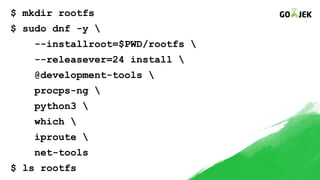
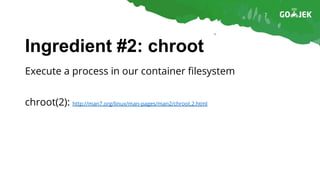
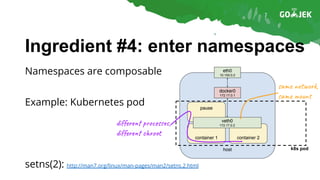
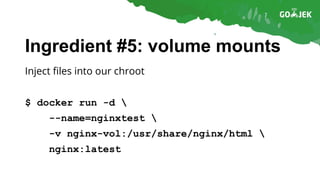
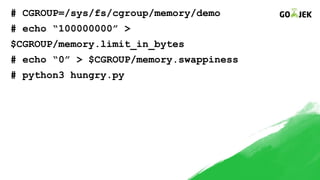
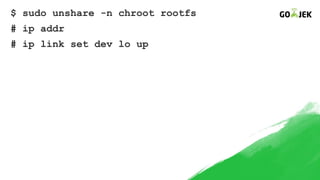
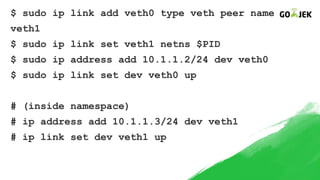
The document details the construction of containers from scratch without using container runtimes like Docker, LXC, or rkt. It outlines essential components such as container images, chroot, namespaces, cgroups, and capabilities that enable this process. Additionally, it provides practical examples and references various tools and methodologies associated with container creation and management.