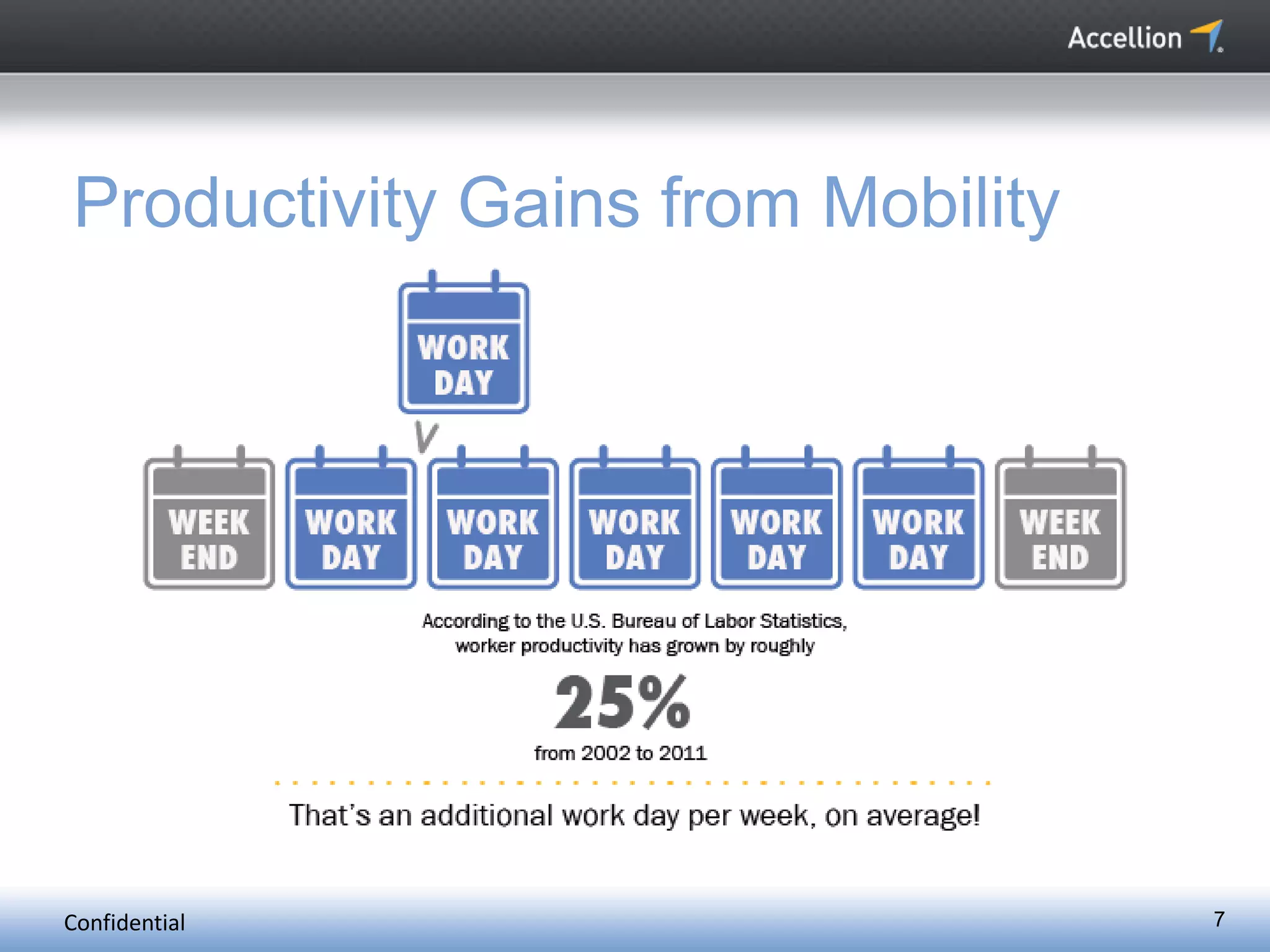
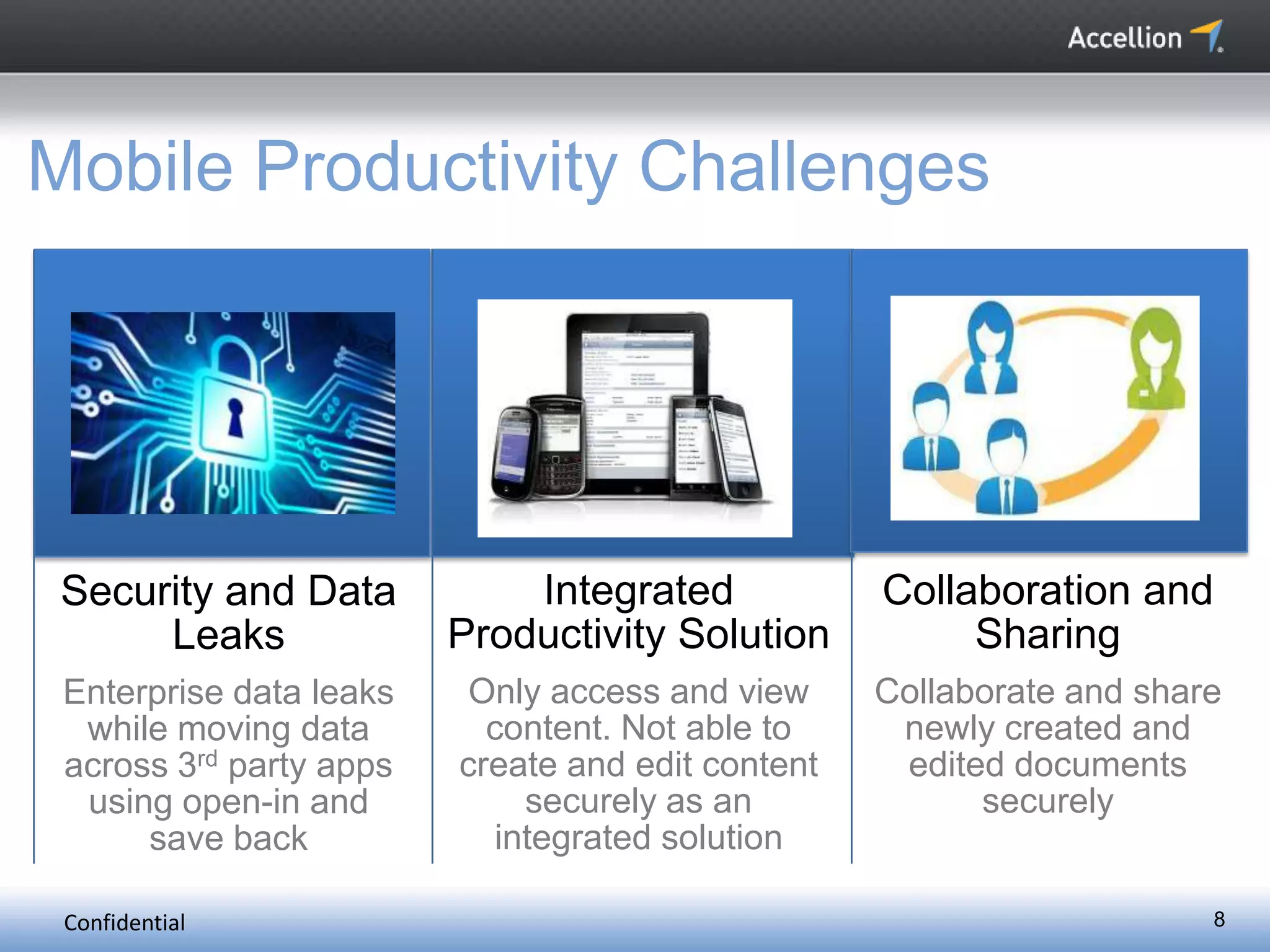
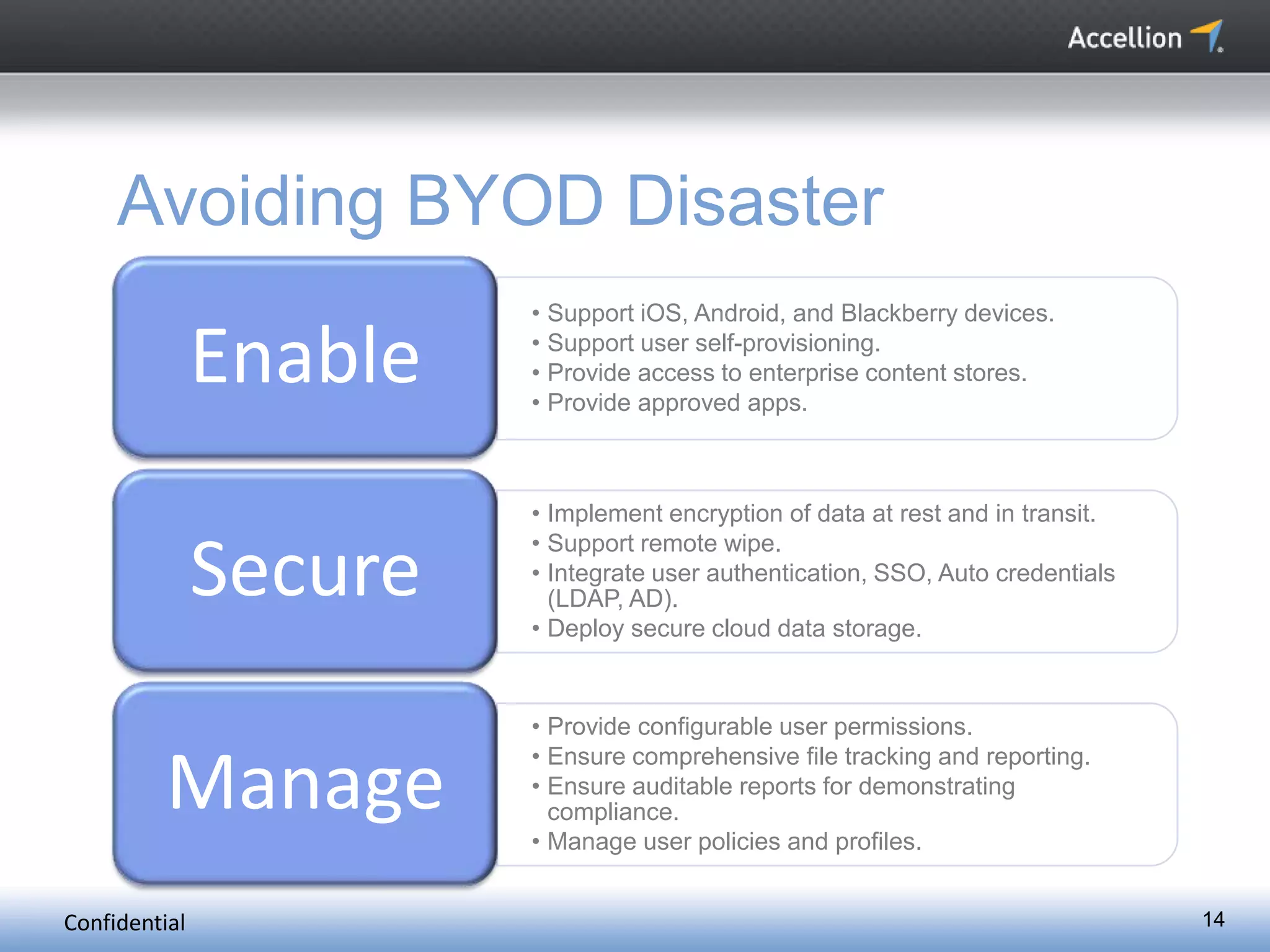
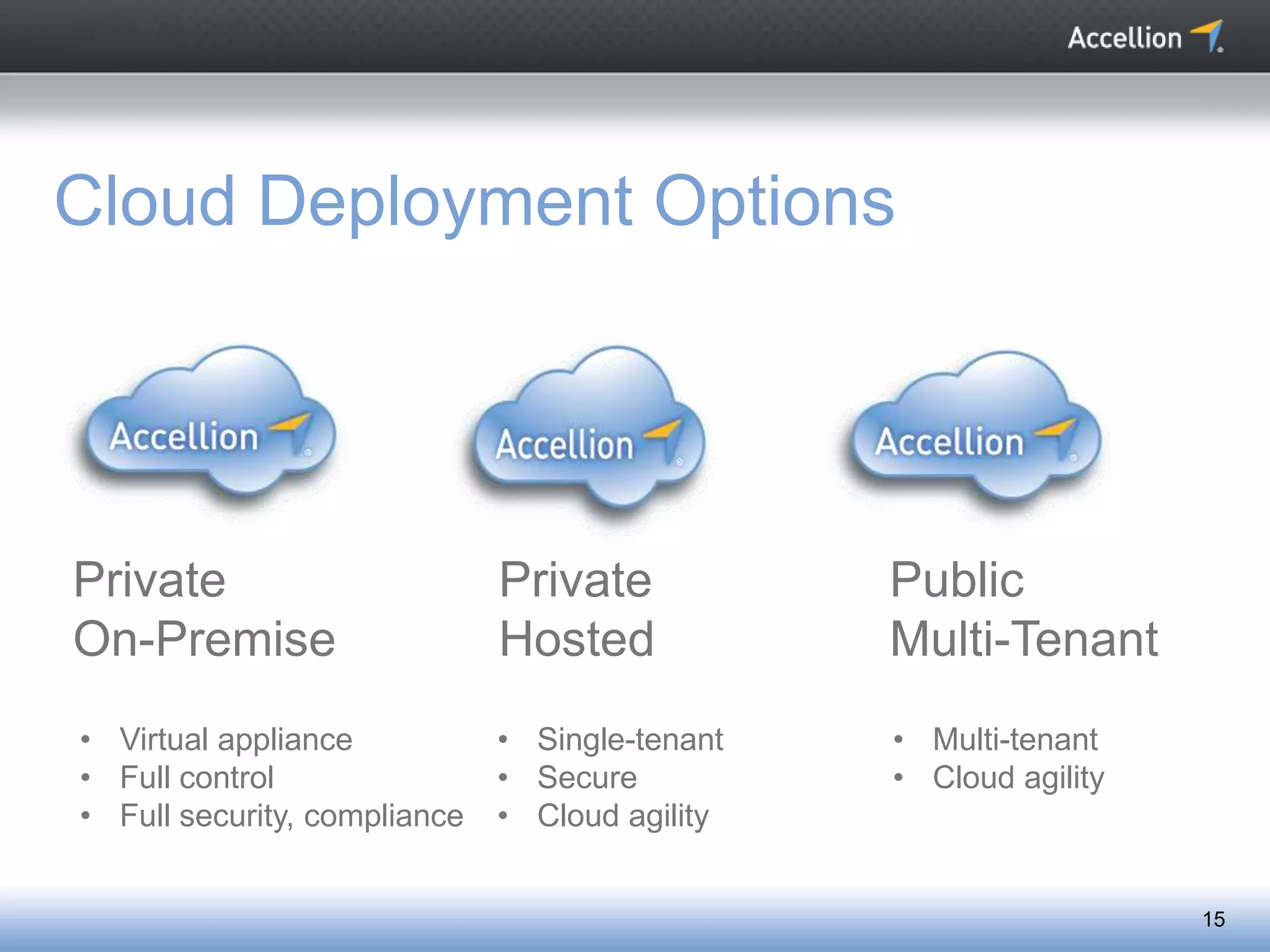
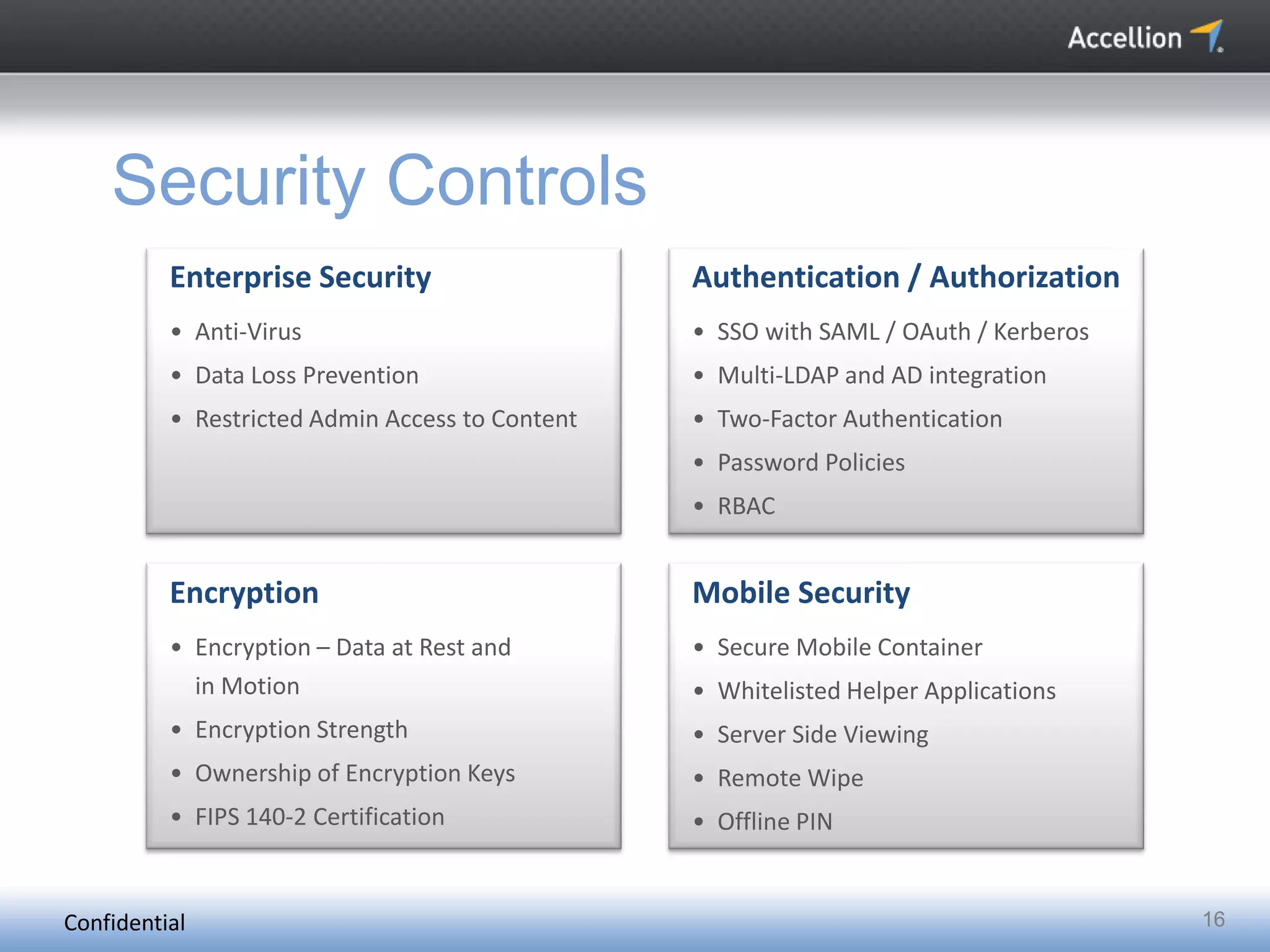
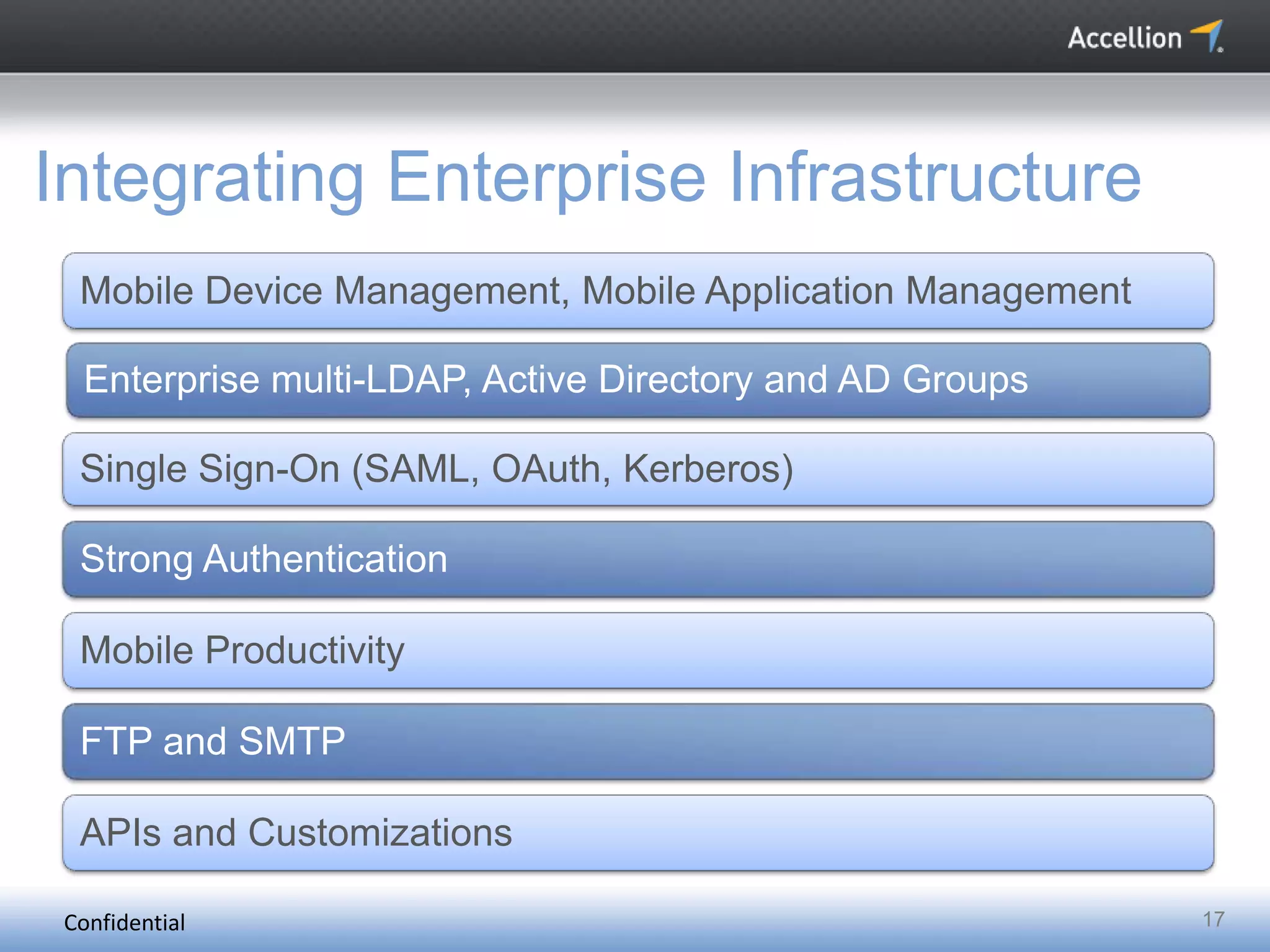
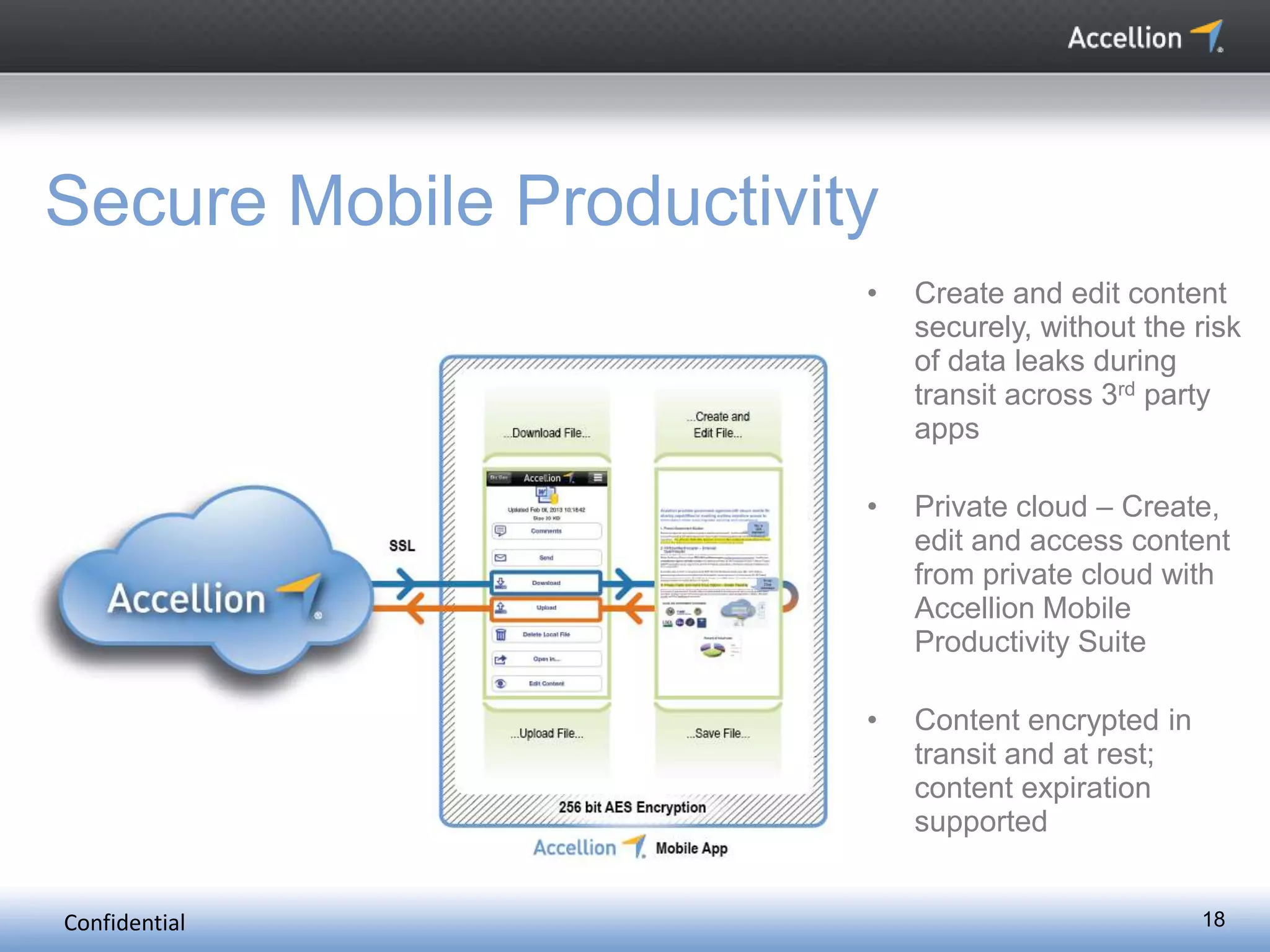
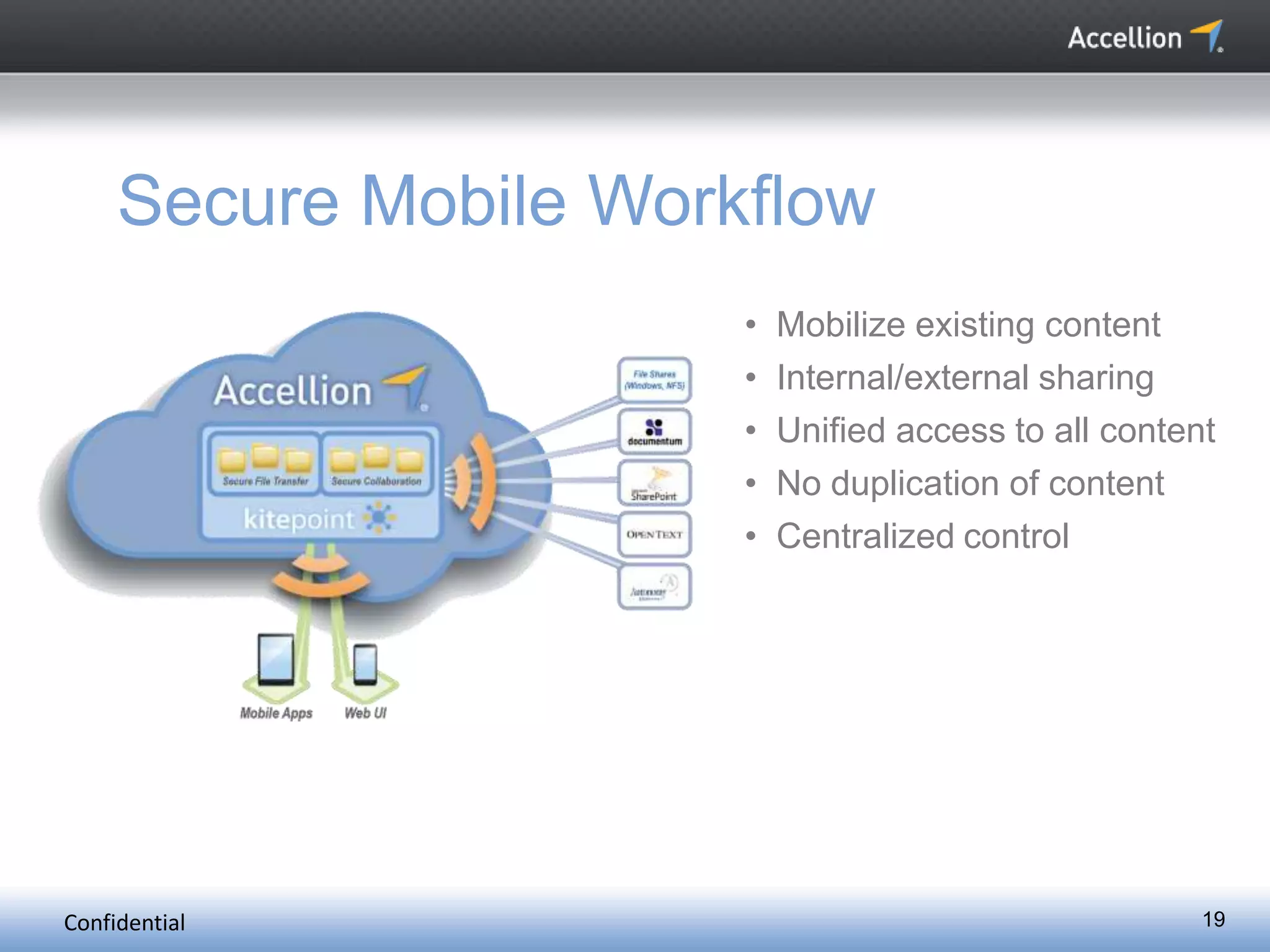
The document discusses the challenges and solutions for secure mobile collaboration, emphasizing the need for effective enterprise content management amid the rise of mobile devices. It outlines Accellion's secure mobile file-sharing solutions aimed at safeguarding enterprise data while promoting productivity. Key strategies include implementing strong security measures, supporting BYOD policies, and maintaining control over data access and sharing.