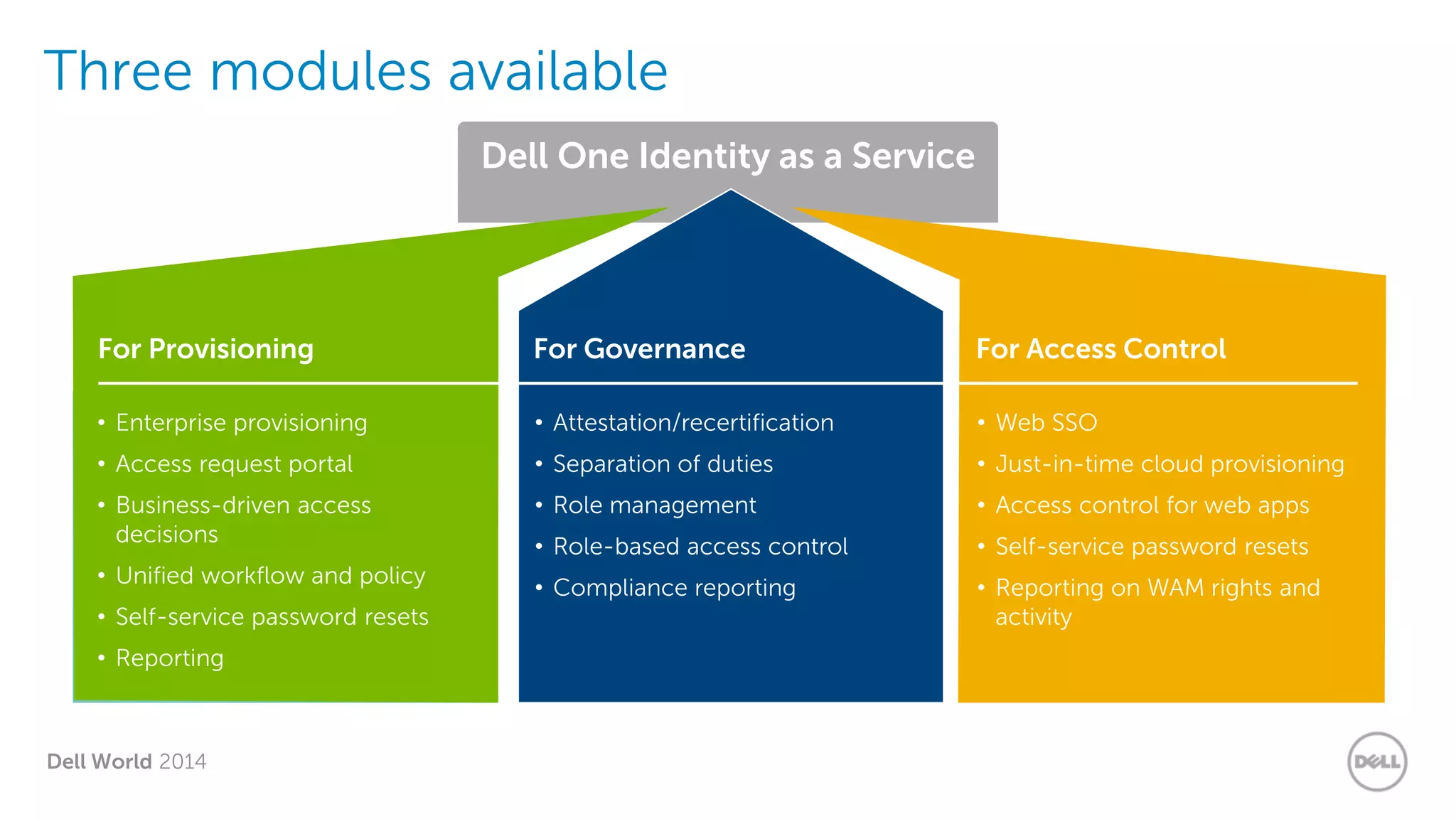
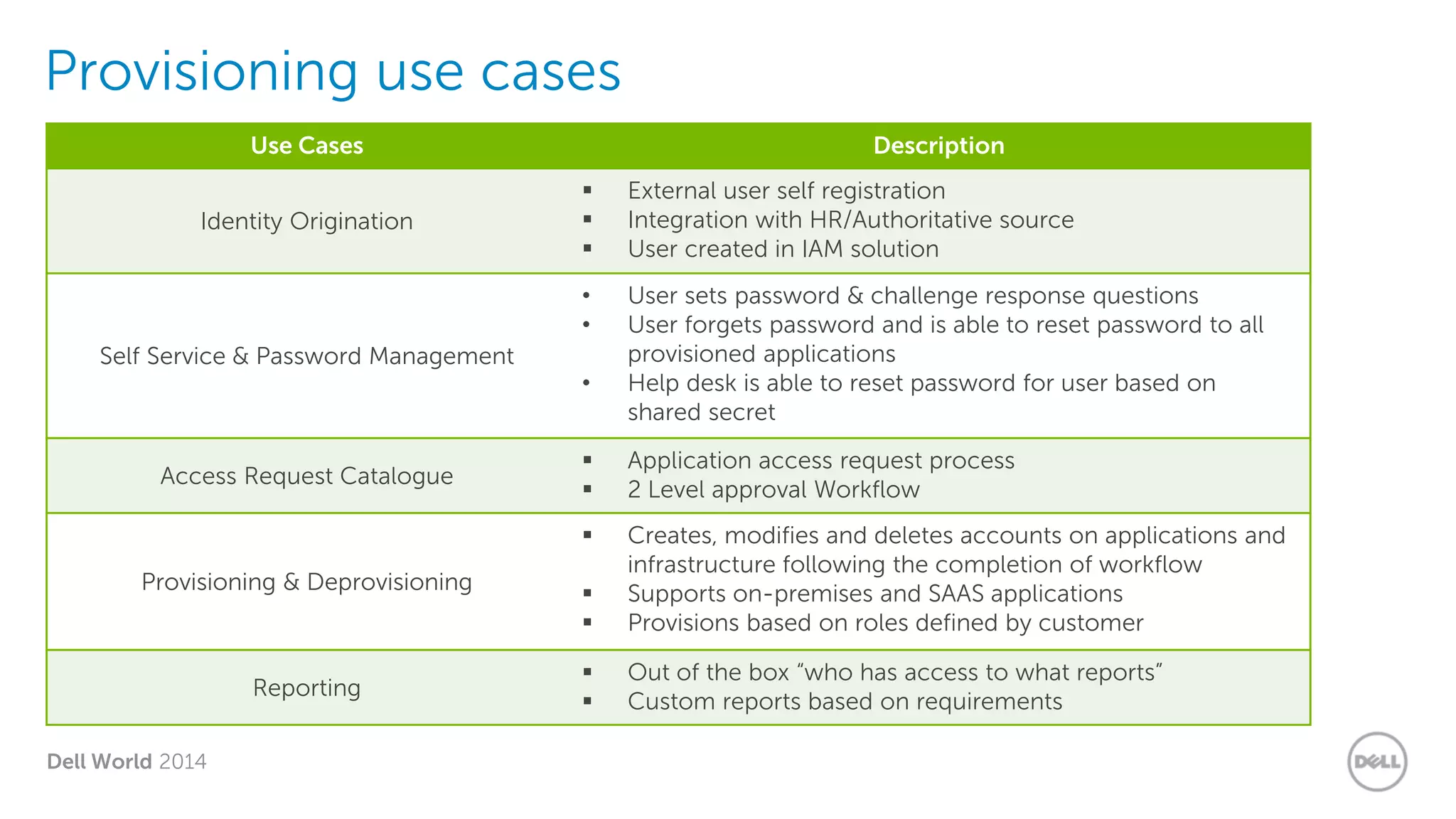
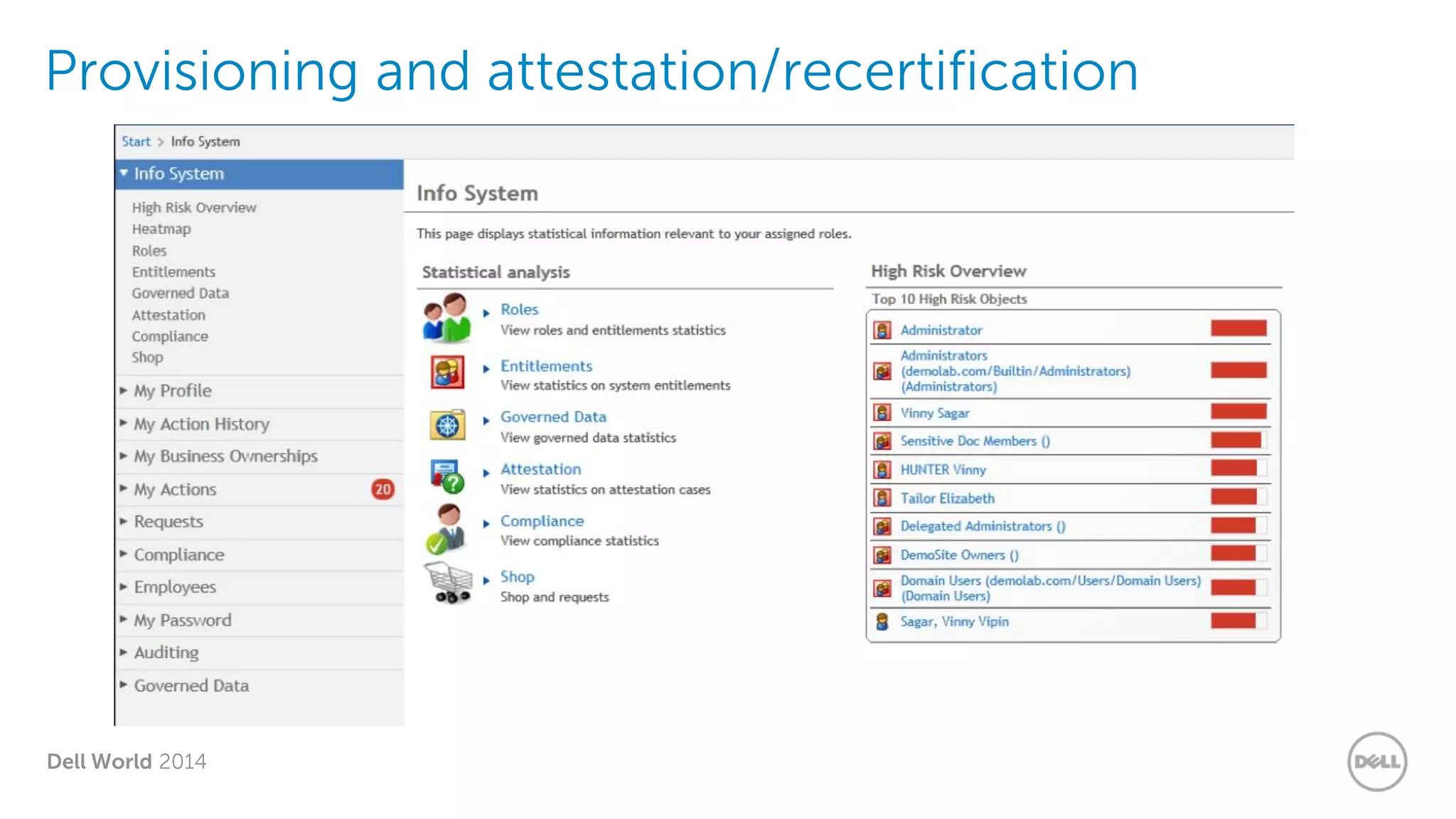
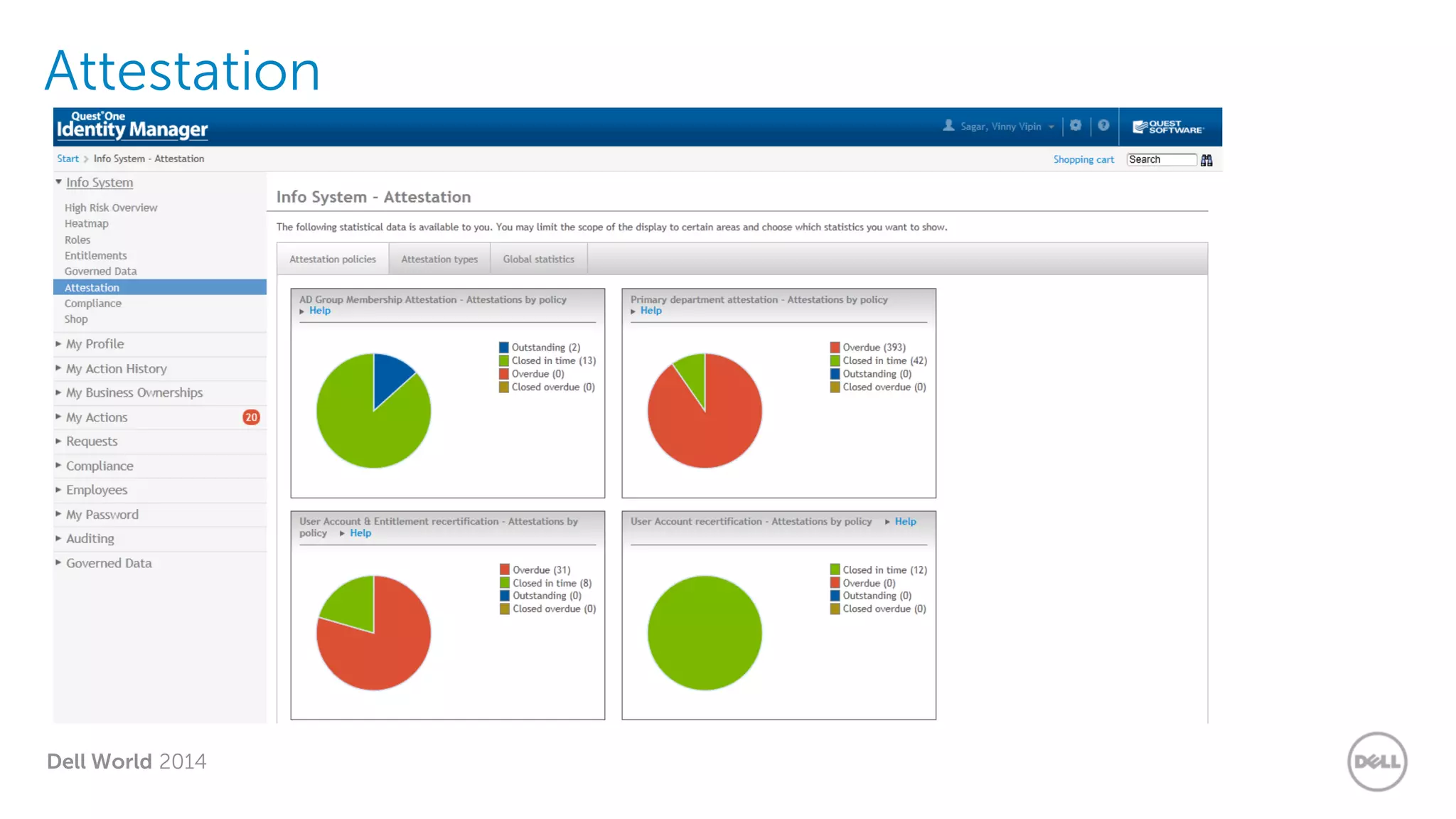
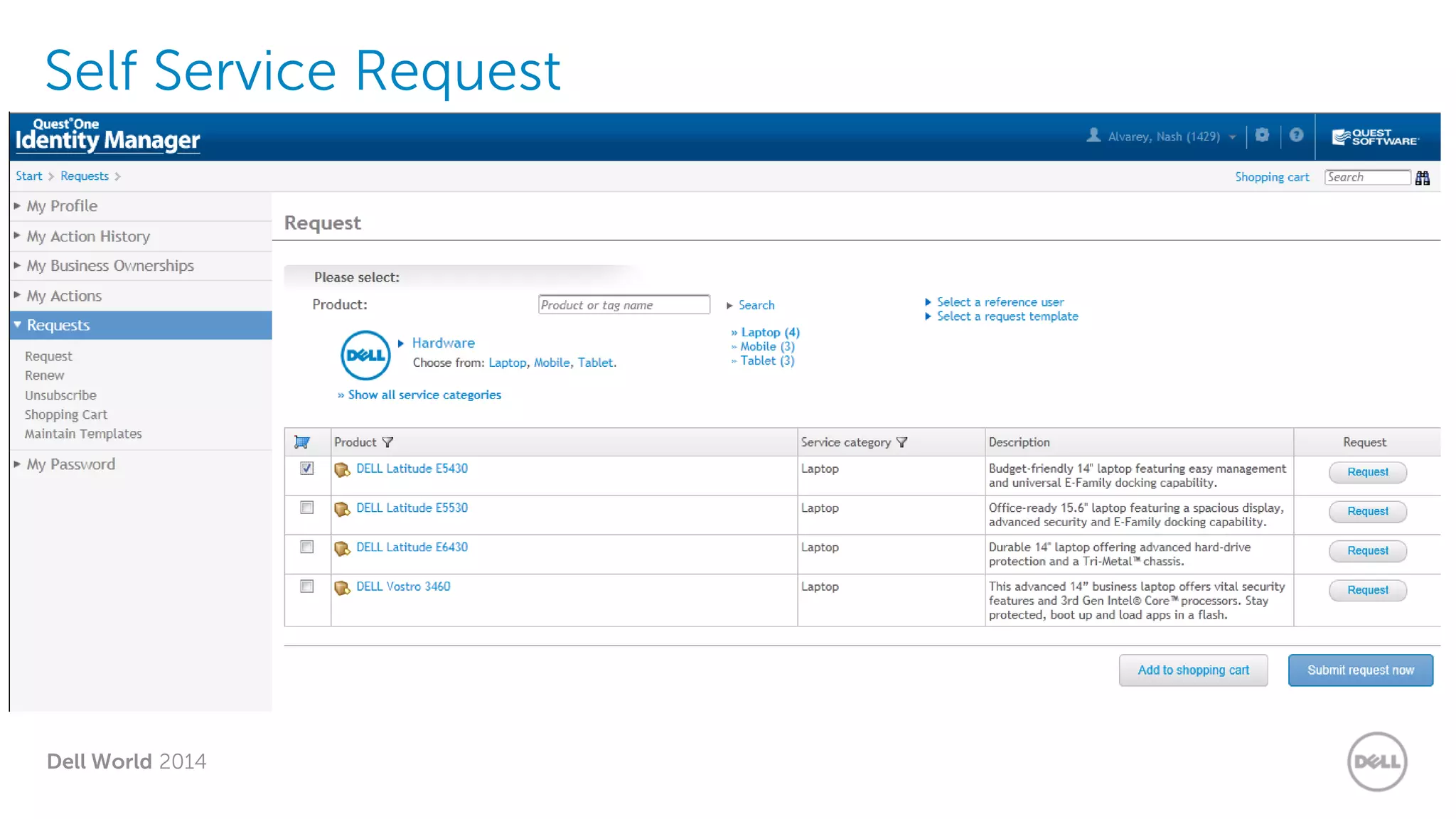
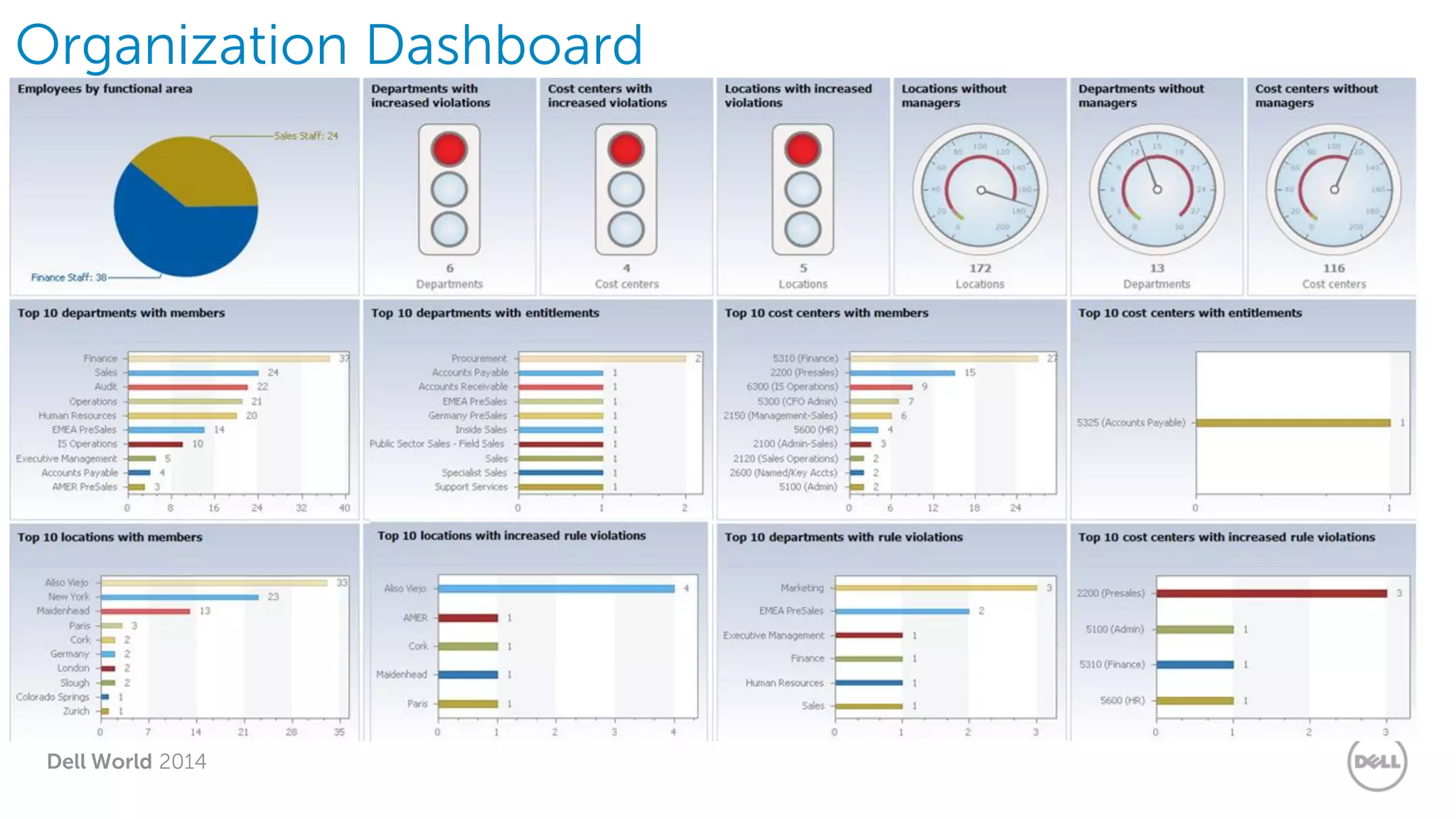
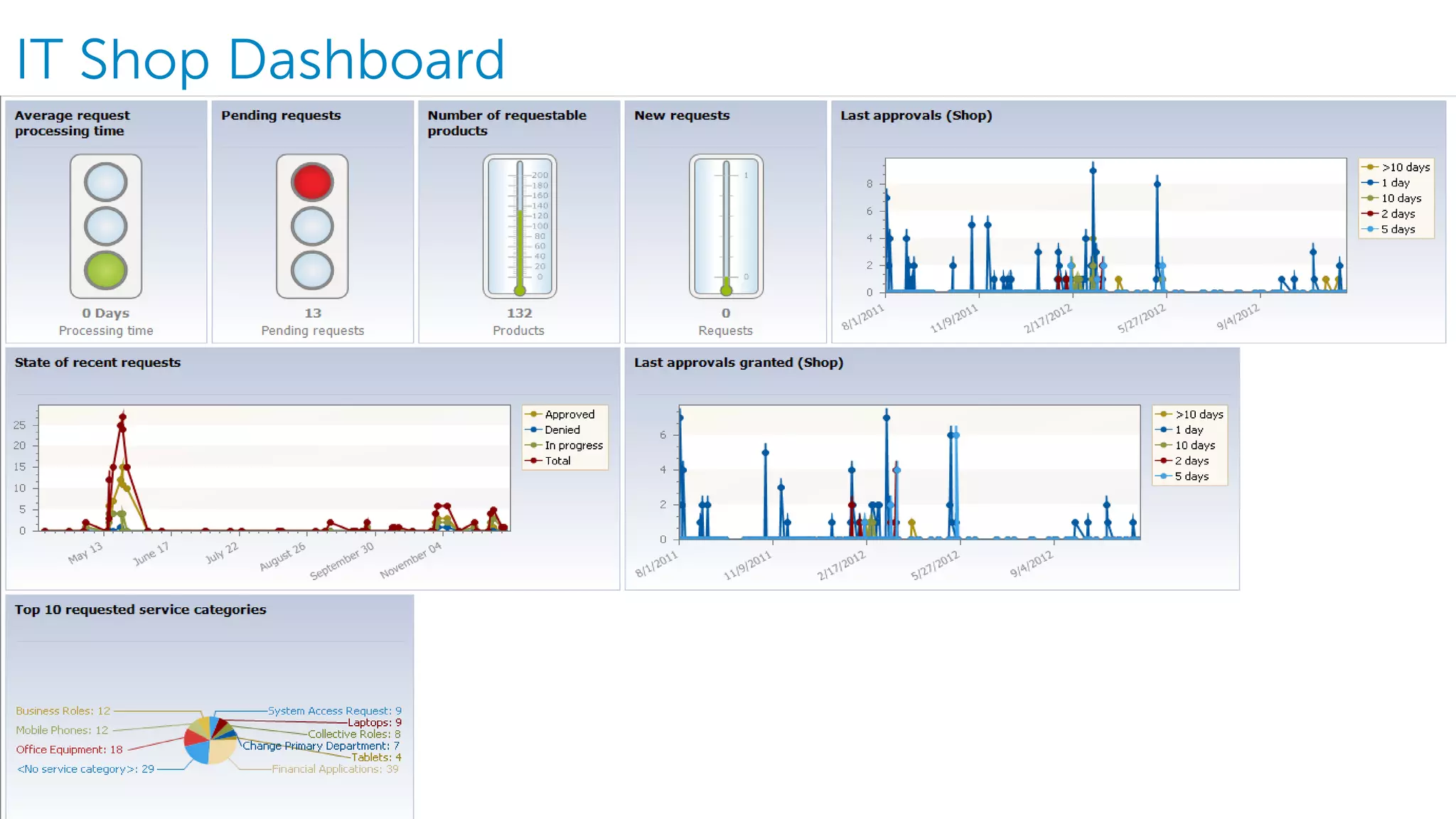
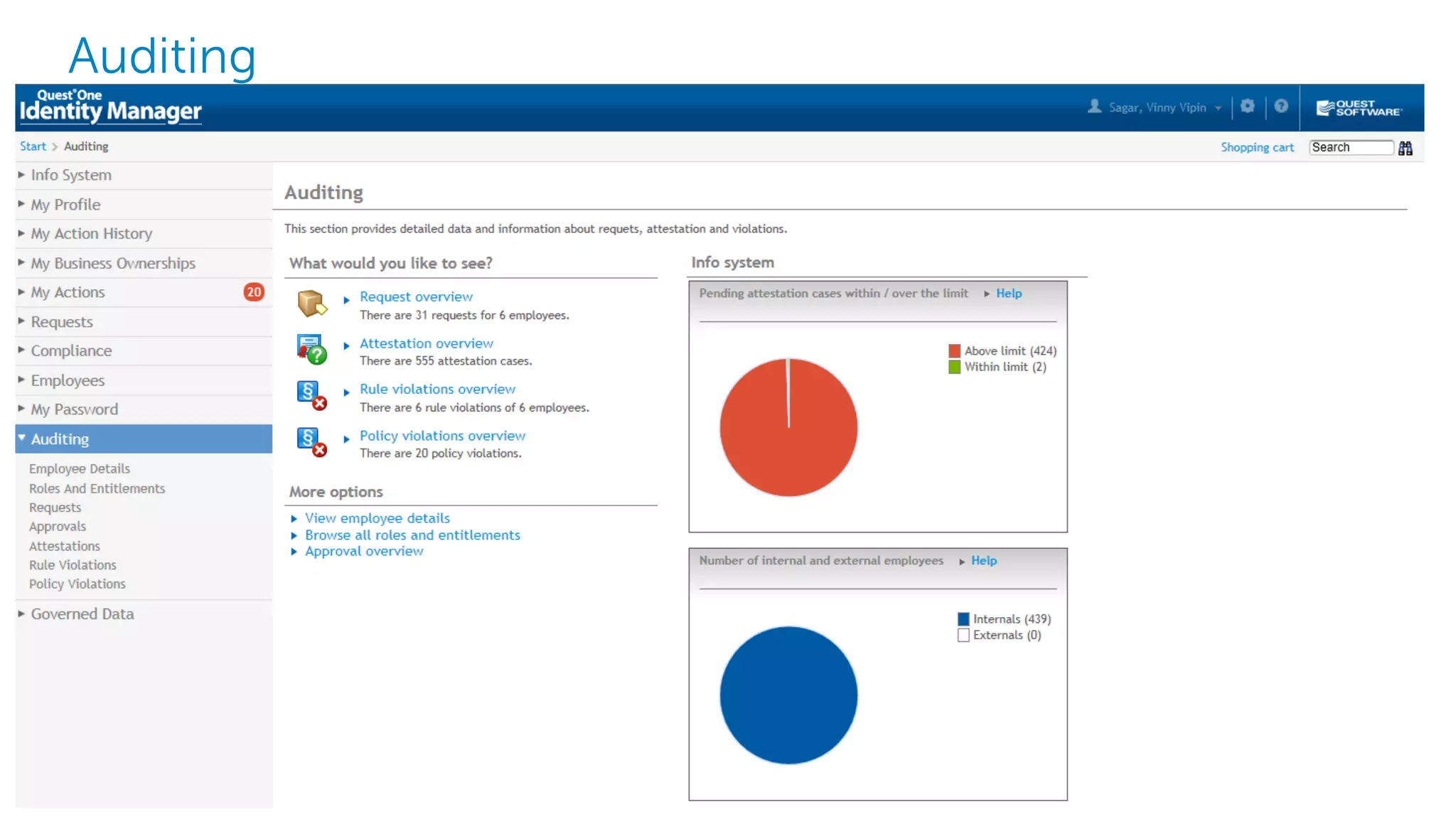
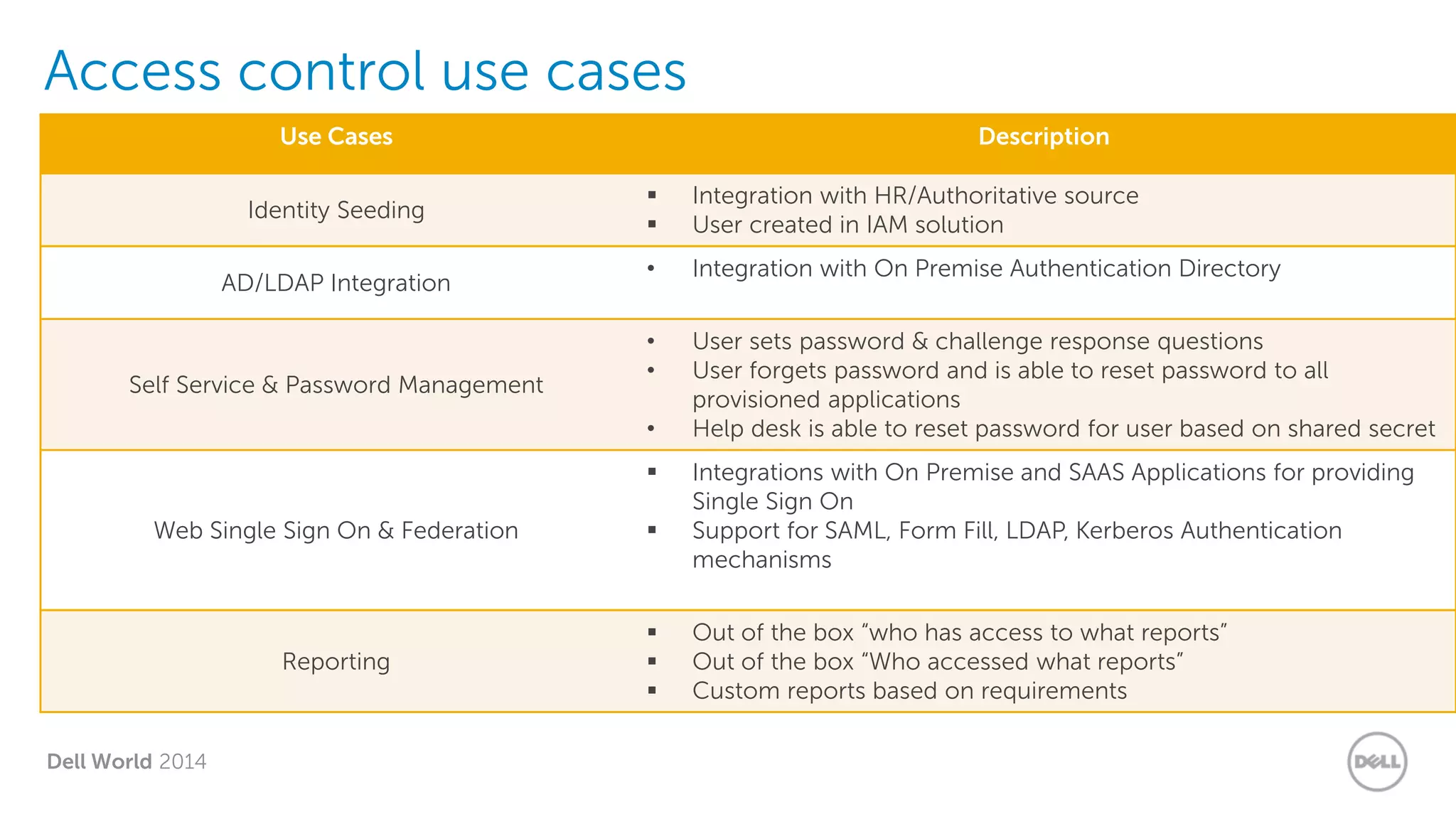
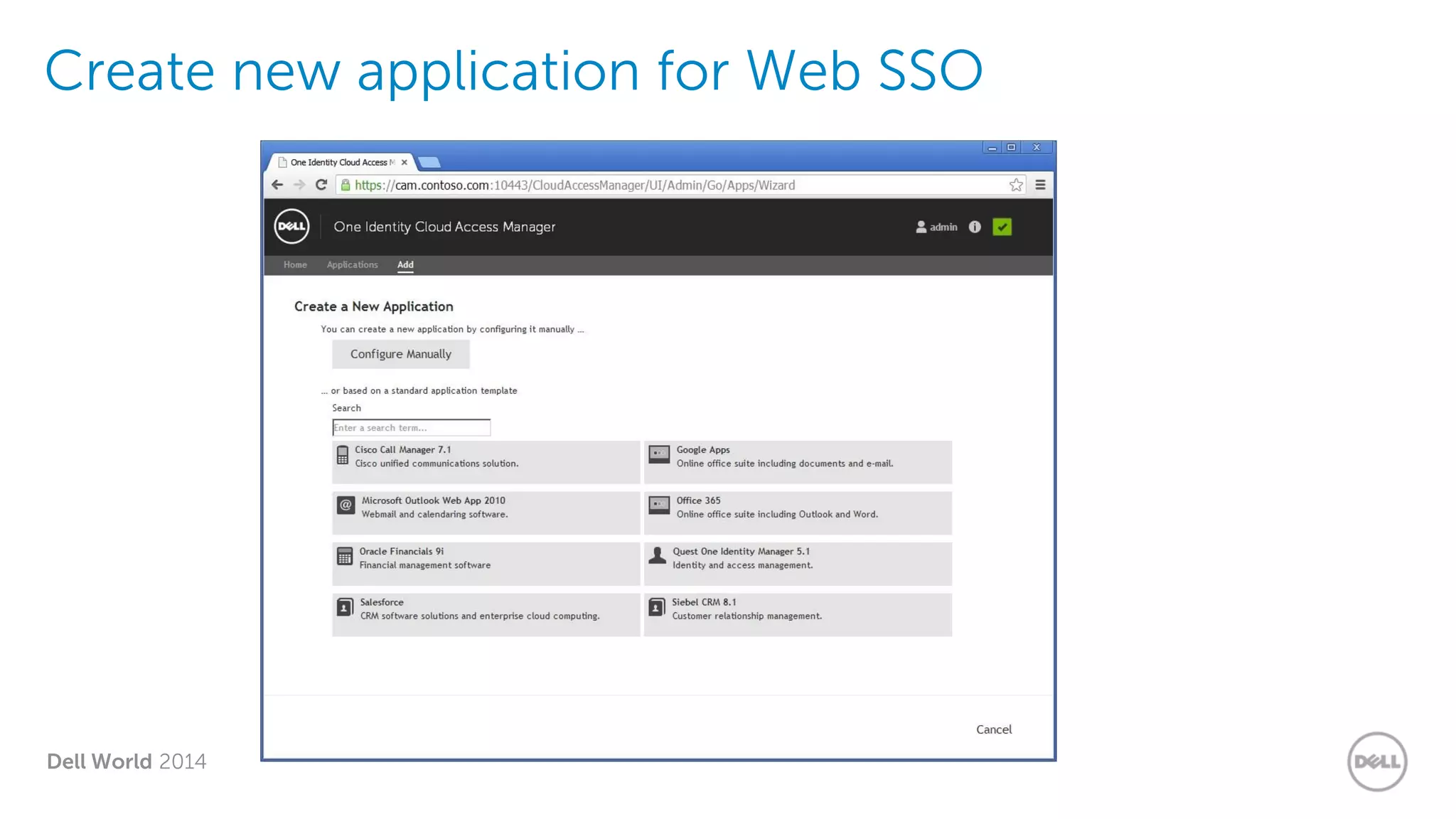
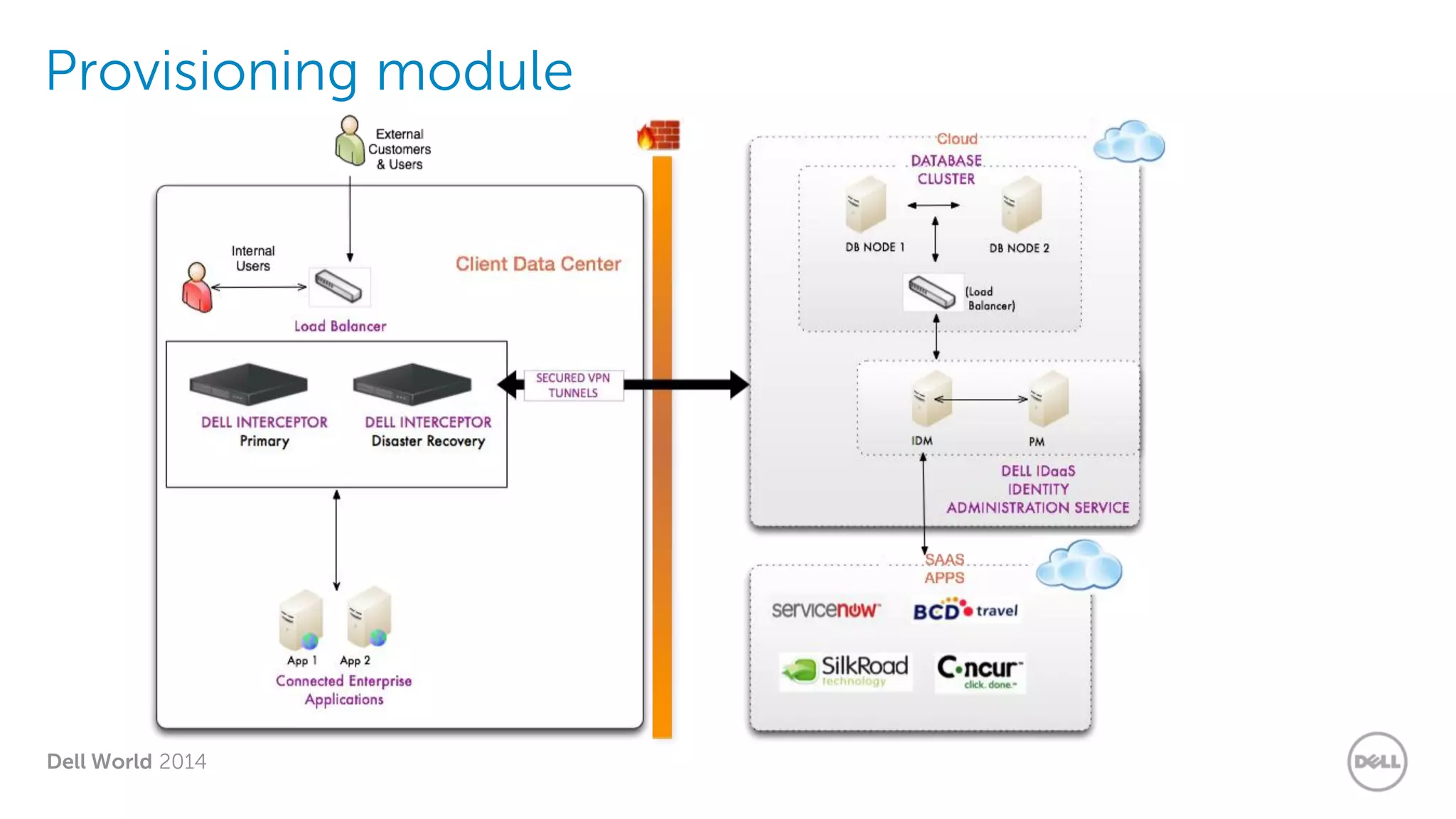
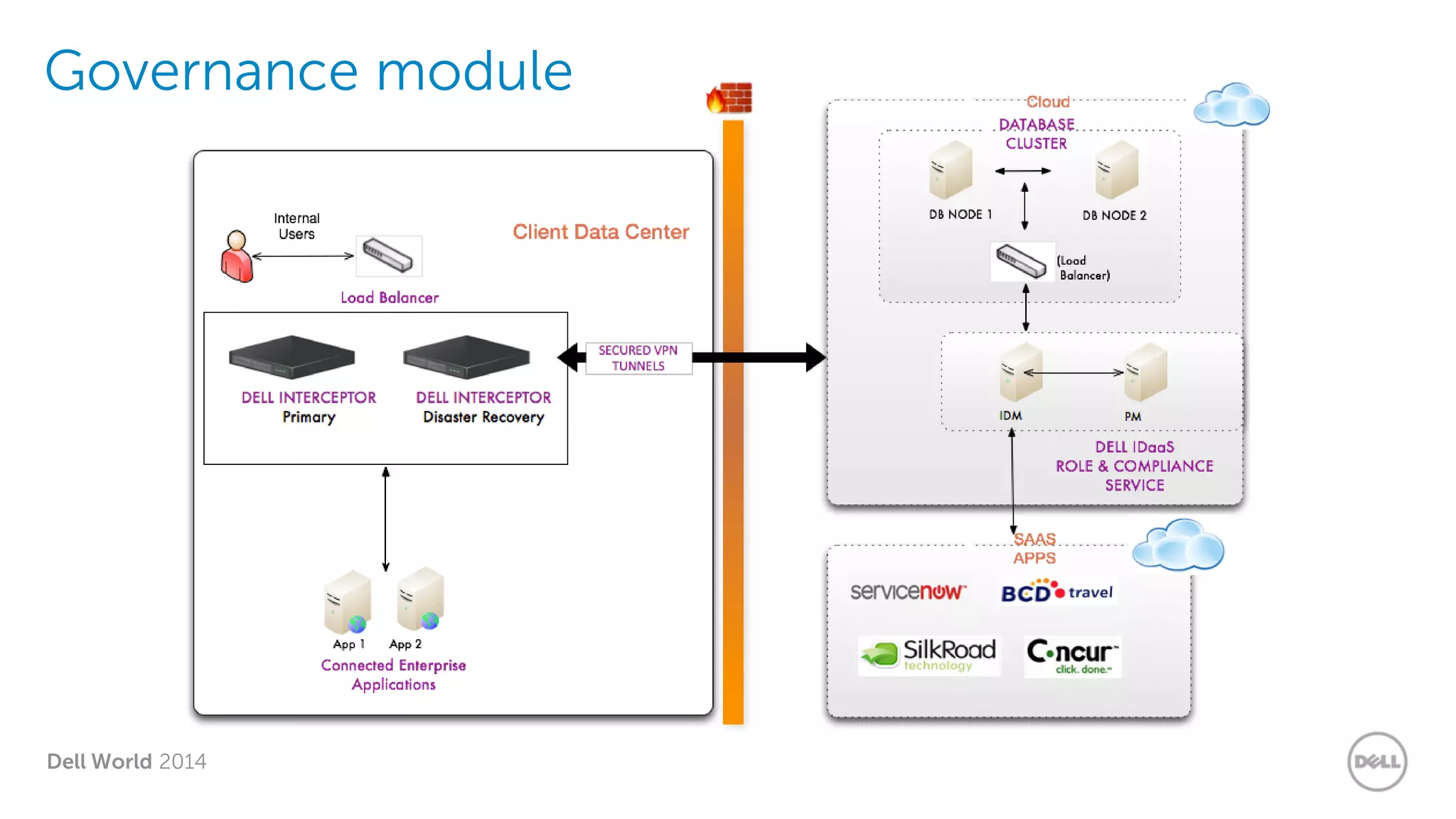
The document summarizes Dell's Identity as a Service (IDaaS) offering, which provides identity and access management solutions delivered as a cloud service. It addresses challenges organizations face with on-premises IAM solutions, such as growing access needs outpacing staff capabilities. Dell's IDaaS offering provides modules for provisioning, governance, and access control that can be implemented individually. The modules help with tasks like provisioning/deprovisioning users, access requests, role-based access control, and compliance reporting. The service is delivered through a partnership with Simeio and leverages their expertise and cloud platform. Benefits highlighted include moving IAM from a capital to operational expense and reducing the burden on IT staff.