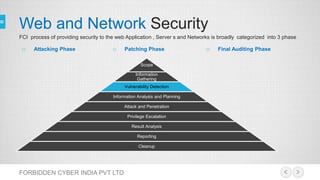
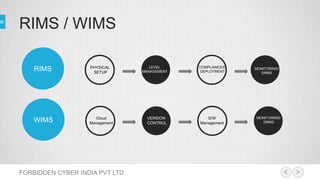
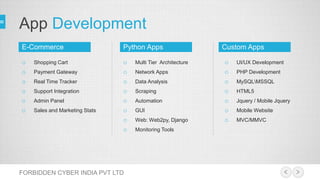
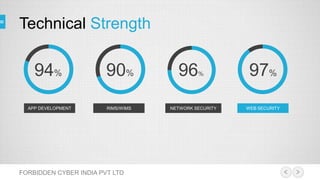
Forbidden Cyber India Pvt Ltd specializes in providing vulnerability assessment, penetration testing services and IT security audits. They provide security for web applications and networks by testing for loopholes, vulnerabilities, and the possibility of external attacks. The company focuses on delivering efficient and effective risk management through knowledge and protection against attacks.