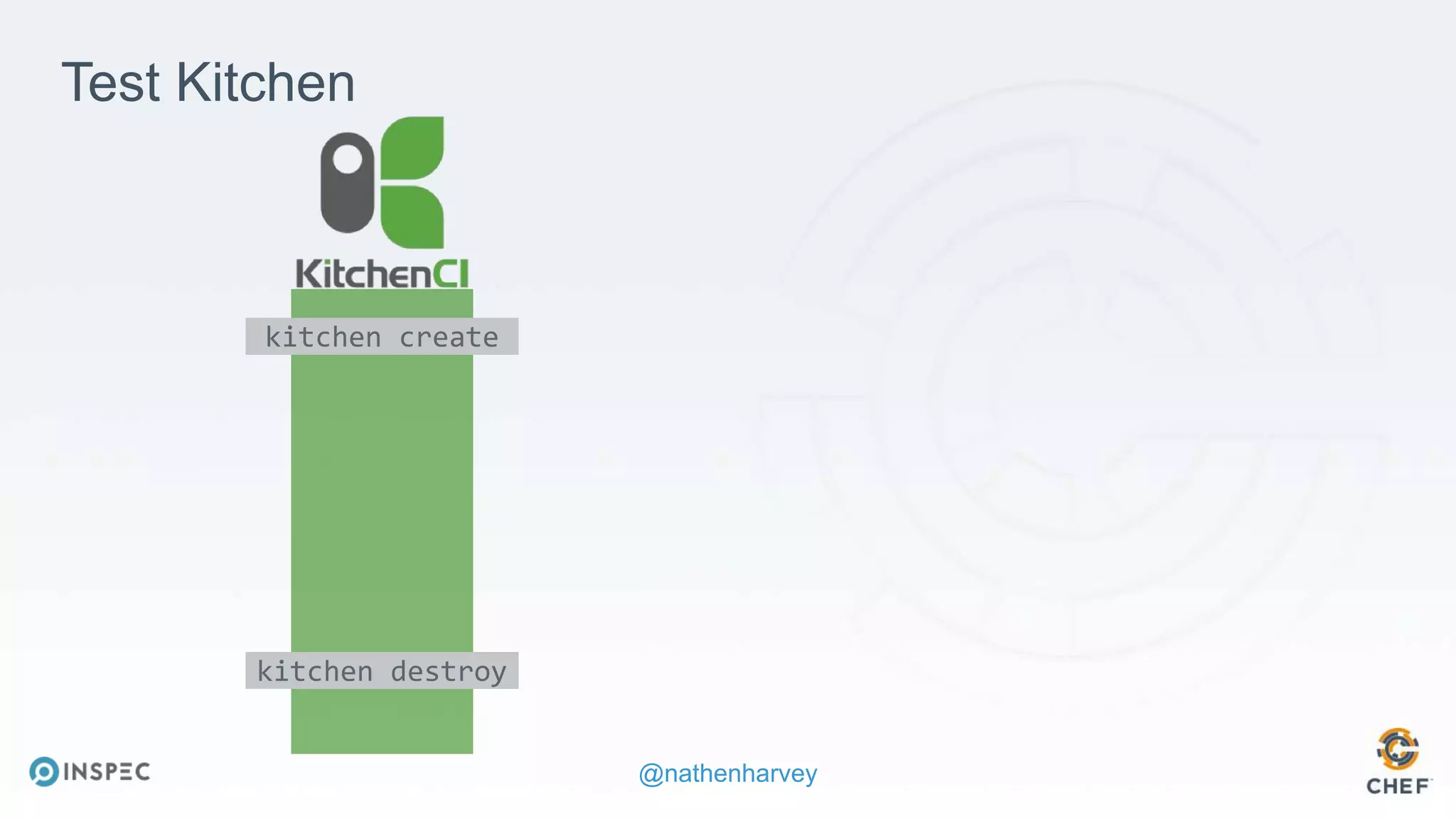
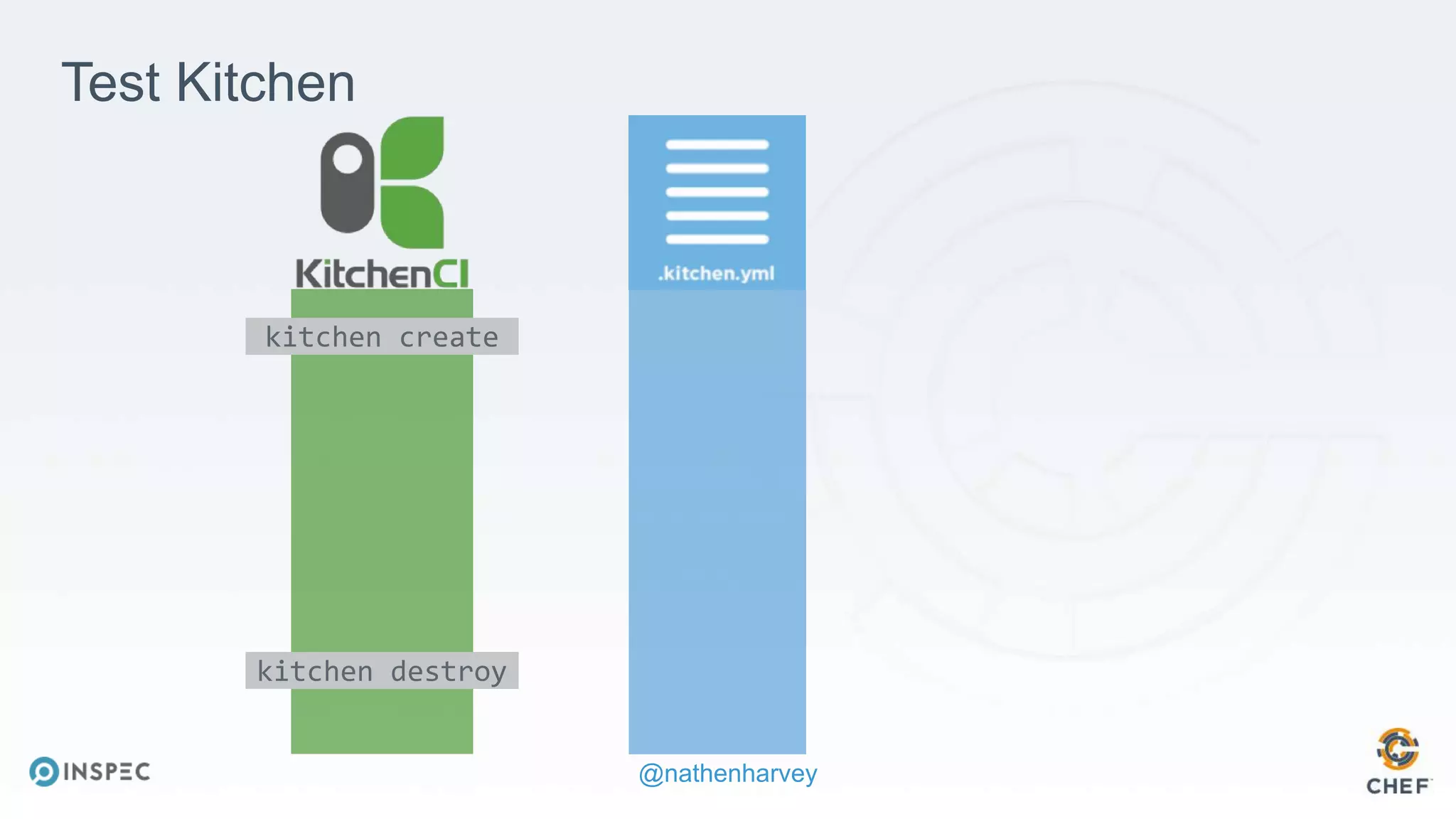
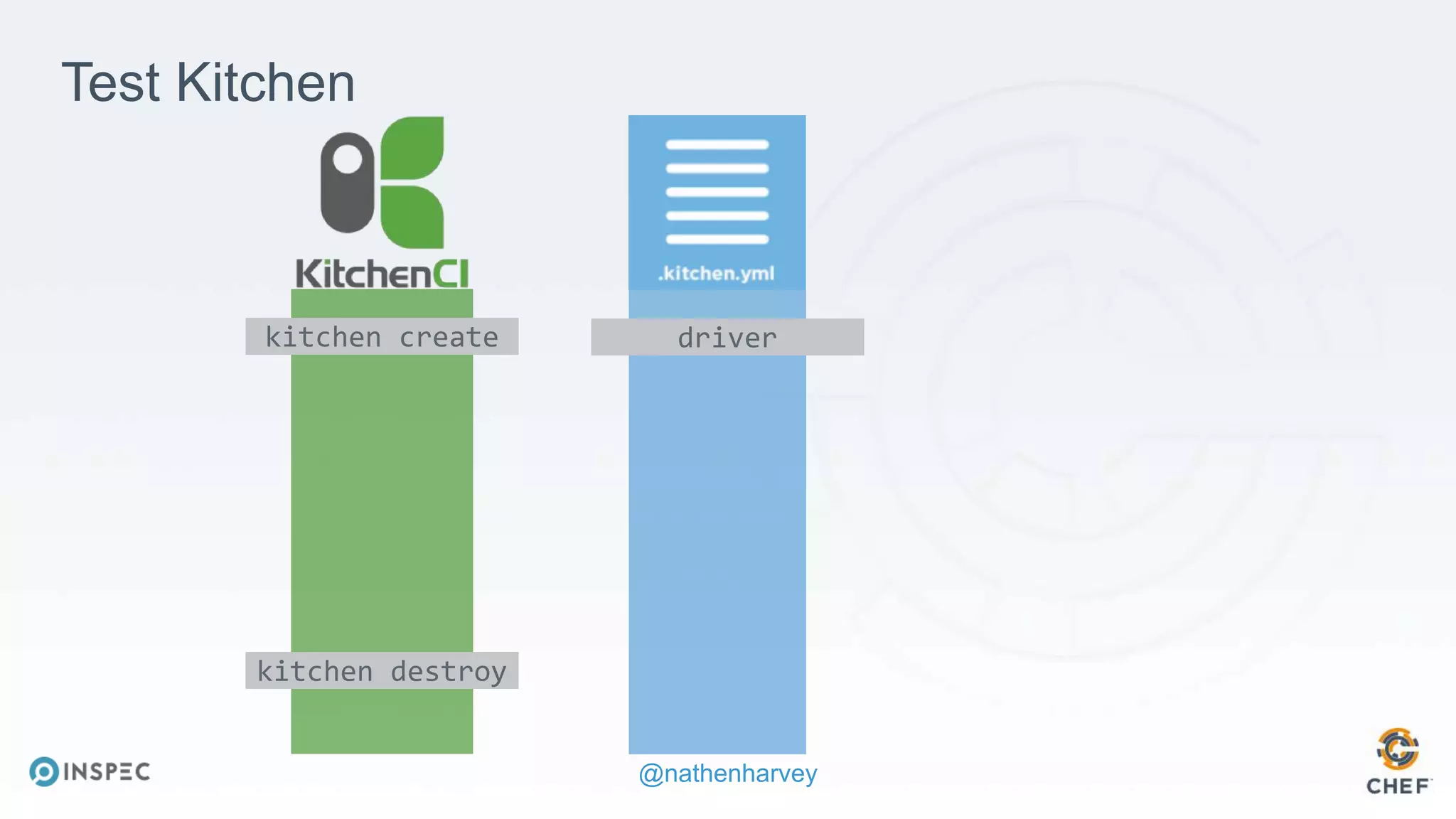
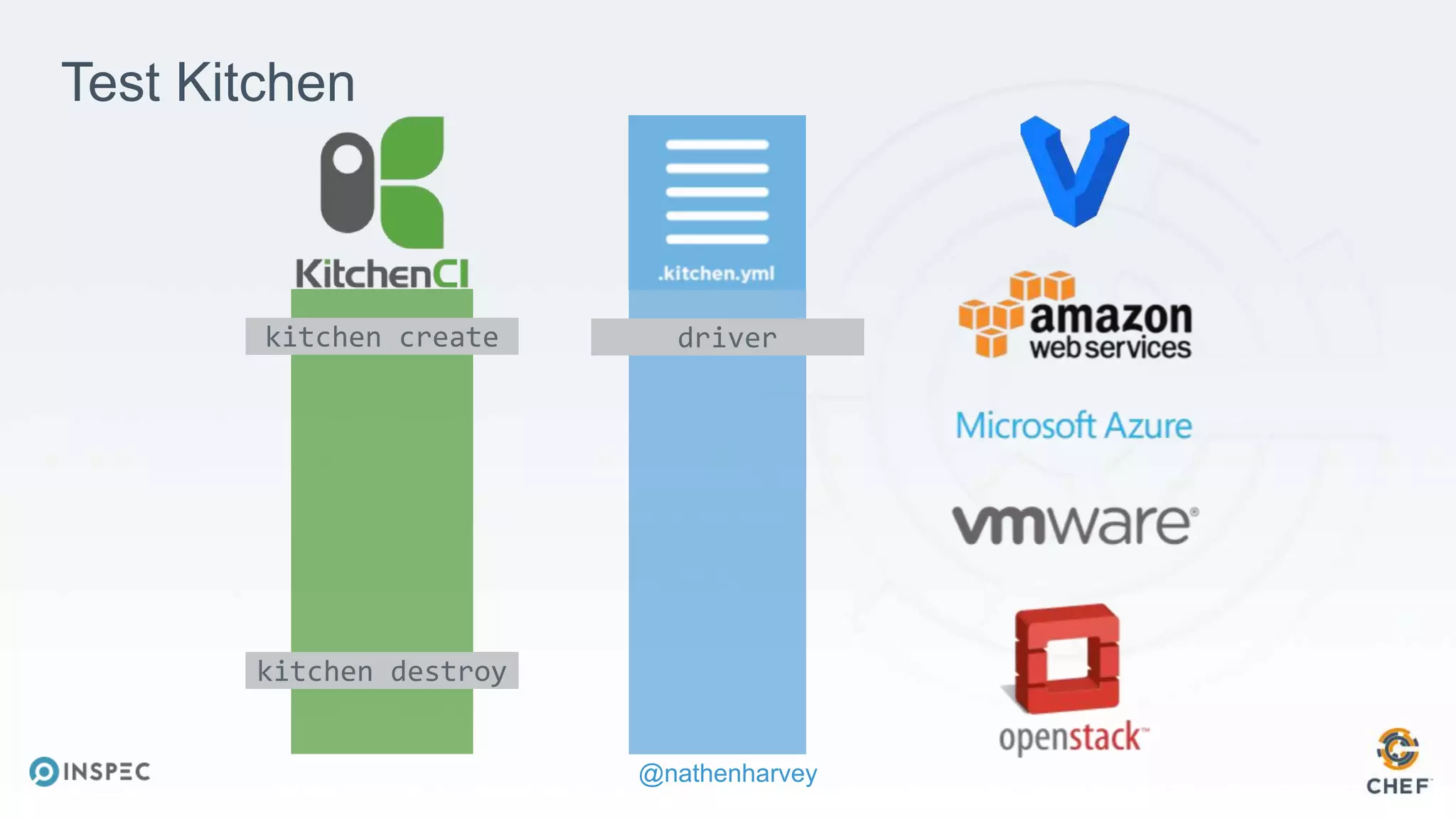
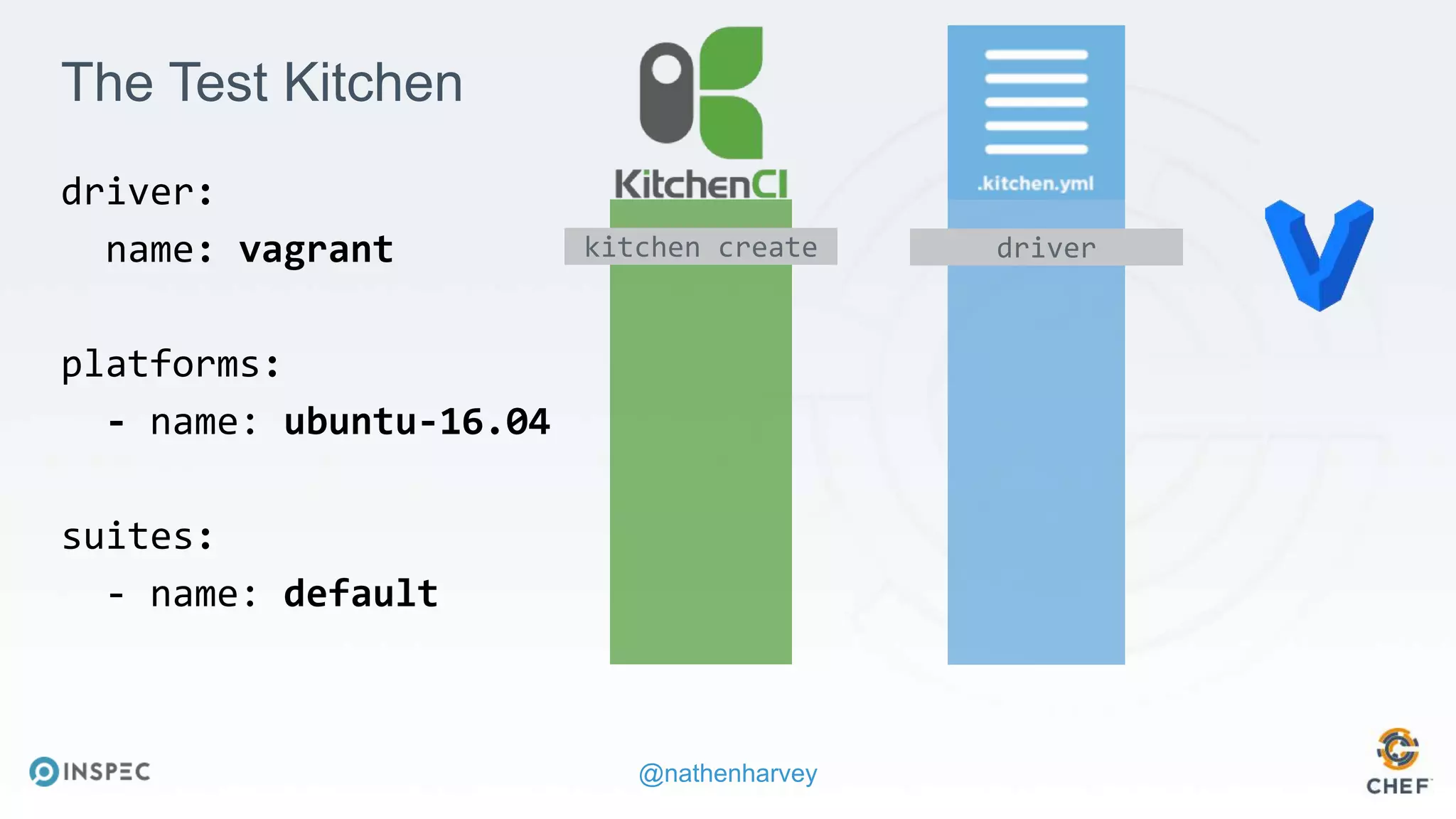
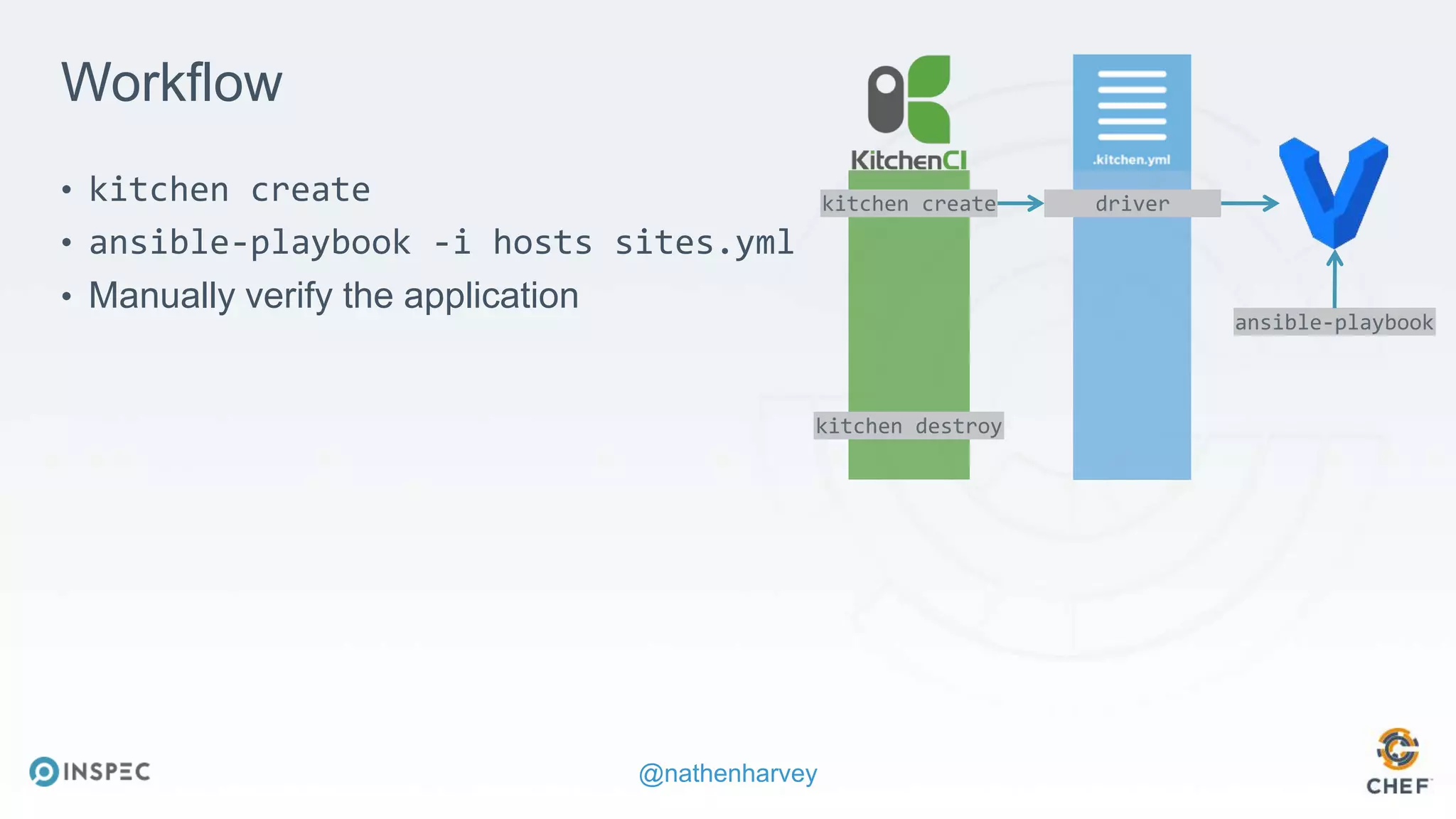
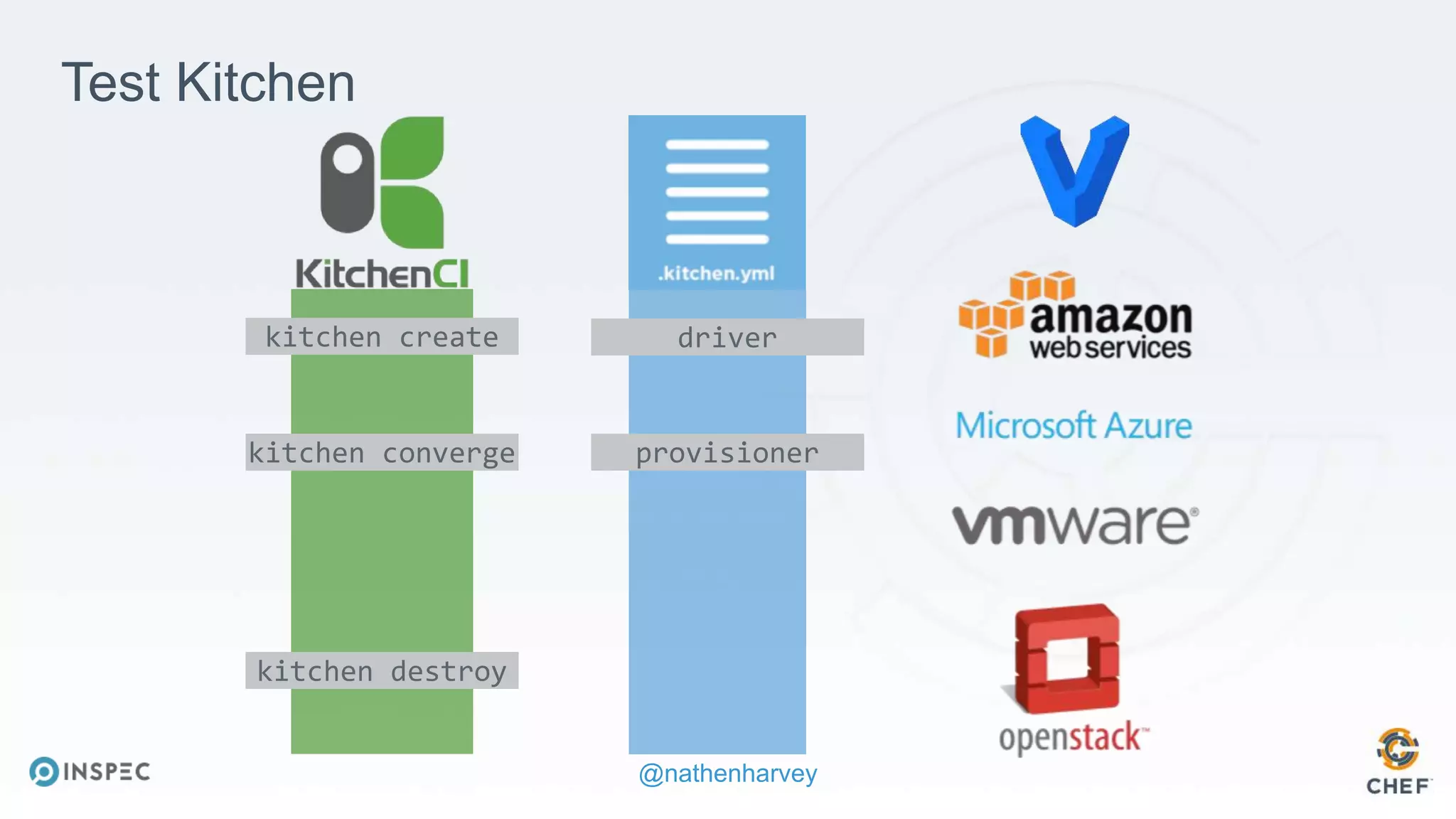
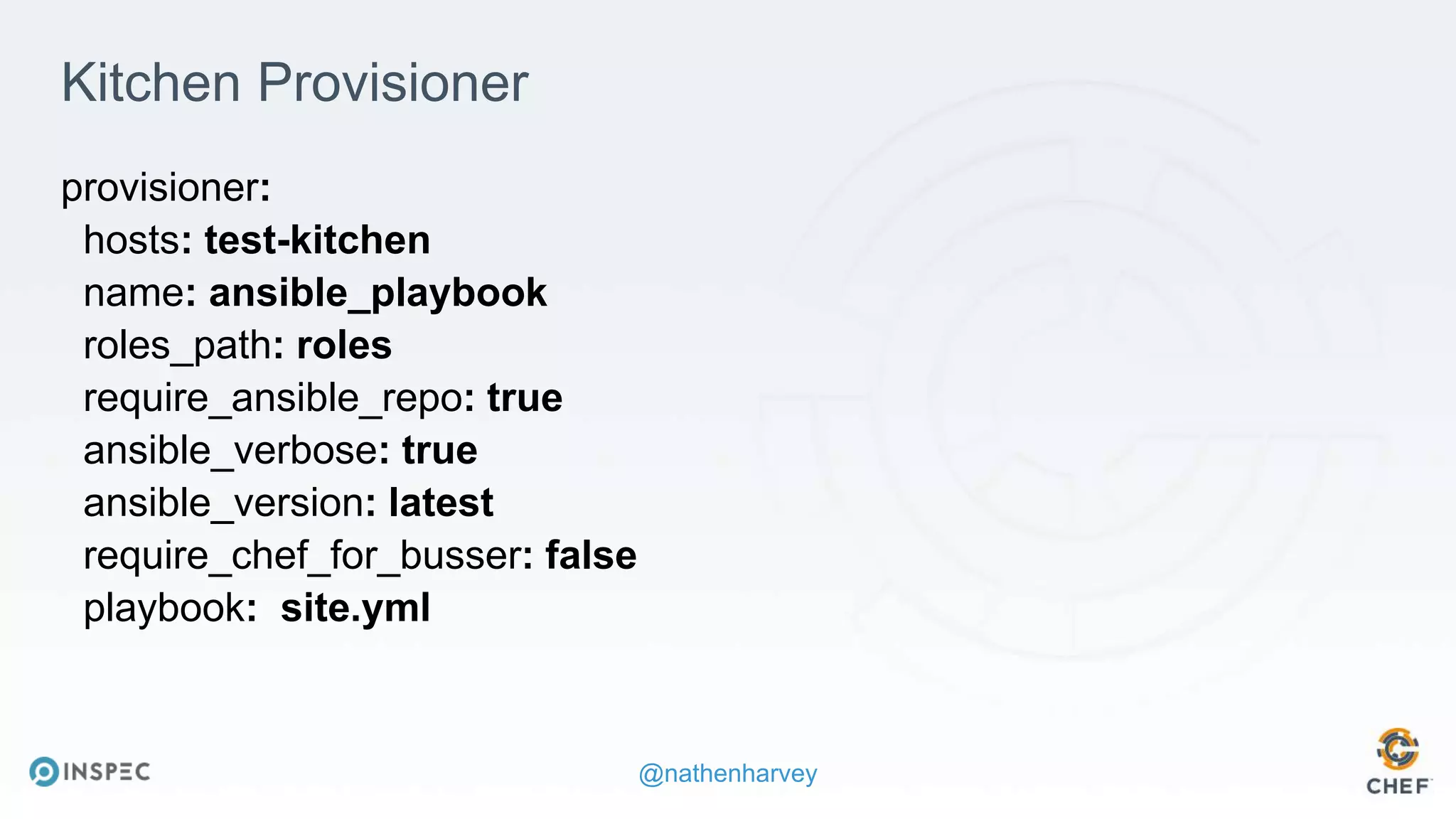
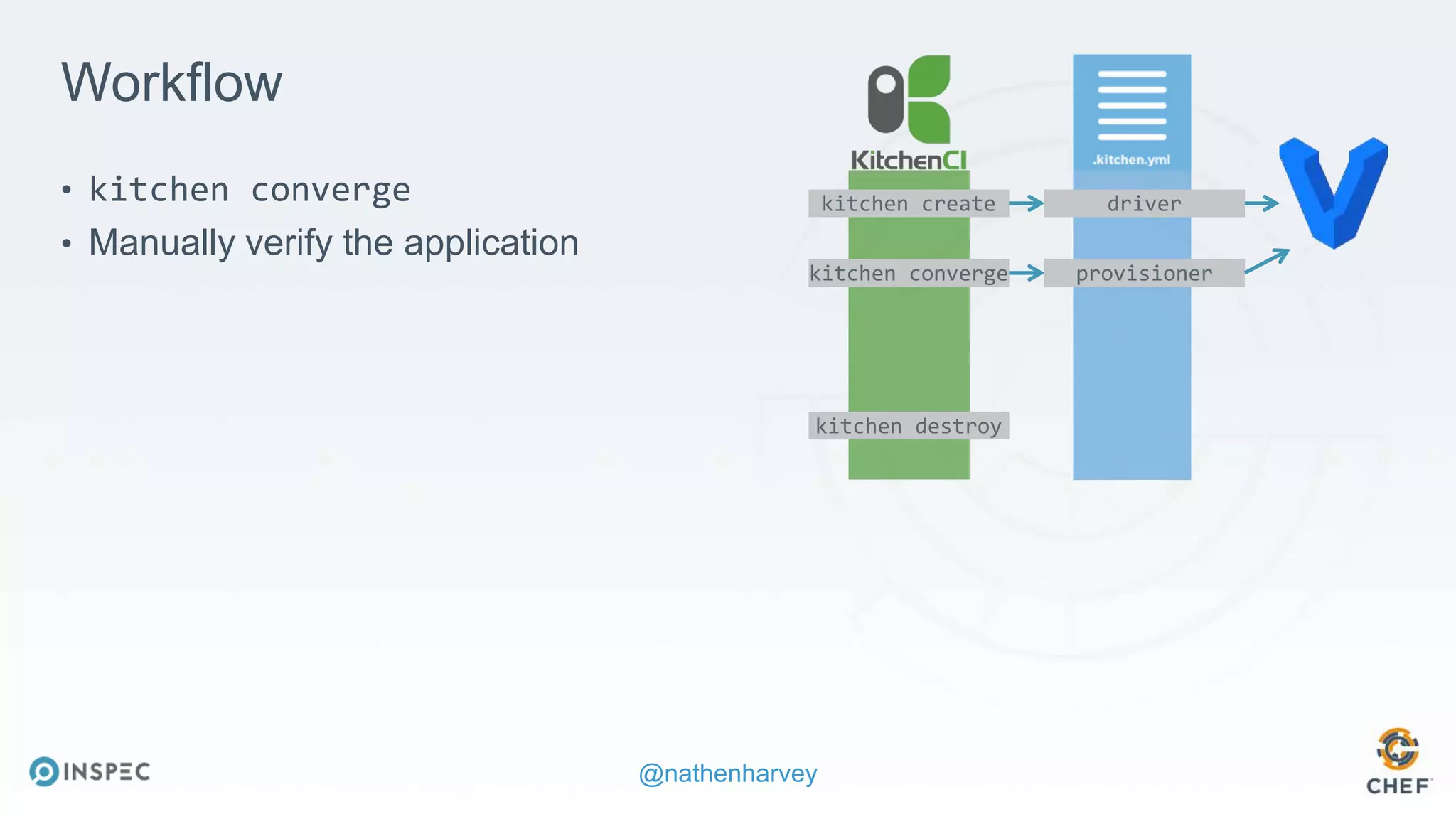
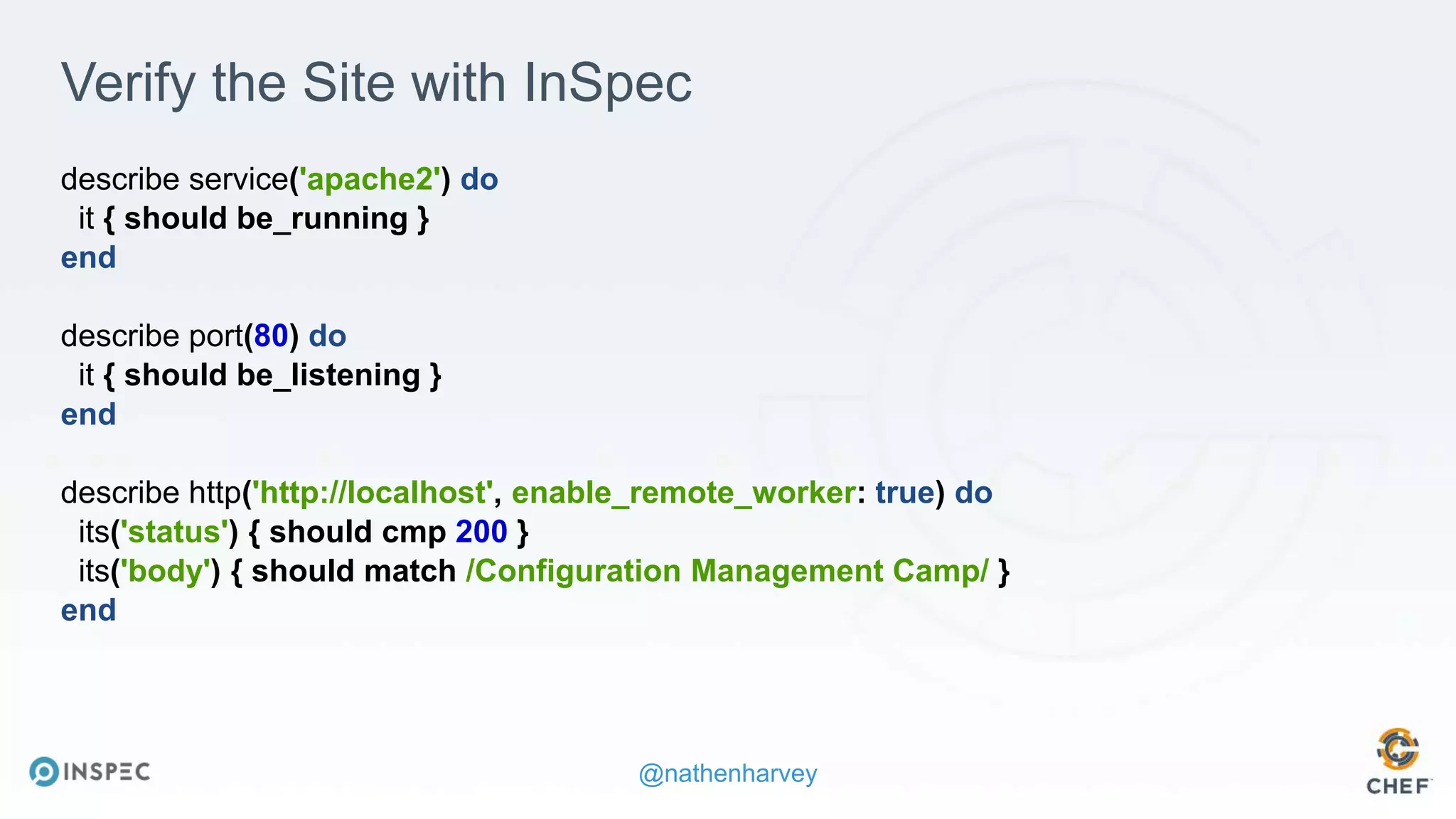
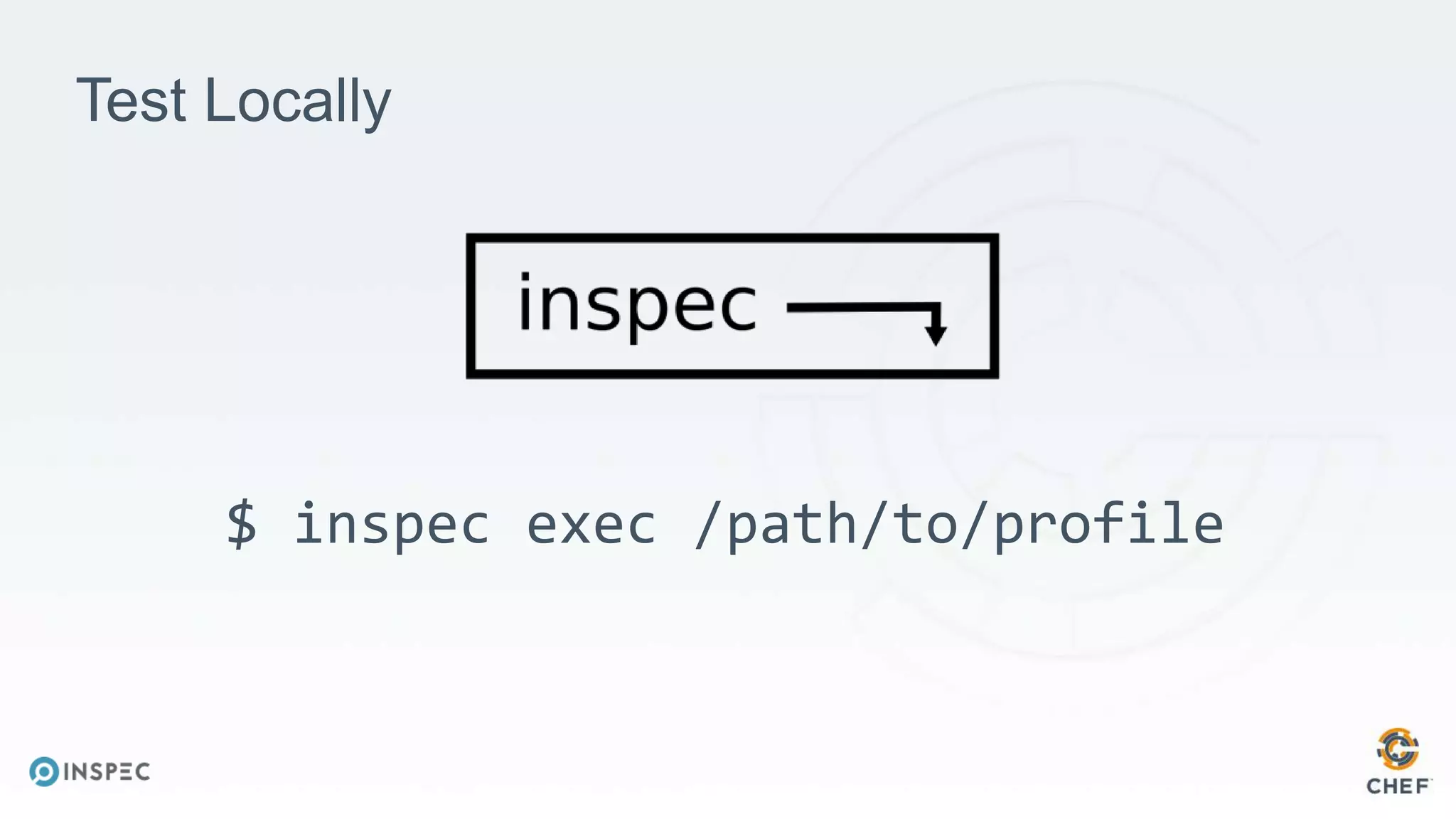
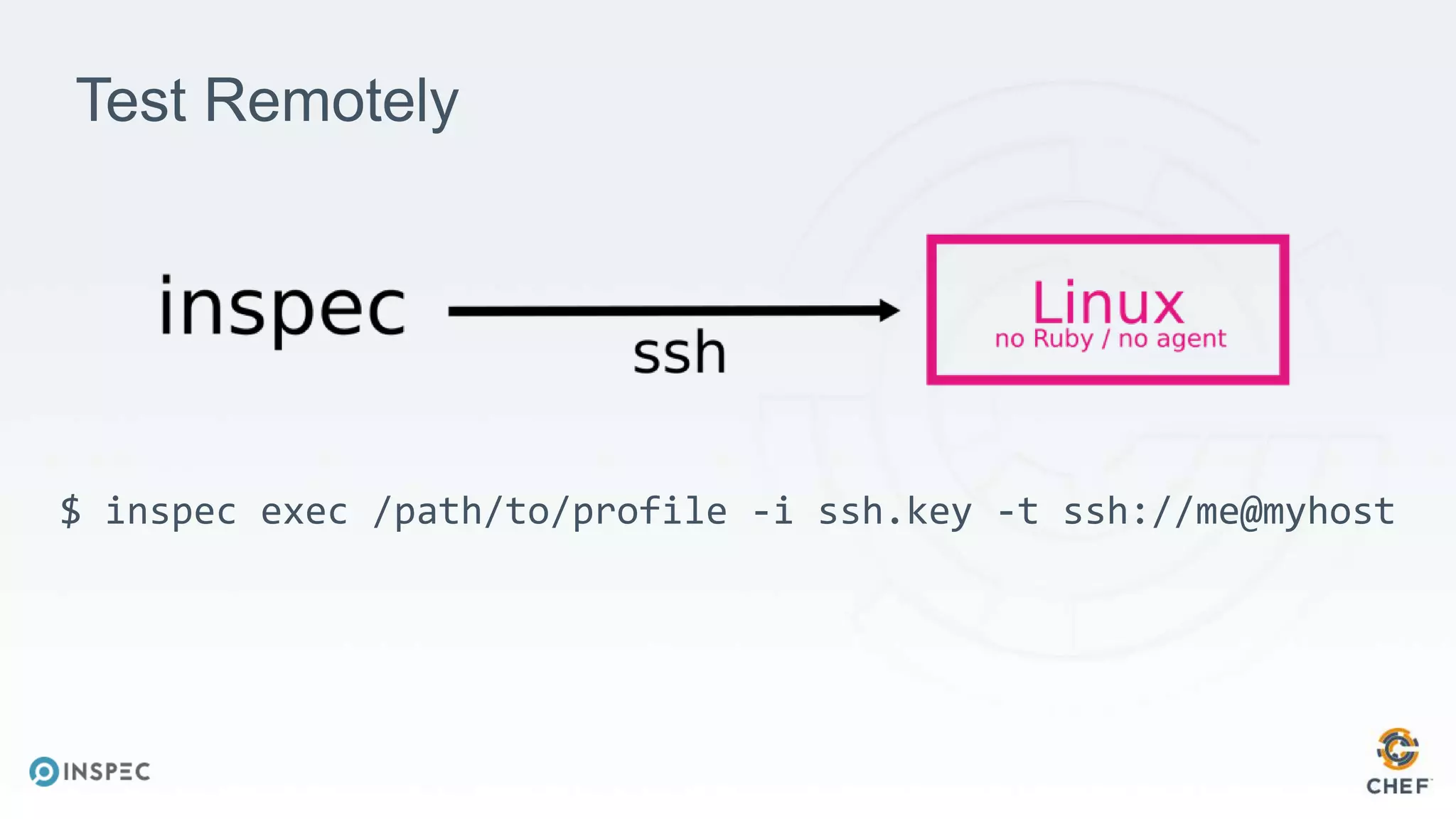
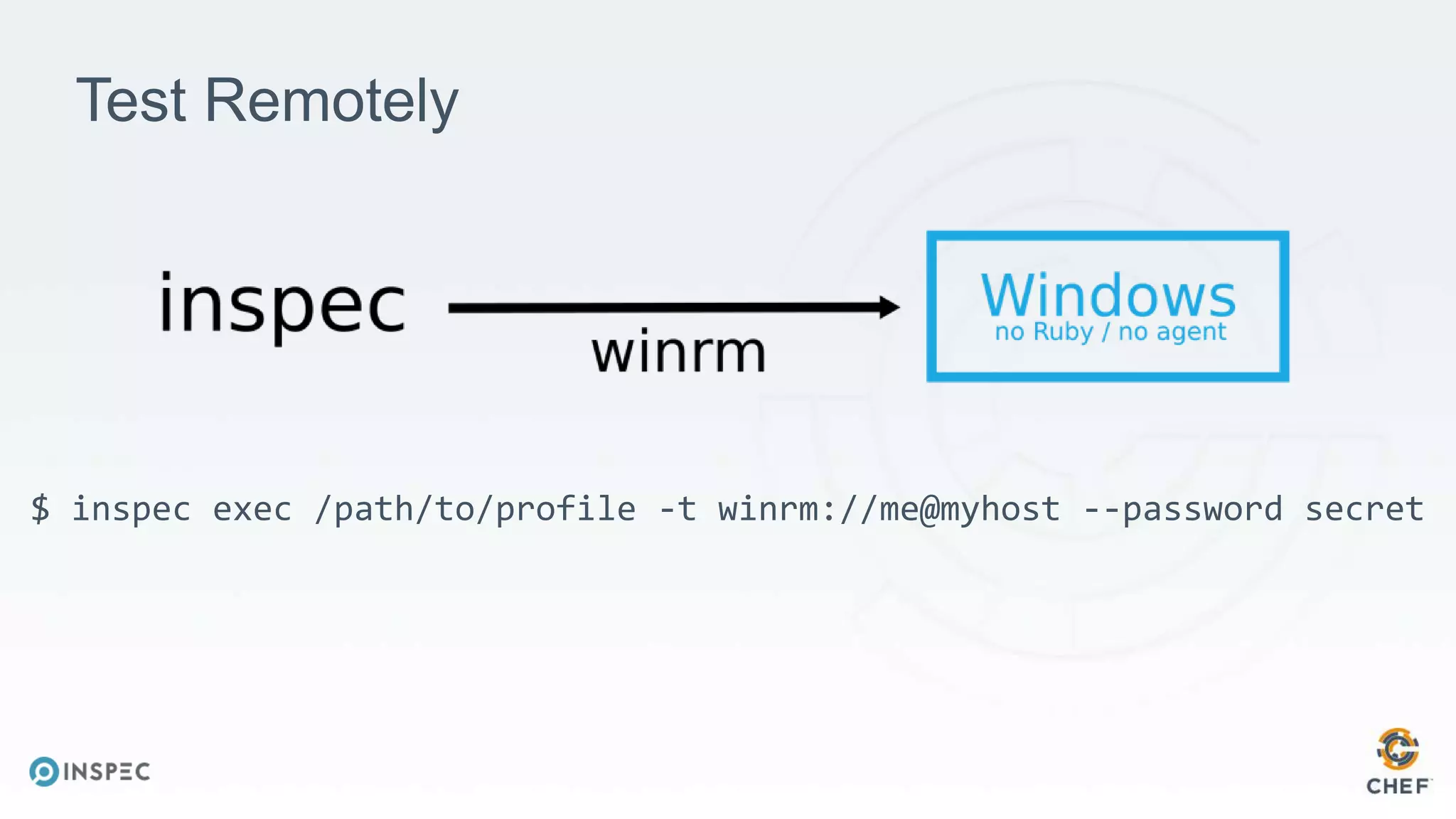
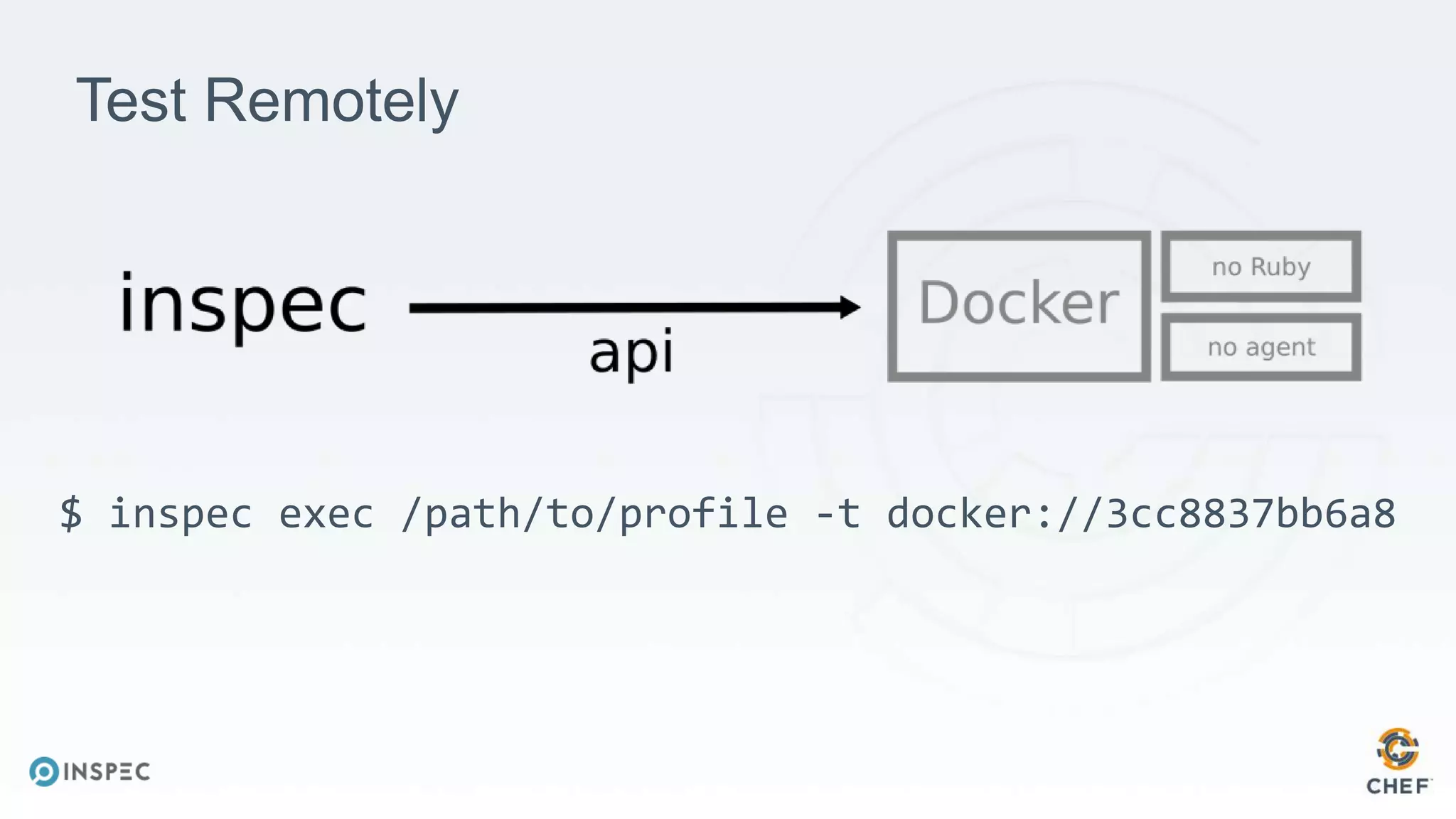
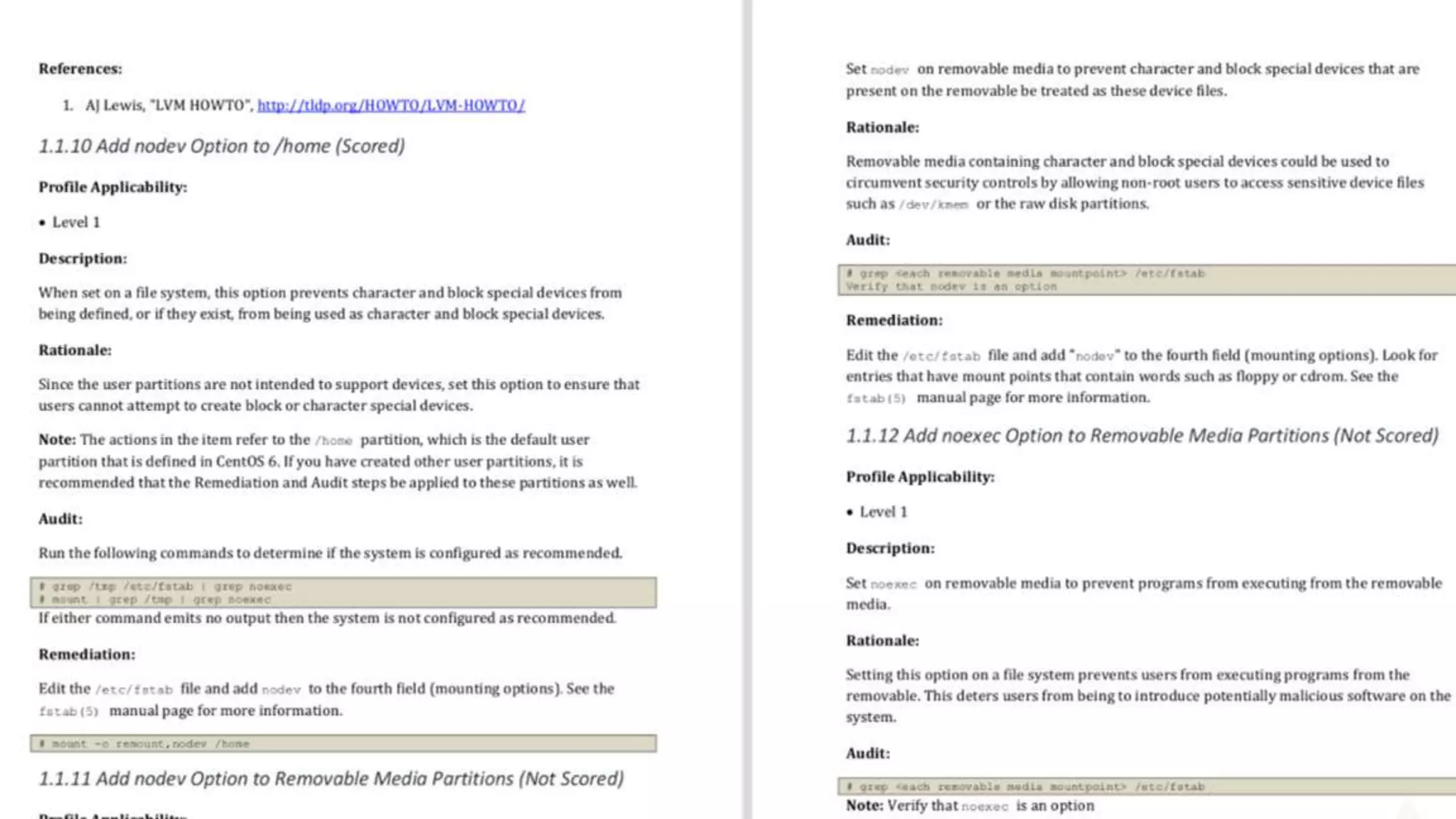
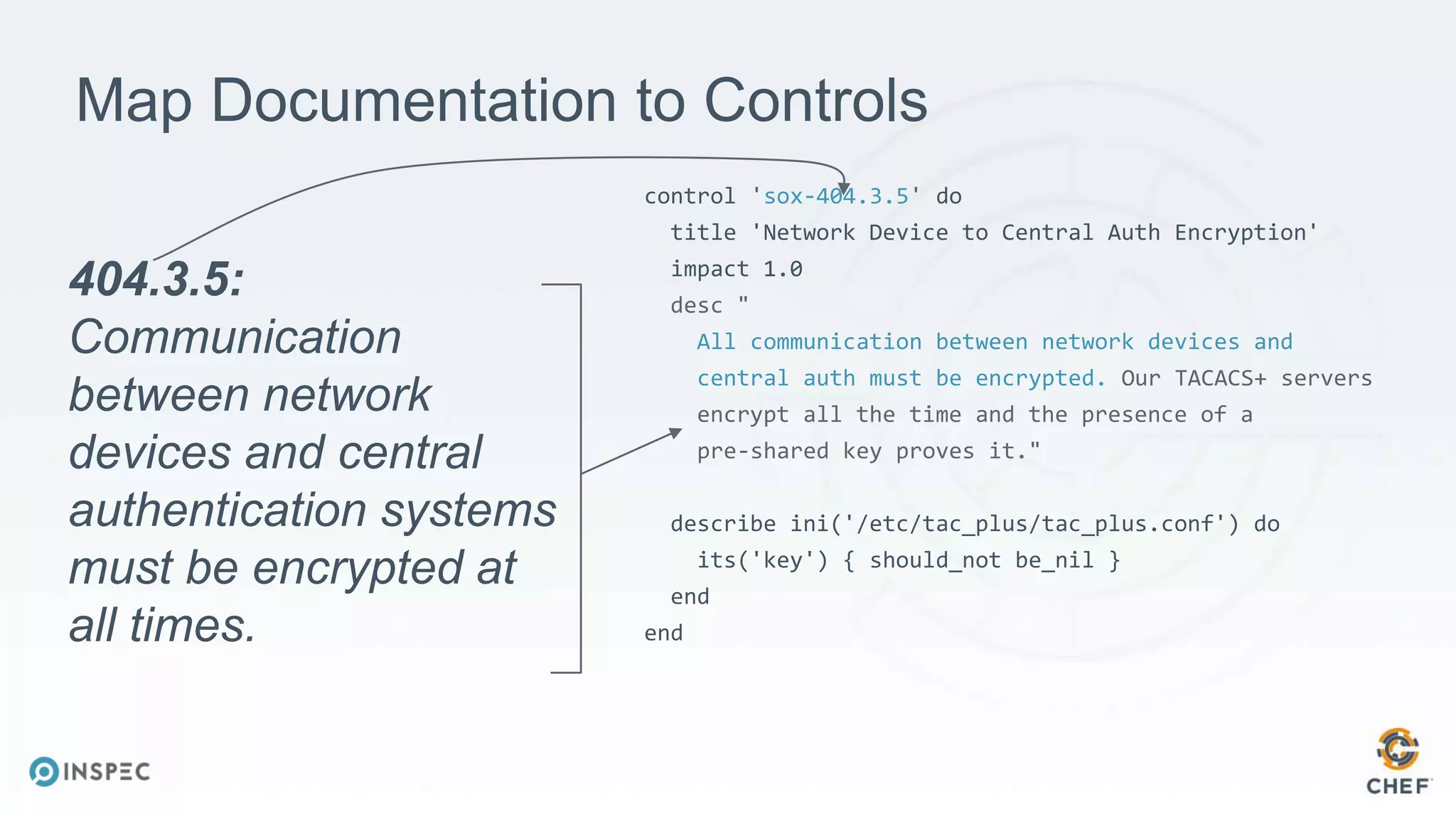
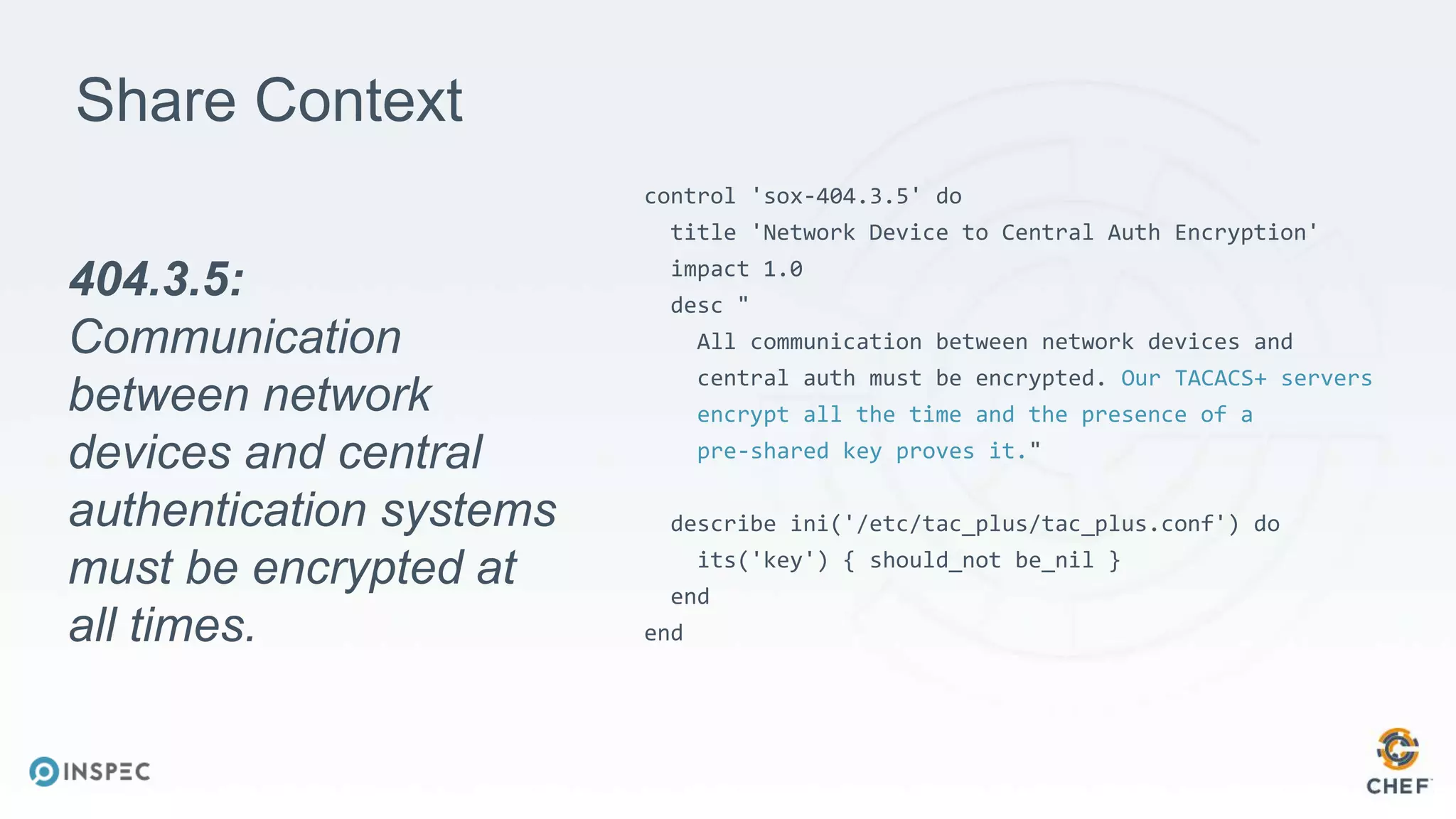
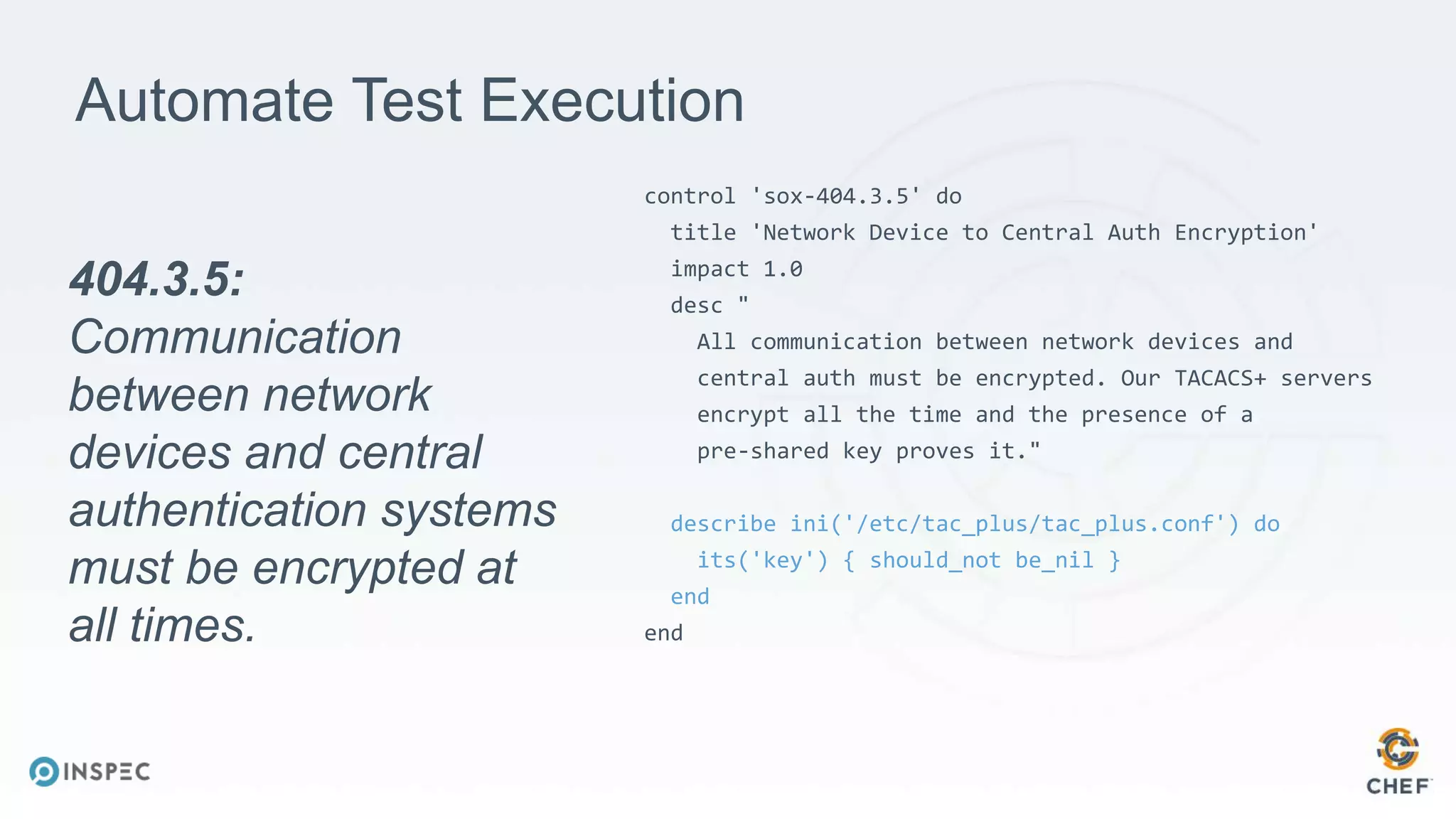
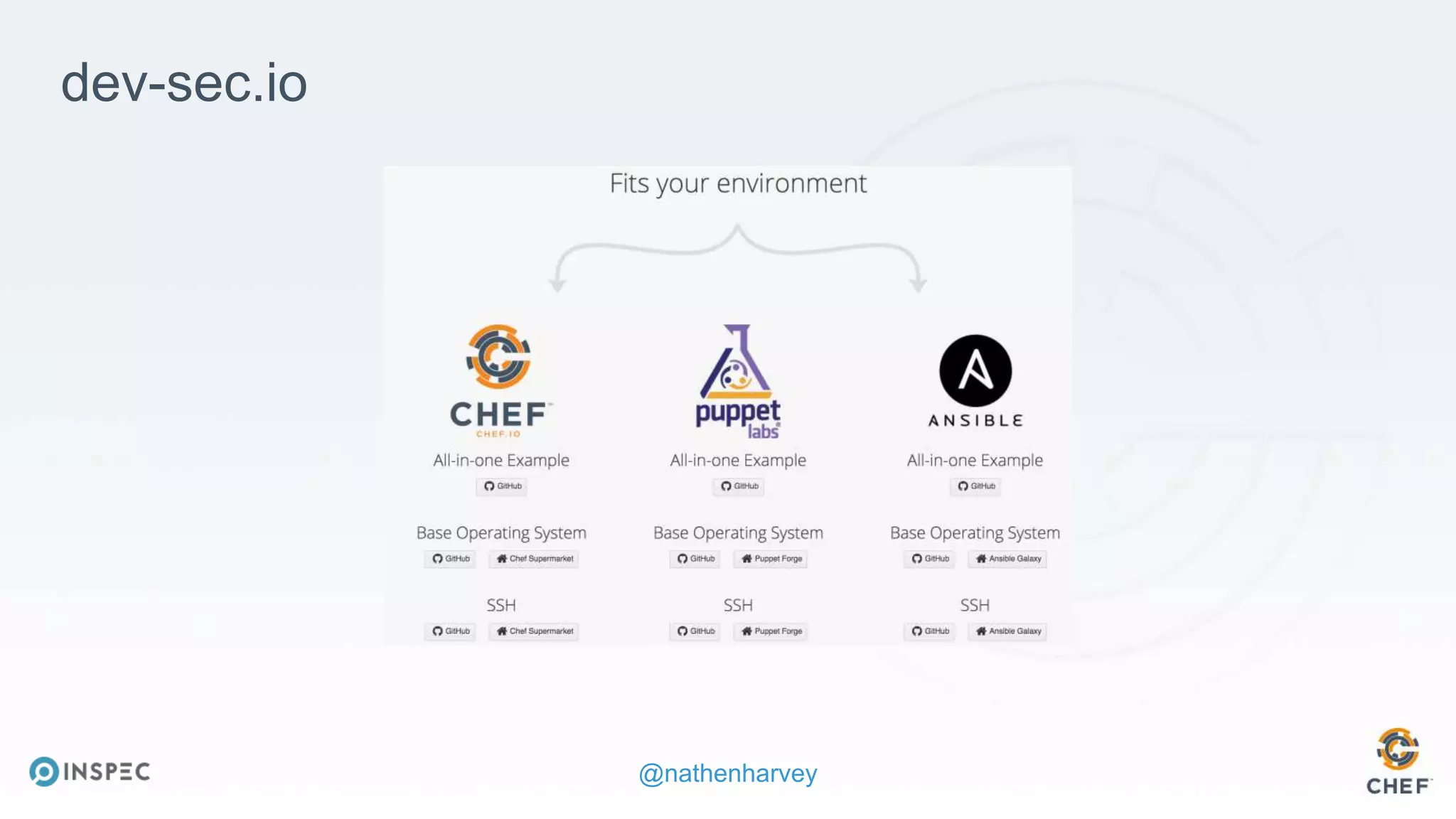
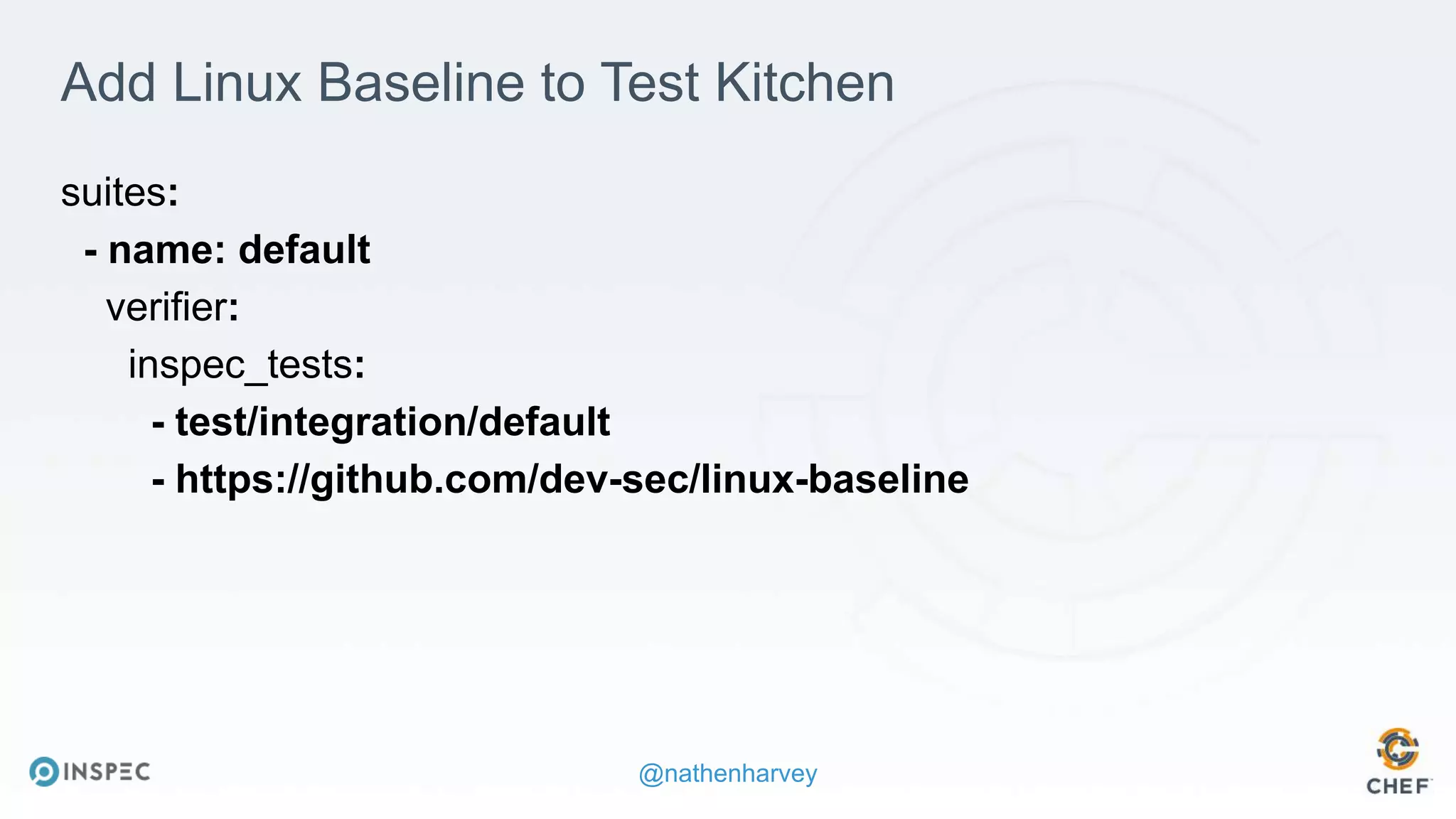
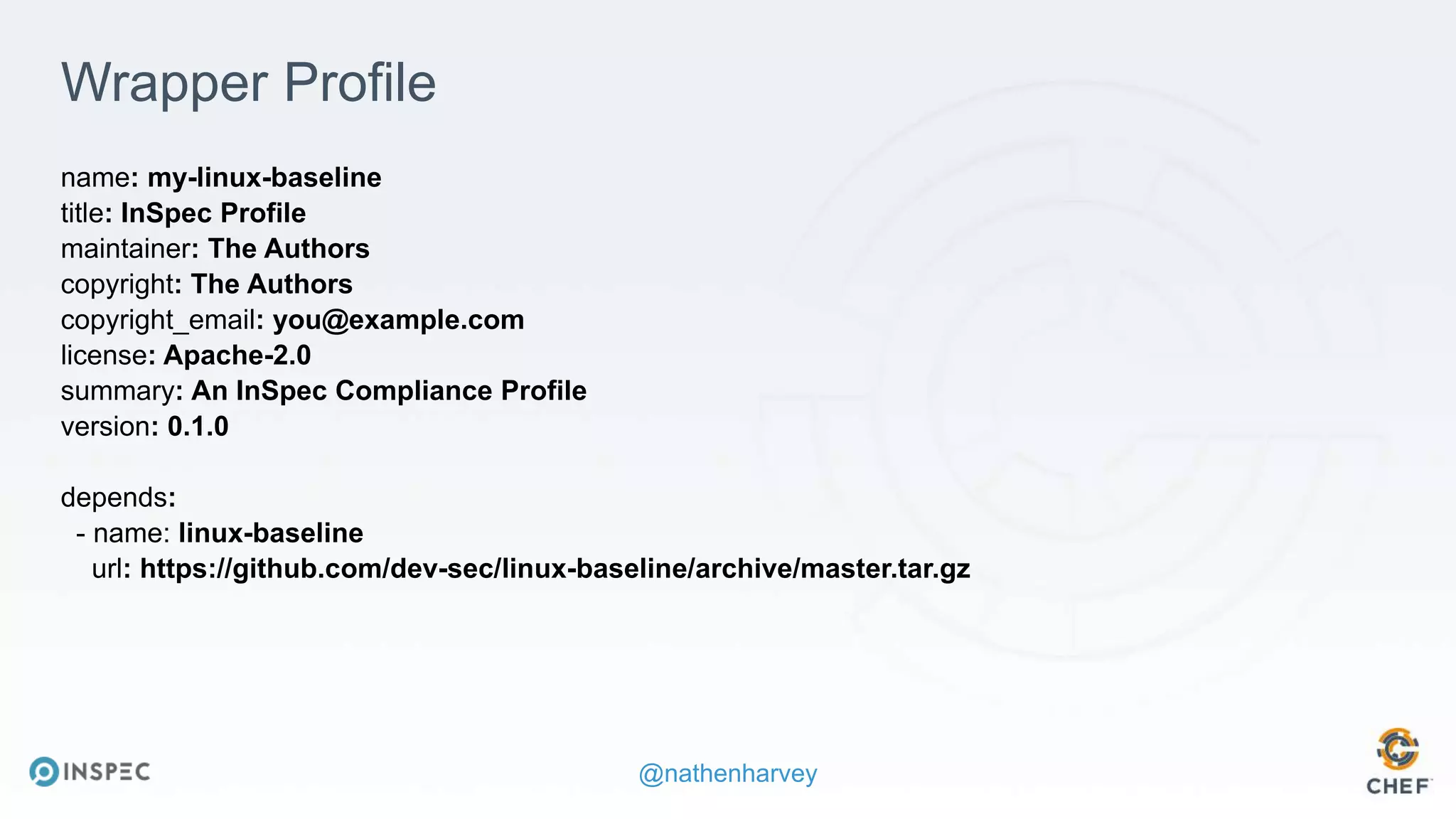
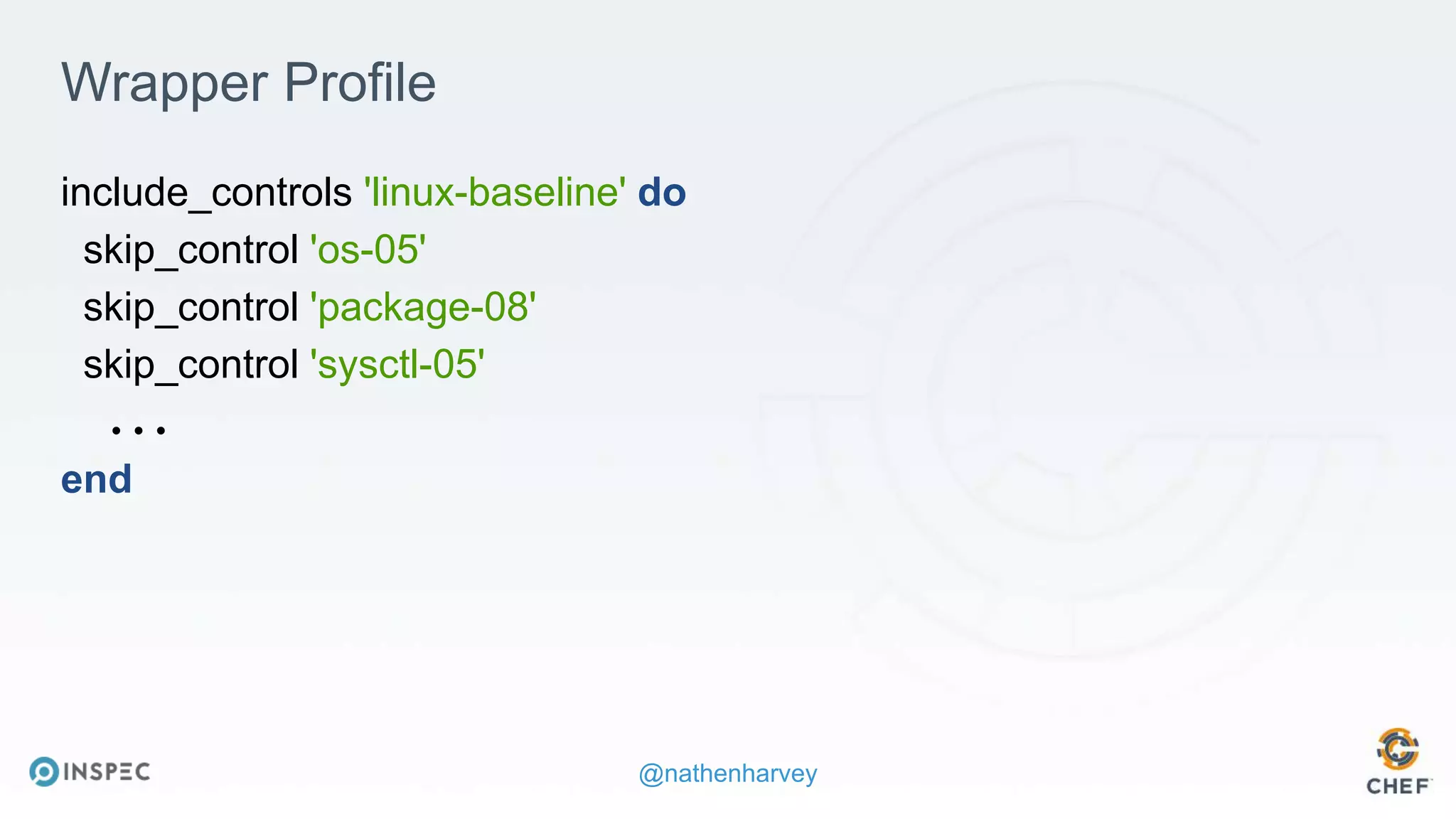
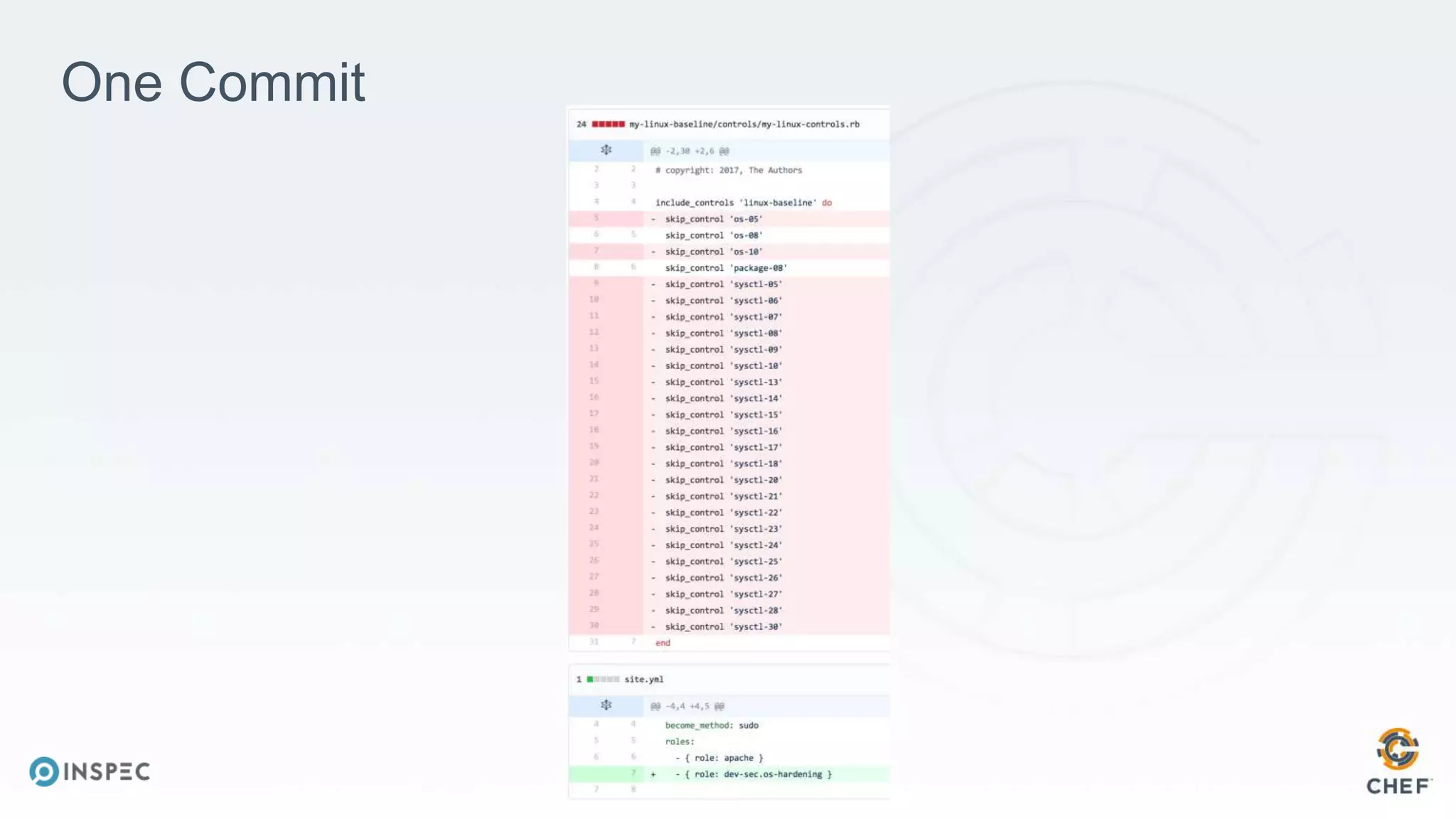
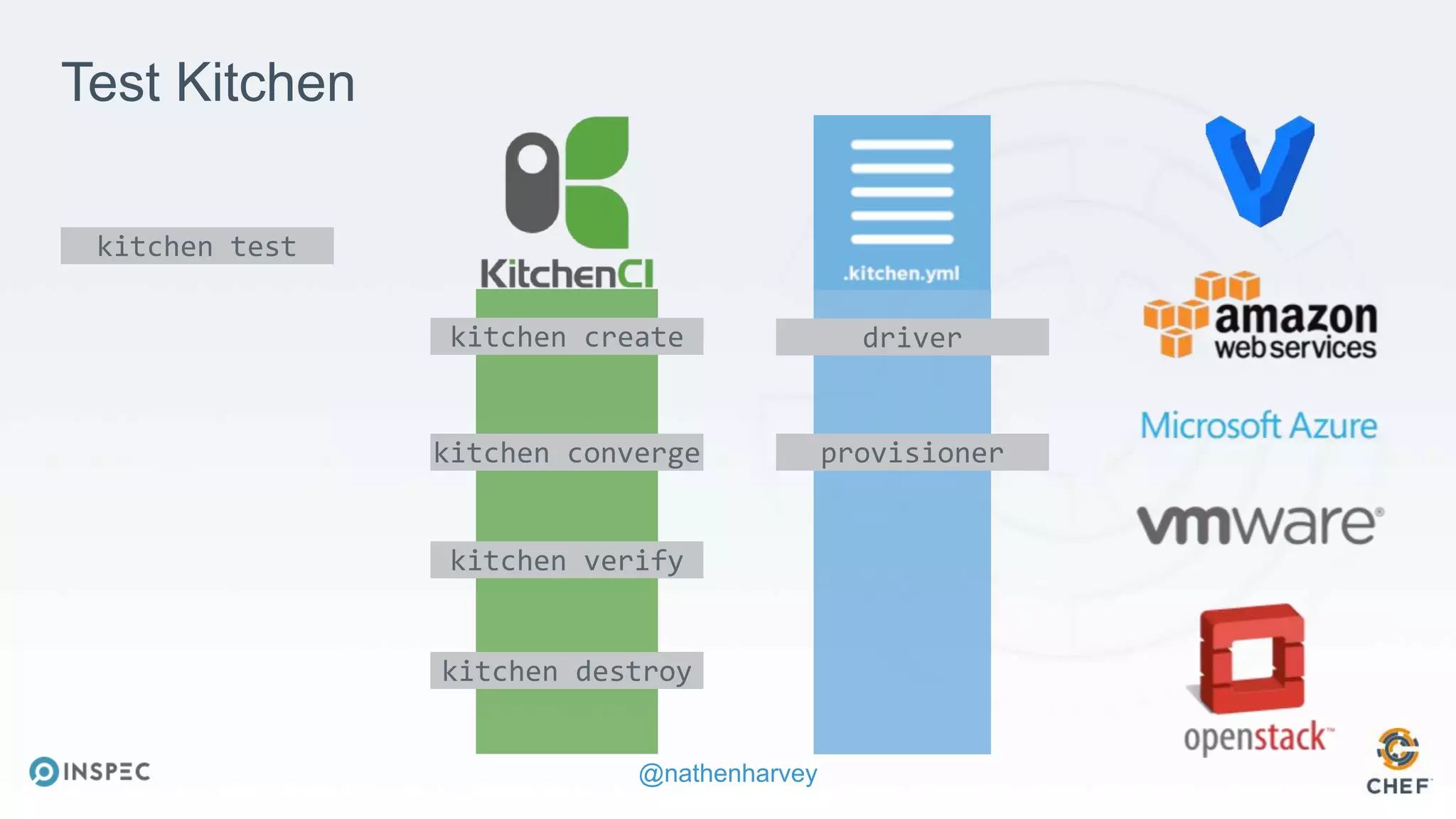
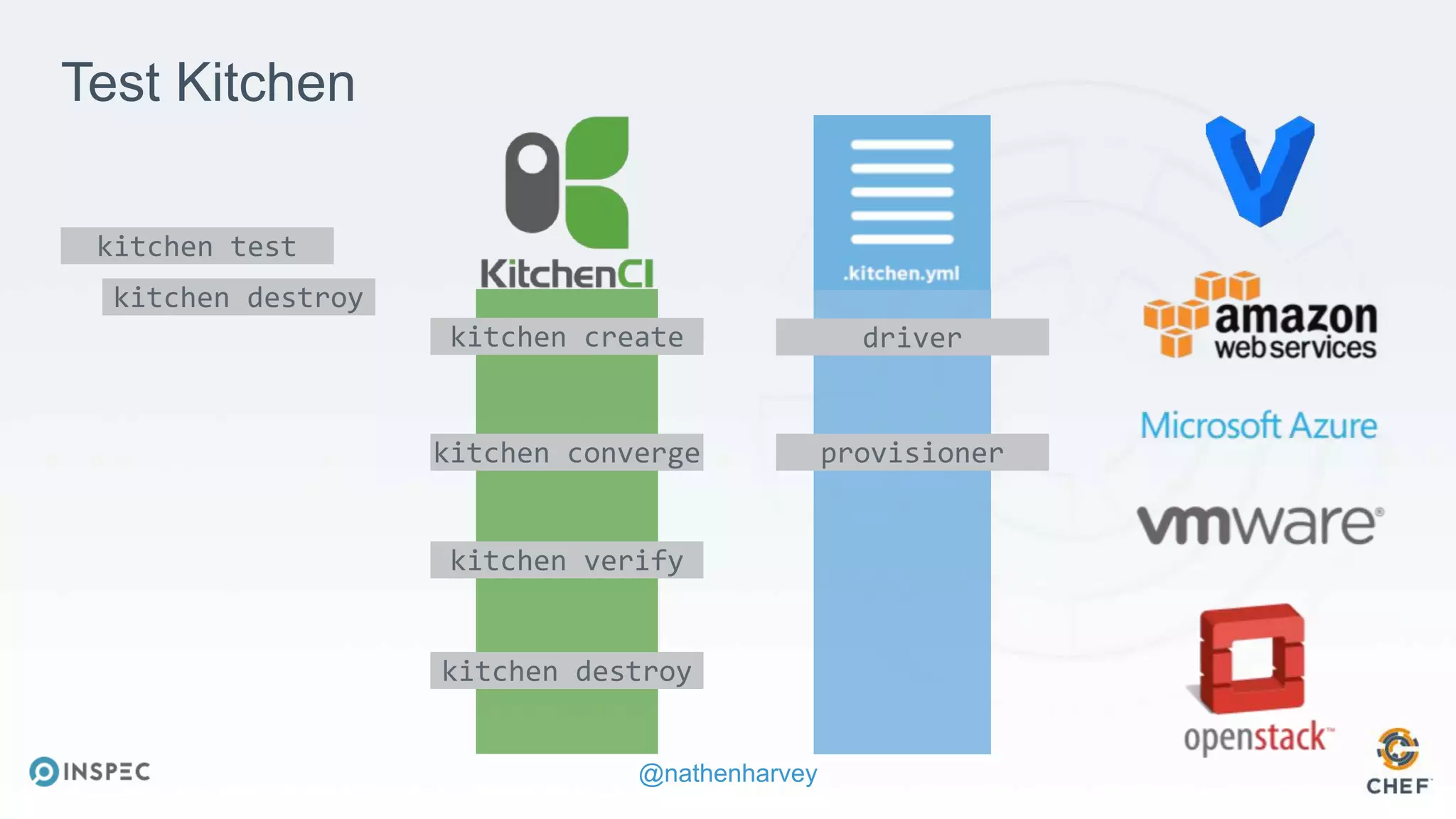
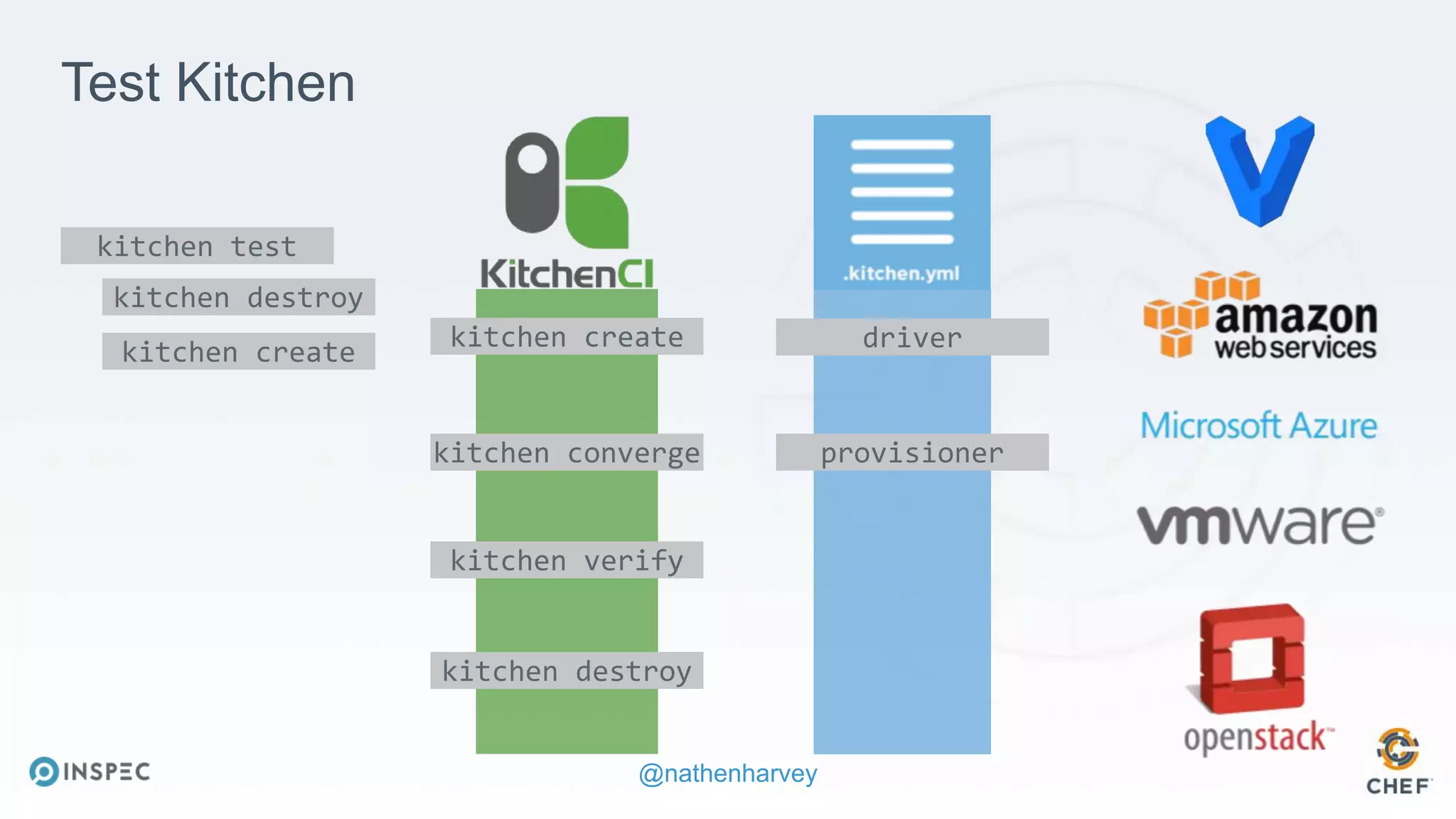
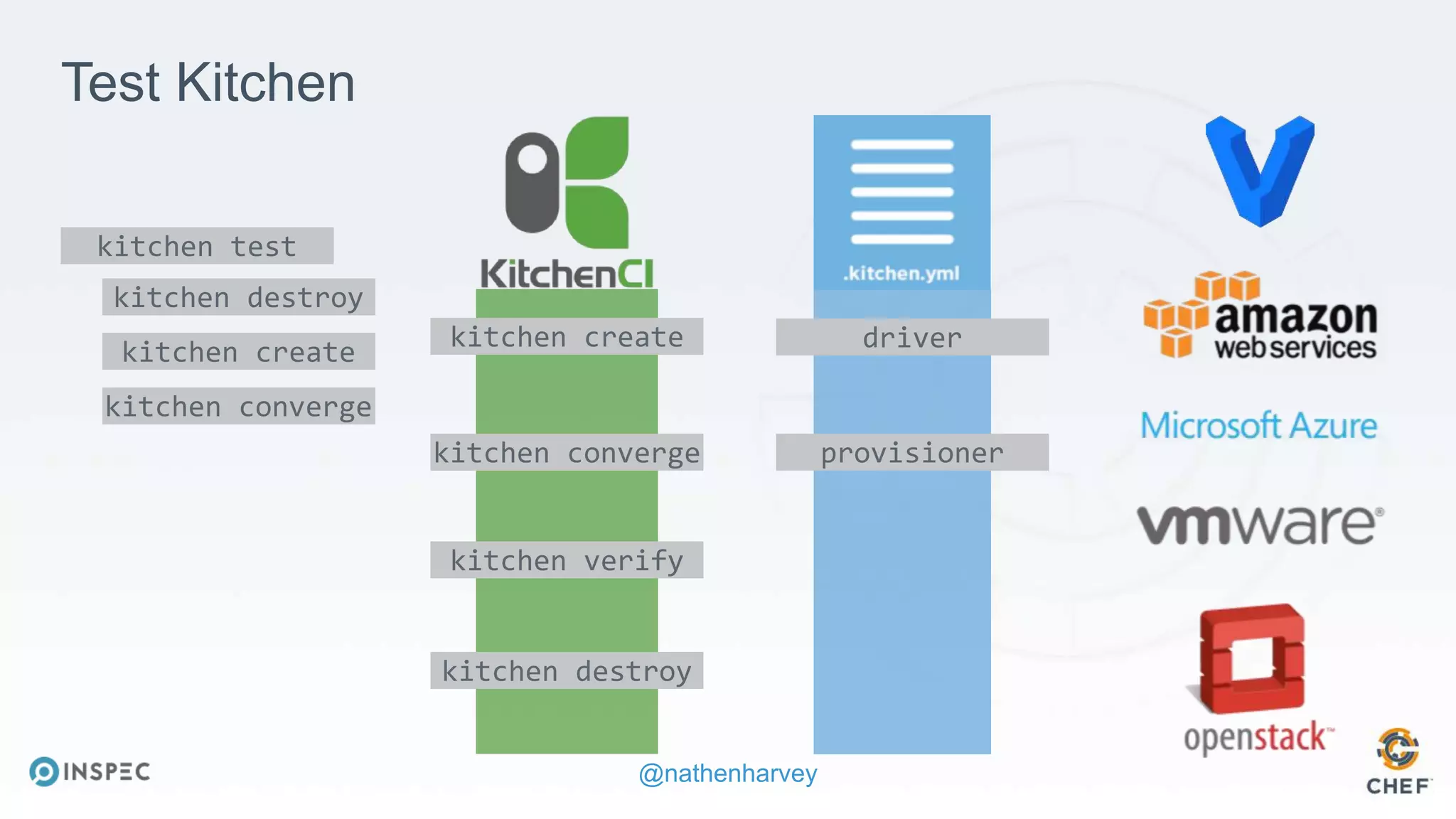
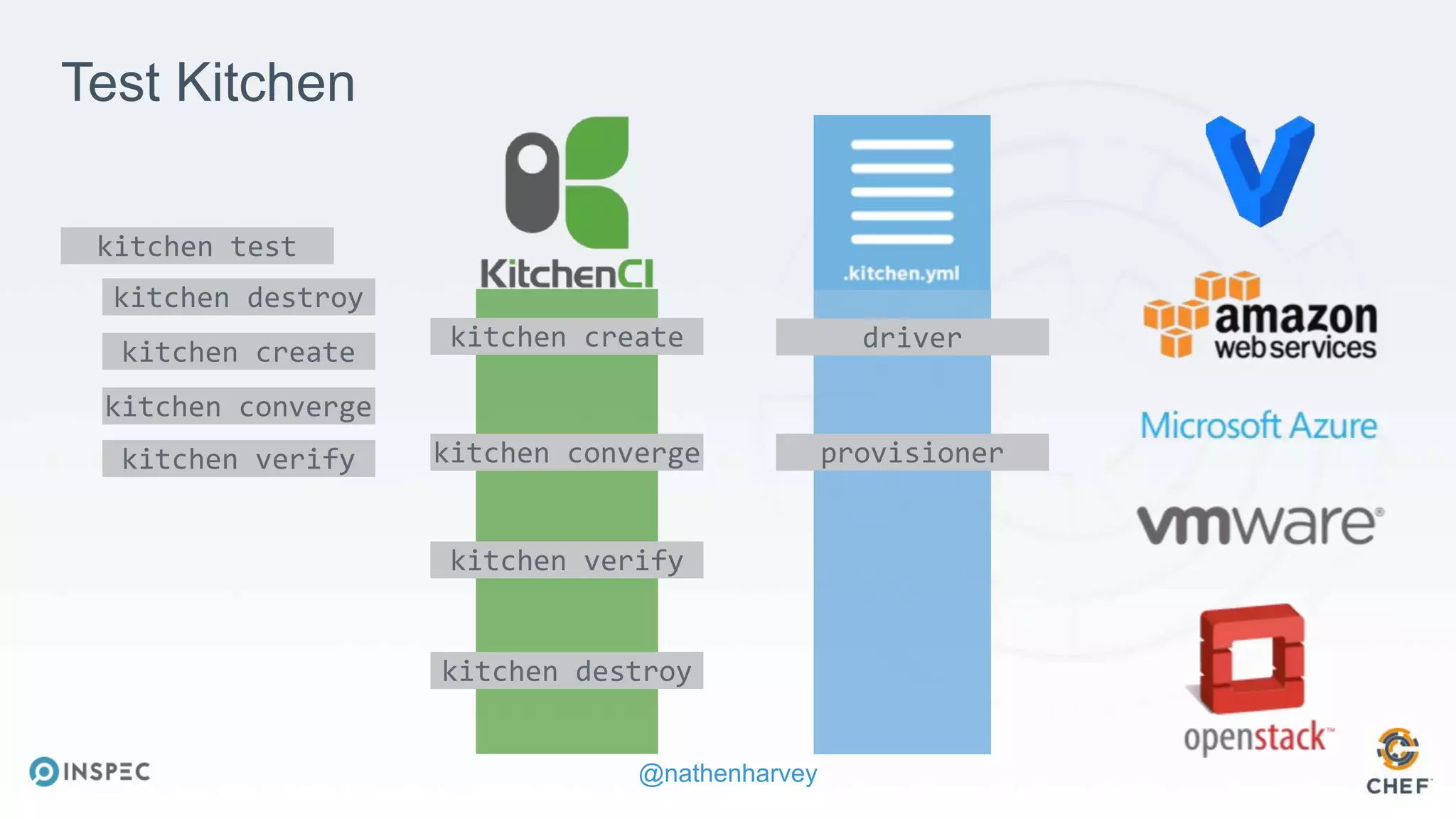
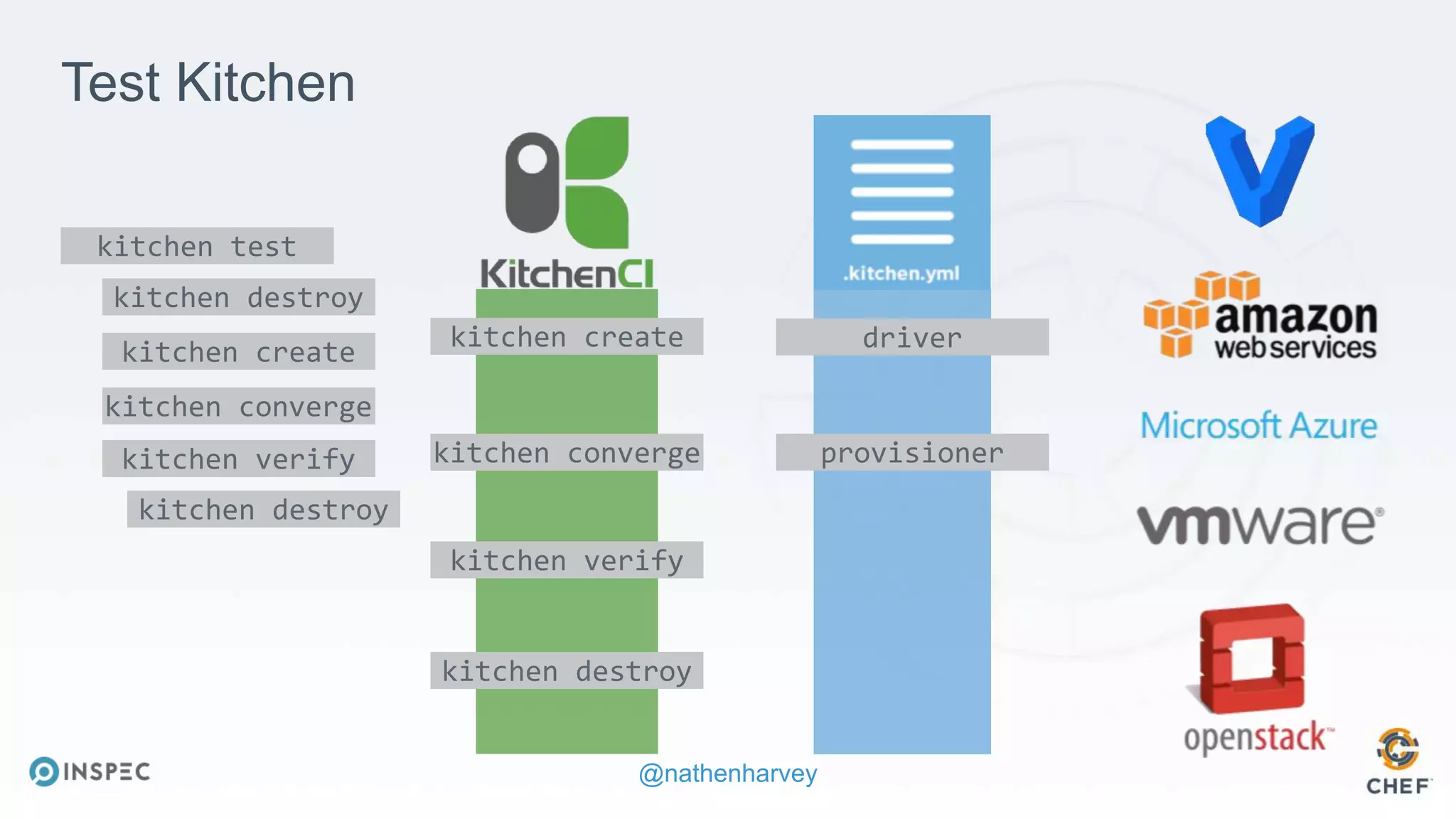
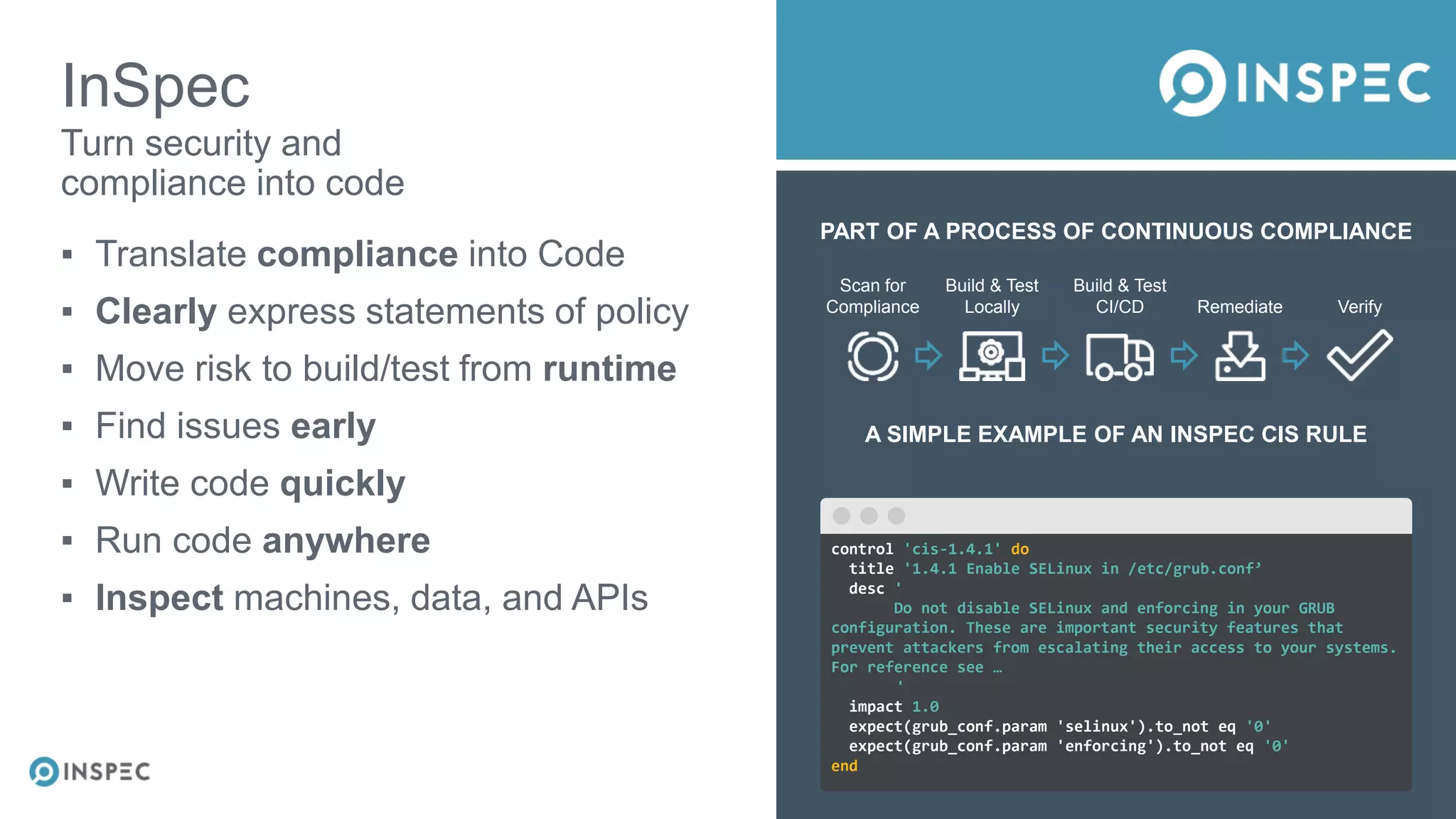
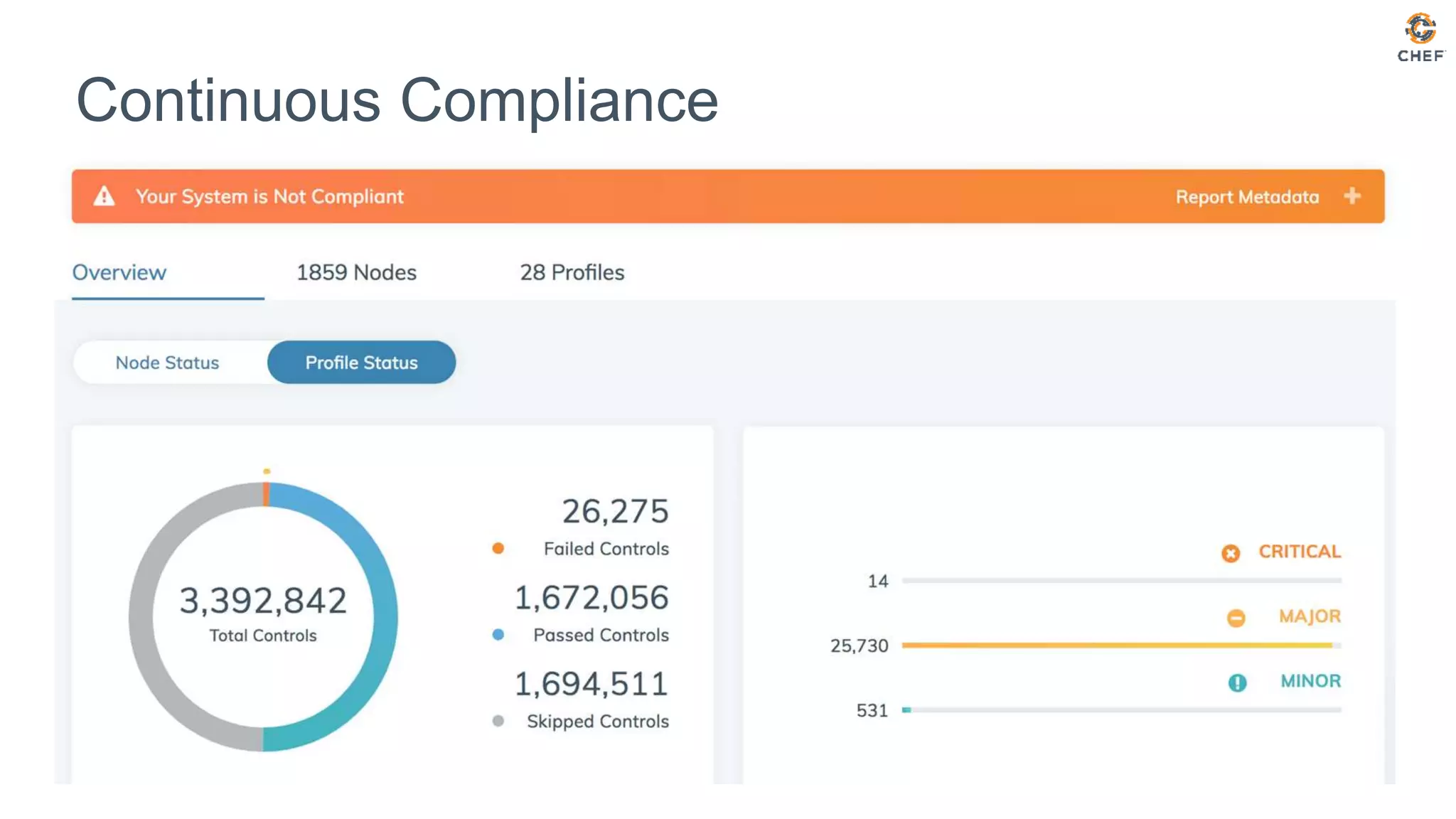
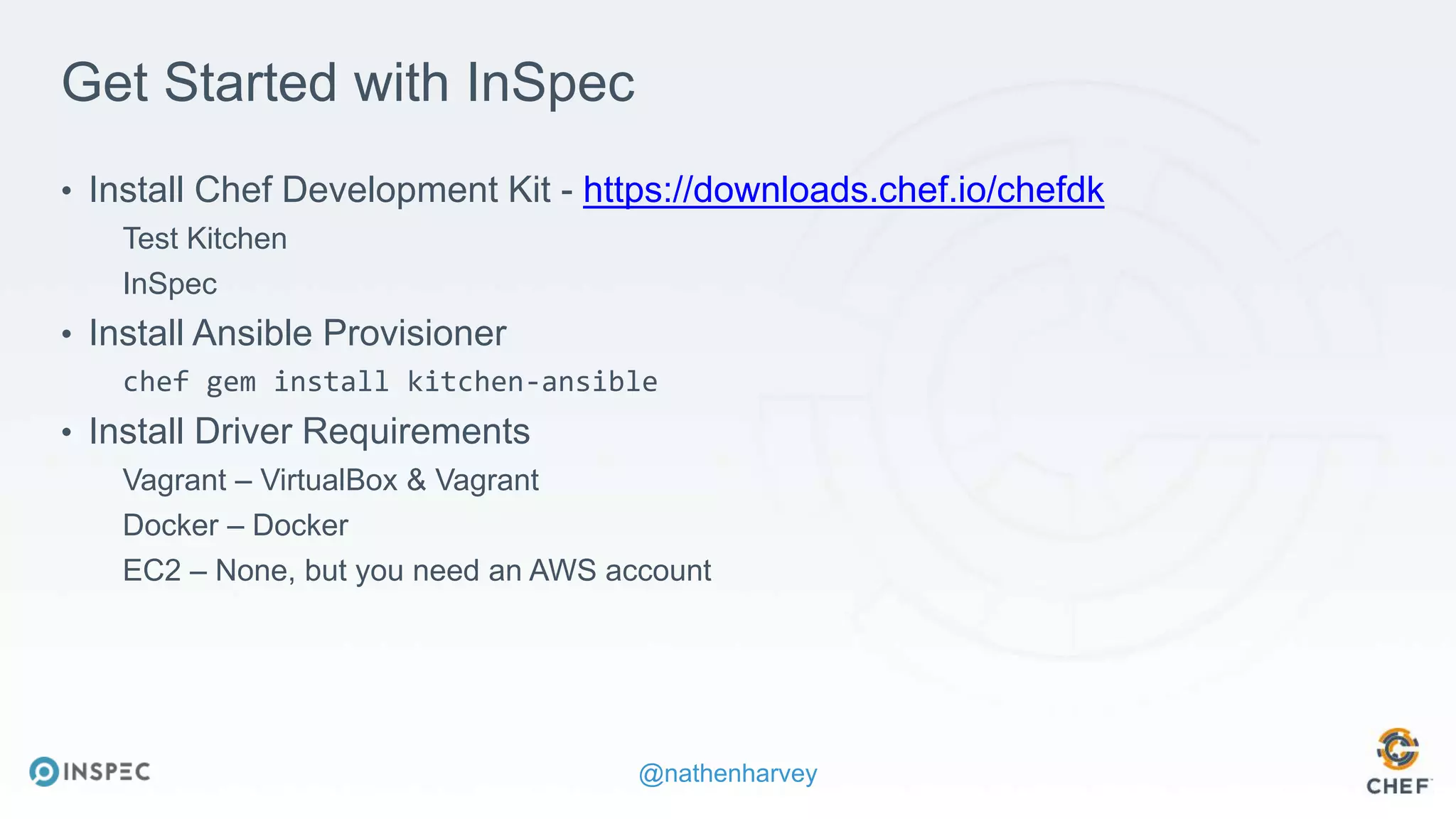
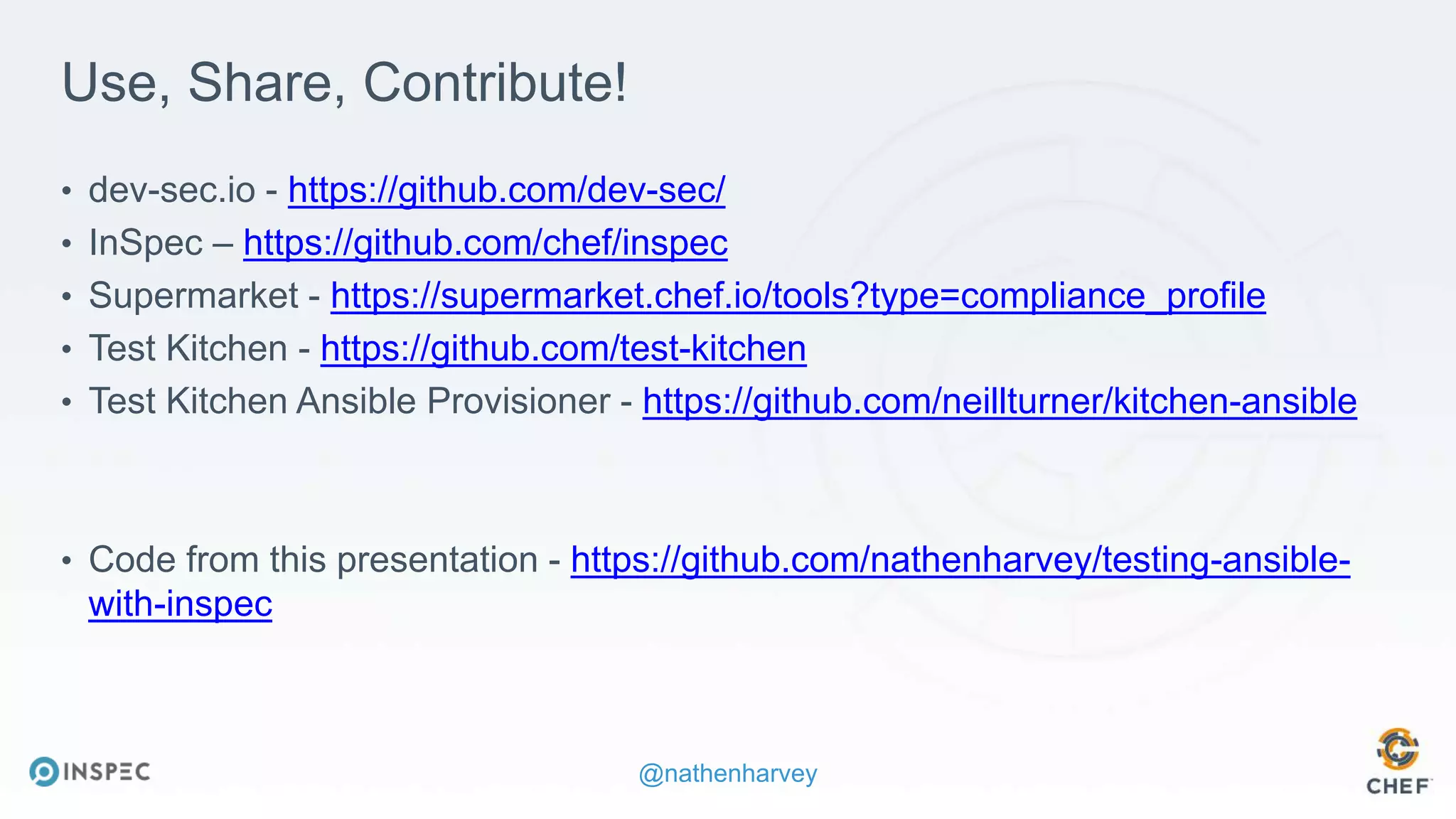
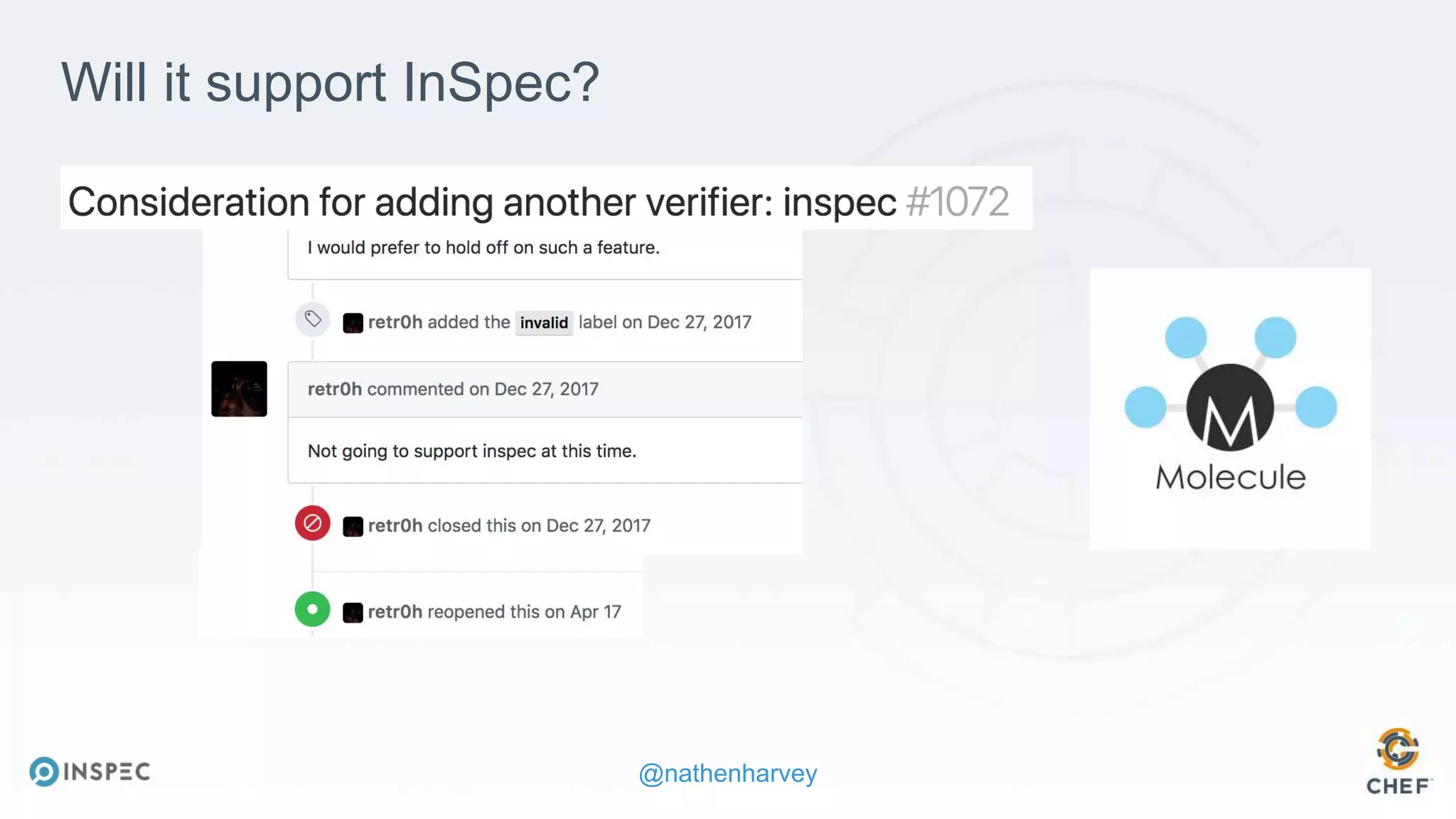
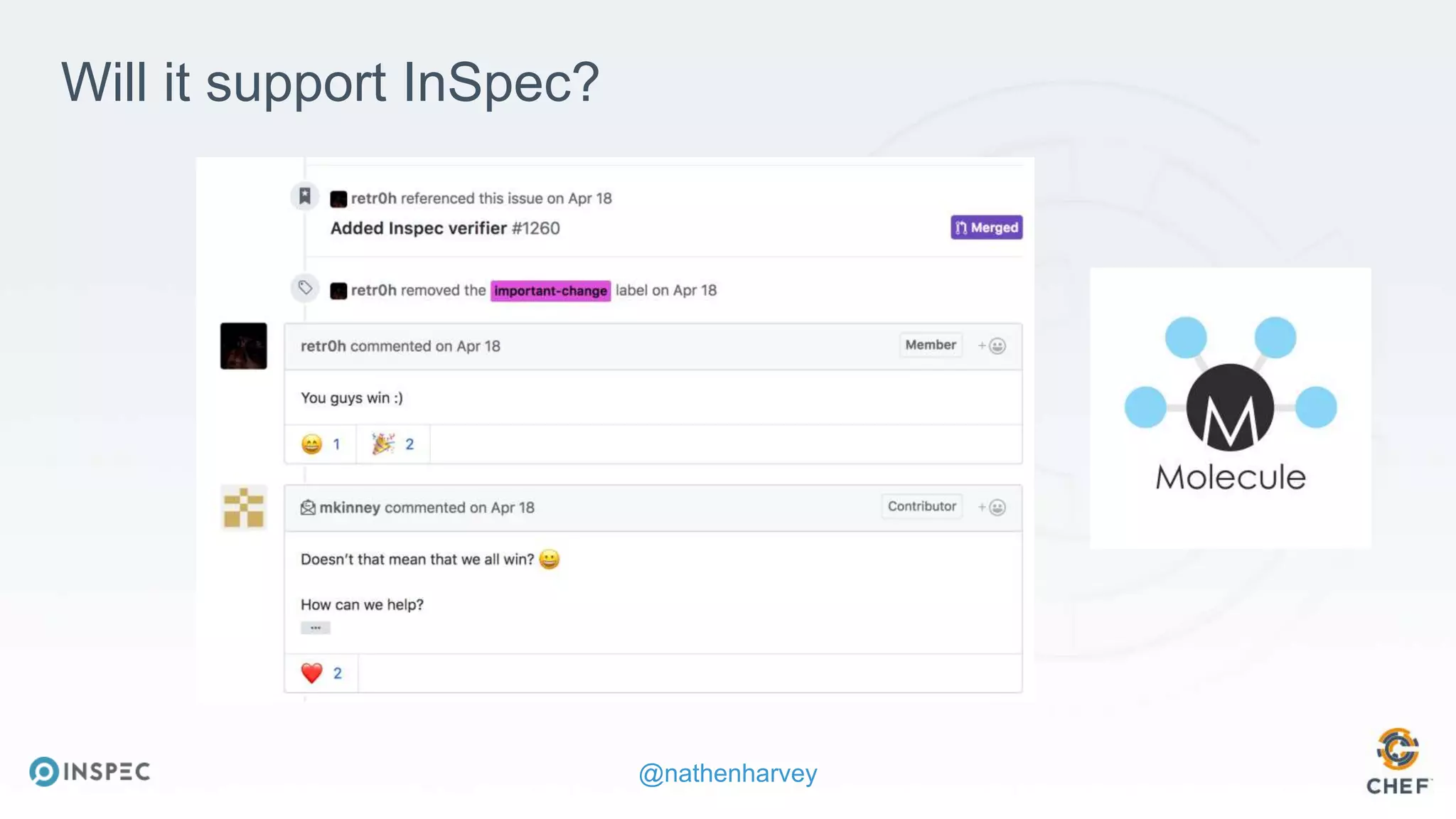
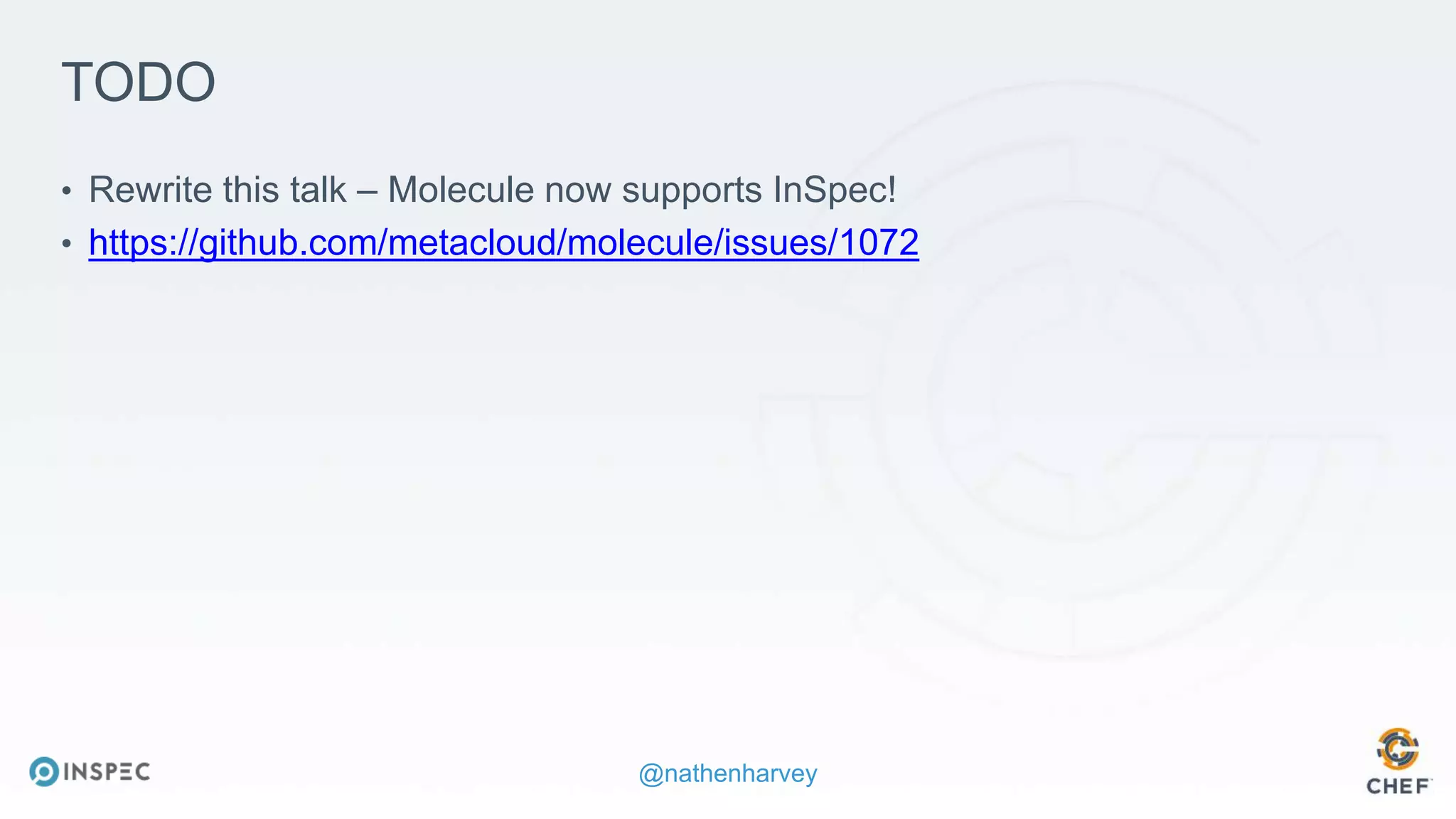
The document discusses effective testing methodologies using Ansible and InSpec, emphasizing the benefits of testing for safety, confidence, and regression prevention. It covers various types of testing, workflows with Test Kitchen, and integration of InSpec for infrastructure compliance testing. The document also provides examples of playbooks, testing scenarios, and resources for further learning in the field of infrastructure testing and compliance.