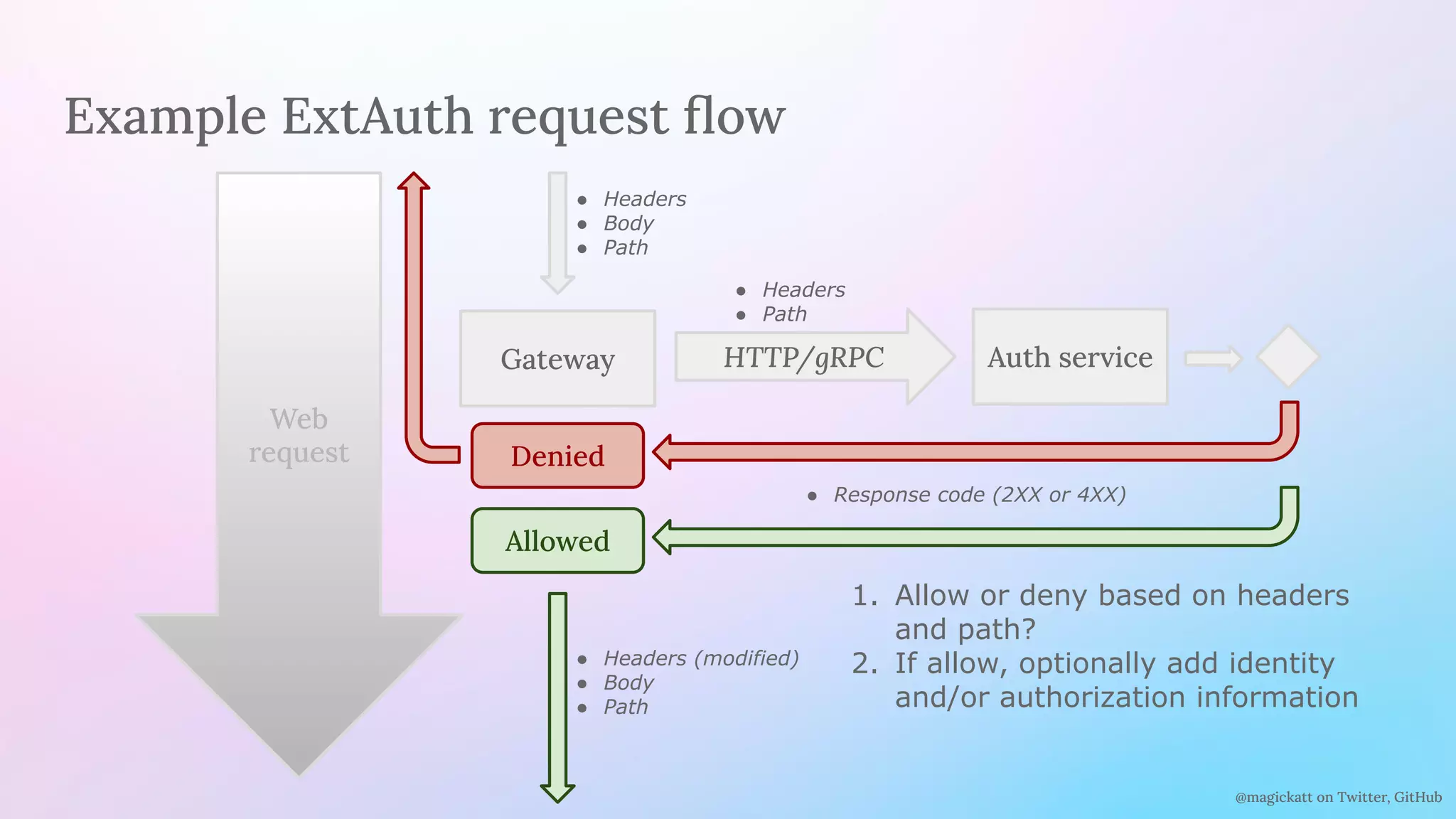
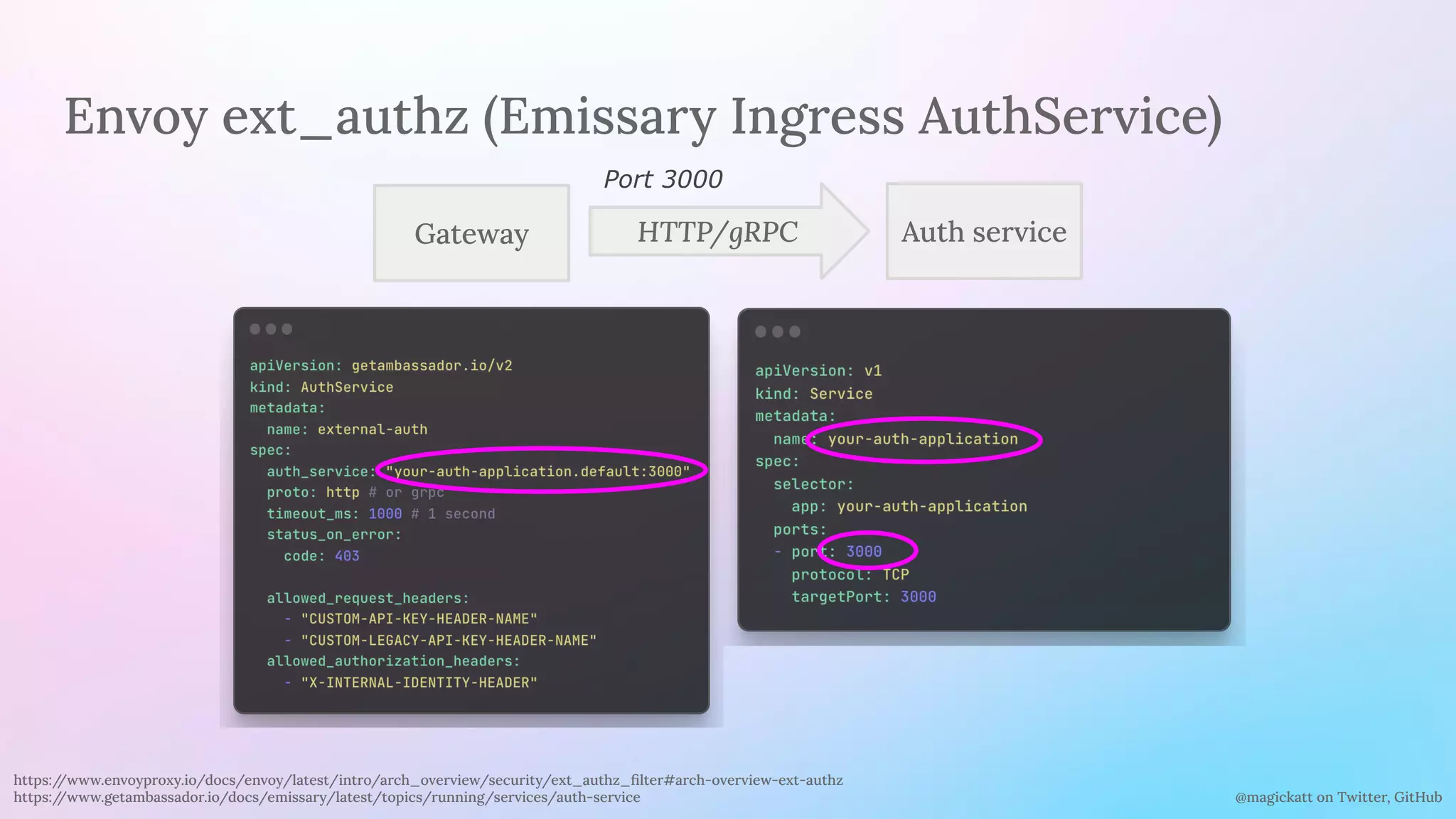
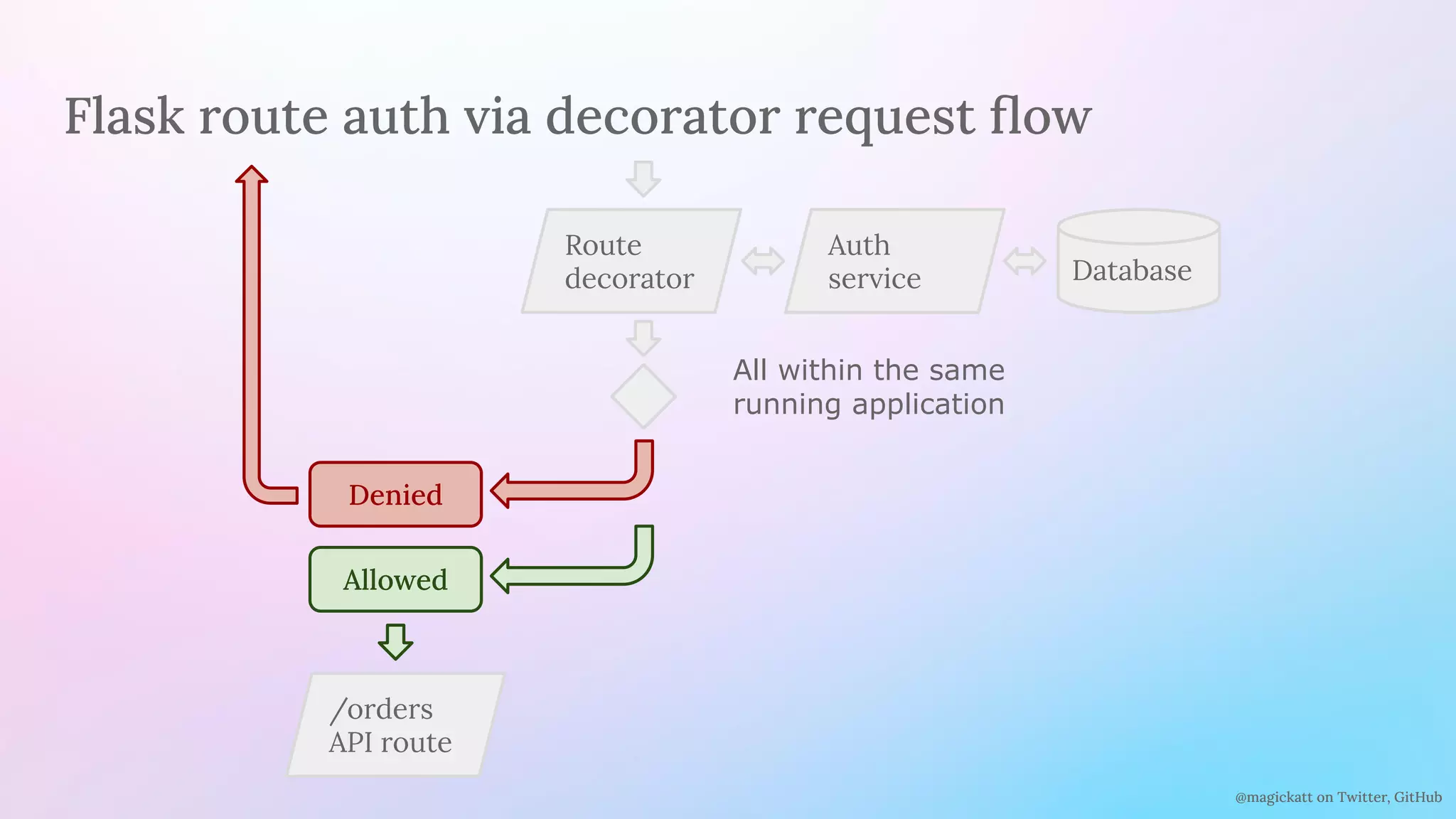
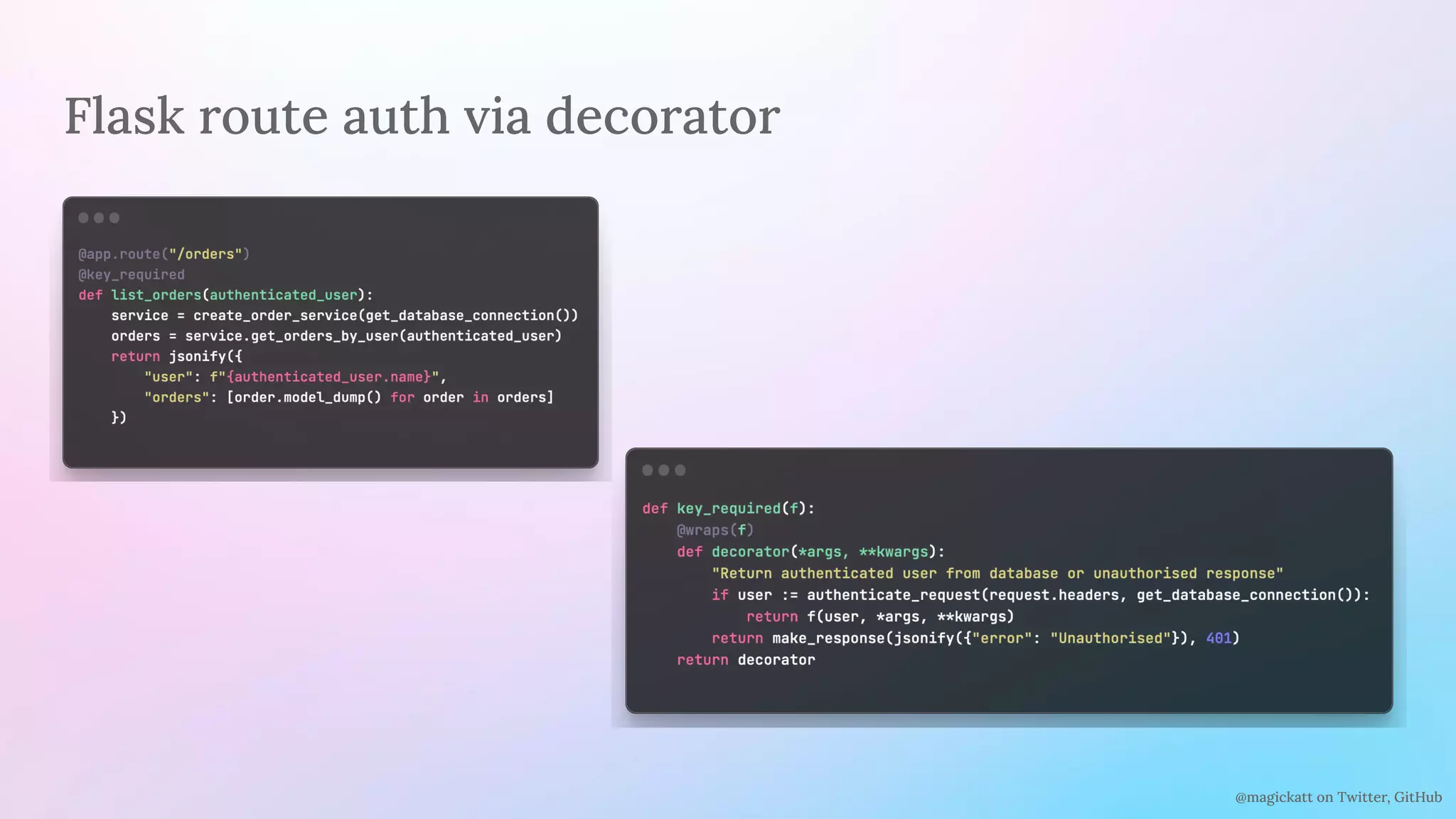
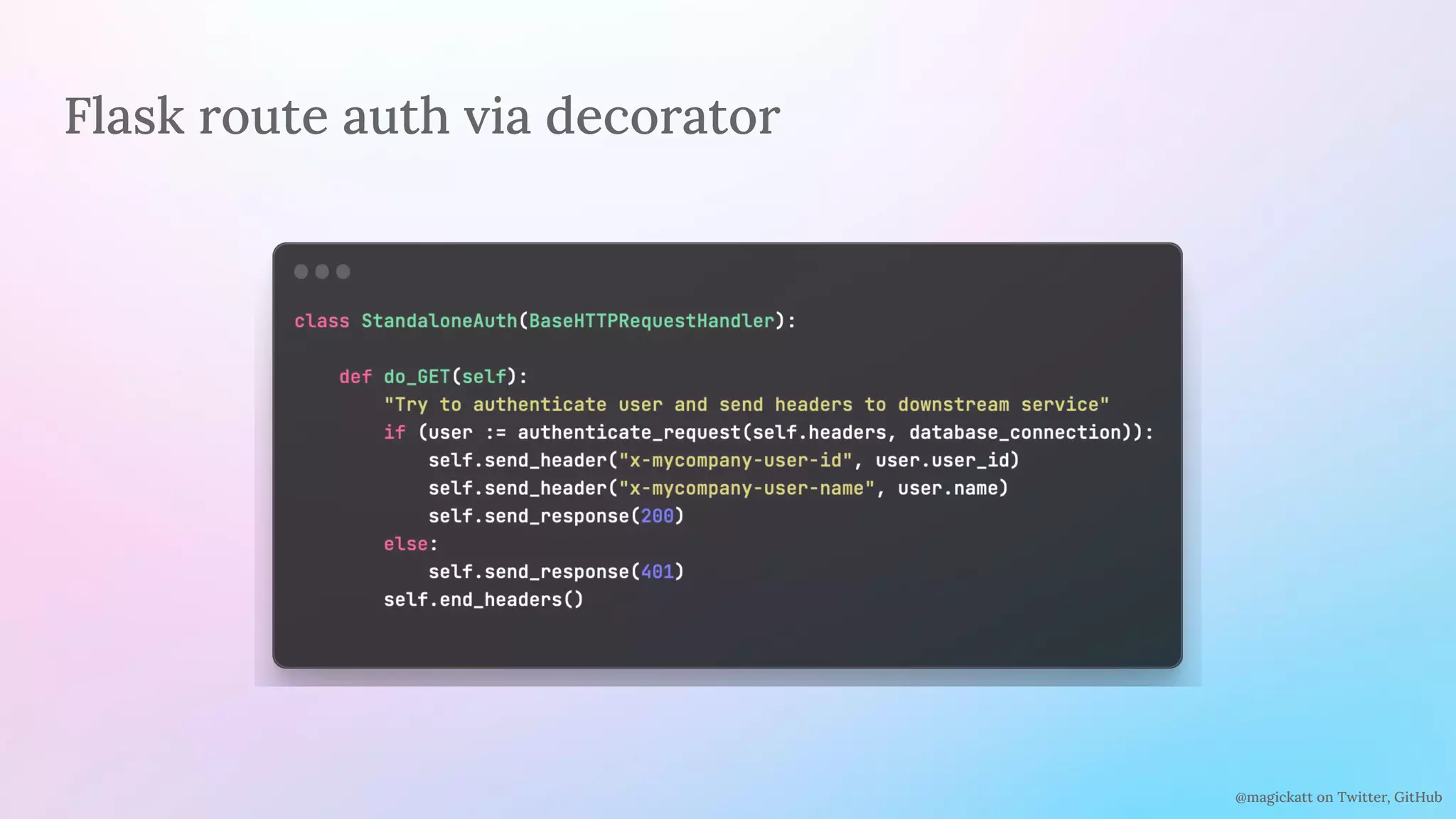
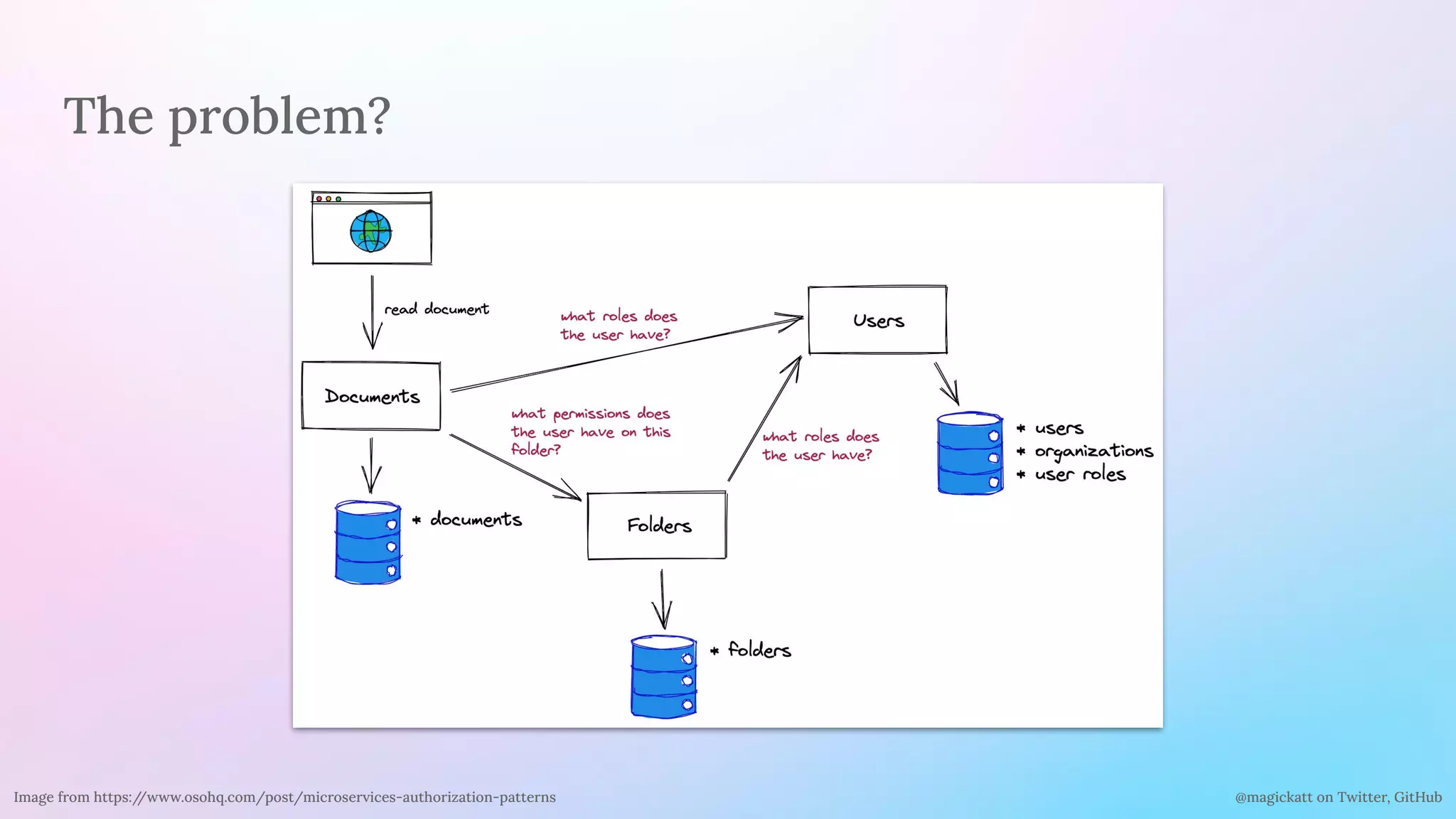
The document discusses the challenges and considerations in centralizing legacy authentication at the ingress gateway, offering insight into various authentication types and their management. It emphasizes the importance of identifying authentication mechanisms, synchronizing user data, and defining where authorization should occur in a system. The content culminates in practical examples and recommendations for integrating authentication services with existing applications for enhanced security and efficiency.










![@magickatt on Twitter, GitHub
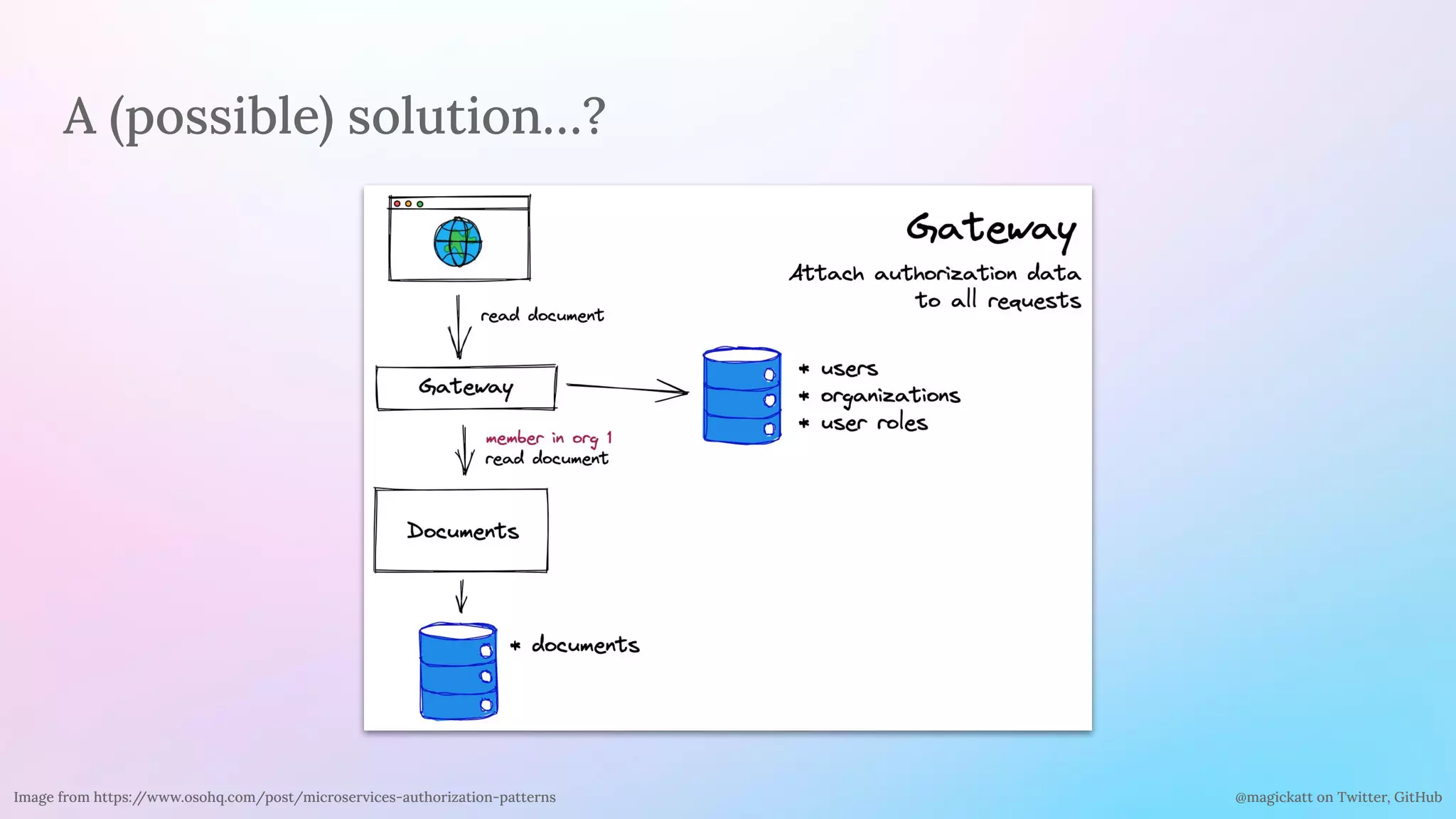
Delegates granular authorization
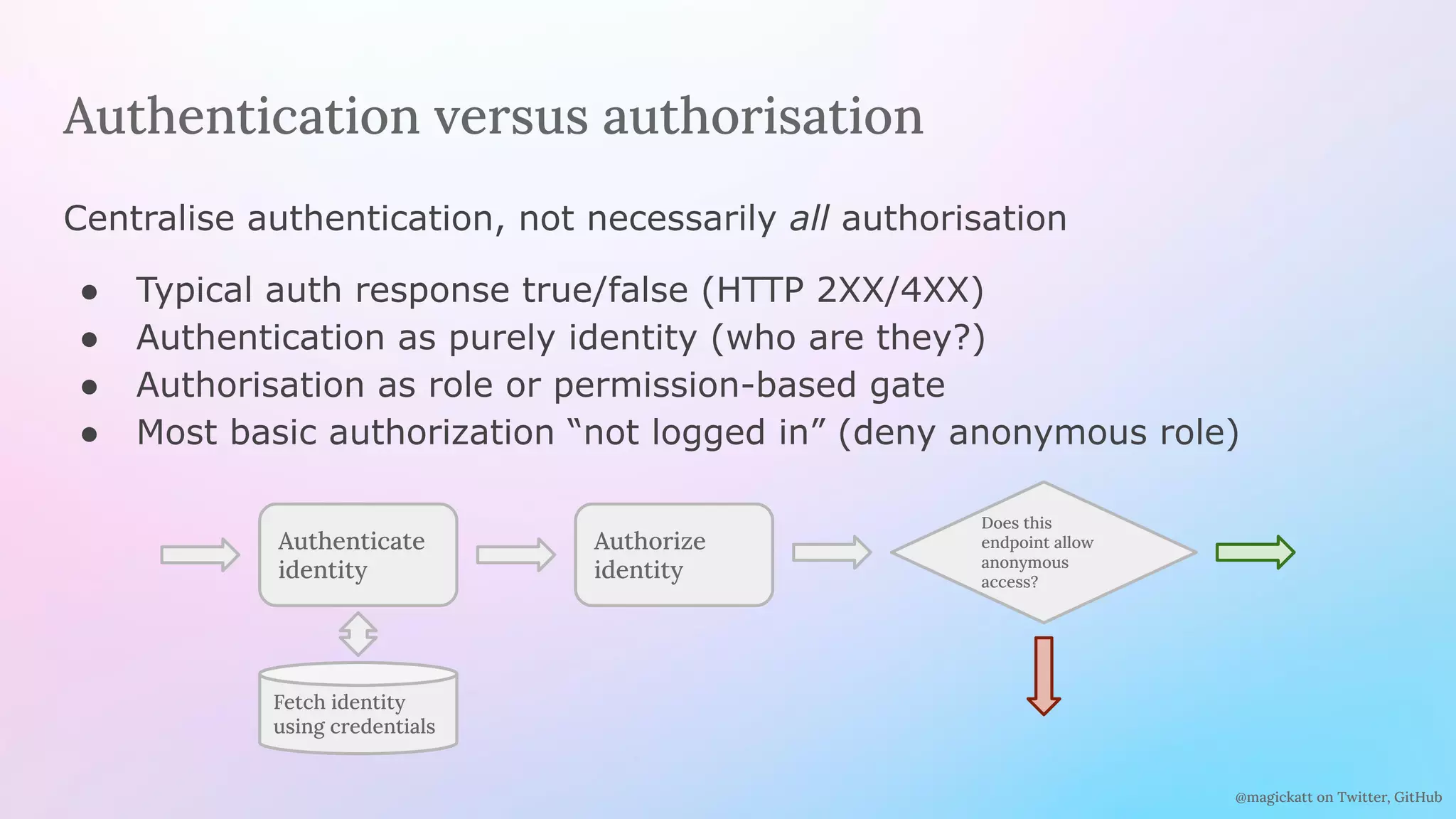
Authenticate
identity
Authorize
identity
Fetch identity
using credentials
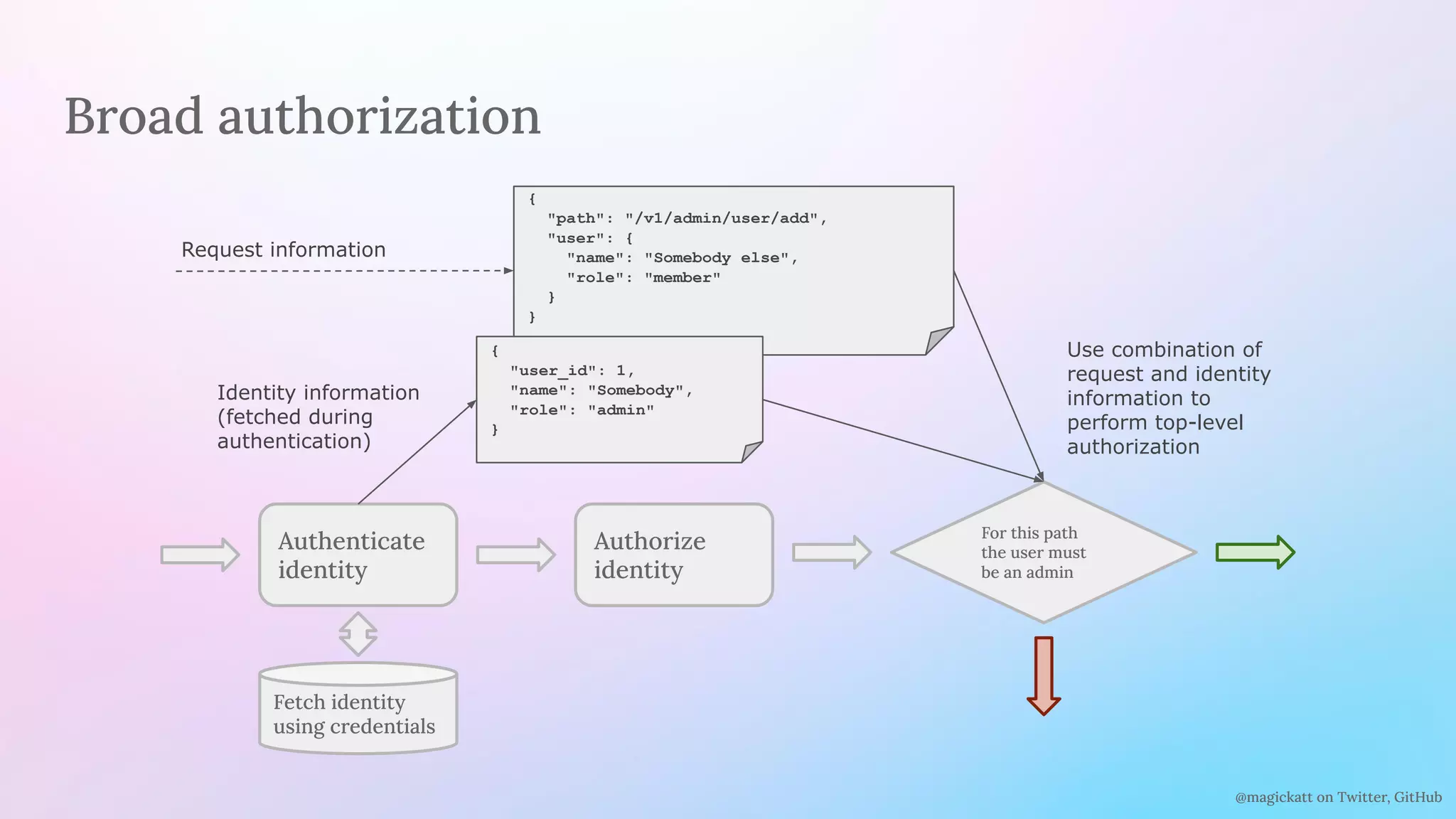
Broad
authz
{
"user_id": 1,
"name": "Somebody",
"group": 2,
"roles": [
"document/viewer",
"group/moderator",
"report/viewer"
],
"acl": {
"document/1/admin": true,
"document/4/admin": true,
"document/8/admin": true
}
}
Too complicated
to authorize here,
let downstream
service decide…
{
"path": "/v1/document/123/attachment/456/delete"
}
Check
ACLs
Check
roles
Delete
document
Document service](https://image.slidesharecdn.com/centraliselegacyauthattheingressgatewaysreday-3-230915083544-3e4d7aff/75/Centralise-legacy-auth-at-the-ingress-gateway-SREday-22-2048.jpg)