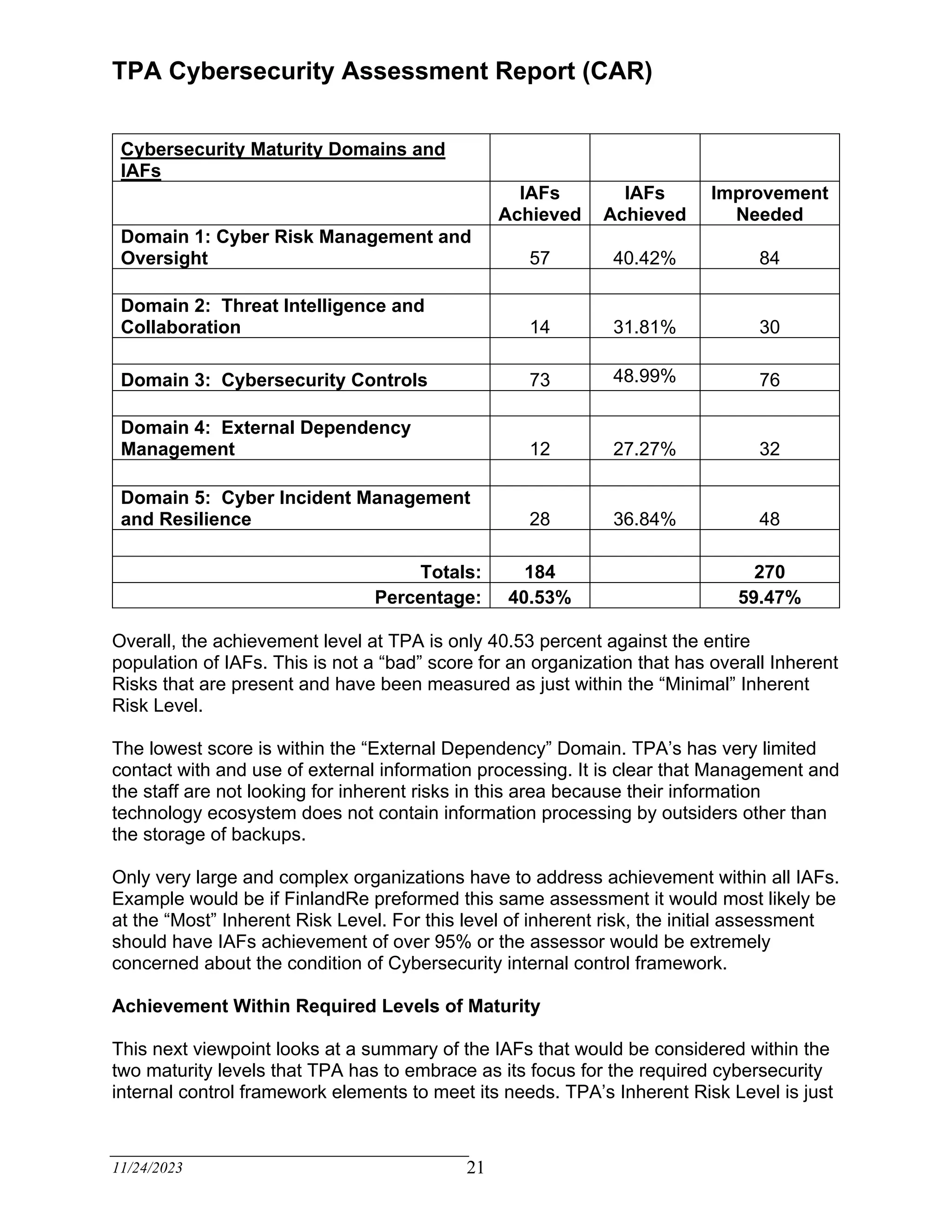
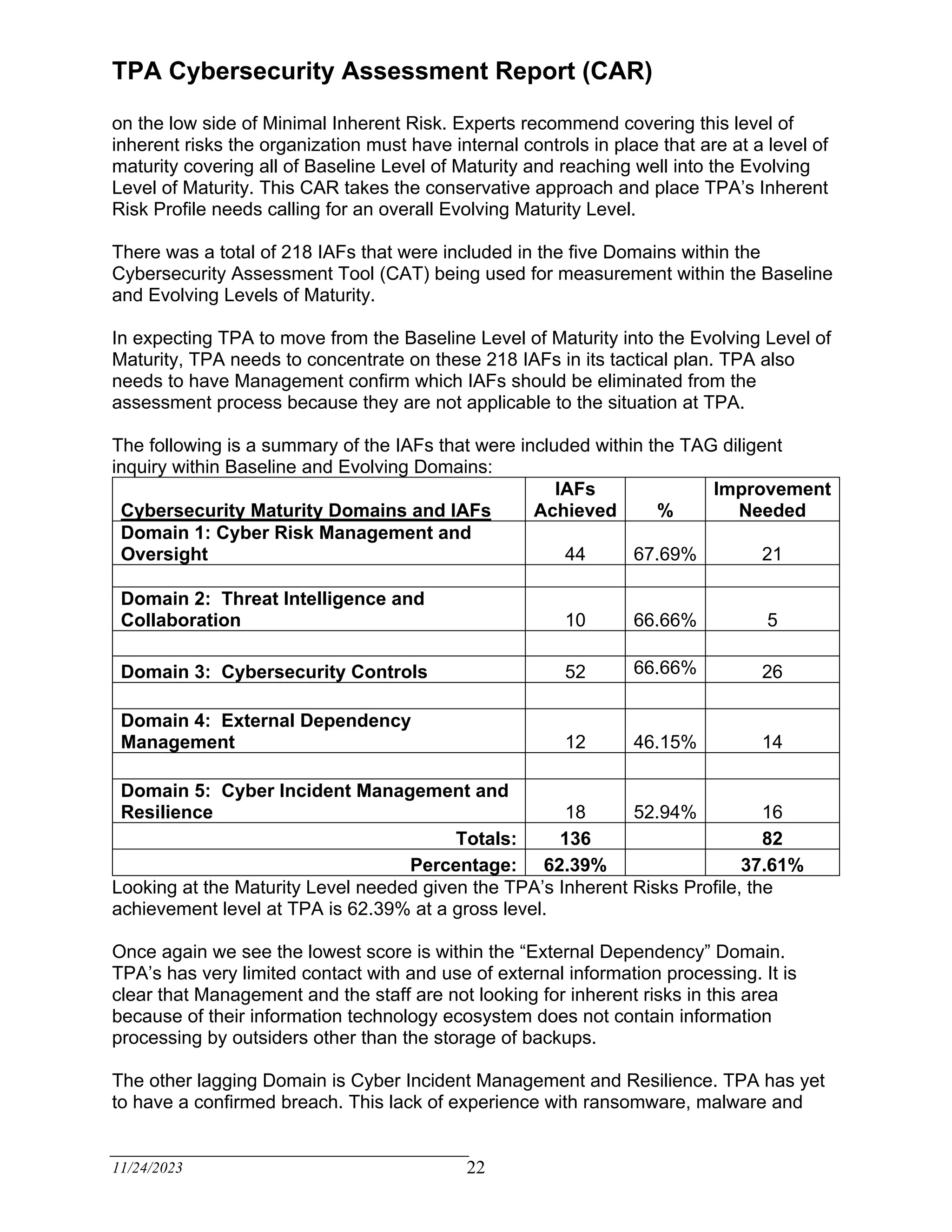
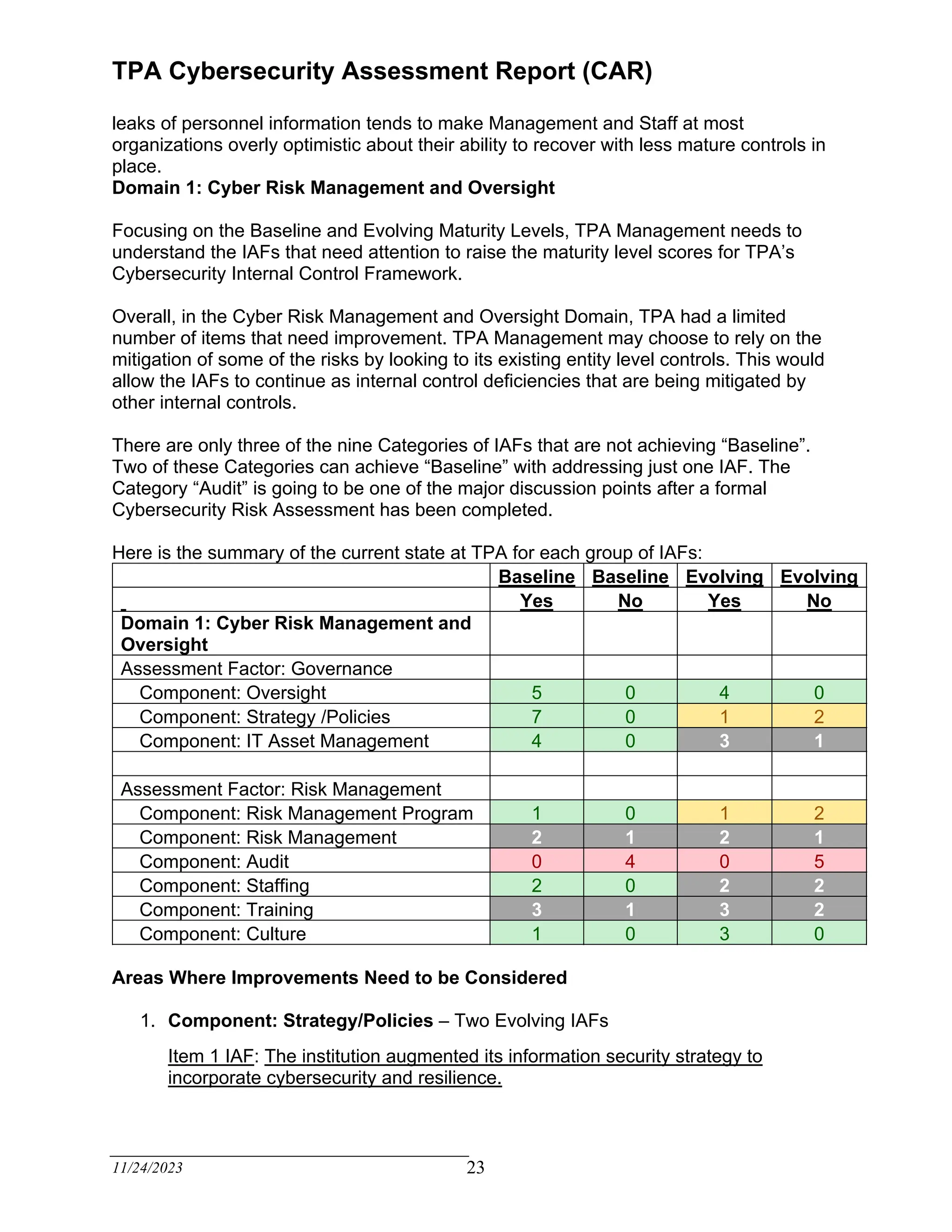
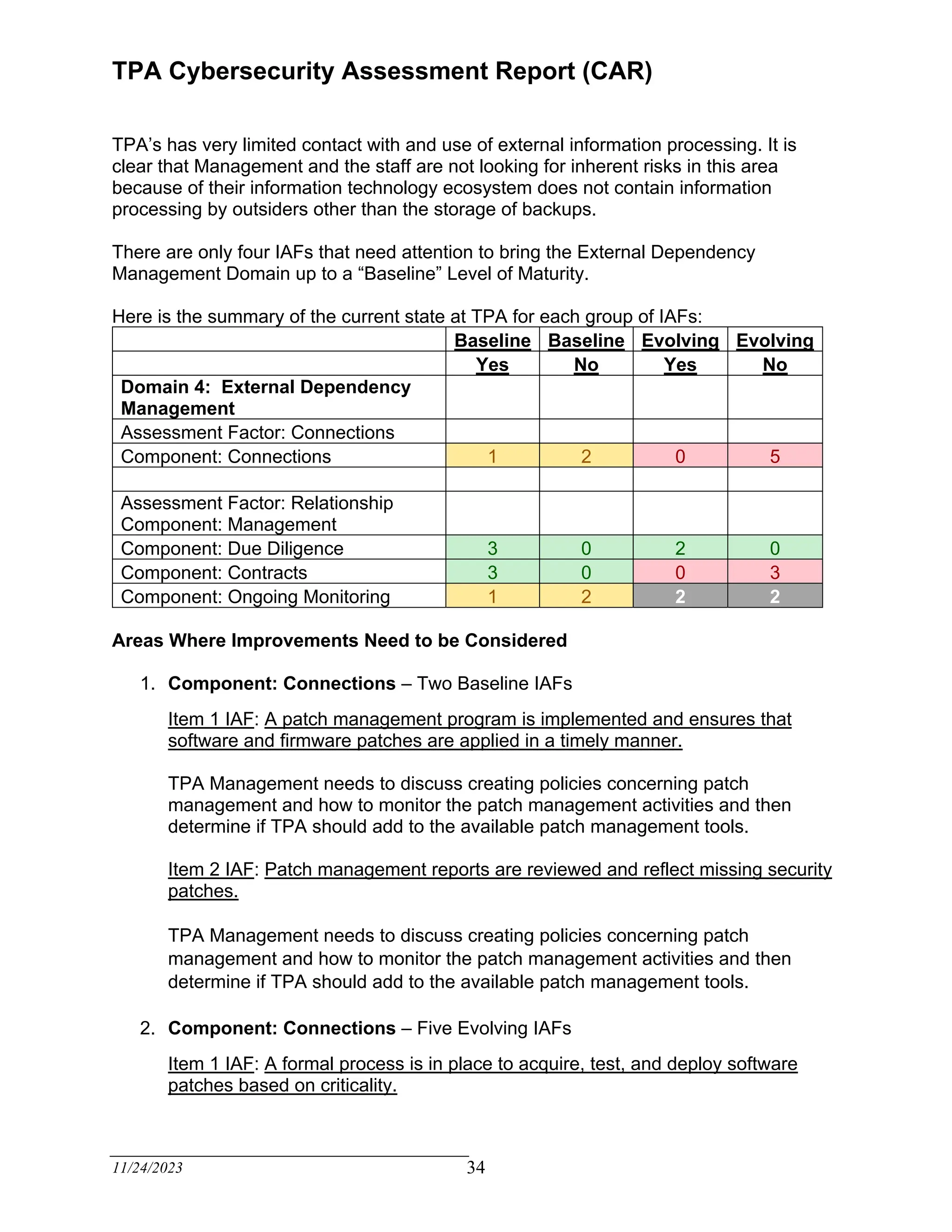
The TPA Cybersecurity Assessment Report evaluates the current cybersecurity internal controls of a third-party administrator based on recognized criteria derived from the FFIEC Cybersecurity Assessment Tool. The assessment identifies areas for improvement, emphasizing the need for a written cybersecurity risk management program and effective risk assessment focused on claimant data. Management is encouraged to enhance the maturity of internal controls to achieve compliance and mitigate inherent risks over the next eighteen months.