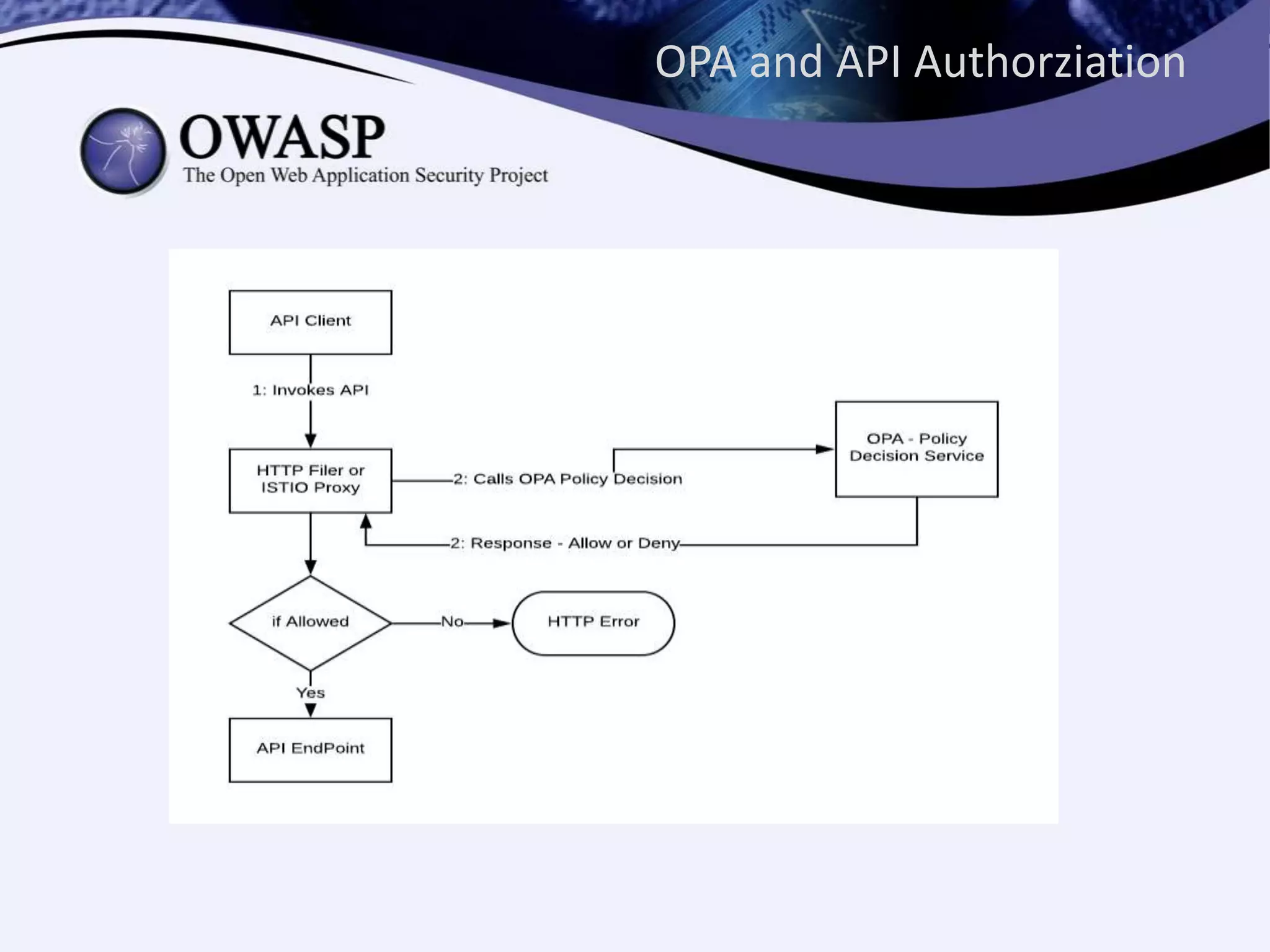
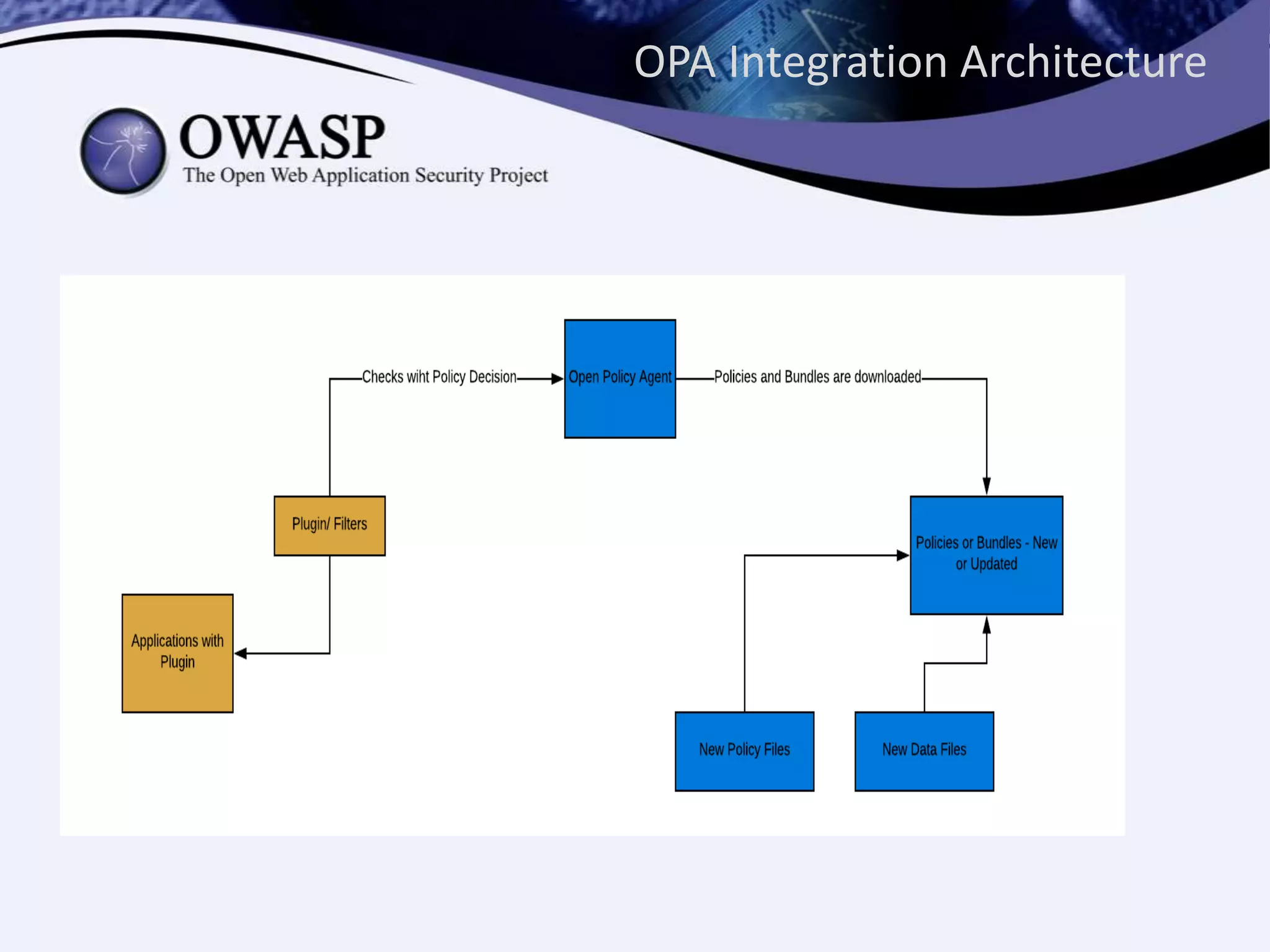
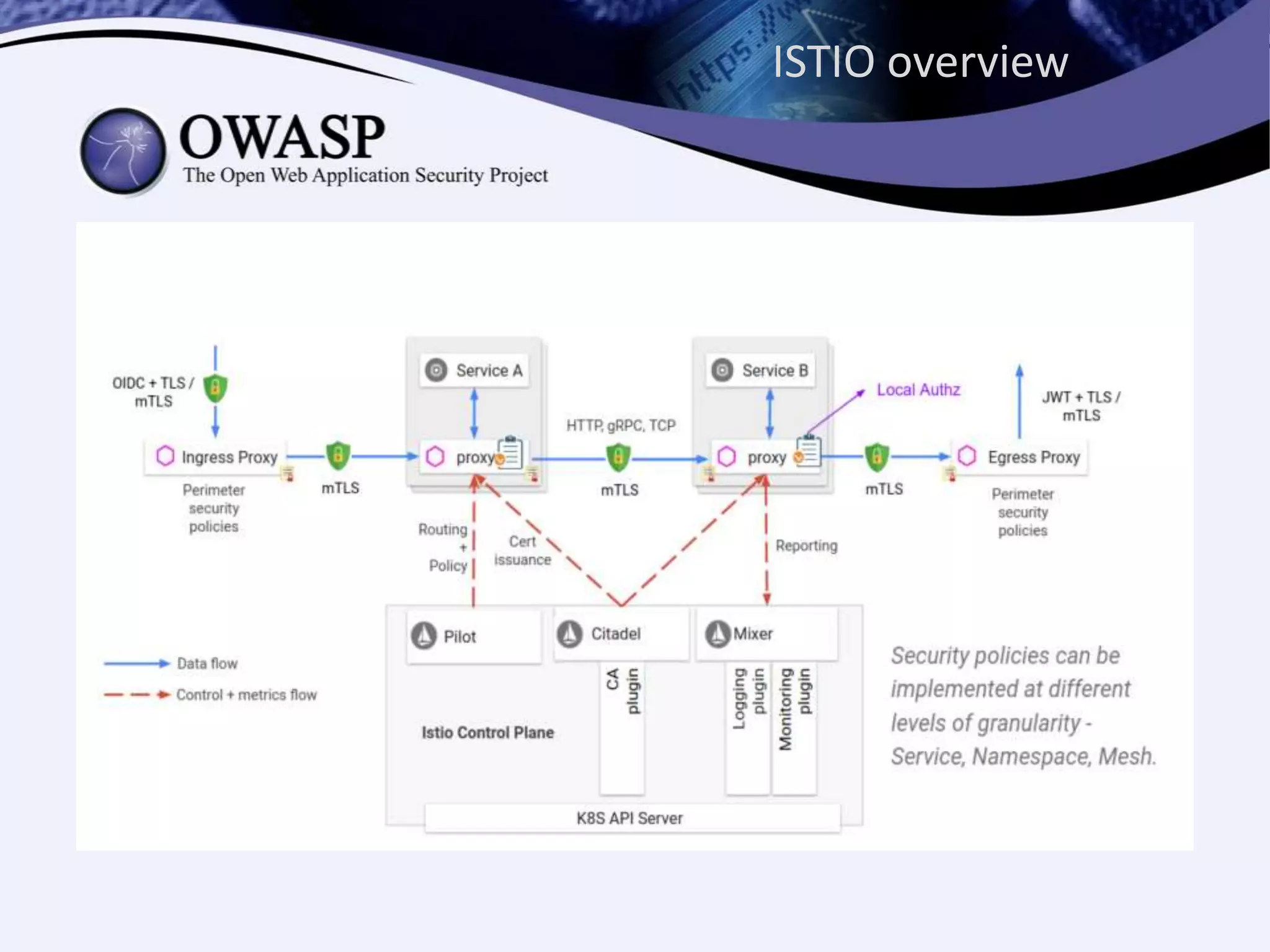
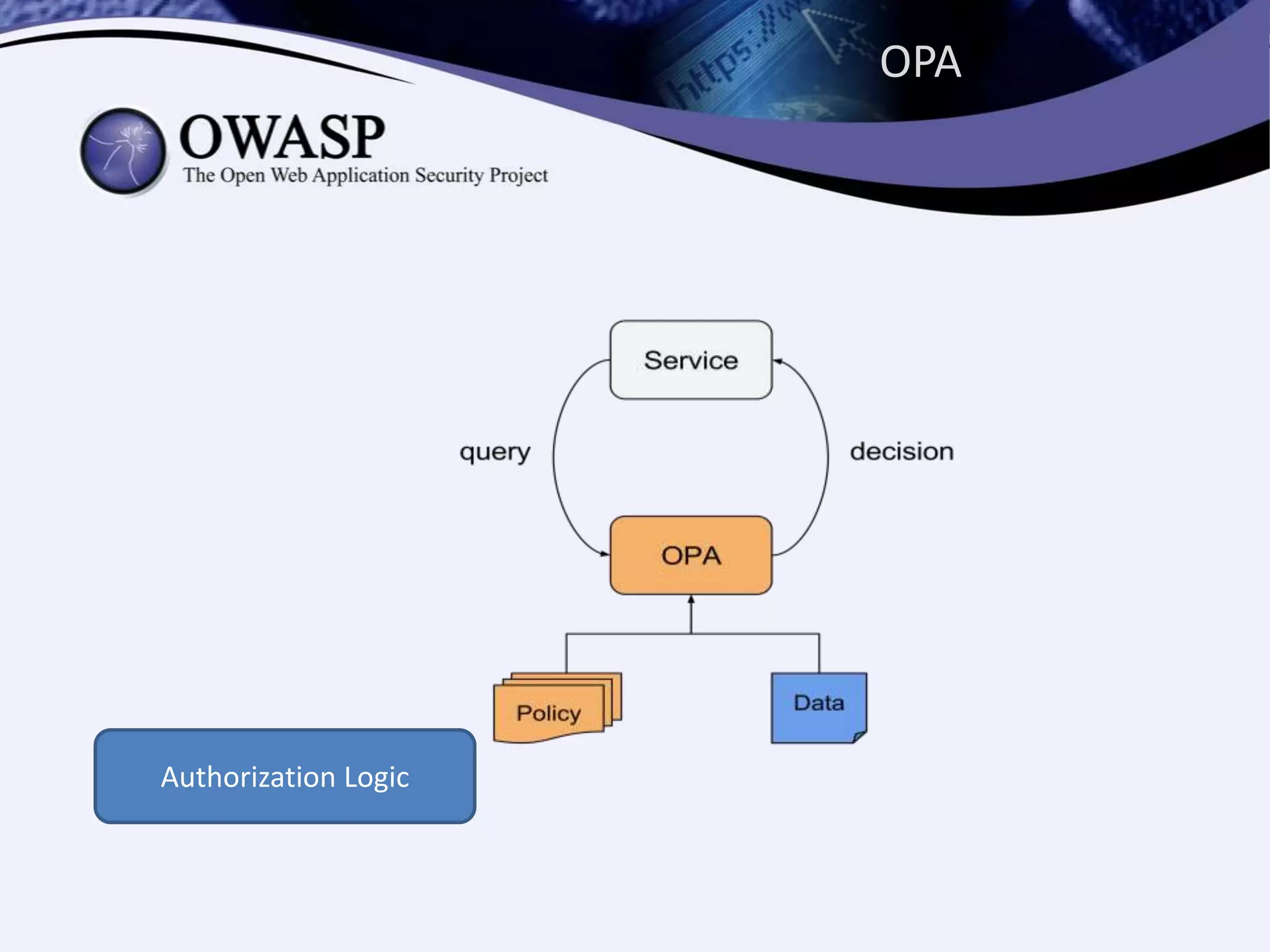
The document discusses authorization in microservices, focusing on the roles of Istio and Open Policy Agent (OPA). Key points include the significance of externalizing authorization from code, the evolution of access control mechanisms, and how OPA allows for declarative policy management that can easily adapt to various platforms. It emphasizes the benefits of using OPA to streamline policy decisions without requiring code redeployment.










![Example Web Hook AuthZ in
K8
{ "apiVersion":
"authorization.k8s.io/v1beta1",
"kind": "SubjectAccessReview",
"spec":
{ "resourceAttributes":
{ "namespace":
"kittensandponies",
"verb": "get",
"group":
"unicorn.example.org",
"resource":
"pods"
},
"user": "jane",
"group": [ "group1",
"group2" ]
}}
K8 API Version, so you can
make decision based on
Version of K8 API Server
Kind –
SubjectAccessReview
Describes type of Object.
Provides flexibility to add
any other review later.
ResourceAttributes – tells
everything you need to know.
What namespace being
accessed, whether its HTTP
get or post , user identity and
Group information ( can
come from JWT Token from
your SSO System, etc.)](https://image.slidesharecdn.com/owasp-appseccali2019-sitaraman-lakshminarayanan-190209181452/75/Externalizing-Authorization-in-Micro-Services-world-24-2048.jpg)




![ISTIO Authorization
apiVersion: "rbac.istio.io/v1alpha1"
kind: ServiceRole
metadata:
name: tester
namespace: default
spec:
rules:
- services: ["test-*"]
methods: ["*"]
- services:
["bookstore.default.svc.cluster.local"
]
paths: ["*/reviews"]
methods: ["GET"]
Authorization now
moved from Code /
Gateway config to
YAML .. We all love
Yet another..
Fine Grained ACL gets
challenging.
This is external to
code but still requires
re-deployment.](https://image.slidesharecdn.com/owasp-appseccali2019-sitaraman-lakshminarayanan-190209181452/75/Externalizing-Authorization-in-Micro-Services-world-30-2048.jpg)




![OPA Policy Walkthrough
Package Name
Rule Name
Compares Input – If method is
GET, Path is finance and
Username , if everything is true it
returns True.
Input is keyword. Assign Input as
http_api variable
package httpapi.authz
subordinates = {"alice": [], "charlie": [],
"bob": ["alice"], "betty": ["charlie"]} Static Data
import input as http_api
allow {
http_api.method = "GET"
http_api.path = ["finance",
"salary", username]
username = http_api.user }](https://image.slidesharecdn.com/owasp-appseccali2019-sitaraman-lakshminarayanan-190209181452/75/Externalizing-Authorization-in-Micro-Services-world-36-2048.jpg)
![How is OPA Policy invoked?
input_dict =
{ # create input to hand to OPA "input":
{ "user": api_user_from_jwt,
"path": “finance”,
"method": “GET”
}
}
rsp =
requests.post("http://example.com/v1/data/htt
papi/authz", data=json.dumps(input_dict))
if rsp.json()["allow"]
Gather Input.
HTTP Filter that gathers all
the data such as User ,
Method, URL Path, etc.
Make a Call to OPA - POST
v1/data/{PolicyName} and
supply the Input, get a
decision back as JSON
JSON is returned with
allow:True or can be any
specific data](https://image.slidesharecdn.com/owasp-appseccali2019-sitaraman-lakshminarayanan-190209181452/75/Externalizing-Authorization-in-Micro-Services-world-37-2048.jpg)