Ernst & Young visuals security survey 2012
•Download as PPTX, PDF•
0 likes•446 views
Risk and Security not always aligned. Not enough non IT focus on security. Hardly surprising that organisational Information Security needs are not being met in enough organisations.
Report
Share
Report
Share
Recommended
2018 U.S State of Cybercrime

This year, CSO partnered with the CERT® Division of Software Engineering Institute at Carnegie Mellon University, U.S. Secret Service and KnowBe4 to evaluate trends in the frequency and impact of cybersecurity incidents
2018 Security Priorities 

In its second year, IDG’s 2018 Security Priorities study was conducted to gain a better understanding of organization’s current and future security posture.
2018 Global State of Information Security Survey

The 2018 Global State of Information Security SurveyTM (GSISS) is conducted by PwC, CIO and CSO to understand how security practices and incidents are impacting the broader market.
Cybersecurity and Healthcare - HIMSS 2018 Survey

Survey of HIMSS 2018 attendees reveals more than 1 in 3 Healthcare Organizations have suffered a cyberattack while 1 in 10 have paid a ransom.
2021 IDG Security Priorities Study

Summary based on IDG's 2021 Security Priorities study which provides insight into the security projects organizations are prioritizing in the coming year.
Understanding the Security-Specific Purchase Process [Infographic]![Understanding the Security-Specific Purchase Process [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Understanding the Security-Specific Purchase Process [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
IDG research infographic shares insight into the specific security purchase process, such as the types of purchases being made whether they be additions, upgrades or replacements, the content types and information sources relied upon by security buyers, and who is involved in each stage of the security purchase process.
Impact of COVID-19 [Infographic]![Impact of COVID-19 [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Impact of COVID-19 [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Infographic based on the CSO Pandemic Impact Survey, fielded March 2020, which shares how COVID-19 is affecting security within organizations.
Recommended
2018 U.S State of Cybercrime

This year, CSO partnered with the CERT® Division of Software Engineering Institute at Carnegie Mellon University, U.S. Secret Service and KnowBe4 to evaluate trends in the frequency and impact of cybersecurity incidents
2018 Security Priorities 

In its second year, IDG’s 2018 Security Priorities study was conducted to gain a better understanding of organization’s current and future security posture.
2018 Global State of Information Security Survey

The 2018 Global State of Information Security SurveyTM (GSISS) is conducted by PwC, CIO and CSO to understand how security practices and incidents are impacting the broader market.
Cybersecurity and Healthcare - HIMSS 2018 Survey

Survey of HIMSS 2018 attendees reveals more than 1 in 3 Healthcare Organizations have suffered a cyberattack while 1 in 10 have paid a ransom.
2021 IDG Security Priorities Study

Summary based on IDG's 2021 Security Priorities study which provides insight into the security projects organizations are prioritizing in the coming year.
Understanding the Security-Specific Purchase Process [Infographic]![Understanding the Security-Specific Purchase Process [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Understanding the Security-Specific Purchase Process [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
IDG research infographic shares insight into the specific security purchase process, such as the types of purchases being made whether they be additions, upgrades or replacements, the content types and information sources relied upon by security buyers, and who is involved in each stage of the security purchase process.
Impact of COVID-19 [Infographic]![Impact of COVID-19 [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Impact of COVID-19 [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Infographic based on the CSO Pandemic Impact Survey, fielded March 2020, which shares how COVID-19 is affecting security within organizations.
State of the CIO 2018 Infographic

Based on the 2018 State of the CIO research, this infographic provides insights into how IT leaders are leading change efforts and promoting a culture of collaboration.
Sécurité Mobile : Votre Entreprise est-elle préparée pour 2020?

Bonjour,
Nous avons pensé que ce webinar devrait vous intéresser.
Comment la mobilité, l'Internet des objets et l'intelligence artificielle vont impacter la votre transformation digitale.
Toutes les entreprises modernes s'activent pour accélérer leur transformation numérique, mettant une pression immense sur les responsables informatiques pour la réalisation de projets nouveaux et ambitieux. Cela arrive à un moment où les équipes informatique et de sécurité sont invitées à s'intégrer davantage. Pendant ce temps, la travail quotidien de la gestion des utilisateurs, des appareils, des applications et du contenu devient plus encombrant.
Revivez ce webinar qui présente sur l'étude Forrester, basée sur la contribution de 556 professionnels de l'IT. Découvrez ce que l'avenir réserve pour mobilité, les terminaux et l'IoT en 2020:
Quel équipe IT sera responsable de la sécurisation de l'IoT?
Combien de systèmes seront nécessaires pour gérer les terminaux du futur?
Dans quelle mesure votre environnement de base changera-t-il radicalement dans quelques années?
D'ici 2020, quel pourcentage d'organisations utiliseront l'informatique propulsée par l'Intelligence Artificielle et l'Analyse Cognitive?
Understanding the Data & Analytics Specific Purchase Process [Infographic]![Understanding the Data & Analytics Specific Purchase Process [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Understanding the Data & Analytics Specific Purchase Process [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
This infographic outlines what goes into data & analytics purchases – who’s involved in the process, the content they rely upon and the sources the turn to to stay up-to-date on industry news.
Cyber-attacks

Cyber-attacks are increasing every day - are corporate leadership and security in sync on how to fight them?
IDG 2020 Security Priorities Research

IDG’s fourth annual Security Priorities study aims to gain a better understanding of the various security projects organizations are focused on now and in the coming year.
CAPP Conference Survey

CynergisTek’s Survey Data Reveals Leading Cybersecurity Concerns for Healthcare Organization Executives.
Client-Conference Data Unveils That Risks Associated with Internet of Things, Medical Devices, Third-Party Vendors, and Program Management are Top of Mind for Security Executives, Yet Action is Lagging
CIO Tech Poll: Tech Priorities 2018

The CIO Tech Poll: Tech Priorities 2018 study explores the upcoming tech spending plans and budgets for organizations, and outlines the technology areas IT leaders expect their budgets to focus on.
Cloud Insights 2018

The 2018 IDG Cloud Computing study was conducted to measure cloud computing trends among technology decision-makers, which includes their usage and plans across various cloud service and deployment models, investments, business drivers and impact on business strategy and plans.
EMA Megatrends in Cyber-Security

These slides--based on the webinar from leading IT research firm Enterprise Management Associates (EMA)--reveal the current state of enterprise security readiness within the context of security management tools, issues, and practices.
CSO Pandemic Impact Survey, 2020

To get a better understanding of how organizations were prepared from a security perspective and the impact that security leaders expect to be long lasting due to COVID-19.
2018 State of the Network

Network World’s State of the Network research is conducted annually to gain a deeper understanding of the network environments within today’s organizations.
State of the CIO 2018

CIO’s 17th annual “State of the CIO” survey was conducted with the goal of understanding how the CIO role continues to evolve in today’s business climate and to help define the CIO agenda for 2018.
The Cyber Security Readiness of Canadian Organizations

Highlights of the 2015 Scalar Security Study, The Cyber Security Readiness of Canadian Organizations, published February 2015. The full report can be downloaded at: http://hubs.ly/y0tFbr0
Executive Summary of the 2016 Scalar Security Study

Executive Summary of the 2016 Scalar Security Study, The Cyber Security Readiness of Canadian Organizations, published February 2016. The full report can be downloaded at: scalar.ca/security-study-2016/
Digital Business 2018

The 2018 IDG Digital Business research was conducted to gain a better understanding of how organizations are evolving to a digital business model in terms of revising technology strategies, changing organizational structures and processes, and innovating to provide a unique customer experience.
SVB Cybersecurity Impact on Innovation Report - Overview

In a survey of U.S. technology and healthcare executives nationwide, Silicon Valley Bank found that companies believe cyber attacks are a serious threat to both their data and their business continuity.
Highlights
- 98% are maintaining or increasing resources devoted to cyber security
- 50% are increasing their cyber security resources, preparing for when, not if, cyber attacks occur
- Just 35% are completely or very confident in the security of their company information, and only 16% feel the same about their business partners
IDG 2019 Digital Business infographic

Insights on how organizations are evolving to a digital-first approach
2017 Role & Influence of the Technology Decision-Maker

The 2017 IDG Role & Influence of the Technology Decision-Maker survey examines the evolving role of IT decision-makers (ITDMs) in today’s corporations, specifically as organizations move towards a more digital-focused business.
How to Connect Your Server Room to the Board Room – Before a Data Breach Occurs

With the board room increasingly being held accountable for data breaches, it's crucial that they know and understand the cyber risks facing their organization.Connect board room to server room
More Related Content
What's hot
State of the CIO 2018 Infographic

Based on the 2018 State of the CIO research, this infographic provides insights into how IT leaders are leading change efforts and promoting a culture of collaboration.
Sécurité Mobile : Votre Entreprise est-elle préparée pour 2020?

Bonjour,
Nous avons pensé que ce webinar devrait vous intéresser.
Comment la mobilité, l'Internet des objets et l'intelligence artificielle vont impacter la votre transformation digitale.
Toutes les entreprises modernes s'activent pour accélérer leur transformation numérique, mettant une pression immense sur les responsables informatiques pour la réalisation de projets nouveaux et ambitieux. Cela arrive à un moment où les équipes informatique et de sécurité sont invitées à s'intégrer davantage. Pendant ce temps, la travail quotidien de la gestion des utilisateurs, des appareils, des applications et du contenu devient plus encombrant.
Revivez ce webinar qui présente sur l'étude Forrester, basée sur la contribution de 556 professionnels de l'IT. Découvrez ce que l'avenir réserve pour mobilité, les terminaux et l'IoT en 2020:
Quel équipe IT sera responsable de la sécurisation de l'IoT?
Combien de systèmes seront nécessaires pour gérer les terminaux du futur?
Dans quelle mesure votre environnement de base changera-t-il radicalement dans quelques années?
D'ici 2020, quel pourcentage d'organisations utiliseront l'informatique propulsée par l'Intelligence Artificielle et l'Analyse Cognitive?
Understanding the Data & Analytics Specific Purchase Process [Infographic]![Understanding the Data & Analytics Specific Purchase Process [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Understanding the Data & Analytics Specific Purchase Process [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
This infographic outlines what goes into data & analytics purchases – who’s involved in the process, the content they rely upon and the sources the turn to to stay up-to-date on industry news.
Cyber-attacks

Cyber-attacks are increasing every day - are corporate leadership and security in sync on how to fight them?
IDG 2020 Security Priorities Research

IDG’s fourth annual Security Priorities study aims to gain a better understanding of the various security projects organizations are focused on now and in the coming year.
CAPP Conference Survey

CynergisTek’s Survey Data Reveals Leading Cybersecurity Concerns for Healthcare Organization Executives.
Client-Conference Data Unveils That Risks Associated with Internet of Things, Medical Devices, Third-Party Vendors, and Program Management are Top of Mind for Security Executives, Yet Action is Lagging
CIO Tech Poll: Tech Priorities 2018

The CIO Tech Poll: Tech Priorities 2018 study explores the upcoming tech spending plans and budgets for organizations, and outlines the technology areas IT leaders expect their budgets to focus on.
Cloud Insights 2018

The 2018 IDG Cloud Computing study was conducted to measure cloud computing trends among technology decision-makers, which includes their usage and plans across various cloud service and deployment models, investments, business drivers and impact on business strategy and plans.
EMA Megatrends in Cyber-Security

These slides--based on the webinar from leading IT research firm Enterprise Management Associates (EMA)--reveal the current state of enterprise security readiness within the context of security management tools, issues, and practices.
CSO Pandemic Impact Survey, 2020

To get a better understanding of how organizations were prepared from a security perspective and the impact that security leaders expect to be long lasting due to COVID-19.
2018 State of the Network

Network World’s State of the Network research is conducted annually to gain a deeper understanding of the network environments within today’s organizations.
State of the CIO 2018

CIO’s 17th annual “State of the CIO” survey was conducted with the goal of understanding how the CIO role continues to evolve in today’s business climate and to help define the CIO agenda for 2018.
The Cyber Security Readiness of Canadian Organizations

Highlights of the 2015 Scalar Security Study, The Cyber Security Readiness of Canadian Organizations, published February 2015. The full report can be downloaded at: http://hubs.ly/y0tFbr0
Executive Summary of the 2016 Scalar Security Study

Executive Summary of the 2016 Scalar Security Study, The Cyber Security Readiness of Canadian Organizations, published February 2016. The full report can be downloaded at: scalar.ca/security-study-2016/
Digital Business 2018

The 2018 IDG Digital Business research was conducted to gain a better understanding of how organizations are evolving to a digital business model in terms of revising technology strategies, changing organizational structures and processes, and innovating to provide a unique customer experience.
SVB Cybersecurity Impact on Innovation Report - Overview

In a survey of U.S. technology and healthcare executives nationwide, Silicon Valley Bank found that companies believe cyber attacks are a serious threat to both their data and their business continuity.
Highlights
- 98% are maintaining or increasing resources devoted to cyber security
- 50% are increasing their cyber security resources, preparing for when, not if, cyber attacks occur
- Just 35% are completely or very confident in the security of their company information, and only 16% feel the same about their business partners
IDG 2019 Digital Business infographic

Insights on how organizations are evolving to a digital-first approach
2017 Role & Influence of the Technology Decision-Maker

The 2017 IDG Role & Influence of the Technology Decision-Maker survey examines the evolving role of IT decision-makers (ITDMs) in today’s corporations, specifically as organizations move towards a more digital-focused business.
How to Connect Your Server Room to the Board Room – Before a Data Breach Occurs

With the board room increasingly being held accountable for data breaches, it's crucial that they know and understand the cyber risks facing their organization.Connect board room to server room
What's hot (20)
Sécurité Mobile : Votre Entreprise est-elle préparée pour 2020?

Sécurité Mobile : Votre Entreprise est-elle préparée pour 2020?
Understanding the Data & Analytics Specific Purchase Process [Infographic]![Understanding the Data & Analytics Specific Purchase Process [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Understanding the Data & Analytics Specific Purchase Process [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Understanding the Data & Analytics Specific Purchase Process [Infographic]
The Cyber Security Readiness of Canadian Organizations

The Cyber Security Readiness of Canadian Organizations
Executive Summary of the 2016 Scalar Security Study

Executive Summary of the 2016 Scalar Security Study
SVB Cybersecurity Impact on Innovation Report - Overview

SVB Cybersecurity Impact on Innovation Report - Overview
2017 Role & Influence of the Technology Decision-Maker

2017 Role & Influence of the Technology Decision-Maker
How to Connect Your Server Room to the Board Room – Before a Data Breach Occurs

How to Connect Your Server Room to the Board Room – Before a Data Breach Occurs
Viewers also liked
The Cyber Threat to the Built Estate 

Cyber Threat is now a very real physical threat to our buildings and national infrastructure. Hackers can now disable buildings, satellites, power stations, air traffic control and many other critical infrastructure elements. Learn more in this presentation from Mike Gillespie of Advent IM Ltd
The IT Cyber Battle

The ongoing battle IT has in getting security issues into the Boardroom and other Security issues that IT need addressing.
The Human Threat in Data protection 

2012 Ponemon Research on Data Protection failings and the human factor in Data Protection
SMEs, Security and How Its a Growing Threat

Data Source: Department For Business, Innovation & Skills
SMEs and Security.
Comparing the security performance with larger organisations and examining some of the weaknesses from a Business Function perspective
Employee monitoring updated

Monitoring employees or actually snooping? Now includes narration by Mike Gillespie - Advent IM MD and Director of Cyber Security Strategy for The Security Institute.
Social Engineering, Insider and Cyber Threat 

Presentation with voice over: Discussion of how Social Engineers can target a business as part of preparation for a cyber attack and how this gives us more opportunities to prevent or limit the affect of the attack through proper policy, use of resources and training.
Drupal 7 Entity & Entity API

http://drupalcity.de/session/drupal-7-development-done-right-leverage-entities
Data Breach and Hacking

Weak and stolen credentials enable much of data breach
#databreach #security #hacking
Viewers also liked (18)
Similar to Ernst & Young visuals security survey 2012
Cyber security: Five leadership issues worthy of board and executive attention

Cyber security: Five leadership issues worthy of board and executive attentionRamón Gómez de Olea y Bustinza
Estudio de Russell Reynolds Associates sobre ciberseguridad que explora la importancia de la relación entre el Chief Information Security Officer y el Consejo de Administración. Cyber security: five leadership issues worthy of Board and executive attention

Cyber security: five leadership issues worthy of Board and executive attentionRamón Gómez de Olea y Bustinza
Russell Reynolds Associates aborda cinco cuestiones de liderazgo en materia de ciberseguridad que los Consejos de Administración y los ejecutivos deben preguntarse. Estas cuestiones abarcan diversos aspectos, desde el nivel de preparación del Consejo hasta la gestión del talento para proteger el negocio de una forma integral.Build a Business-Driven IT Risk Management Program

Your Challenge
Risk is an unavoidable part of IT. And what you don't know, can hurt you. The question is, do you tackle risk head-on or leave it to chance?
Get a handle on risk management quickly using Info-Tech's methodology and reduce unfortunate IT surprises.
Our Advice
Critical Insight
1. IT risk is business risk.
Every IT risk has business implications. Create an IT risk management program that shares risk accountability with the business.
2. Risk is money.
It’s impossible to make intelligent decisions about risks without knowing what they’re worth.
3. You don’t know what you don’t know.
And what you don’t know can hurt you – so find out. To find hidden risks, you need a structured approach.
Impact and Result
Stop leaving IT risk to chance. Transform your ad hoc IT risk management processes into a formalized, ongoing program and increase risk management success by 53%.
Take a proactive stance against IT threats and vulnerabilities by identifying and assessing IT’s greatest risks before they happen.
Involve key stakeholders including the business senior management team to gain buy-in and to focus on IT risks that matter most to the organization.
Share accountability for IT risk with business stakeholders and have them weigh-in on prioritizing investments in risk response activities.
Remote Work Fuels Zero Trust Growth

See what Ping’s Executive Survey reveals about the security impacts of the shift to remote work.
Breaches Are Bad for Business. How Will You Detect and Respond to Your Next C...

Breaches Are Bad for Business. How Will You Detect and Respond to Your Next C...Hewlett Packard Enterprise Business Value Exchange
Incident Response Management: How European Enterprises are Planning to Prepare for a Cyber Security Breach2014 Executive Breach Preparedness Research Report

2014 Executive Breach Preparedness Research ReportHewlett Packard Enterprise Business Value Exchange
According to the HP sponsored1 2014 Executive Breach Preparedness Research Report, more than 70 percent of executives think that their organization only partially understands the information risks they’re exposed to as a result of a breach. To add to that, less than half of c-suite and board-level executives are kept informed about the breach response process.
This report also found that business leadership knows that their involvement in data breach incident response is important – but they don’t believe, generally, that they are actually accountable for data breaches. In fact, only 45% stated that they think they are accountable for data breaches in their organization.
Read the full report for more insights.Information Security Benchmarking 2015

Information Security assessment of companies in Germany, Austria and Switzerland, February 2015.
Every day critical security incidents show the drastic extent of "successful" cyber attacks for organizations in terms of monetary and material loss. With increasing use of digital technologies and the growing spread of mobile and IoT cyber security is becoming a key factor for companies’ successful digital transformation. To analyze current challenges, trends and maturity of companies state of information security, Capgemini Consulting DACH conducted a survey in Germany, Austria and Switzerland. The 2014 Information Security Benchmarking Study shows that information security is insufficiently embedded in most companies‘ business strategy and operations to effectively safeguard organizations against current cyber threats.
https://www.de.capgemini-consulting.com/resources/information-security-benchmarking
Finding a strategic voice

Learn how an integrated approach, strategic reach and measurement systems of Influencers point to a new kind of security organization and a new breed of leader. For more information on IBM Systems, visit http://ibm.co/RKEeMO.
Visit the official Scribd Channel of IBM India Smarter Computing at http://bit.ly/VwO86R to get access to more documents.
Insights from the IBM Chief Information Security Officer Assessment

To obtain a global snapshot of security leaders’ strategies and approaches, the IBM Center for Applied Insights conducted double-blind interviews with 138 security leaders – the IT and line-of-business executives responsible for information security in their enterprises. Some of these leaders carried the title of Chief Information Security Officer (CISO), but given the diversity of organizational structures, many did not. The Center supplemented this quantitative research through in-depth conversations with 25 information security leaders.
Participation spanned a broad range of industries and seven different countries. Nearly 20 percent of the respondents lead information security in enterprises with more than 10,000 employees; 55 percent are in enterprises with 1,000 to 9,999 employees.
Harvey Nash UK & IRE Cyber Security Survey 2016

A complete breakdown of our Recent (2nd annual) Cyber Security Survey. Responses canvassed form over 200 like minded Professionals - and now here, free for you to see the issues, changes & shortages affecting your local Industry. As told from the people you'd want to hear from.
Government and Education Webinar: Public Sector Cybersecurity Survey - What I...

Join SolarWinds® CISO, Tim Brown, and Group Vice President, Brandon Shopp for a webinar to review and discuss our most recent Public Sector Cybersecurity Survey results, including significant differences across public sector market segments and how confident the respondents were in their teams’ ability to keep up with evolving threats.
The Cyber Security Leap: From Laggard to Leader

Security has risen to the top of the agenda amongst most C-suite executives and boards of directors today. Rapidly evolving security threats pose an ongoing, central challenge, as companies and governments face an increasingly sophisticated threat environment.
Accenture collaborated with the Ponemon Institute, LLC to explore the success factors of companies that demonstrated measurable improvement in security effectiveness over a period of two years. Find out how leapfrog organizations are improving their security posture and more quickly detecting security threats.
01-Build-an-IT-Risk-Management-Program--Phases-1-3.pptx

Overall document to help organizations mitigate the risks inherent with IT and how of to confidently handle to reduce impact.
ESG TechTruth: Advanced Persistent Threat: The Pervasive IT Security Skills S...

ESG TechTruth: Advanced Persistent Threat: The Pervasive IT Security Skills S...Enterprise Strategy Group
Most Commonly Cited Area with a Problematic Shortage of IT Skills for 4th Consecutive Year: Information SecurityCyber Security in the Digital Age: A Survey and its Analysis

Kapil Dev Singh, Principal Analyst, Core Quadrant
5 Questions Executives Should Be Asking Their Security Teams 

5 Questions Executives Should Be Asking Their Security Teams Arun Chinnaraju MBA, PMP, CSM, CSPO, SA
1. How often do you see non-sanctioned cloud services in use?
2. Are we protecting ourselves against insider threats?
3. Do we have a cyber security task force in place?
4. Is our BYOD policy secure?
5. Do you feel limited by your security budget or staff size?Is Your Company Ready for a Big Data Breach?

All information, data, and material contained, presented, or provided on is for educational purposes only.
Company names mentioned herein are the property of, and may be trademarks of, their respective owners.
It is not to be construed or intended as providing legal advice.
Company names mentioned herein are the property of, and may be trademarks of, their respective owners and are for educational purposes only.
17 U.S. Code § 107 - Limitations on exclusive rights: Fair use
Notwithstanding the provisions of sections 106 and 106A, the fair use of a copyrighted work, including such use by reproduction in copies or phonorecords or by any other means specified by that section, for purposes such as criticism, comment, news reporting, teaching (including multiple copies for classroom use), scholarship, or research, is not an infringement of copyright.
Accenture 2015 Global Risk Management Study: Insurance Report Key Findings an...

Representing life, property & casualty and reinsurance, some 150 insurance risk leaders participated in Accenture’s 2015 Global Risk Management Study: Insurance Report. See how these leaders are working to systematically operationalize risk management.
Security Incident Response Readiness Survey 

Jaspreet Singh, Partner, Cybersecurity, Advisory Services, EY India
Similar to Ernst & Young visuals security survey 2012 (20)
Cyber security: Five leadership issues worthy of board and executive attention

Cyber security: Five leadership issues worthy of board and executive attention
Cyber security: five leadership issues worthy of Board and executive attention

Cyber security: five leadership issues worthy of Board and executive attention
Build a Business-Driven IT Risk Management Program

Build a Business-Driven IT Risk Management Program
Breaches Are Bad for Business. How Will You Detect and Respond to Your Next C...

Breaches Are Bad for Business. How Will You Detect and Respond to Your Next C...
2014 Executive Breach Preparedness Research Report

2014 Executive Breach Preparedness Research Report
Insights from the IBM Chief Information Security Officer Assessment

Insights from the IBM Chief Information Security Officer Assessment
Government and Education Webinar: Public Sector Cybersecurity Survey - What I...

Government and Education Webinar: Public Sector Cybersecurity Survey - What I...
01-Build-an-IT-Risk-Management-Program--Phases-1-3.pptx

01-Build-an-IT-Risk-Management-Program--Phases-1-3.pptx
ESG TechTruth: Advanced Persistent Threat: The Pervasive IT Security Skills S...

ESG TechTruth: Advanced Persistent Threat: The Pervasive IT Security Skills S...
Cyber Security in the Digital Age: A Survey and its Analysis

Cyber Security in the Digital Age: A Survey and its Analysis
5 Questions Executives Should Be Asking Their Security Teams 

5 Questions Executives Should Be Asking Their Security Teams
Accenture 2015 Global Risk Management Study: Insurance Report Key Findings an...

Accenture 2015 Global Risk Management Study: Insurance Report Key Findings an...
Recently uploaded
Search and Society: Reimagining Information Access for Radical Futures

The field of Information retrieval (IR) is currently undergoing a transformative shift, at least partly due to the emerging applications of generative AI to information access. In this talk, we will deliberate on the sociotechnical implications of generative AI for information access. We will argue that there is both a critical necessity and an exciting opportunity for the IR community to re-center our research agendas on societal needs while dismantling the artificial separation between the work on fairness, accountability, transparency, and ethics in IR and the rest of IR research. Instead of adopting a reactionary strategy of trying to mitigate potential social harms from emerging technologies, the community should aim to proactively set the research agenda for the kinds of systems we should build inspired by diverse explicitly stated sociotechnical imaginaries. The sociotechnical imaginaries that underpin the design and development of information access technologies needs to be explicitly articulated, and we need to develop theories of change in context of these diverse perspectives. Our guiding future imaginaries must be informed by other academic fields, such as democratic theory and critical theory, and should be co-developed with social science scholars, legal scholars, civil rights and social justice activists, and artists, among others.
JMeter webinar - integration with InfluxDB and Grafana

Watch this recorded webinar about real-time monitoring of application performance. See how to integrate Apache JMeter, the open-source leader in performance testing, with InfluxDB, the open-source time-series database, and Grafana, the open-source analytics and visualization application.
In this webinar, we will review the benefits of leveraging InfluxDB and Grafana when executing load tests and demonstrate how these tools are used to visualize performance metrics.
Length: 30 minutes
Session Overview
-------------------------------------------
During this webinar, we will cover the following topics while demonstrating the integrations of JMeter, InfluxDB and Grafana:
- What out-of-the-box solutions are available for real-time monitoring JMeter tests?
- What are the benefits of integrating InfluxDB and Grafana into the load testing stack?
- Which features are provided by Grafana?
- Demonstration of InfluxDB and Grafana using a practice web application
To view the webinar recording, go to:
https://www.rttsweb.com/jmeter-integration-webinar
How world-class product teams are winning in the AI era by CEO and Founder, P...

How world-class product teams are winning in the AI era by CEO and Founder, Product School
The Art of the Pitch: WordPress Relationships and Sales

Clients don’t know what they don’t know. What web solutions are right for them? How does WordPress come into the picture? How do you make sure you understand scope and timeline? What do you do if sometime changes?
All these questions and more will be explored as we talk about matching clients’ needs with what your agency offers without pulling teeth or pulling your hair out. Practical tips, and strategies for successful relationship building that leads to closing the deal.
To Graph or Not to Graph Knowledge Graph Architectures and LLMs

Reflecting on new architectures for knowledge based systems in light of generative ai
Designing Great Products: The Power of Design and Leadership by Chief Designe...

Designing Great Products: The Power of Design and Leadership by Chief Designer, Beats by Dr Dre
UiPath Test Automation using UiPath Test Suite series, part 4

Welcome to UiPath Test Automation using UiPath Test Suite series part 4. In this session, we will cover Test Manager overview along with SAP heatmap.
The UiPath Test Manager overview with SAP heatmap webinar offers a concise yet comprehensive exploration of the role of a Test Manager within SAP environments, coupled with the utilization of heatmaps for effective testing strategies.
Participants will gain insights into the responsibilities, challenges, and best practices associated with test management in SAP projects. Additionally, the webinar delves into the significance of heatmaps as a visual aid for identifying testing priorities, areas of risk, and resource allocation within SAP landscapes. Through this session, attendees can expect to enhance their understanding of test management principles while learning practical approaches to optimize testing processes in SAP environments using heatmap visualization techniques
What will you get from this session?
1. Insights into SAP testing best practices
2. Heatmap utilization for testing
3. Optimization of testing processes
4. Demo
Topics covered:
Execution from the test manager
Orchestrator execution result
Defect reporting
SAP heatmap example with demo
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
When stars align: studies in data quality, knowledge graphs, and machine lear...

Keynote at DQMLKG workshop at the 21st European Semantic Web Conference 2024
Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...

💥 Speed, accuracy, and scaling – discover the superpowers of GenAI in action with UiPath Document Understanding and Communications Mining™:
See how to accelerate model training and optimize model performance with active learning
Learn about the latest enhancements to out-of-the-box document processing – with little to no training required
Get an exclusive demo of the new family of UiPath LLMs – GenAI models specialized for processing different types of documents and messages
This is a hands-on session specifically designed for automation developers and AI enthusiasts seeking to enhance their knowledge in leveraging the latest intelligent document processing capabilities offered by UiPath.
Speakers:
👨🏫 Andras Palfi, Senior Product Manager, UiPath
👩🏫 Lenka Dulovicova, Product Program Manager, UiPath
Transcript: Selling digital books in 2024: Insights from industry leaders - T...

The publishing industry has been selling digital audiobooks and ebooks for over a decade and has found its groove. What’s changed? What has stayed the same? Where do we go from here? Join a group of leading sales peers from across the industry for a conversation about the lessons learned since the popularization of digital books, best practices, digital book supply chain management, and more.
Link to video recording: https://bnctechforum.ca/sessions/selling-digital-books-in-2024-insights-from-industry-leaders/
Presented by BookNet Canada on May 28, 2024, with support from the Department of Canadian Heritage.
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar
Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...

Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI)
LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...

Do you want to learn how to model and simulate an electrical network from scratch in under an hour?
Then welcome to this PowSyBl workshop, hosted by Rte, the French Transmission System Operator (TSO)!
During the webinar, you will discover the PowSyBl ecosystem as well as handle and study an electrical network through an interactive Python notebook.
PowSyBl is an open source project hosted by LF Energy, which offers a comprehensive set of features for electrical grid modelling and simulation. Among other advanced features, PowSyBl provides:
- A fully editable and extendable library for grid component modelling;
- Visualization tools to display your network;
- Grid simulation tools, such as power flows, security analyses (with or without remedial actions) and sensitivity analyses;
The framework is mostly written in Java, with a Python binding so that Python developers can access PowSyBl functionalities as well.
What you will learn during the webinar:
- For beginners: discover PowSyBl's functionalities through a quick general presentation and the notebook, without needing any expert coding skills;
- For advanced developers: master the skills to efficiently apply PowSyBl functionalities to your real-world scenarios.
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

Effective Application Security in Software Delivery lifecycle using Deployment Firewall and DBOM
The modern software delivery process (or the CI/CD process) includes many tools, distributed teams, open-source code, and cloud platforms. Constant focus on speed to release software to market, along with the traditional slow and manual security checks has caused gaps in continuous security as an important piece in the software supply chain. Today organizations feel more susceptible to external and internal cyber threats due to the vast attack surface in their applications supply chain and the lack of end-to-end governance and risk management.
The software team must secure its software delivery process to avoid vulnerability and security breaches. This needs to be achieved with existing tool chains and without extensive rework of the delivery processes. This talk will present strategies and techniques for providing visibility into the true risk of the existing vulnerabilities, preventing the introduction of security issues in the software, resolving vulnerabilities in production environments quickly, and capturing the deployment bill of materials (DBOM).
Speakers:
Bob Boule
Robert Boule is a technology enthusiast with PASSION for technology and making things work along with a knack for helping others understand how things work. He comes with around 20 years of solution engineering experience in application security, software continuous delivery, and SaaS platforms. He is known for his dynamic presentations in CI/CD and application security integrated in software delivery lifecycle.
Gopinath Rebala
Gopinath Rebala is the CTO of OpsMx, where he has overall responsibility for the machine learning and data processing architectures for Secure Software Delivery. Gopi also has a strong connection with our customers, leading design and architecture for strategic implementations. Gopi is a frequent speaker and well-known leader in continuous delivery and integrating security into software delivery.
Bits & Pixels using AI for Good.........

A whirlwind tour of tech & AI for socio-environmental impact.
Accelerate your Kubernetes clusters with Varnish Caching

A presentation about the usage and availability of Varnish on Kubernetes. This talk explores the capabilities of Varnish caching and shows how to use the Varnish Helm chart to deploy it to Kubernetes.
This presentation was delivered at K8SUG Singapore. See https://feryn.eu/presentations/accelerate-your-kubernetes-clusters-with-varnish-caching-k8sug-singapore-28-2024 for more details.
Essentials of Automations: Optimizing FME Workflows with Parameters

Are you looking to streamline your workflows and boost your projects’ efficiency? Do you find yourself searching for ways to add flexibility and control over your FME workflows? If so, you’re in the right place.
Join us for an insightful dive into the world of FME parameters, a critical element in optimizing workflow efficiency. This webinar marks the beginning of our three-part “Essentials of Automation” series. This first webinar is designed to equip you with the knowledge and skills to utilize parameters effectively: enhancing the flexibility, maintainability, and user control of your FME projects.
Here’s what you’ll gain:
- Essentials of FME Parameters: Understand the pivotal role of parameters, including Reader/Writer, Transformer, User, and FME Flow categories. Discover how they are the key to unlocking automation and optimization within your workflows.
- Practical Applications in FME Form: Delve into key user parameter types including choice, connections, and file URLs. Allow users to control how a workflow runs, making your workflows more reusable. Learn to import values and deliver the best user experience for your workflows while enhancing accuracy.
- Optimization Strategies in FME Flow: Explore the creation and strategic deployment of parameters in FME Flow, including the use of deployment and geometry parameters, to maximize workflow efficiency.
- Pro Tips for Success: Gain insights on parameterizing connections and leveraging new features like Conditional Visibility for clarity and simplicity.
We’ll wrap up with a glimpse into future webinars, followed by a Q&A session to address your specific questions surrounding this topic.
Don’t miss this opportunity to elevate your FME expertise and drive your projects to new heights of efficiency.
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic (NeSy) AI is on the rise. However, simply machine learning on just any symbolic structure is not sufficient to really harvest the gains of NeSy. These will only be gained when the symbolic structures have an actual semantics. I give an operational definition of semantics as “predictable inference”.
All of this illustrated with link prediction over knowledge graphs, but the argument is general.
Recently uploaded (20)
Search and Society: Reimagining Information Access for Radical Futures

Search and Society: Reimagining Information Access for Radical Futures
JMeter webinar - integration with InfluxDB and Grafana

JMeter webinar - integration with InfluxDB and Grafana
How world-class product teams are winning in the AI era by CEO and Founder, P...

How world-class product teams are winning in the AI era by CEO and Founder, P...
The Art of the Pitch: WordPress Relationships and Sales

The Art of the Pitch: WordPress Relationships and Sales
To Graph or Not to Graph Knowledge Graph Architectures and LLMs

To Graph or Not to Graph Knowledge Graph Architectures and LLMs
Designing Great Products: The Power of Design and Leadership by Chief Designe...

Designing Great Products: The Power of Design and Leadership by Chief Designe...
UiPath Test Automation using UiPath Test Suite series, part 4

UiPath Test Automation using UiPath Test Suite series, part 4
When stars align: studies in data quality, knowledge graphs, and machine lear...

When stars align: studies in data quality, knowledge graphs, and machine lear...
Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...

Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...
Transcript: Selling digital books in 2024: Insights from industry leaders - T...

Transcript: Selling digital books in 2024: Insights from industry leaders - T...
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf
Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...

Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...
LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...

LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...
FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf

FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf
Accelerate your Kubernetes clusters with Varnish Caching

Accelerate your Kubernetes clusters with Varnish Caching
Essentials of Automations: Optimizing FME Workflows with Parameters

Essentials of Automations: Optimizing FME Workflows with Parameters
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic is not enough, we need neuro-*semantic*
Ernst & Young visuals security survey 2012
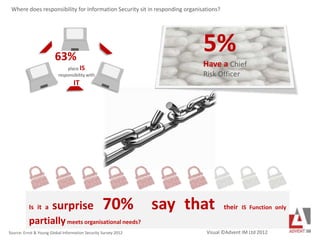
- 1. 63% place IS responsibility with IT 5% Have a Chief Risk Officer Source: Ernst & Young Global Information Security Survey 2012 Where does responsibility for Information Security sit in responding organisations? Is it a surprise 70% say that their IS Function only partiallymeets organisational needs? Visual ©Advent IM Ltd 2012
- 2. 46% neveror almost never discuss Information Security at top governing structure of their organisation 56% 42% 38% aligned to IT Strategyaligned to Business Strategyaligned to Risk Appetit how is Information Security aligned in your organisation?
- 3. planned spend increase of 5-15% planned spend increase of 25% or more With so little boardroom involvement and so little specialist security resourcing, how will any additional spending be effectively appropriately controlled?
- 4. 63% place IS responsibility with IT 5% Have a Chief Risk Officer Source: Ernst & Young Global Information Security Survey 2012 Where does responsibility for Information Security sit in responding organisations? Is it a surprise 70% say that their IS Function only partiallymeets organisational needs?
