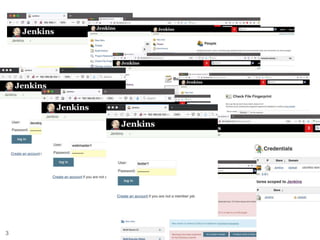
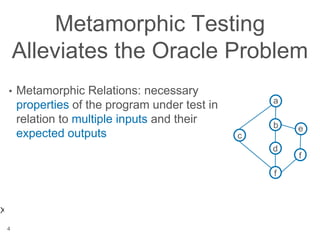
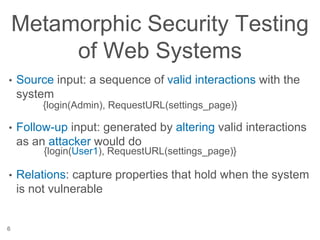
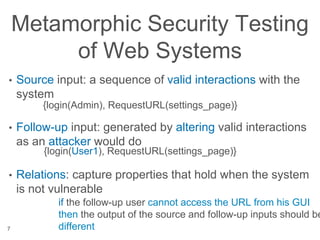
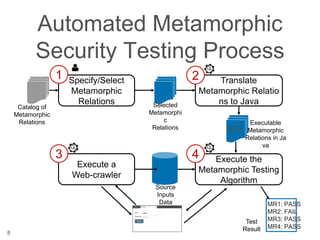
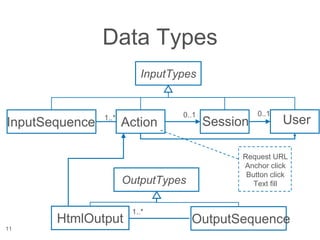
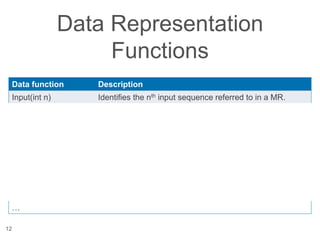
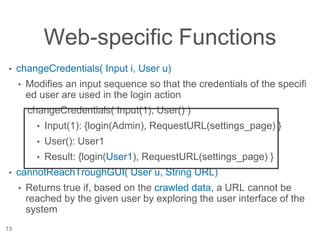
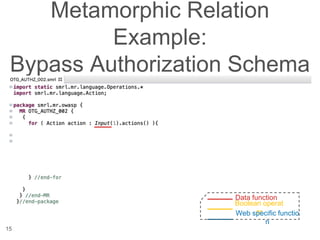
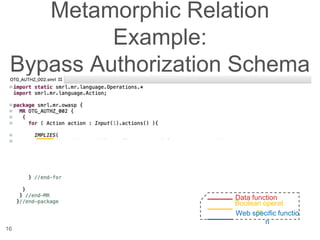
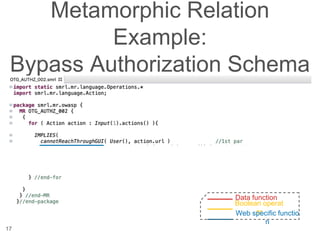
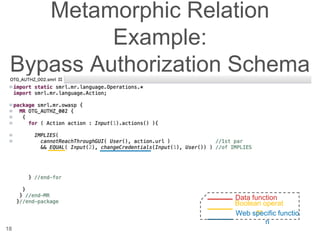
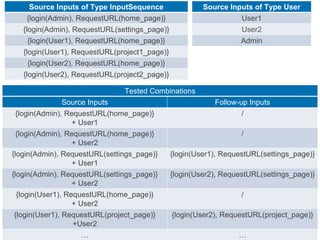
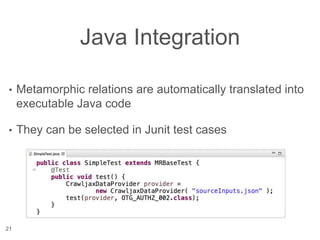
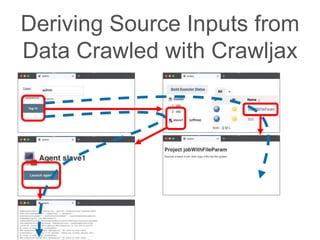
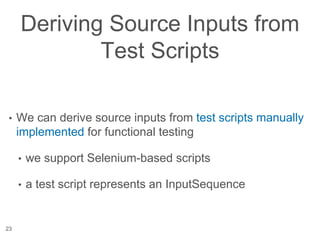
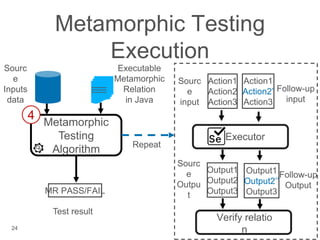
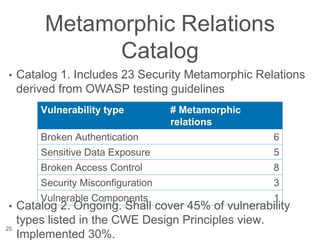
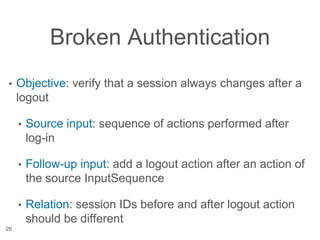
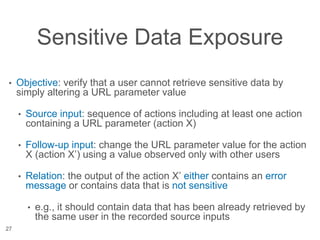
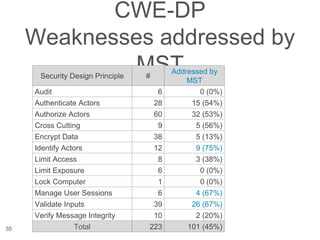
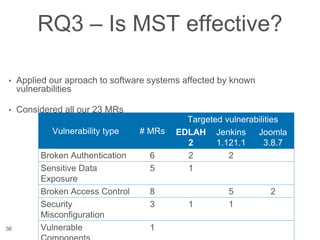
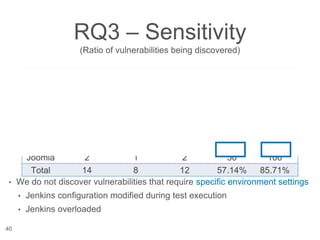
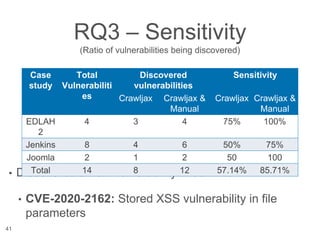
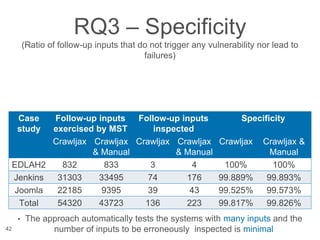
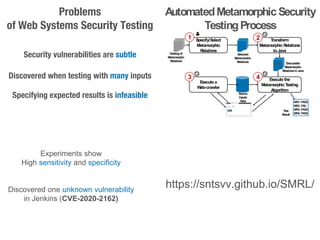
The document presents a novel approach to security testing for web systems using metamorphic testing to address the oracle problem, where expected results are hard to specify. It describes how automated metamorphic security testing can be implemented using a catalog of metamorphic relations that help identify security vulnerabilities, including specific case studies demonstrating the effectiveness of this method. The findings indicate high sensitivity and specificity in discovering vulnerabilities, including a previously unknown vulnerability in Jenkins.