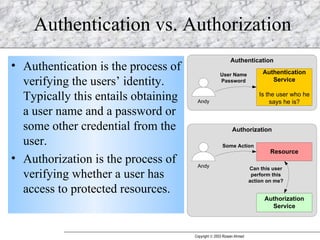
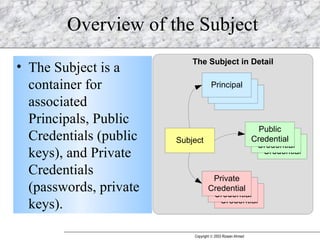
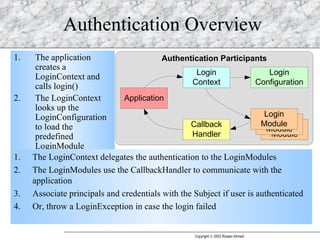
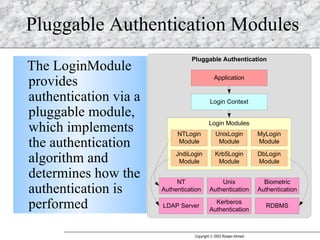
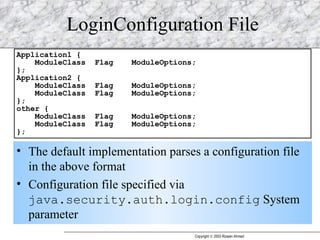
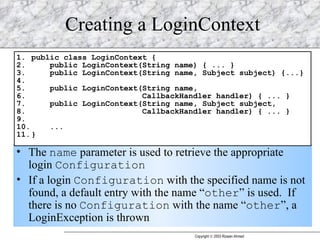
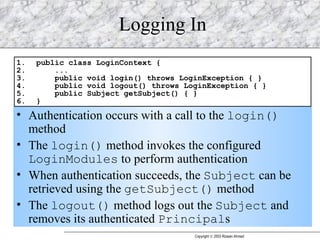
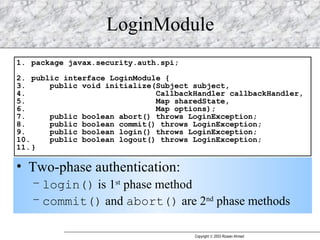
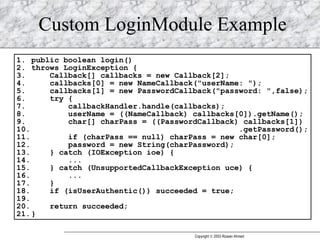
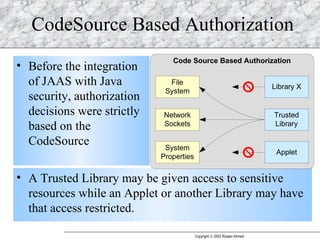
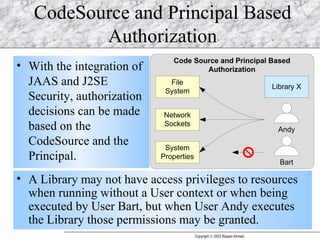
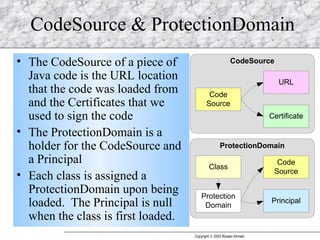
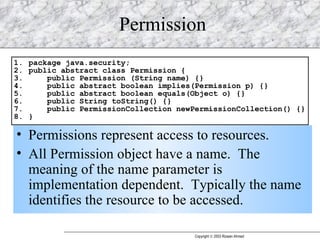
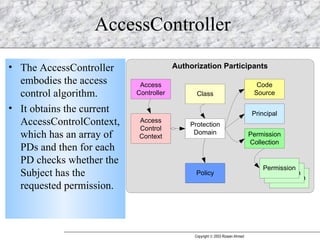
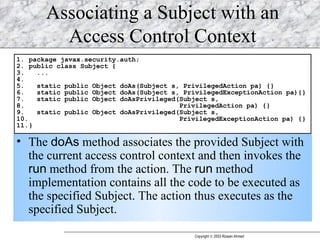
JAAS (Java Authentication and Authorization Service) provides a pluggable framework for authentication and authorization in Java applications. It allows developers to incorporate different security mechanisms and sources. JAAS includes interfaces and classes for authentication, where users verify their identity, and authorization, where users are granted access to protected resources based on their roles and permissions. Developers can implement custom login modules for authentication and policies for authorization to integrate various security systems.