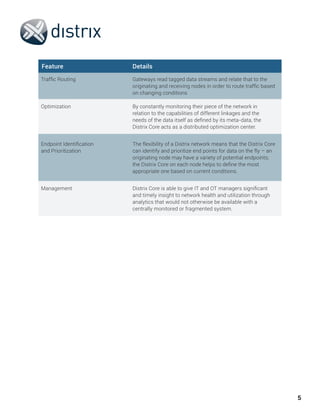
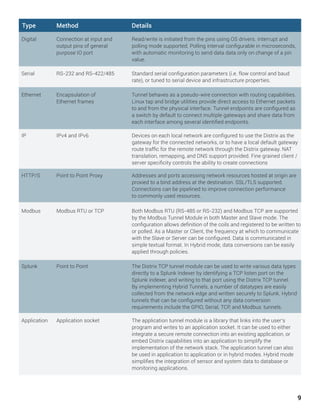
Distrix provides a software defined infrastructure that overlays existing networks to increase flexibility, security and management capabilities. It applies management, routing, rules, redundancy and security to data at any network layer. Distrix tunnels establish secure communication channels that can transmit data efficiently regardless of the physical infrastructure by tagging data streams. This allows data to be dynamically routed based on changing network conditions and application needs. Distrix also increases network performance through capabilities like adding metadata, filtering data, prioritizing traffic and translating data formats.