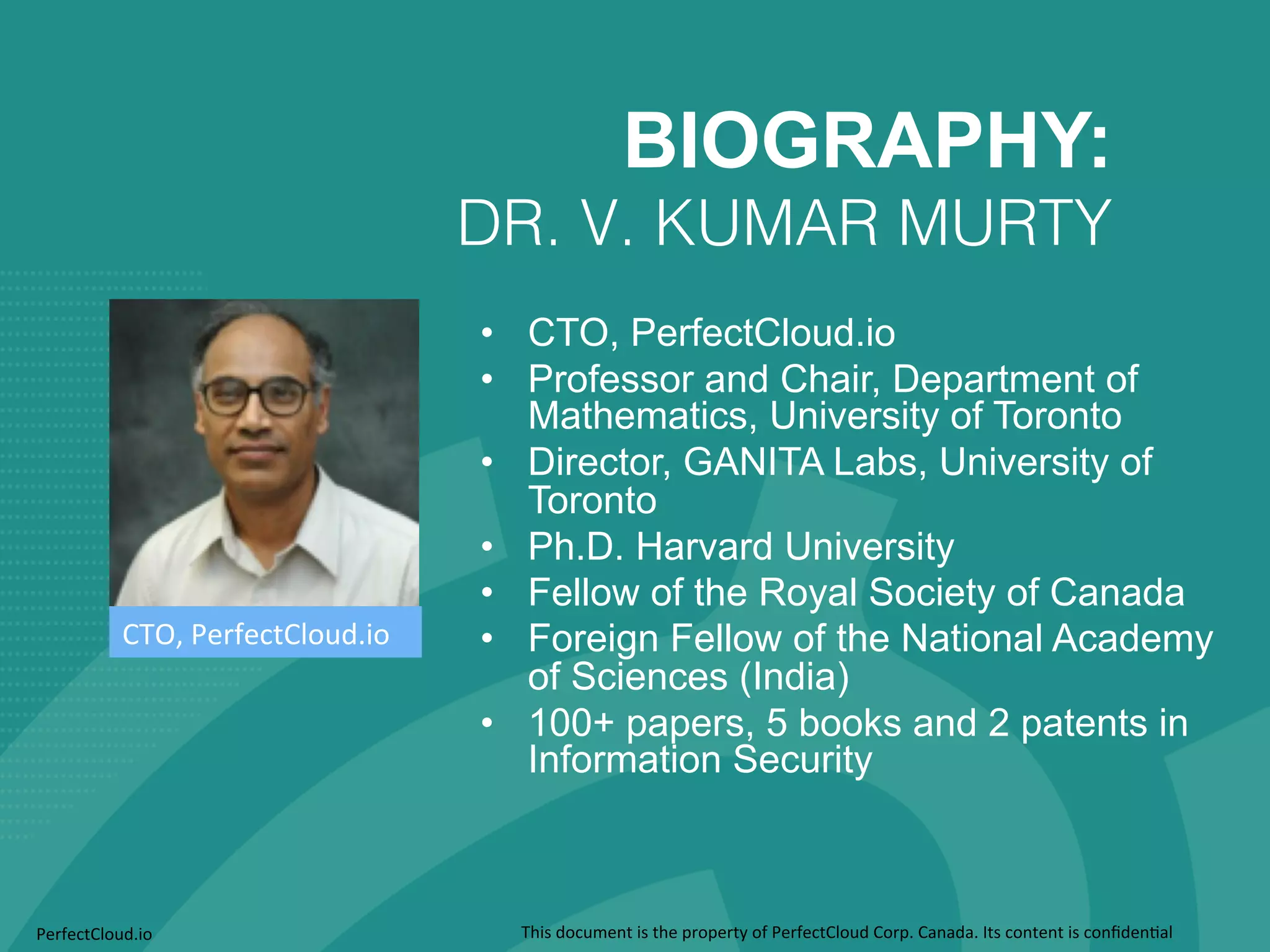
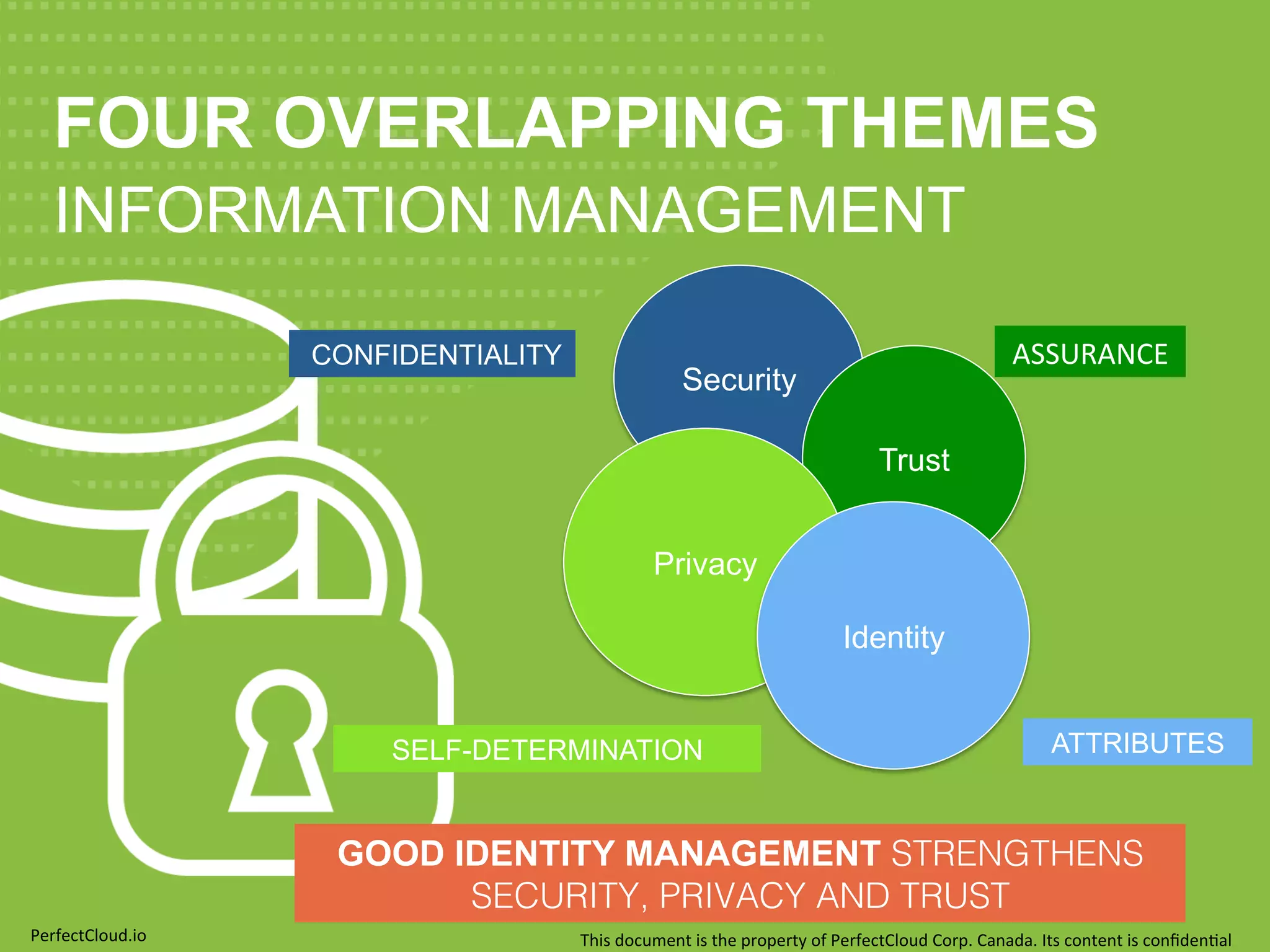
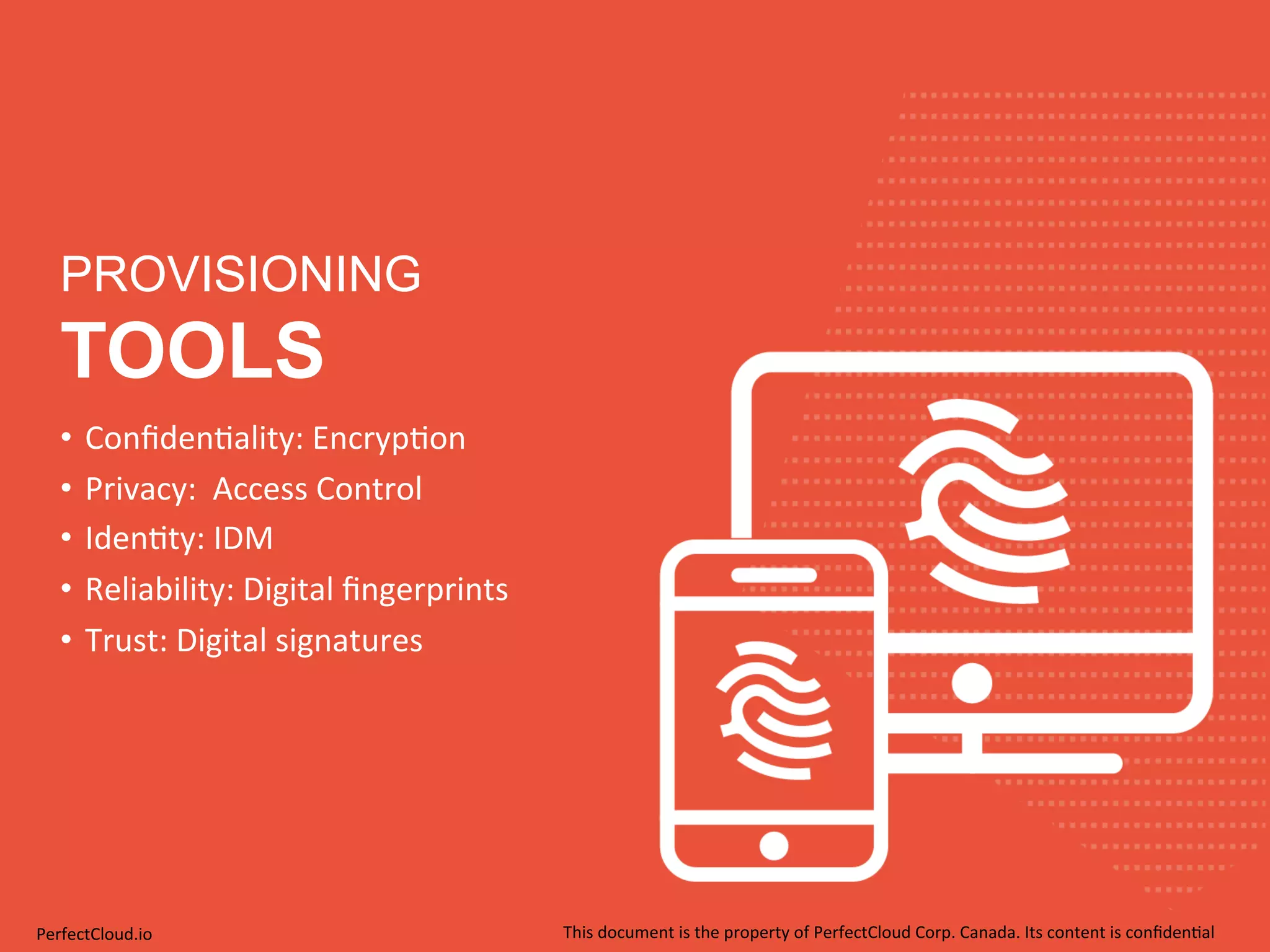
Dr. V. Kumar Murty is the CTO of Perfect Cloud Corp. He has extensive experience in information security as a professor at the University of Toronto, with over 100 papers published. The document discusses concepts related to data security including encryption algorithms, identity management, and the importance of both technology and policies for protecting data throughout its lifecycle.