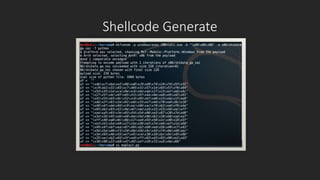
The document discusses Win32 buffer overflow exploitation, including prerequisites like understanding memory stacks, CPU registers, and assembly language. It explains various CPU registers like general purpose, segment, index/pointer, and EFLAGS registers. The document also covers stack layout, what a buffer overflow is, sample vulnerable code, and the steps to develop an exploit including fuzzing to find the crash point, overwriting EIP to control execution flow, generating shellcode, and creating a final payload.















![Vul code sample
Array
int [20];
int [20][5];
int [20][5][3];
Format Strings;
printf(), fprint(),sprint(),sprintf()
Overflow
strcpy()
strcat()
sprintf()
vsprint()
scanf()](https://image.slidesharecdn.com/c56bb387-7f58-4855-a321-efd8f4919174-170130103649/85/Exploit-Development-16-320.jpg)
![Sample Program
GetInput()
{
char buffer[8];
gets(buffer);
puts(buffer);
}](https://image.slidesharecdn.com/c56bb387-7f58-4855-a321-efd8f4919174-170130103649/85/Exploit-Development-17-320.jpg)