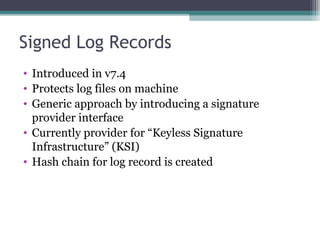
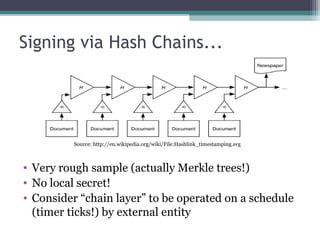
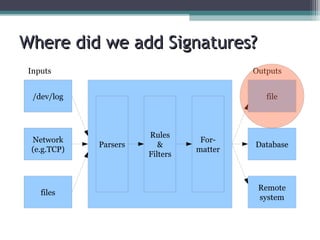
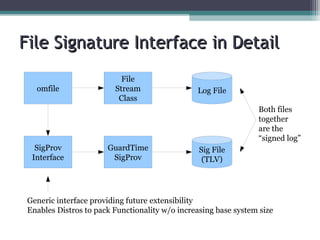
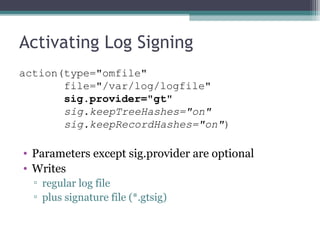
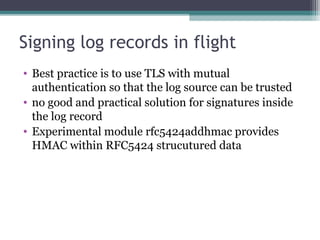
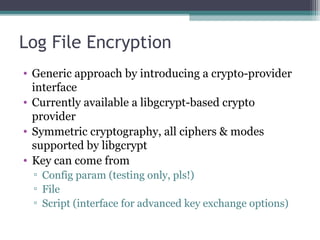
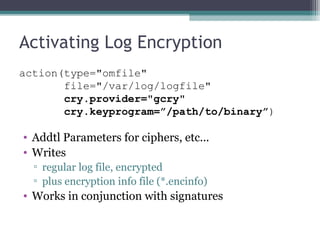
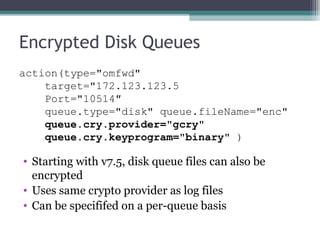
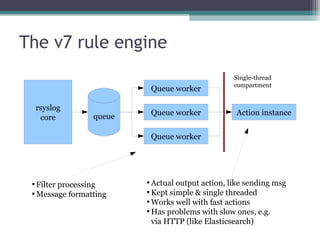
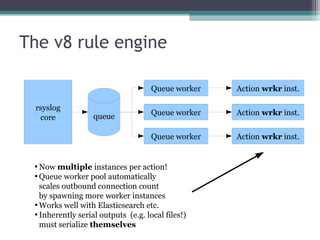
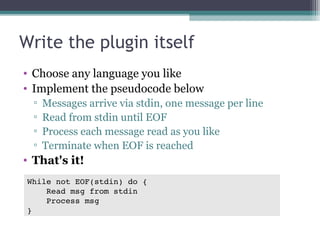
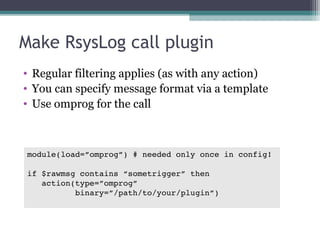
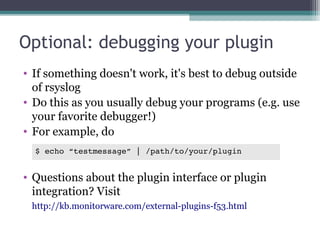
The document discusses the features and improvements introduced in rsyslog versions 7 and 8, focusing on security enhancements such as TLS encryption and log signing, as well as new integration options with system journals. It highlights the ability to write plugins in various programming languages and provides an overview of how to implement external output plugins. The document also mentions the upcoming features, improvements in the v8 engine, and how to engage with the rsyslog documentation project.