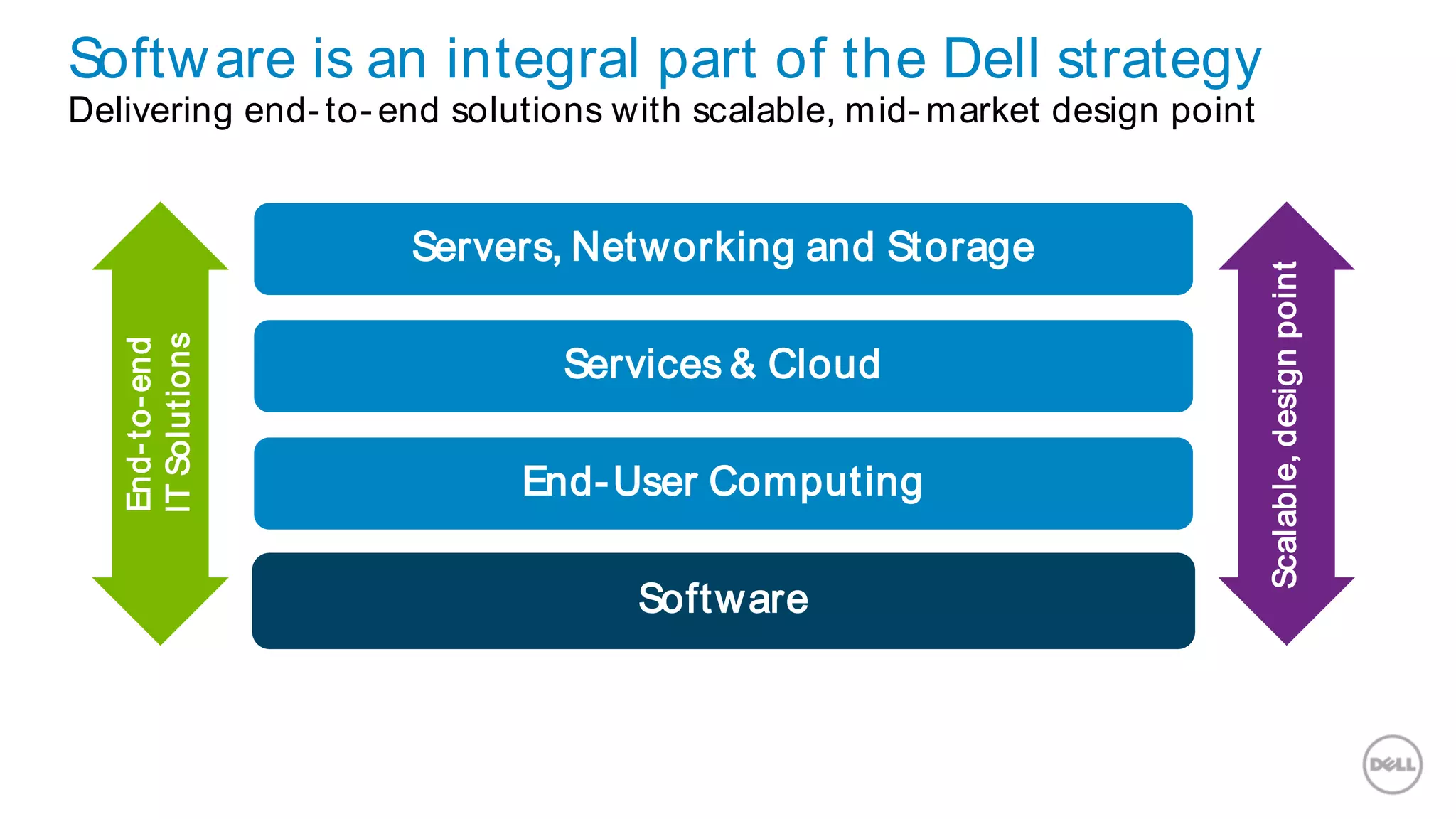
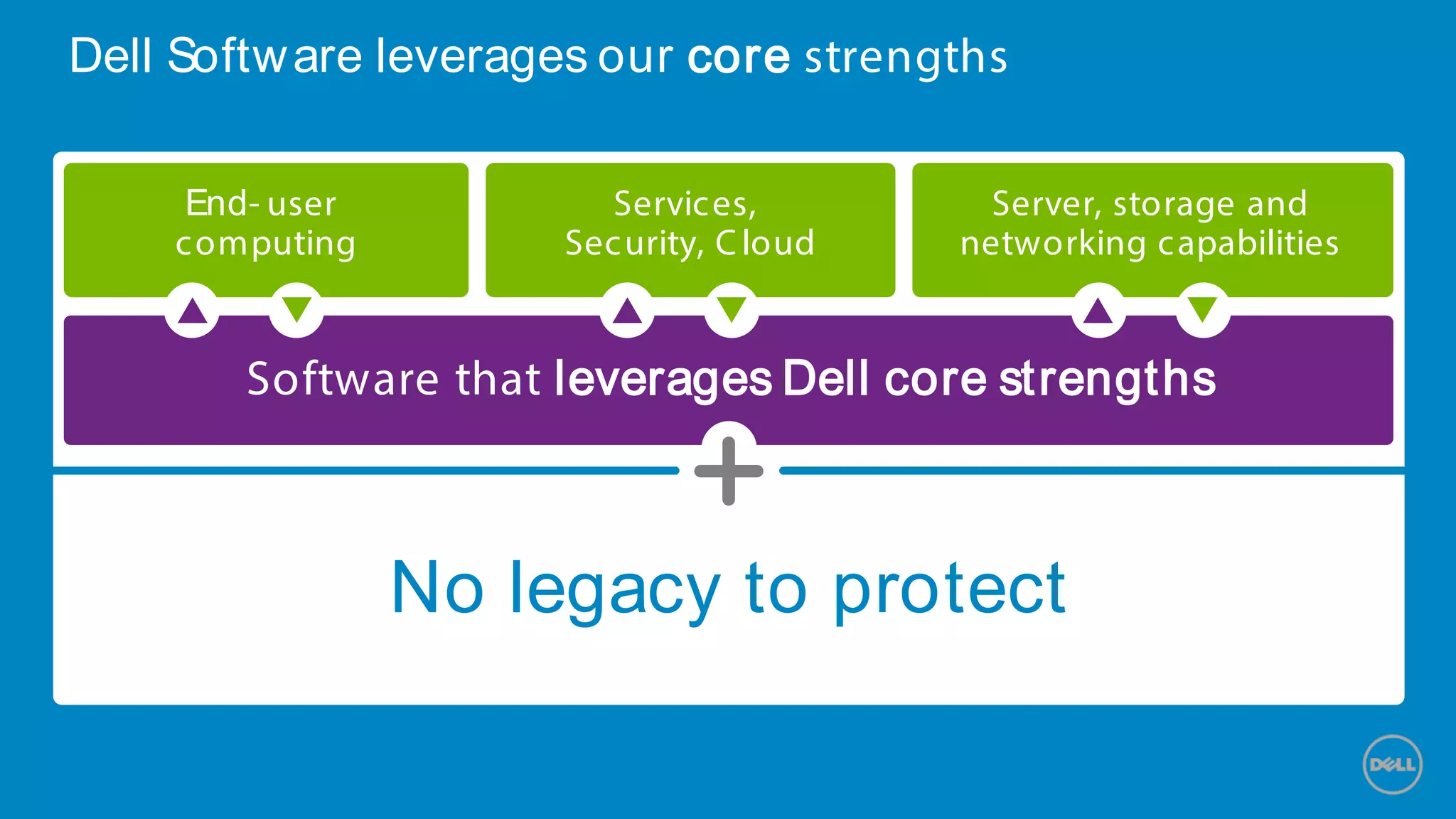
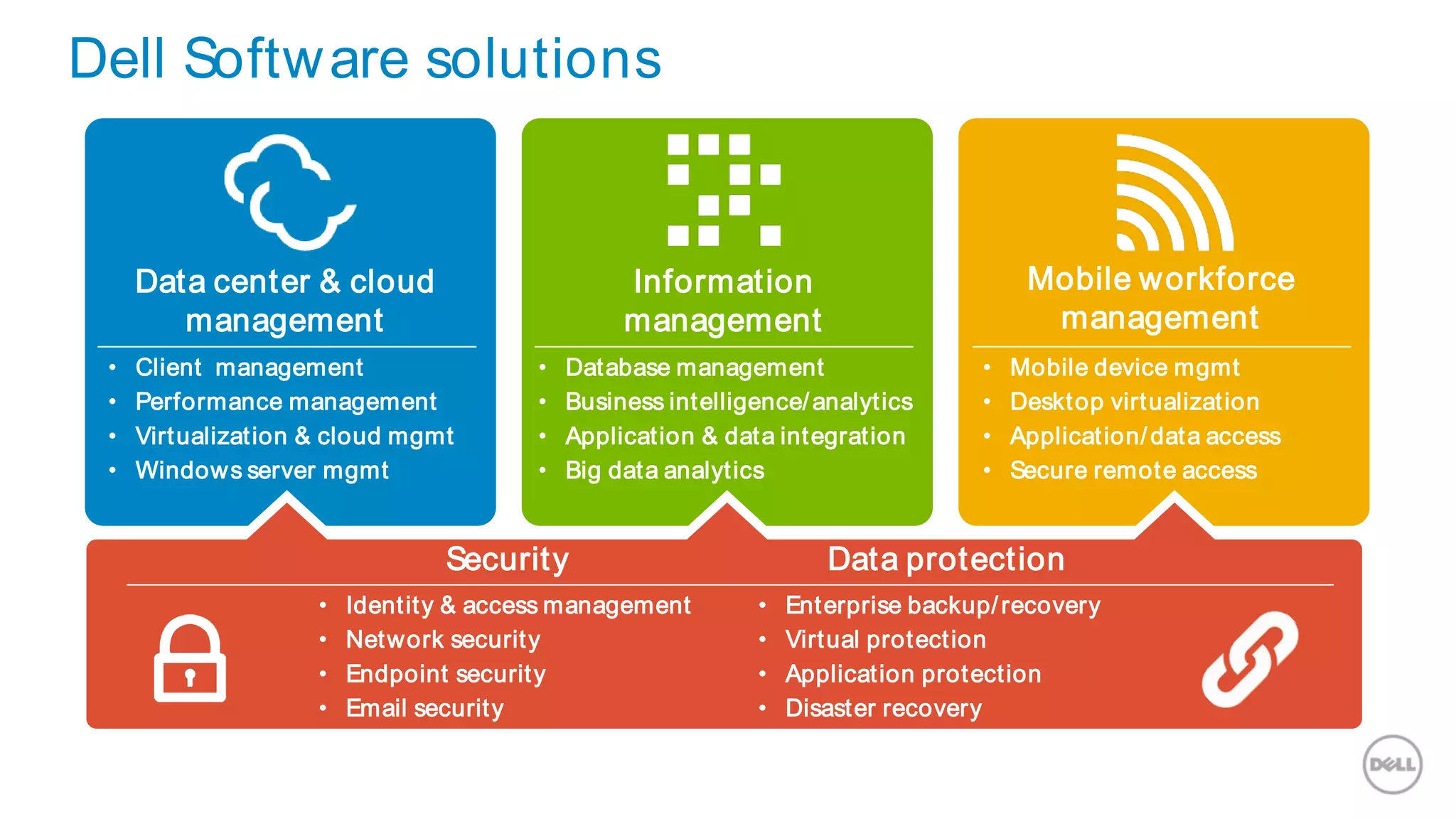
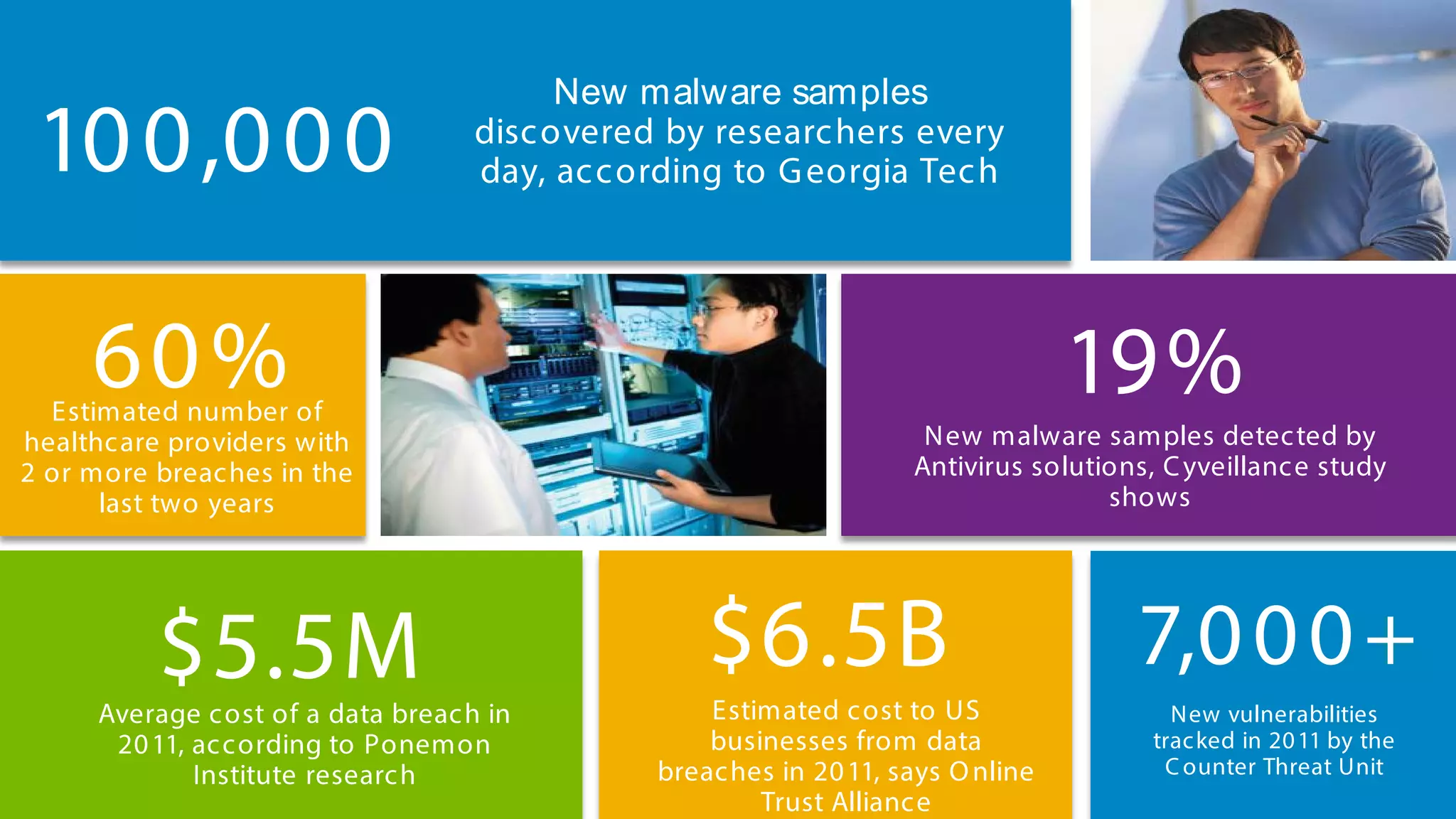
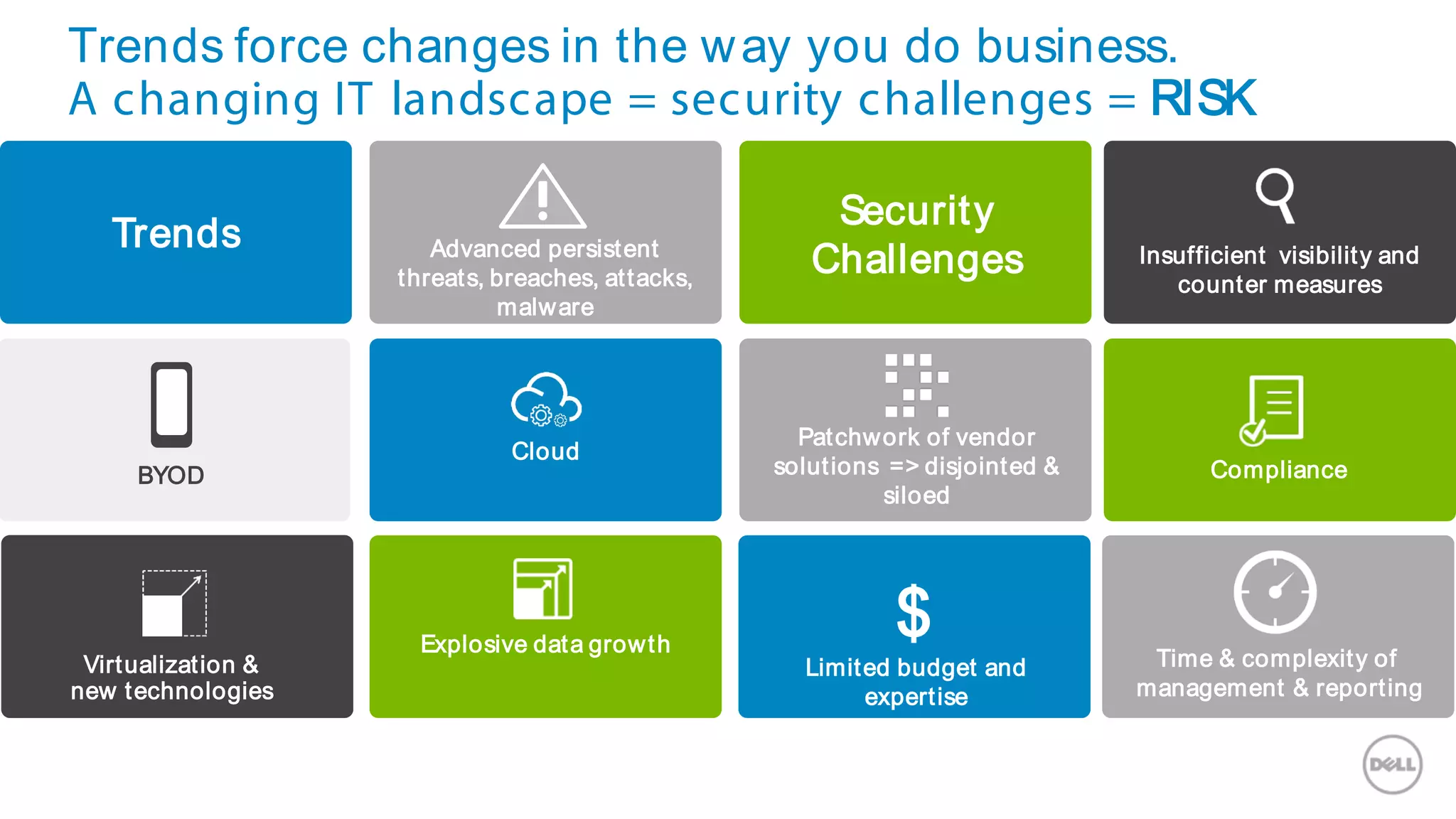
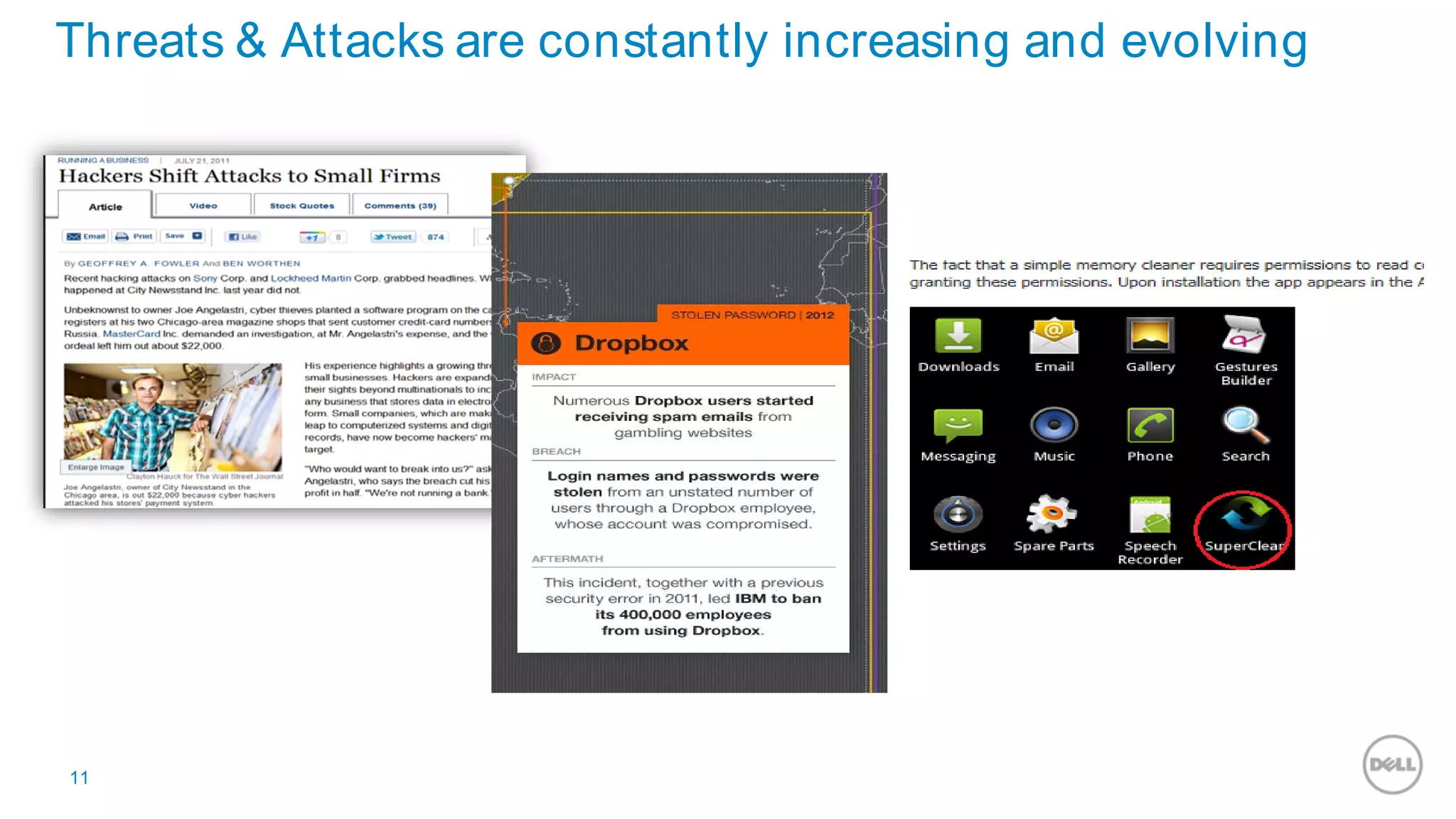
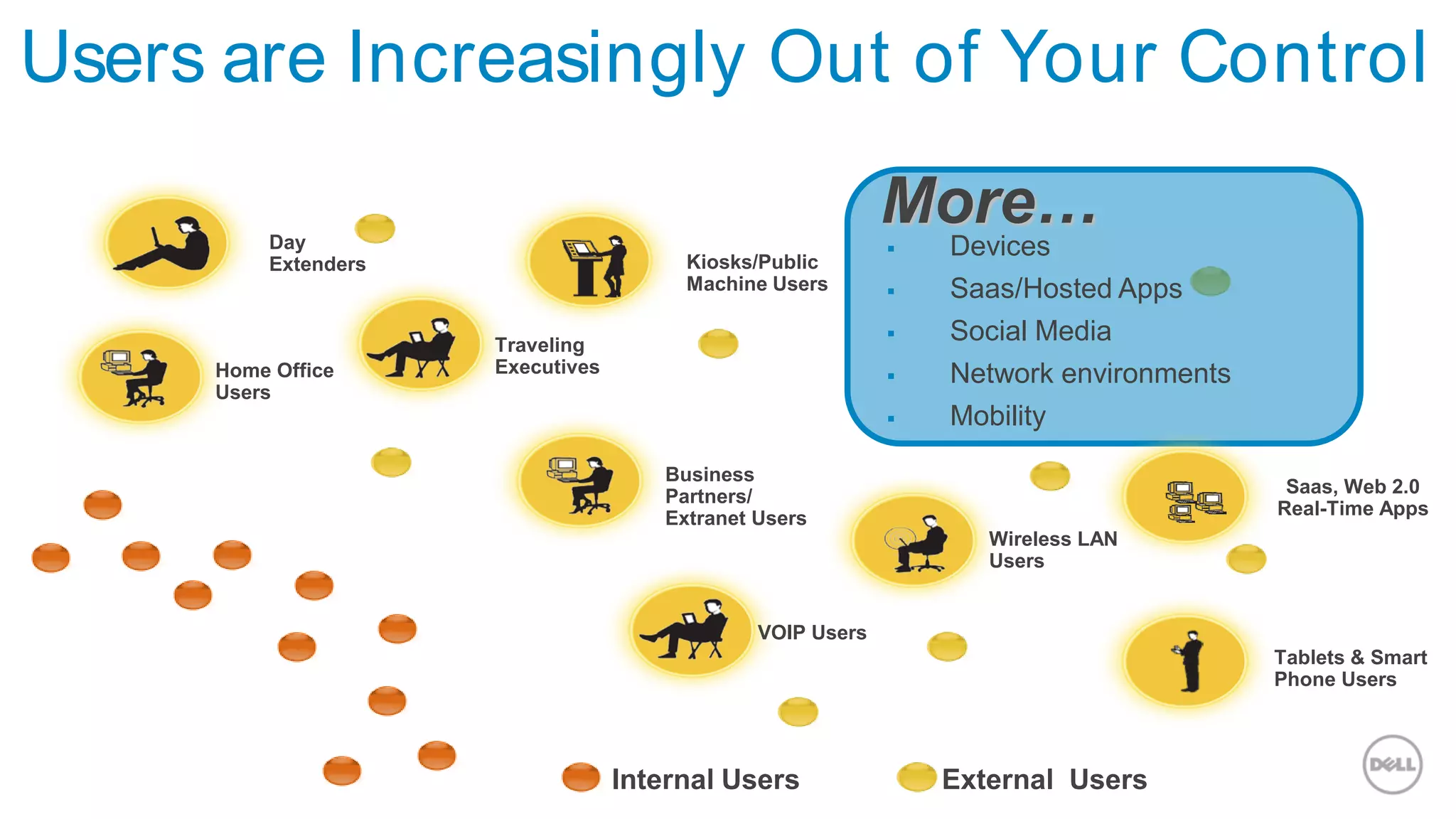
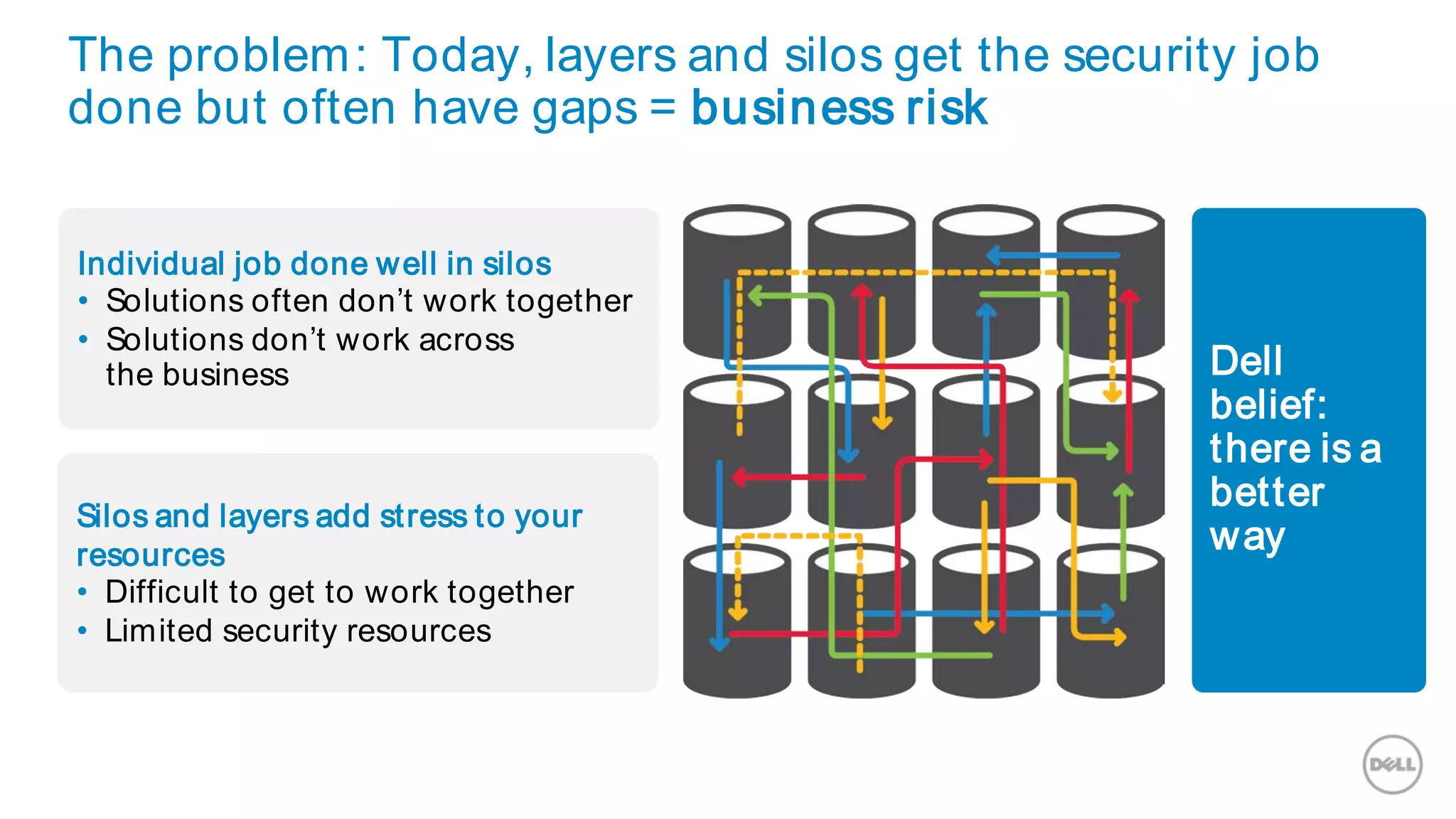
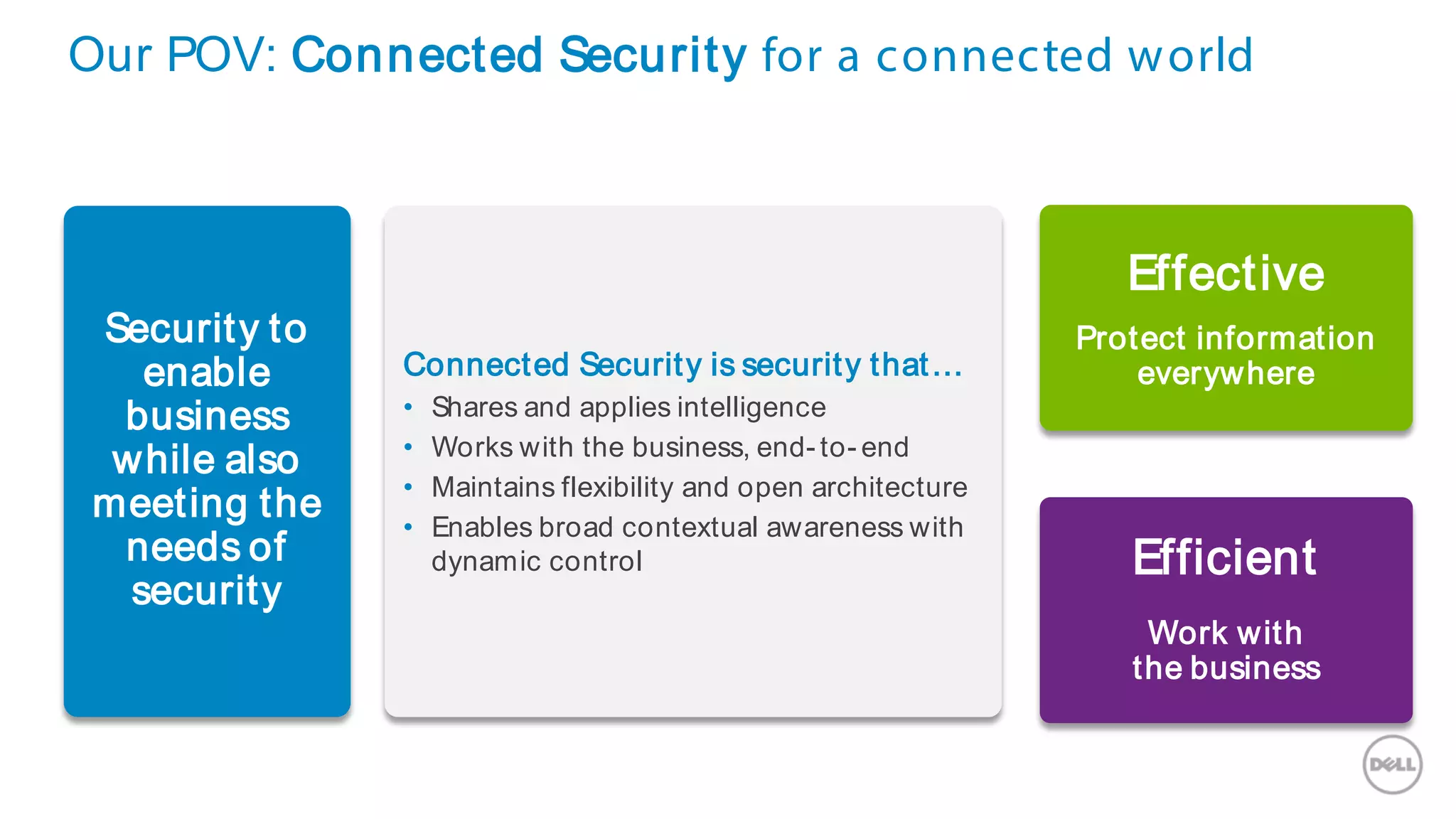
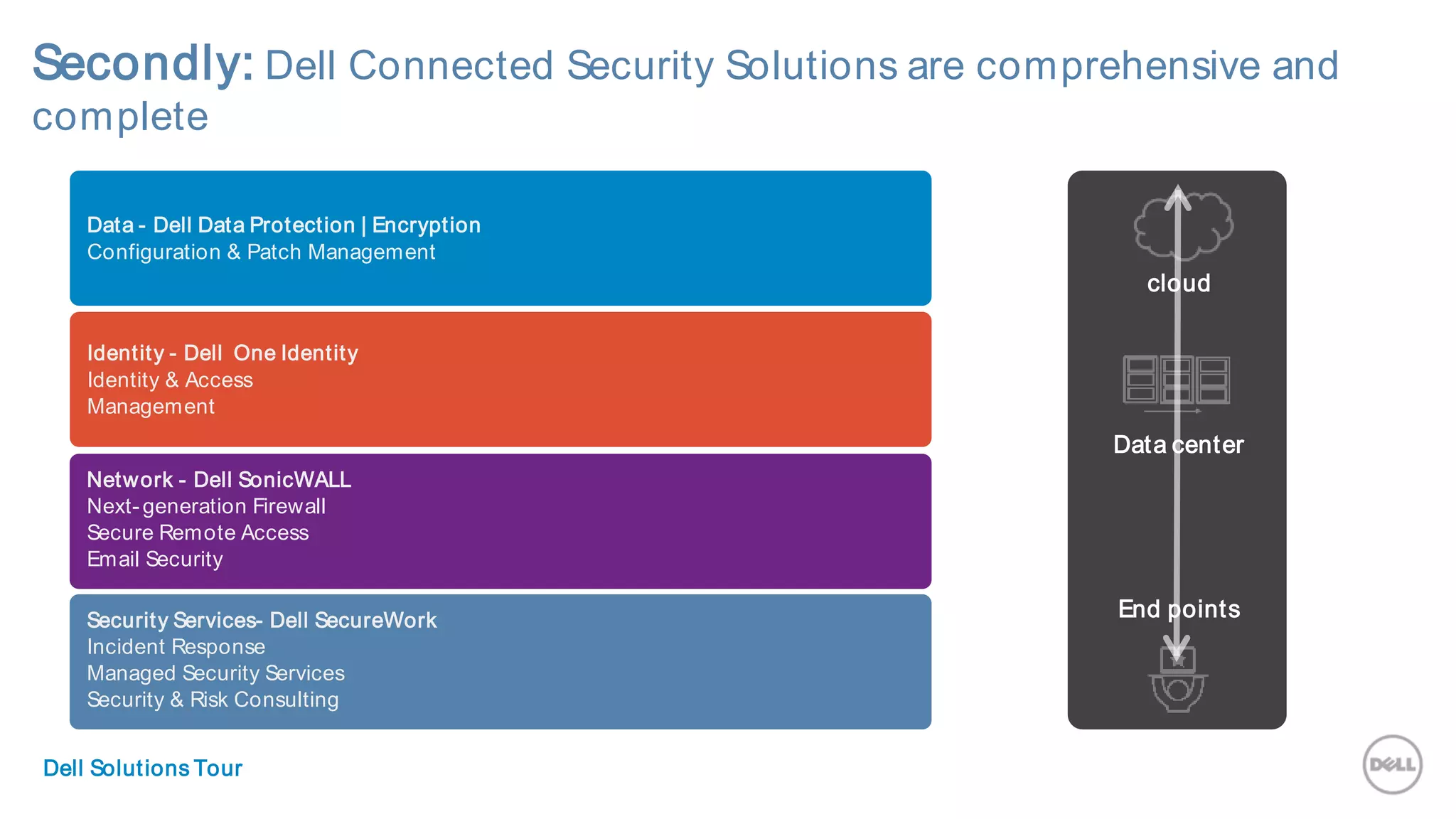
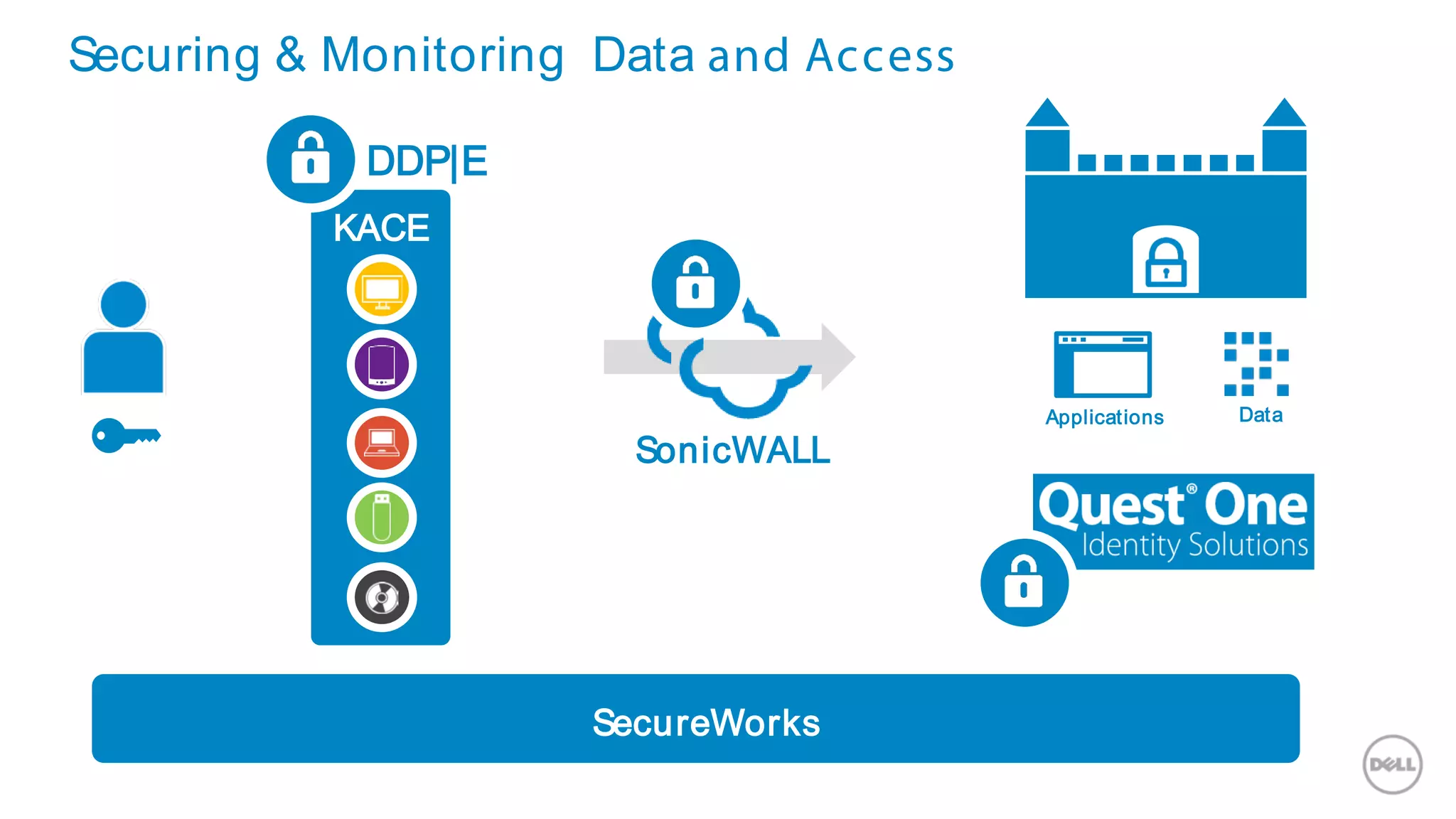
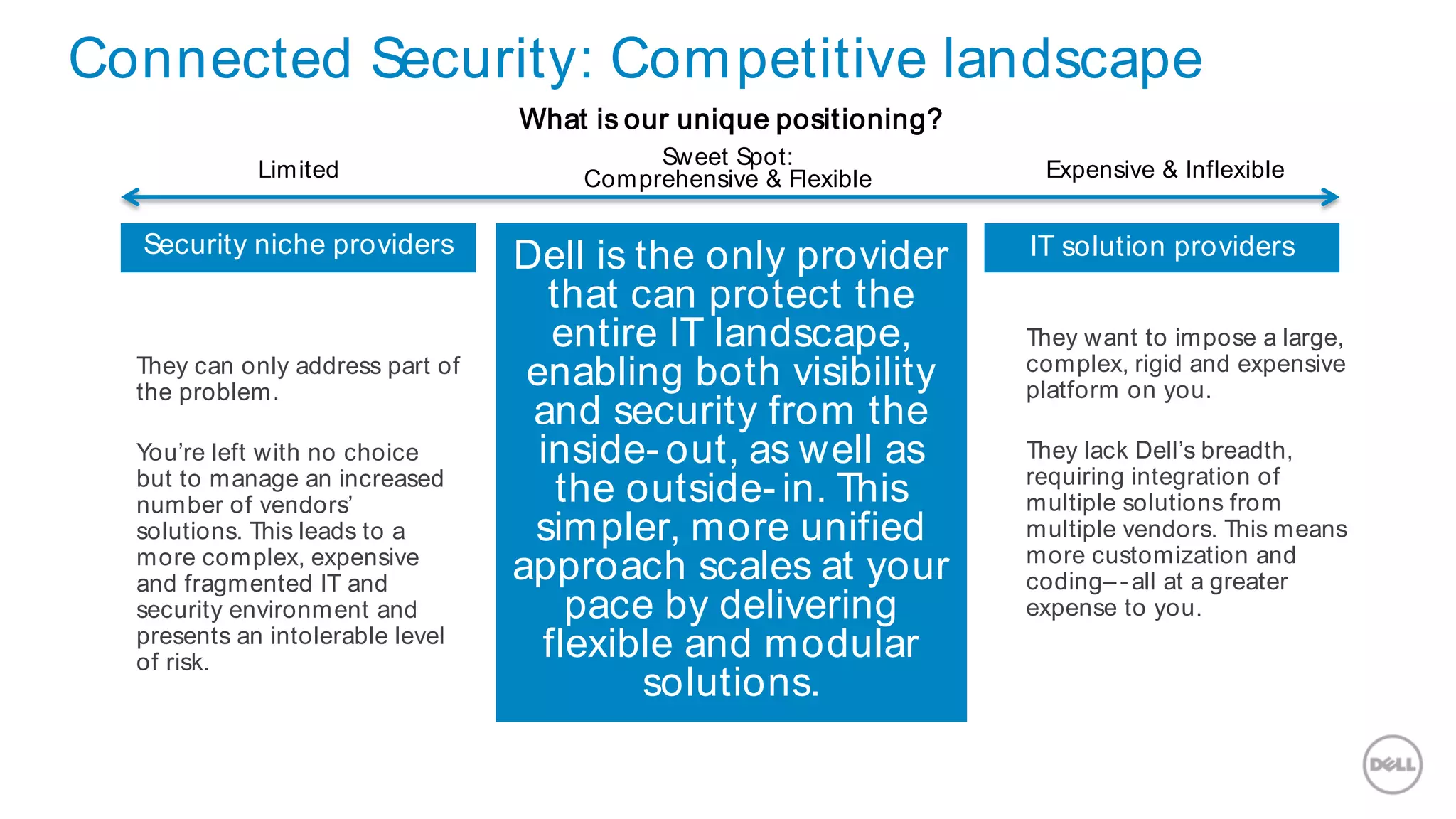
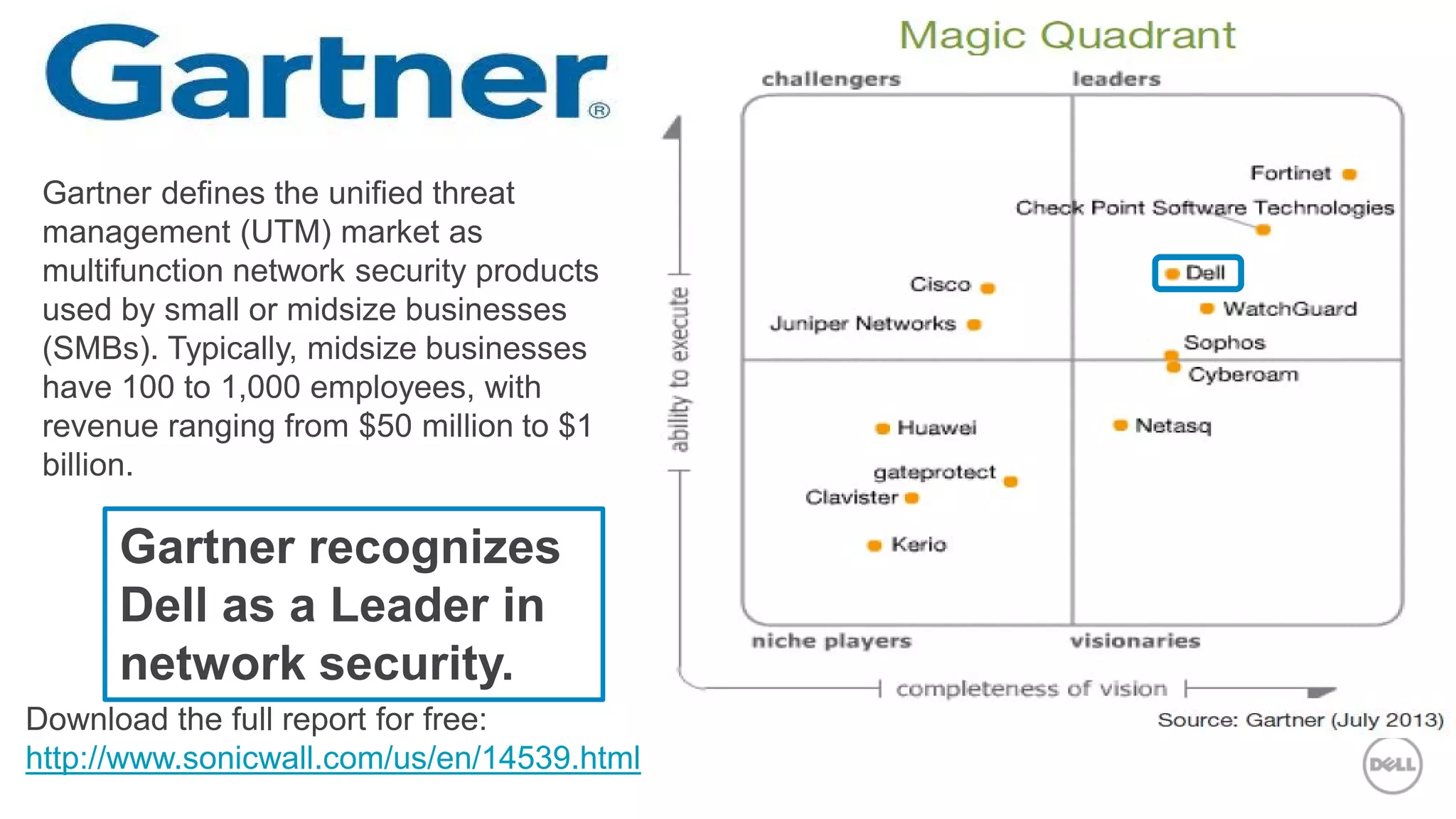
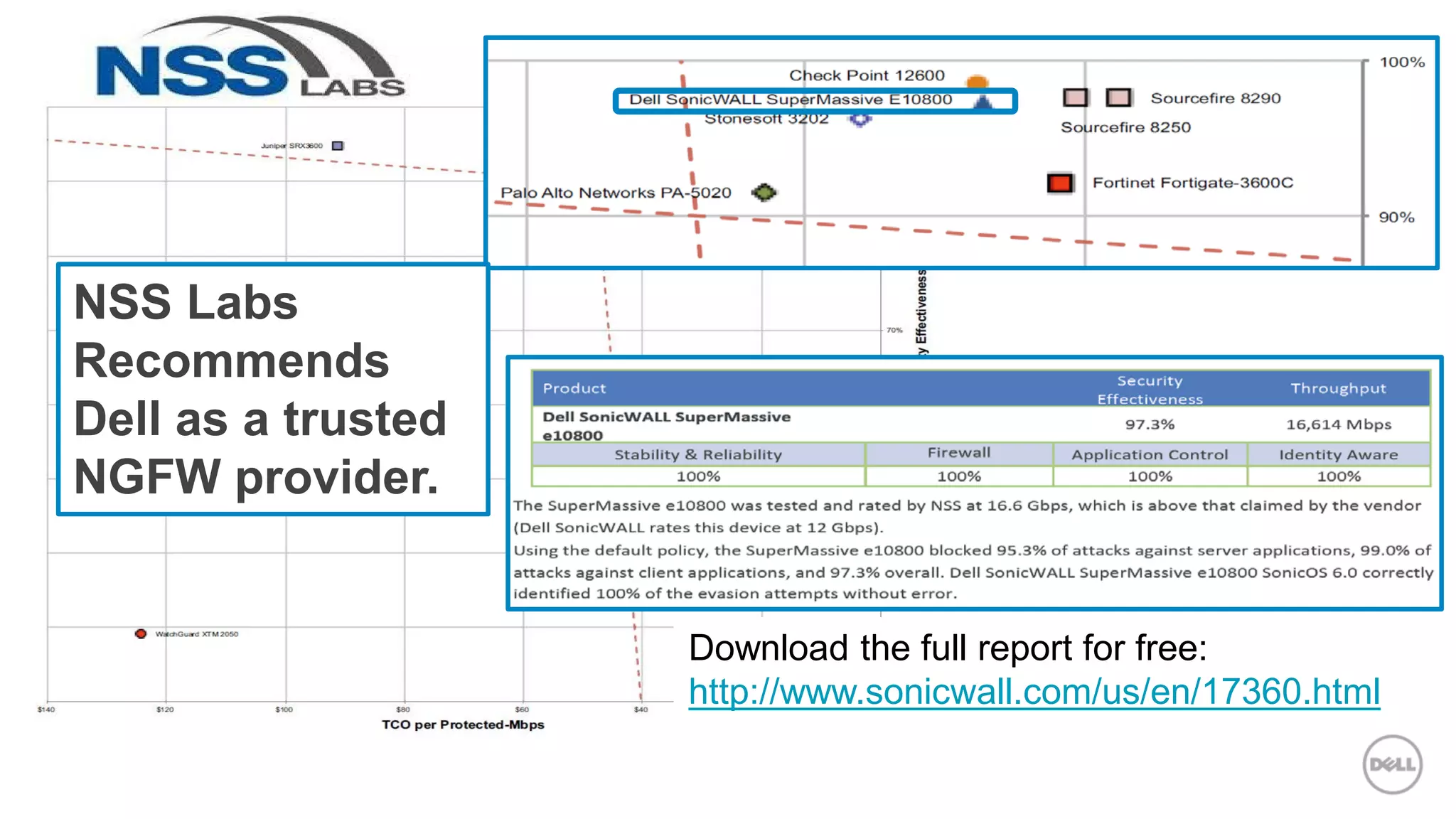
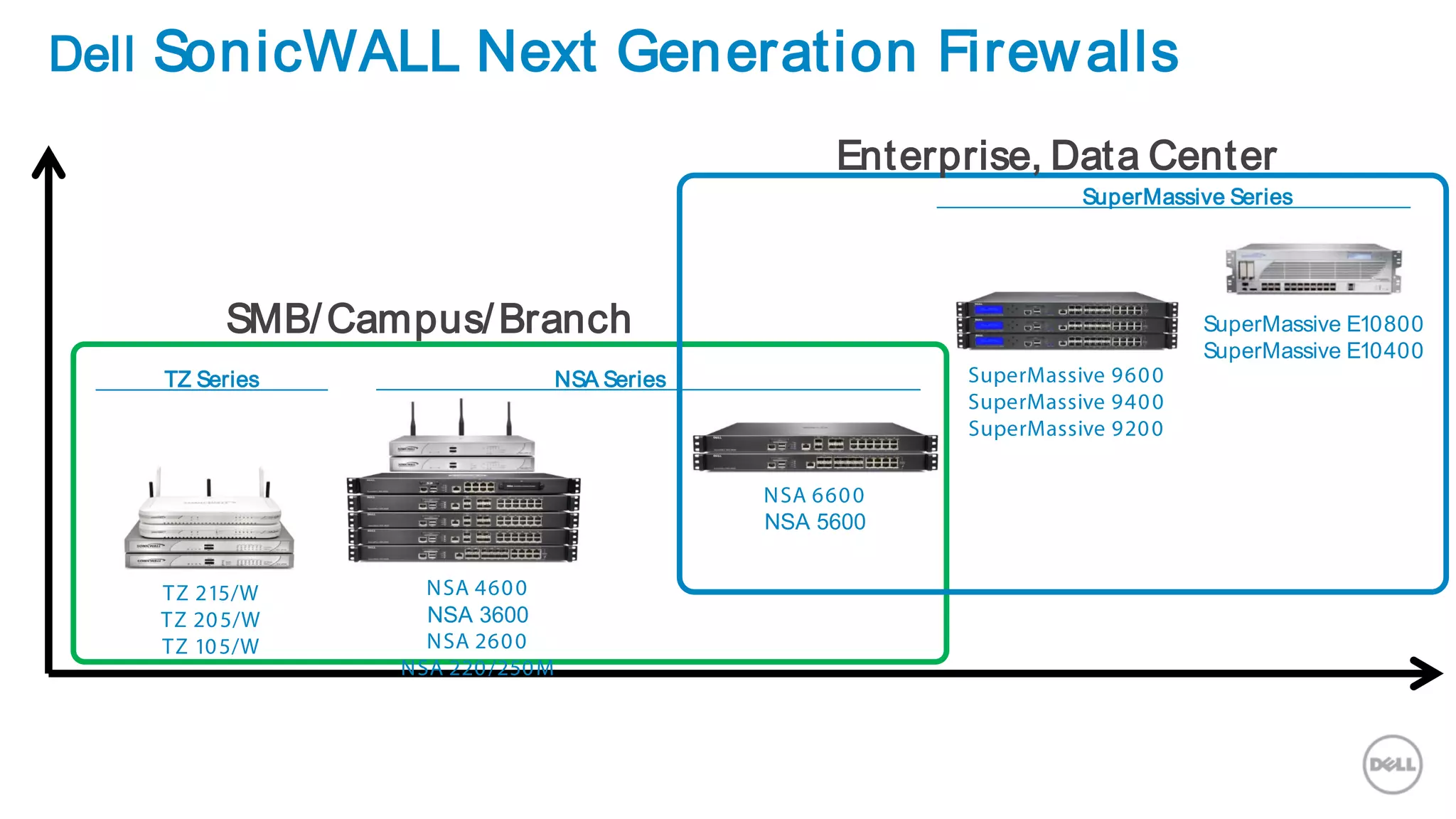
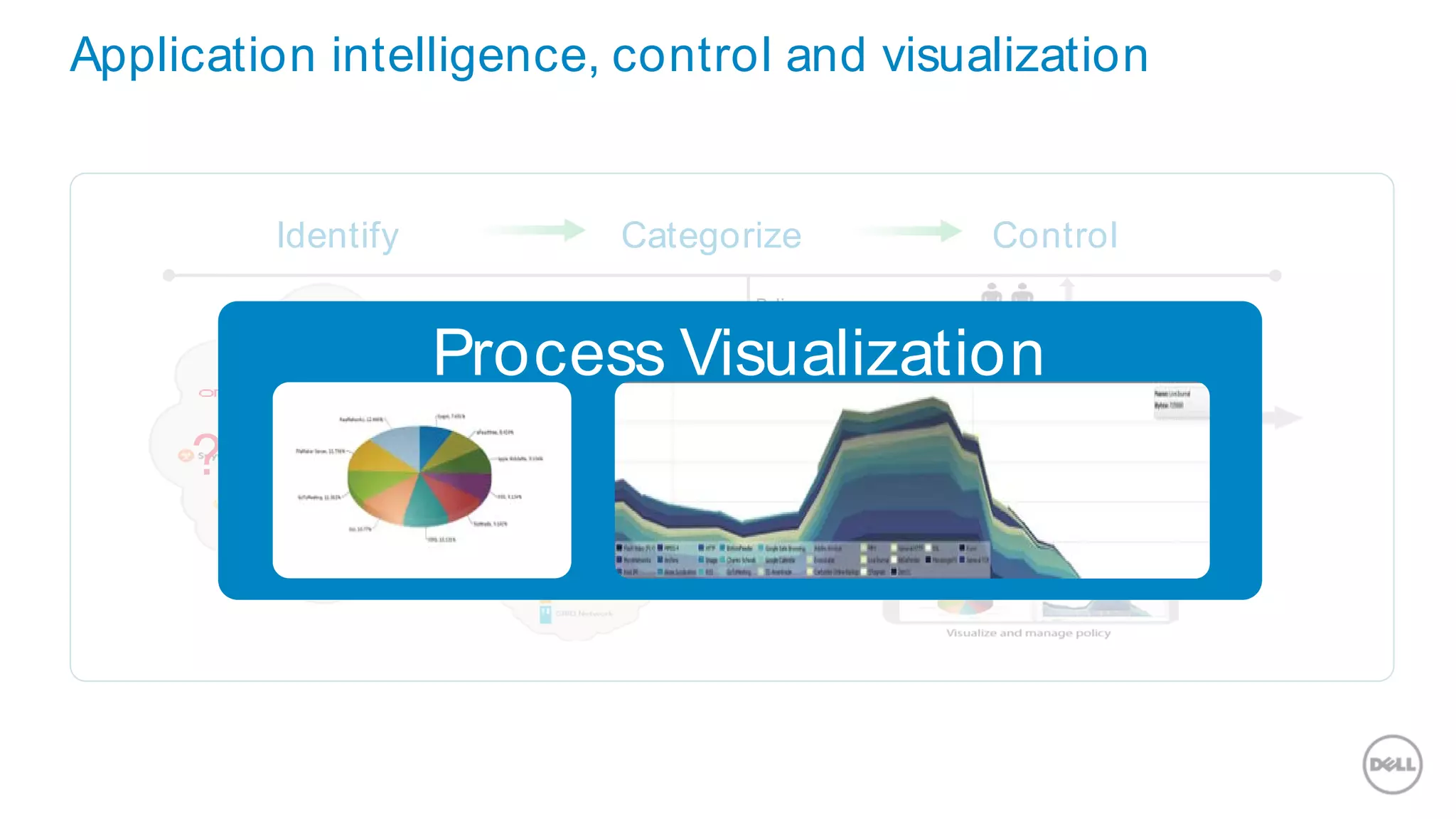
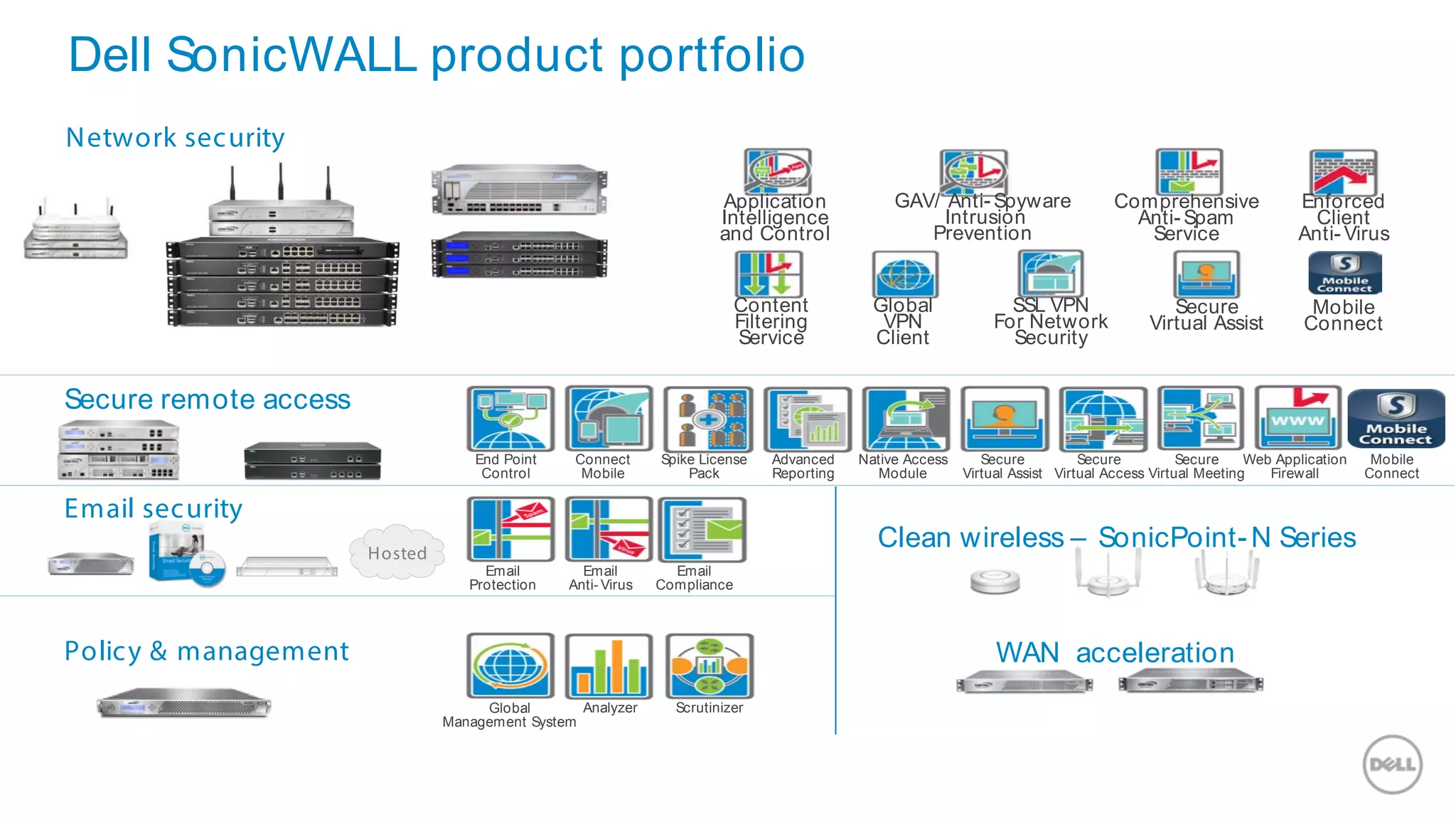
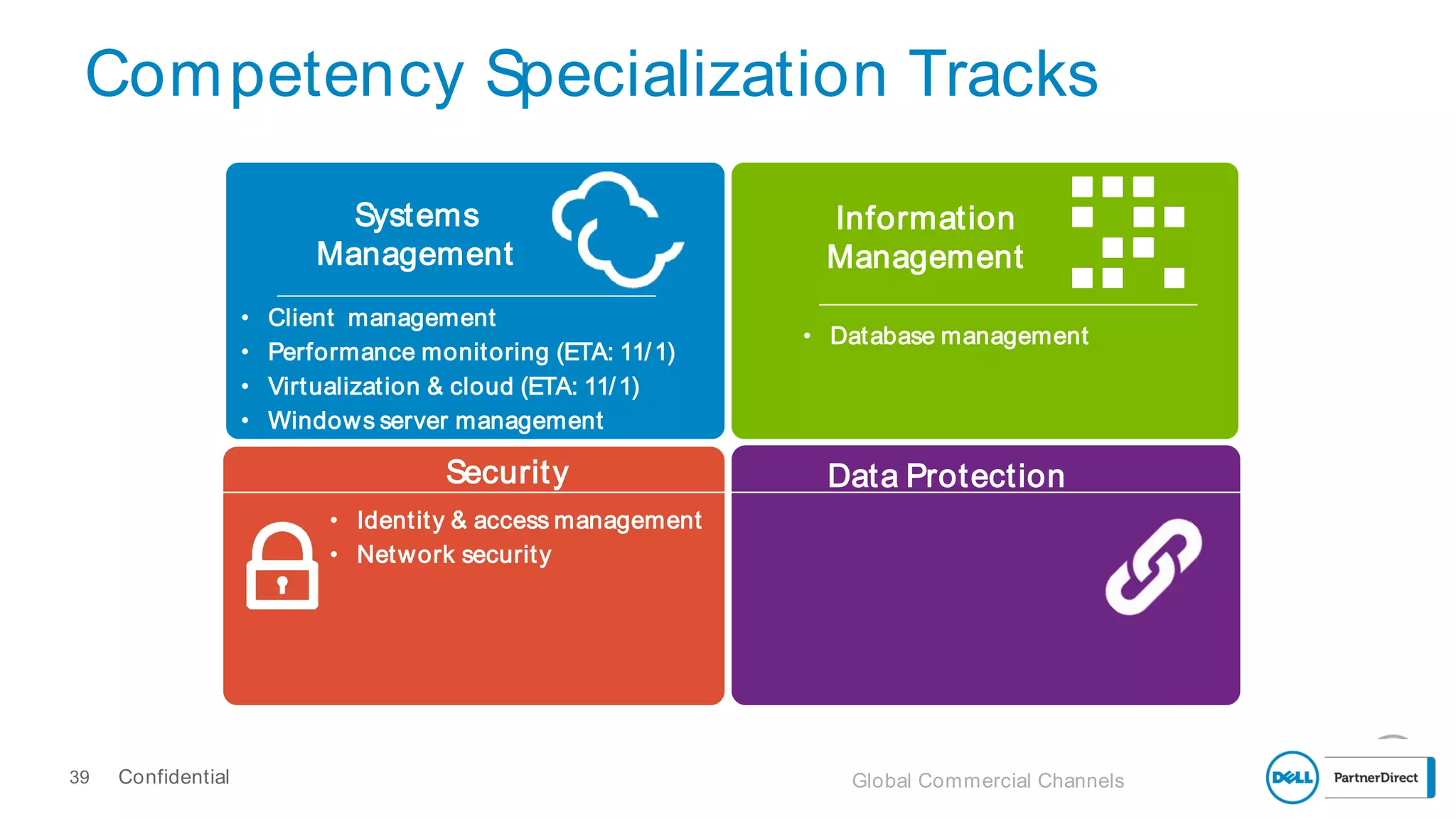
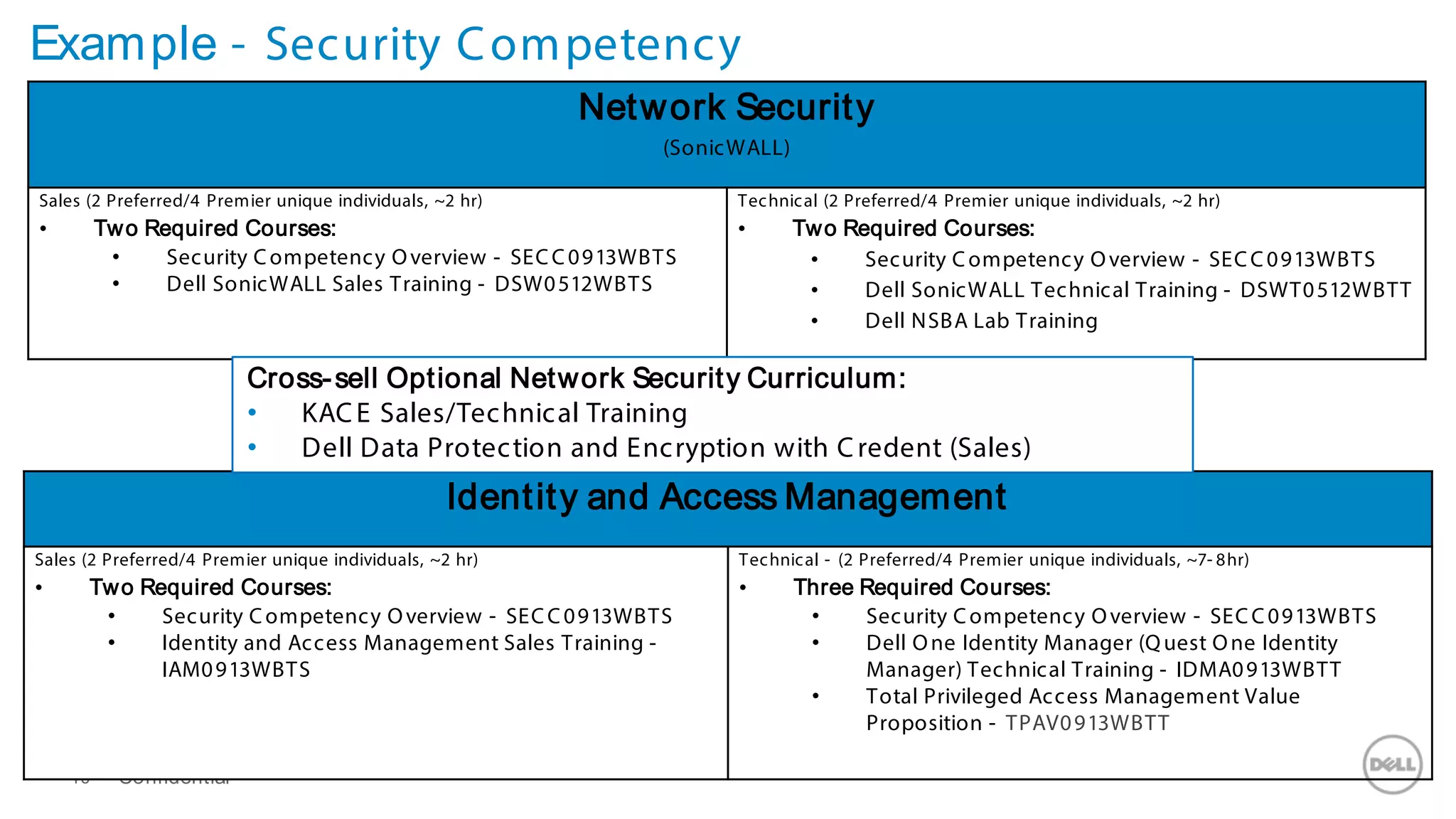
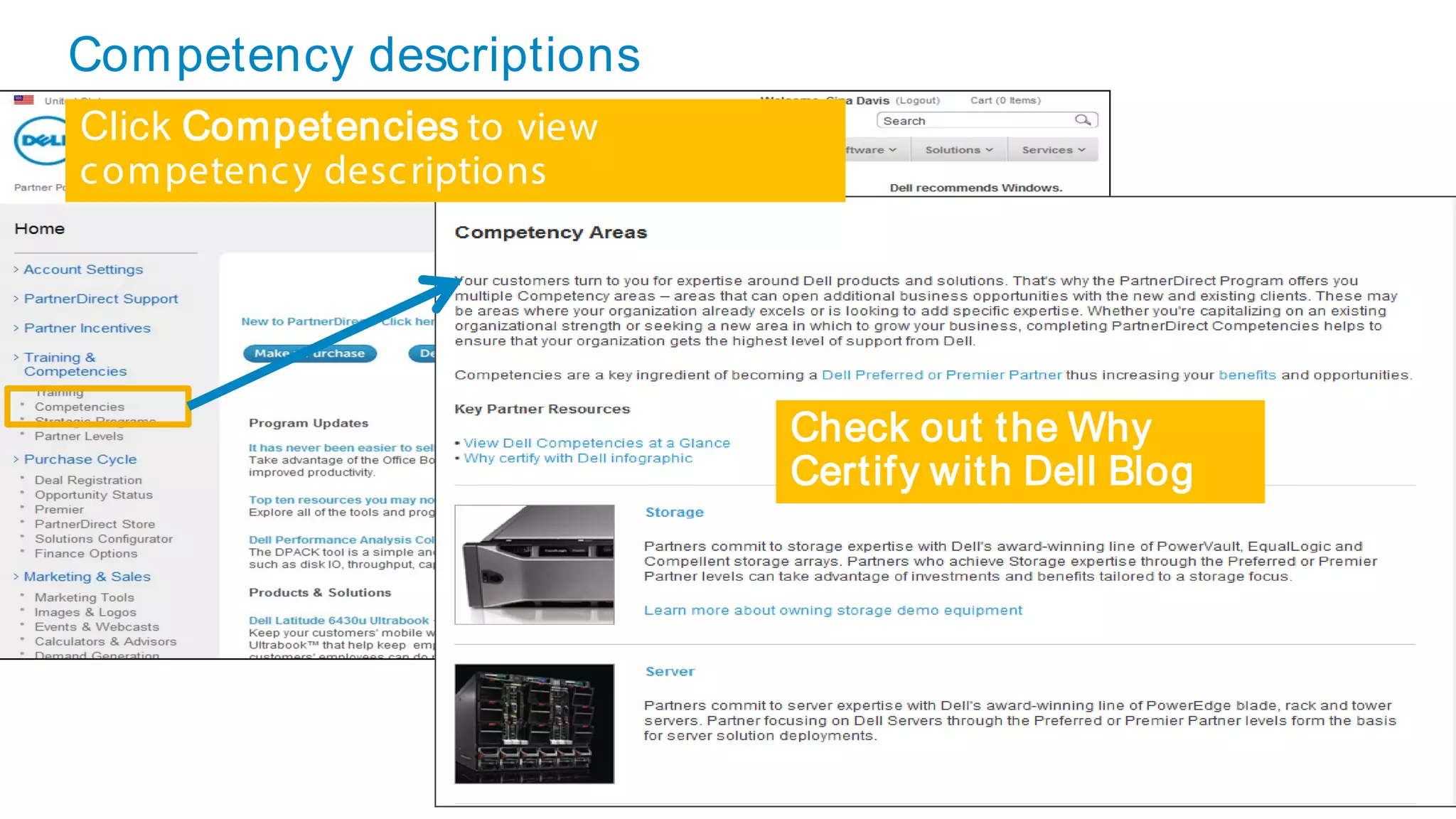
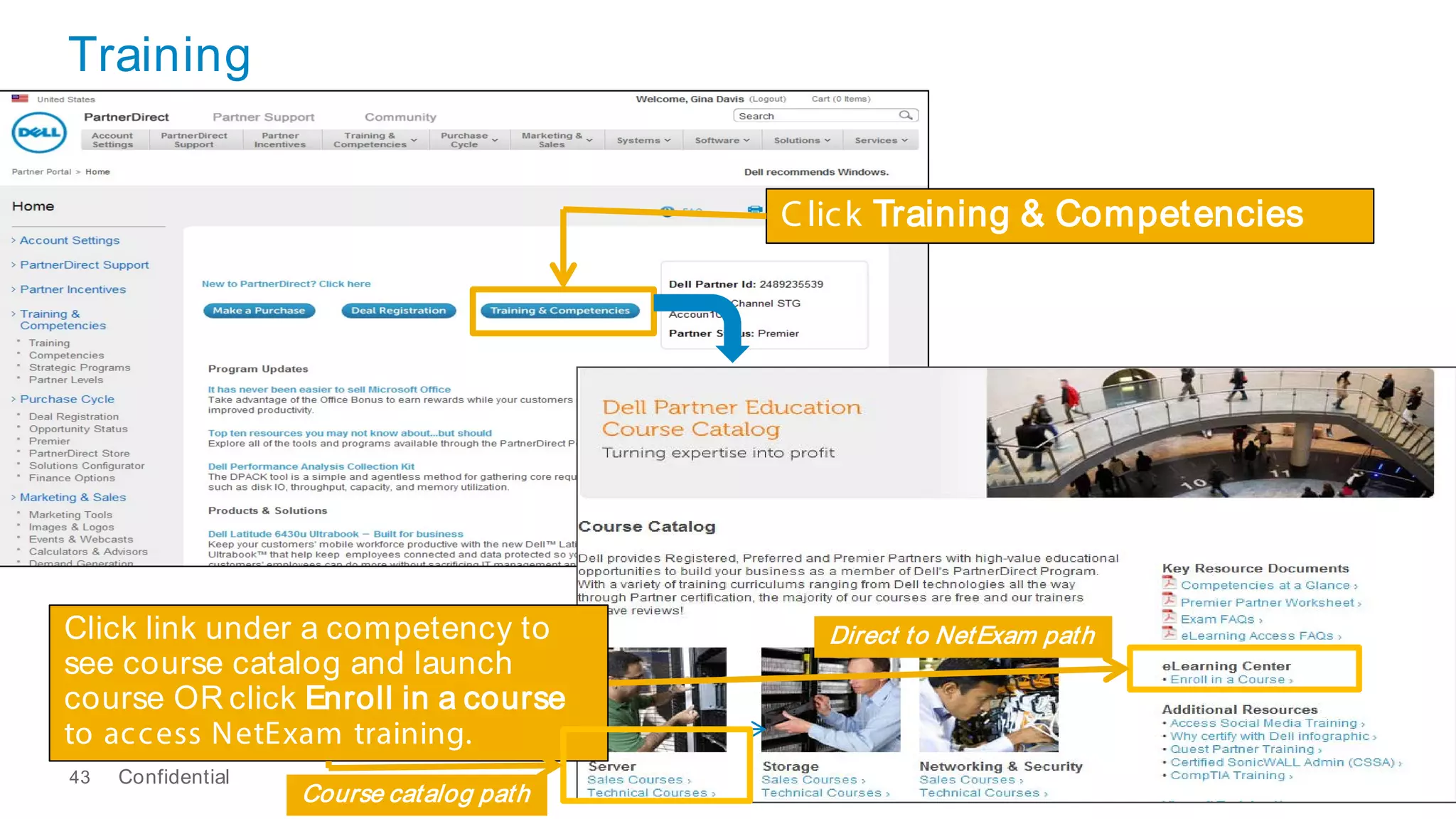
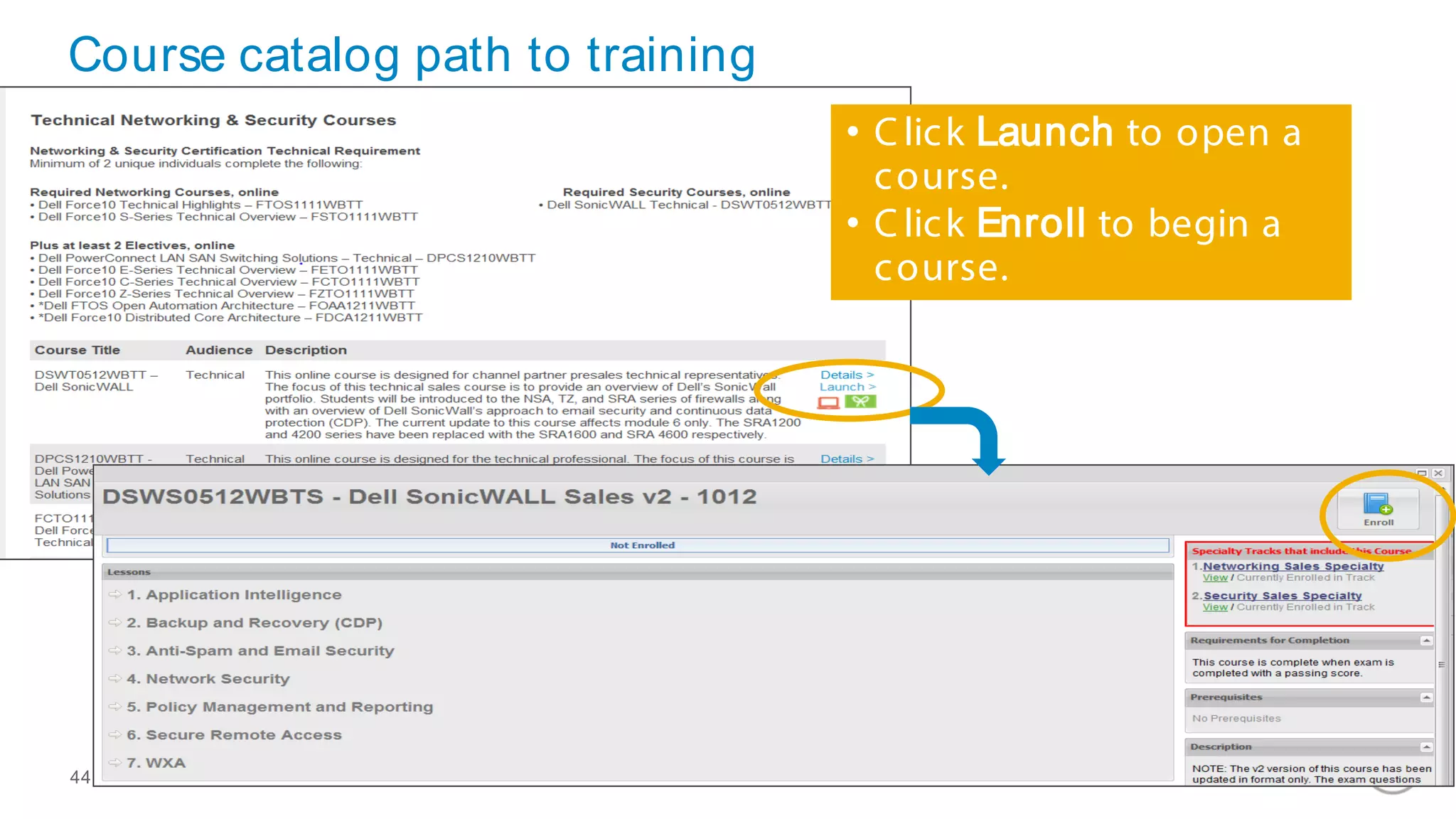
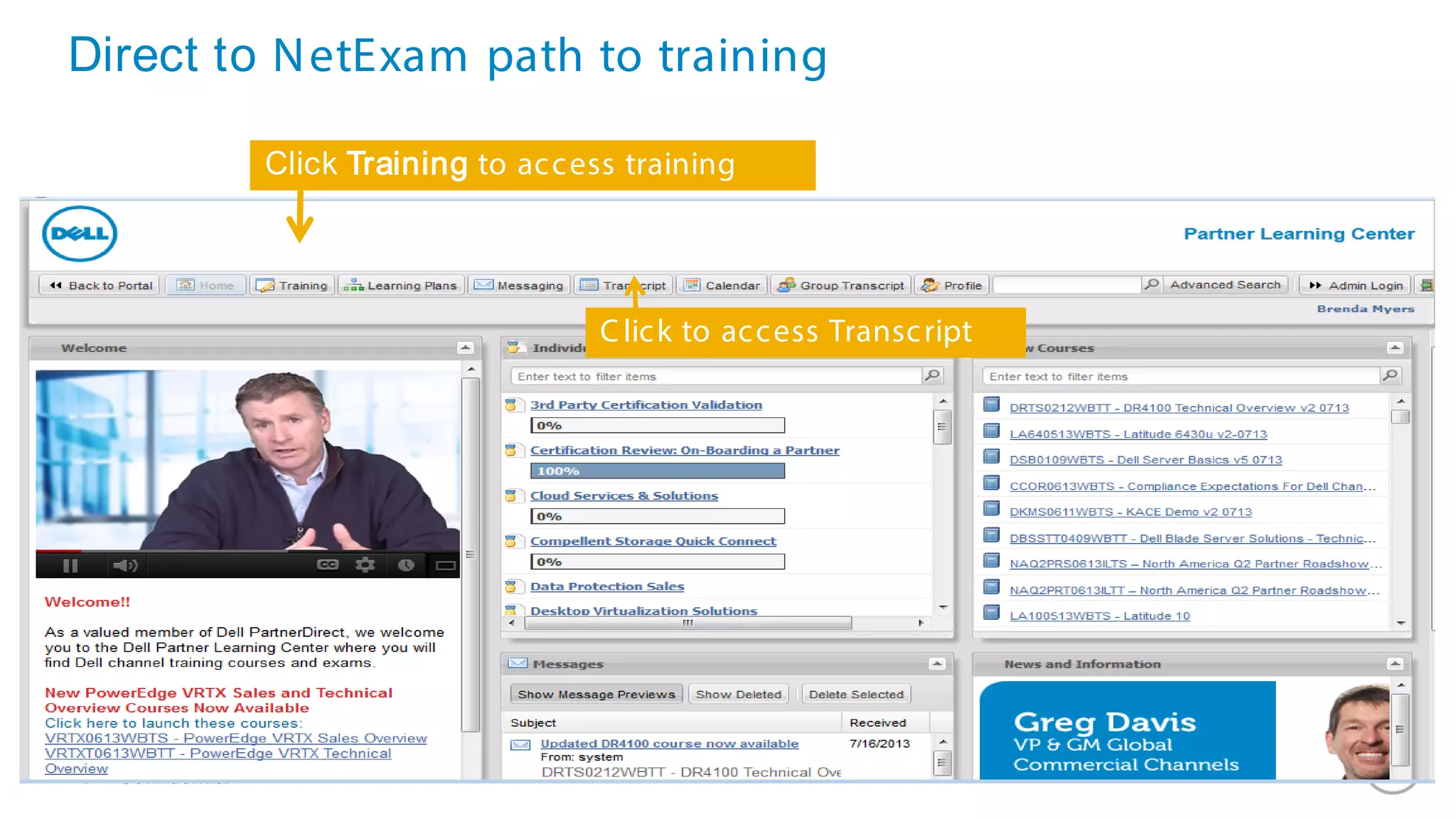
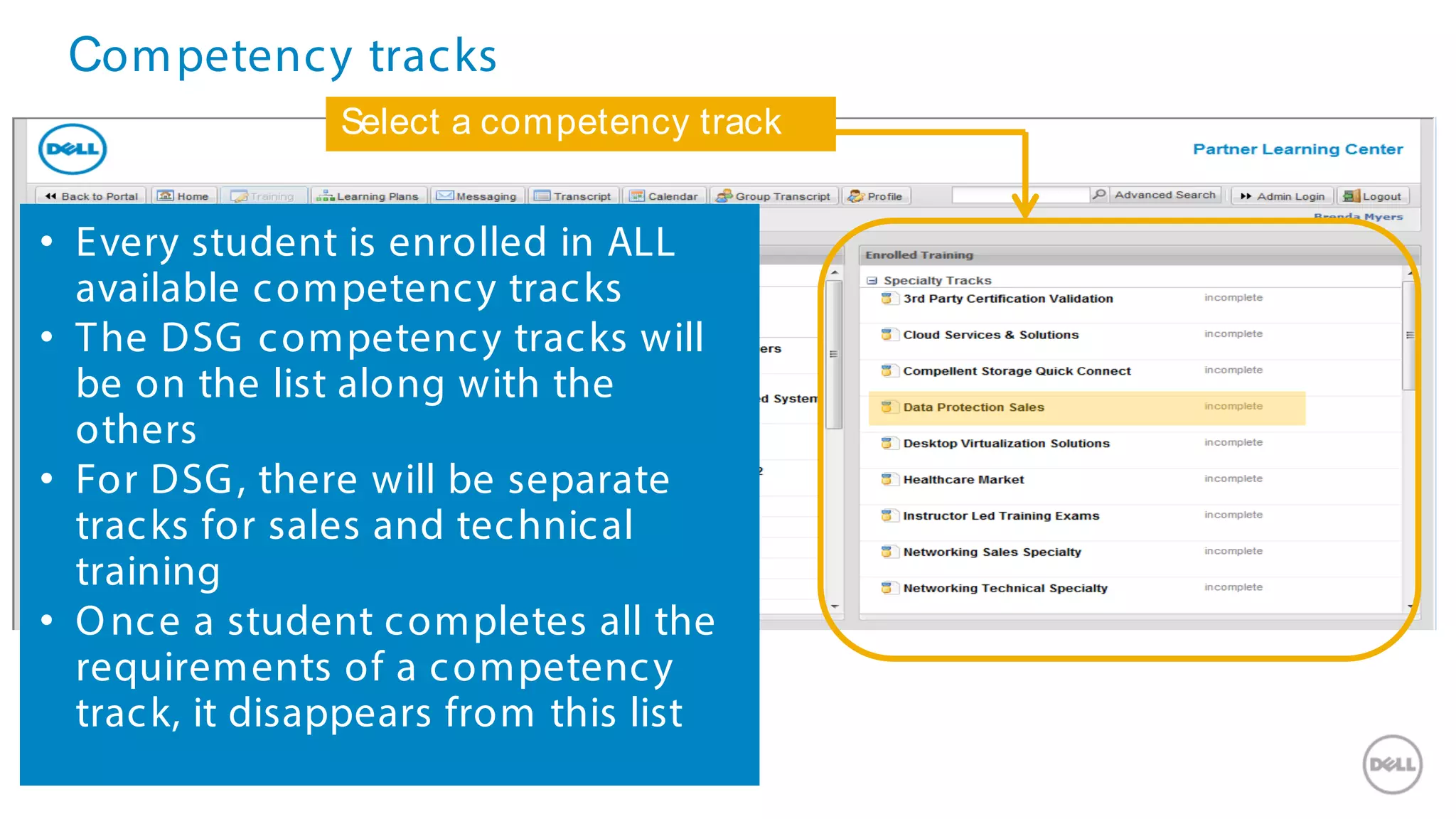
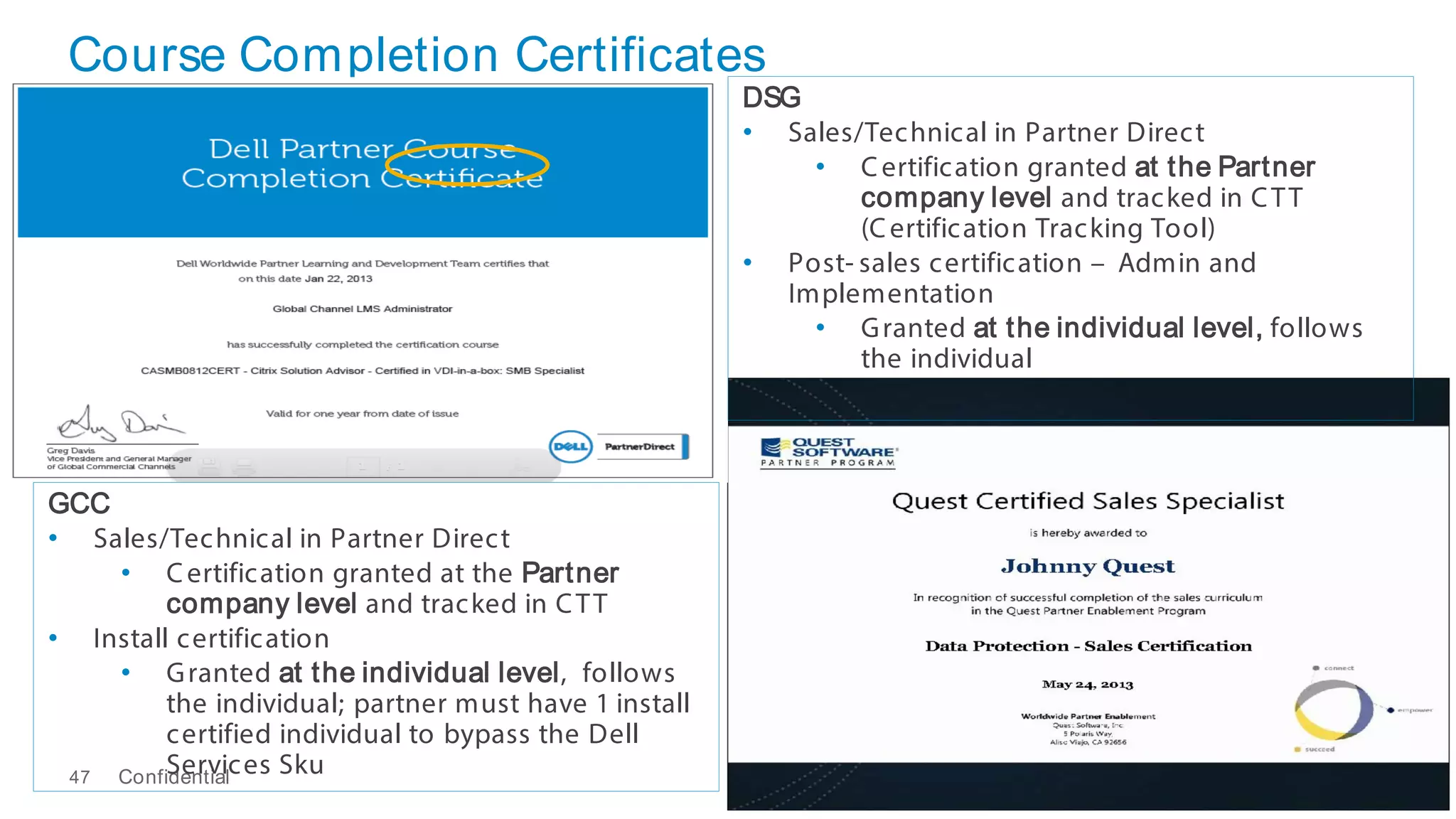
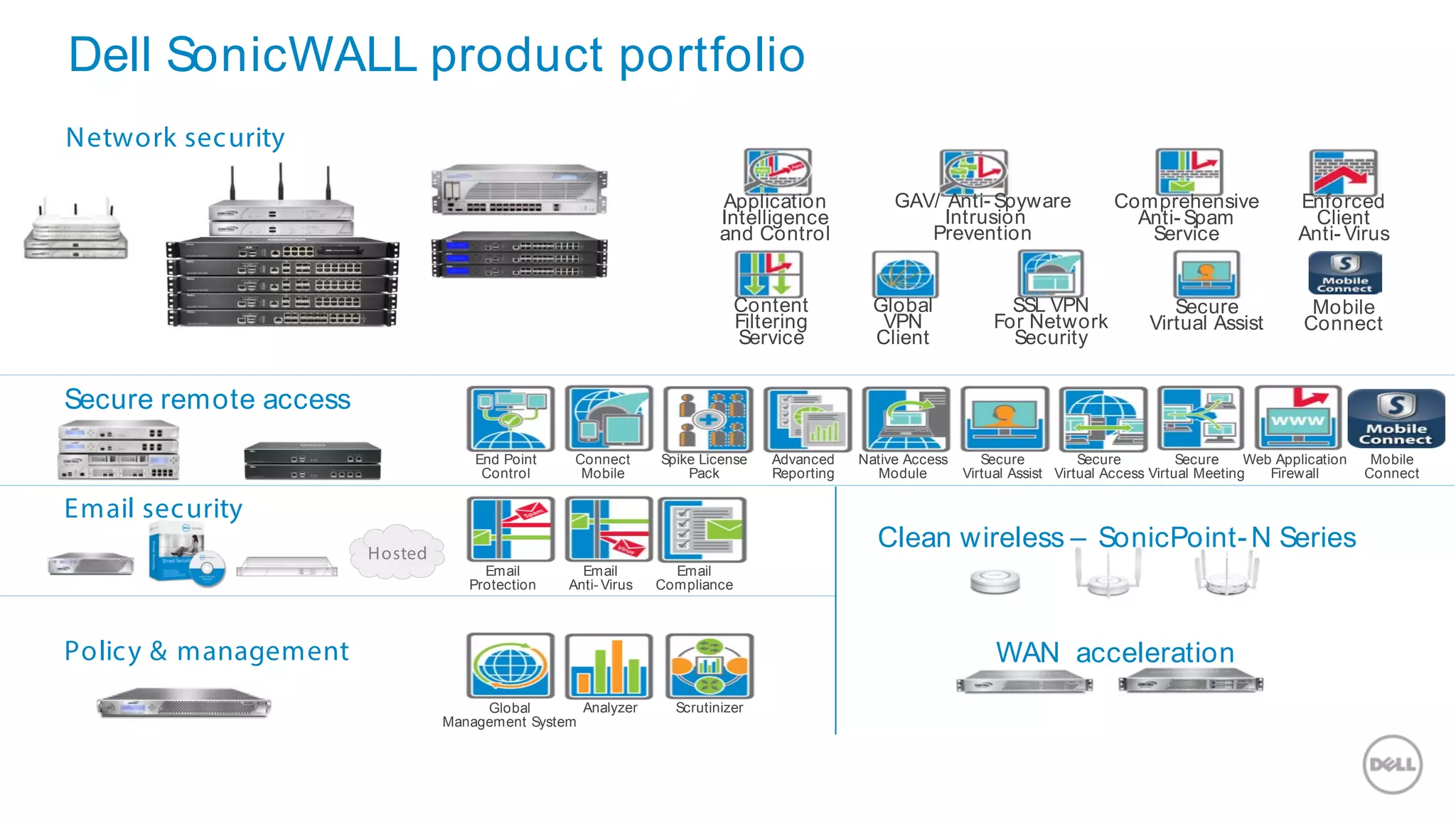
This document discusses Dell's approach to connected security and why Dell is well-positioned to deliver comprehensive yet flexible security solutions. It summarizes Dell's security portfolio, which includes solutions for data protection, identity and access management, network security, security services, and more. It also outlines Dell's partner program and competency tracks to help partners sell, implement, and support Dell's connected security offerings.