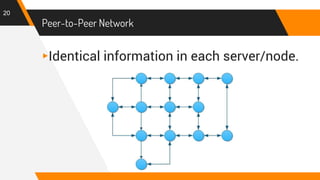
This document provides an overview and comparison of e-money and cryptocurrency. It begins with defining money and its functions, then describes the evolution of money from precious metals to digital currencies. E-money is defined as fiat money in digital form issued by financial institutions, while cryptocurrency uses blockchain technology and decentralization without a central authority. The key differences between the two are that e-money has centralized control and backing from governments or banks, while cryptocurrency operates on peer-to-peer networks without middlemen. Security issues for each such as private key theft and cyberattacks are also discussed. In conclusion, e-money provides consumer protections but cryptocurrency allows for faster transactions and tamper-proof data.