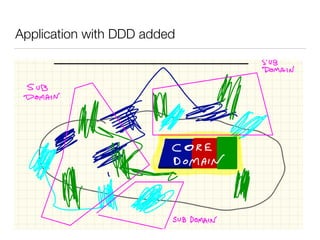
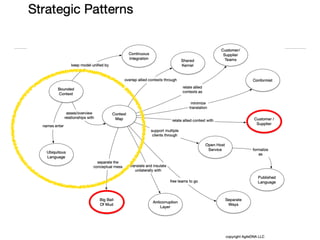
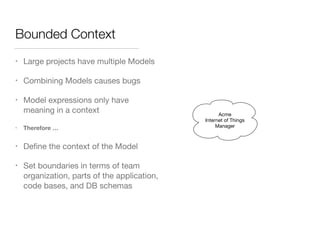
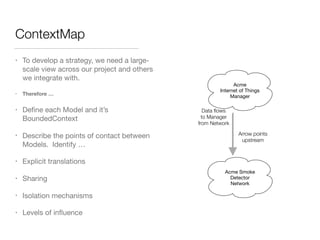
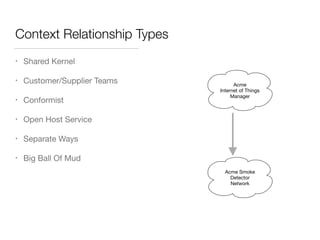
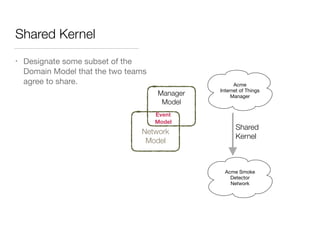
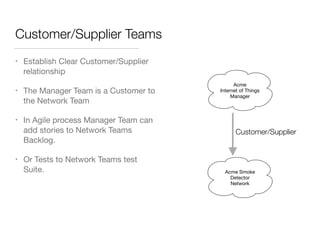
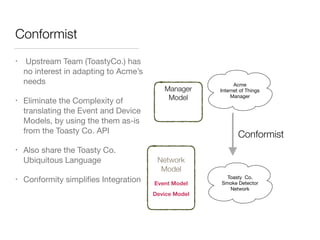
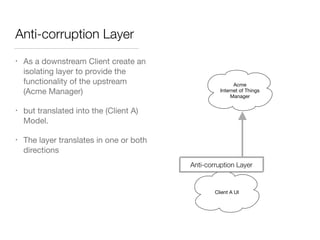
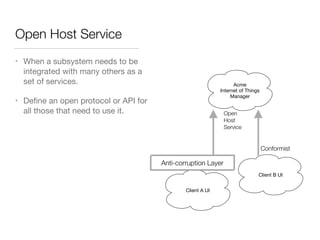
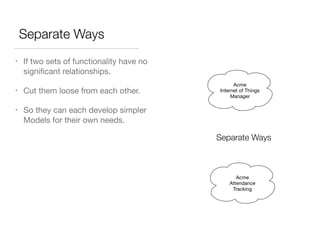
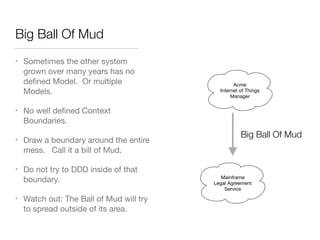
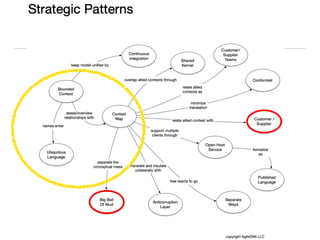
The document discusses Domain-Driven Design (DDD), an approach to software development for complex problems. It provides an overview of DDD and strategic patterns for organizing large projects with multiple teams, such as defining bounded contexts and context maps. Context maps describe the relationships between models, including shared kernels, customer/supplier, and conformist relationships. The document emphasizes defining a ubiquitous language within each context and mapping contexts to understand integration strategies at a large scale.