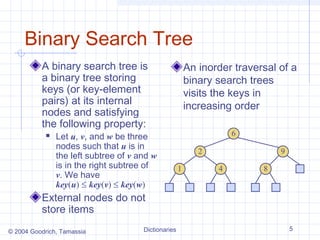
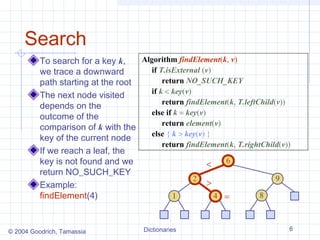
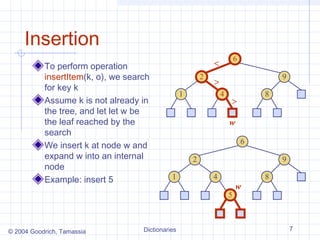
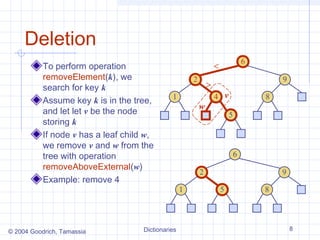
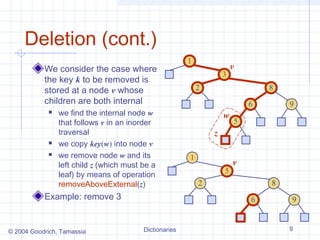
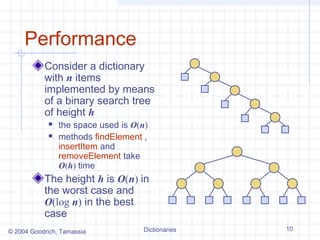
The document describes different data structures that can be used to implement dictionaries, including log files, lookup tables, binary search trees, and hash tables. It explains the basic operations for each structure, such as search, insertion, and deletion times. Binary search trees provide efficient search times of O(log n) on average but can degrade to O(n) in the worst case. Hash tables provide expected constant time for search, insertion, and deletion if collisions are handled well.



![Hash Functions and
Hash Tables
A hash function h maps keys of a given type to integers
in a fixed interval [0, N − 1]
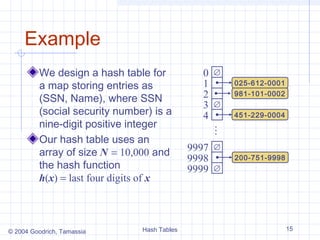
Example:
h(x) = x mod N
is a hash function for integer keys
The integer h(x) is called the hash value of key x
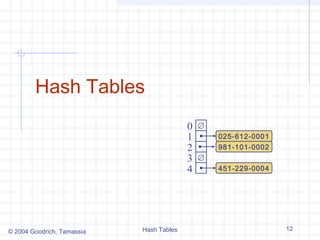
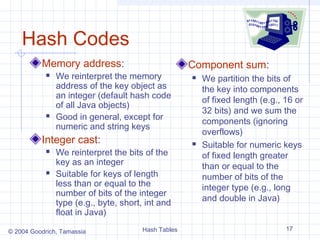
A hash table for a given key type consists of
Hash function h
Array (called table) of size N
When implementing a map with a hash table, the goal
is to store item (k, o) at index i = h(k)
© 2004 Goodrich, Tamassia Hash Tables 14](https://image.slidesharecdn.com/dichash-121113034935-phpapp02/85/Dic-hash-14-320.jpg)
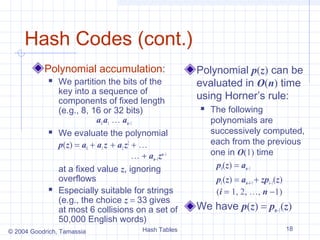
![Hash Functions
A hash function is The hash code is
usually specified as the applied first, and the
compression function
composition of two
is applied next on the
functions: result, i.e.,
Hash code: h(x) = h2(h1(x))
h1: keys → integers The goal of the hash
function is to
Compression function:
“disperse” the keys in
h2: integers → [0, N − 1] an apparently random
way
© 2004 Goodrich, Tamassia Hash Tables 16](https://image.slidesharecdn.com/dichash-121113034935-phpapp02/85/Dic-hash-16-320.jpg)

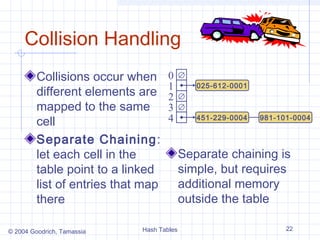
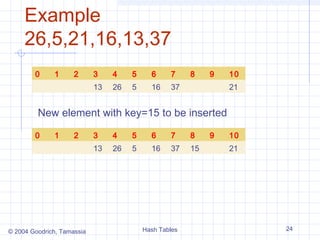
![Linear probing
A simple open addressing collision handling strategy
is called linear probing. In this if we try to insert an
item (k,e) into a bucket A[i] that is already occupied ,
where i=h(k), then we try next at A[(i+1)mod N]. If
A[(i+1)mod N] is occupied then we try at A[(i+2)mod
N] and so on, until we find the empty bucket in A that
can accept the new item.
© 2004 Goodrich, Tamassia Hash Tables 23](https://image.slidesharecdn.com/dichash-121113034935-phpapp02/85/Dic-hash-23-320.jpg)