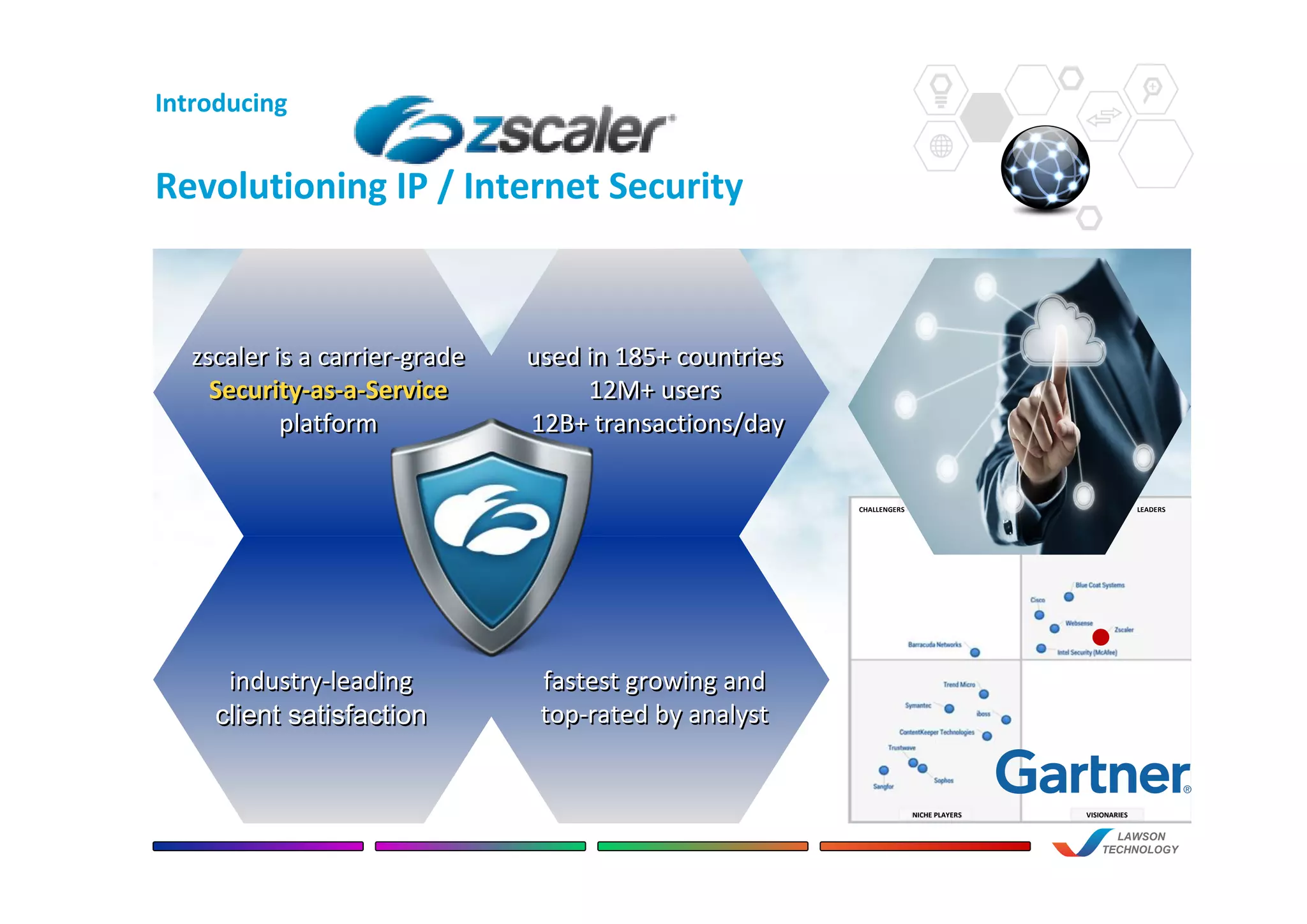
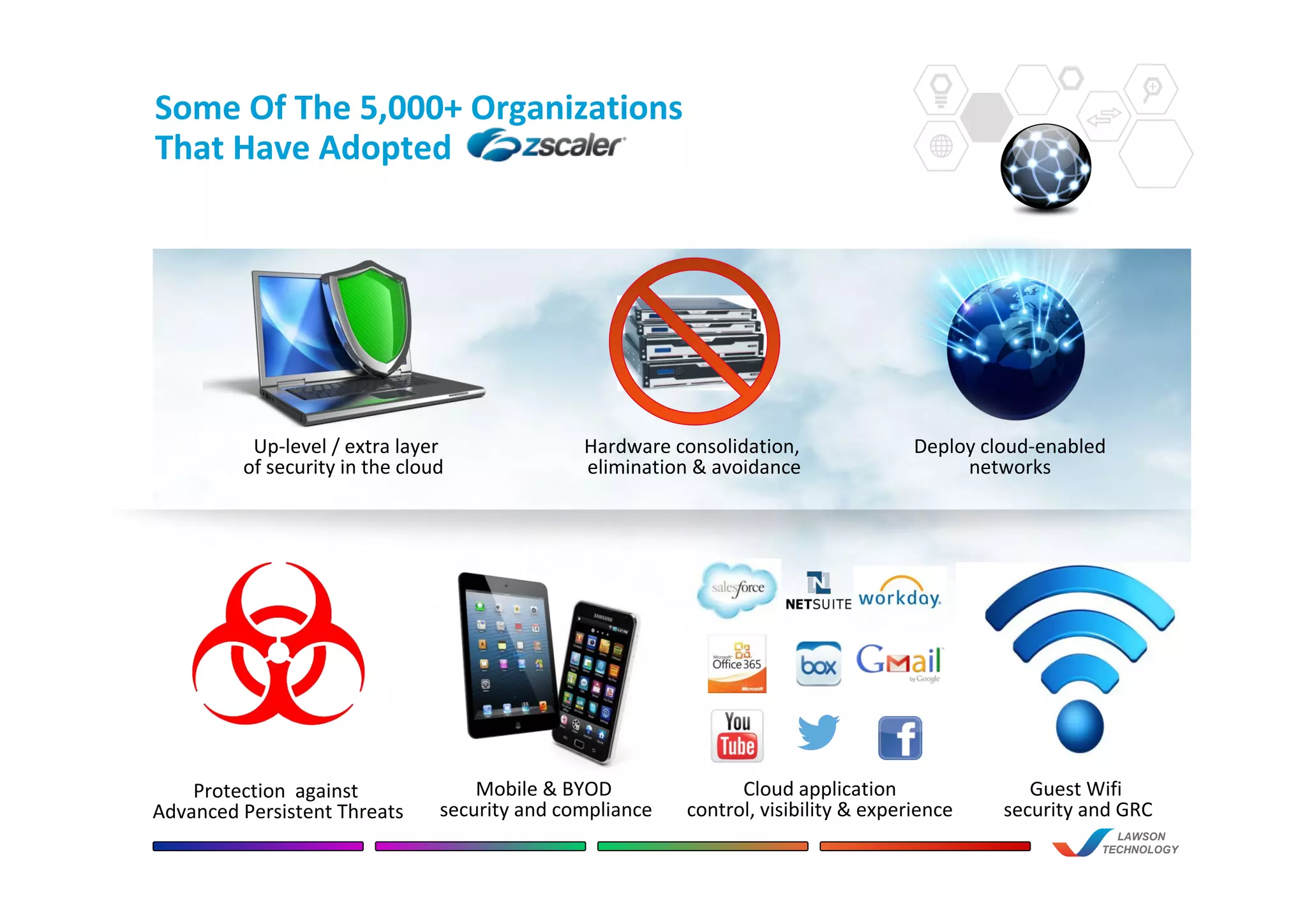
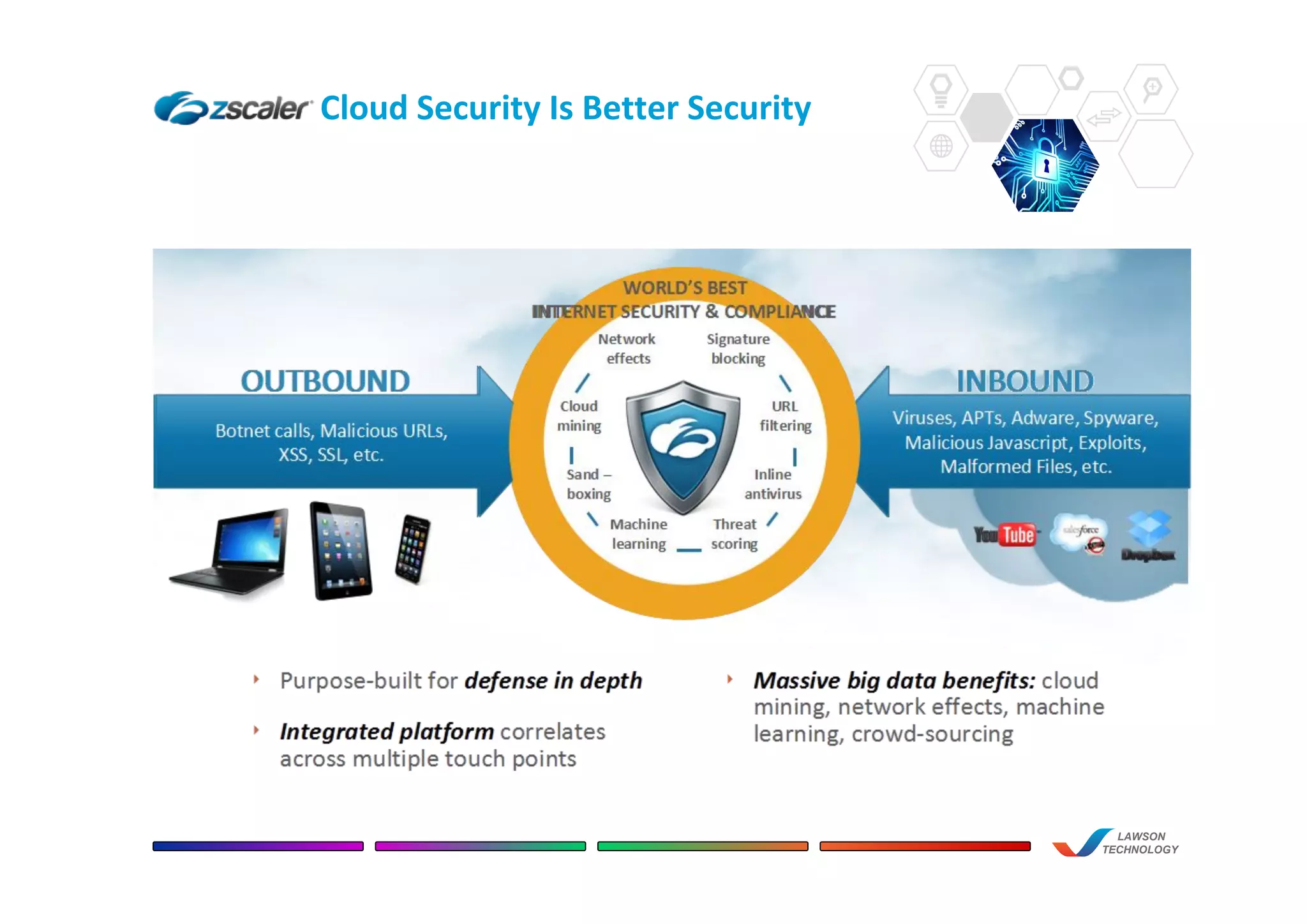
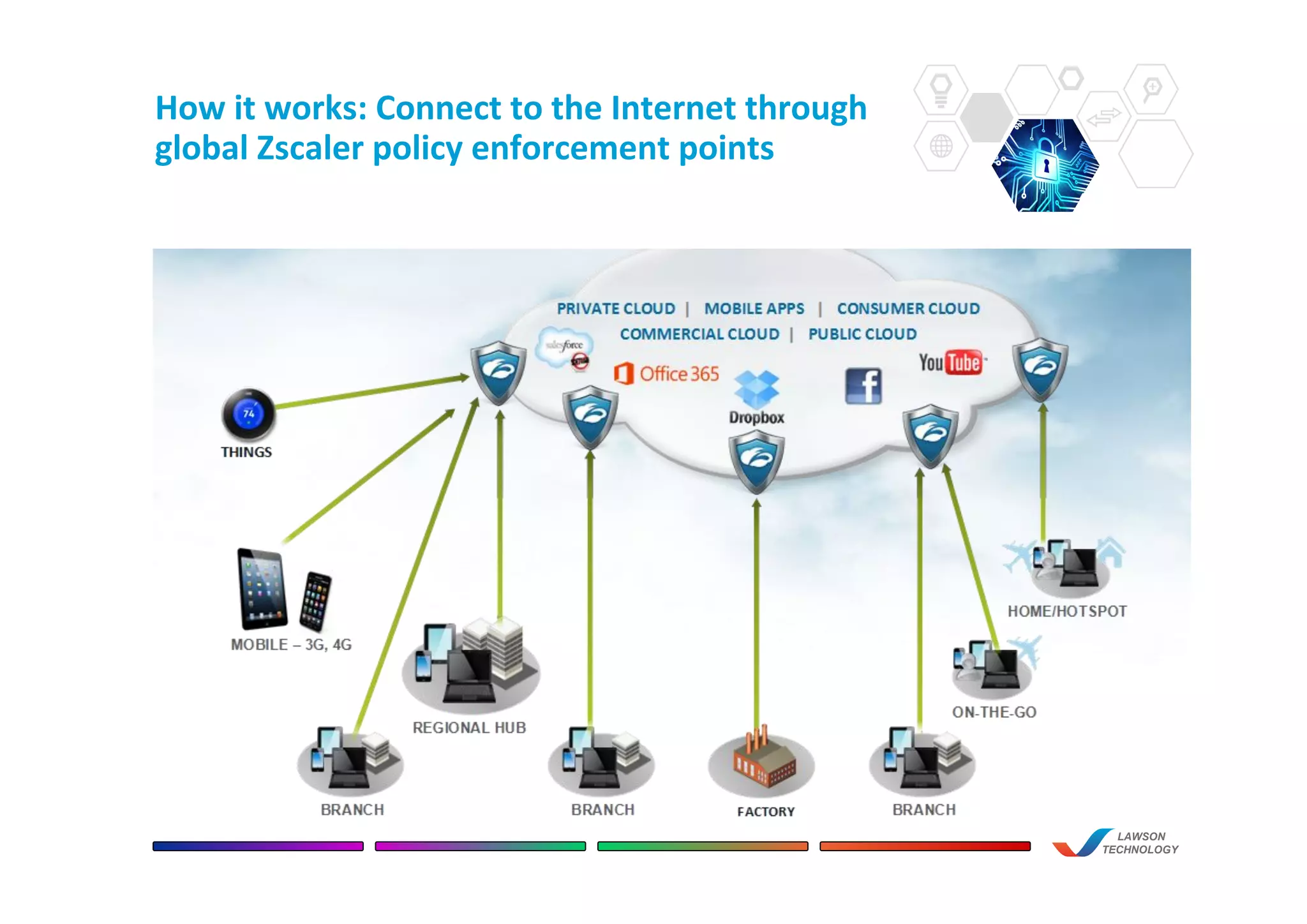
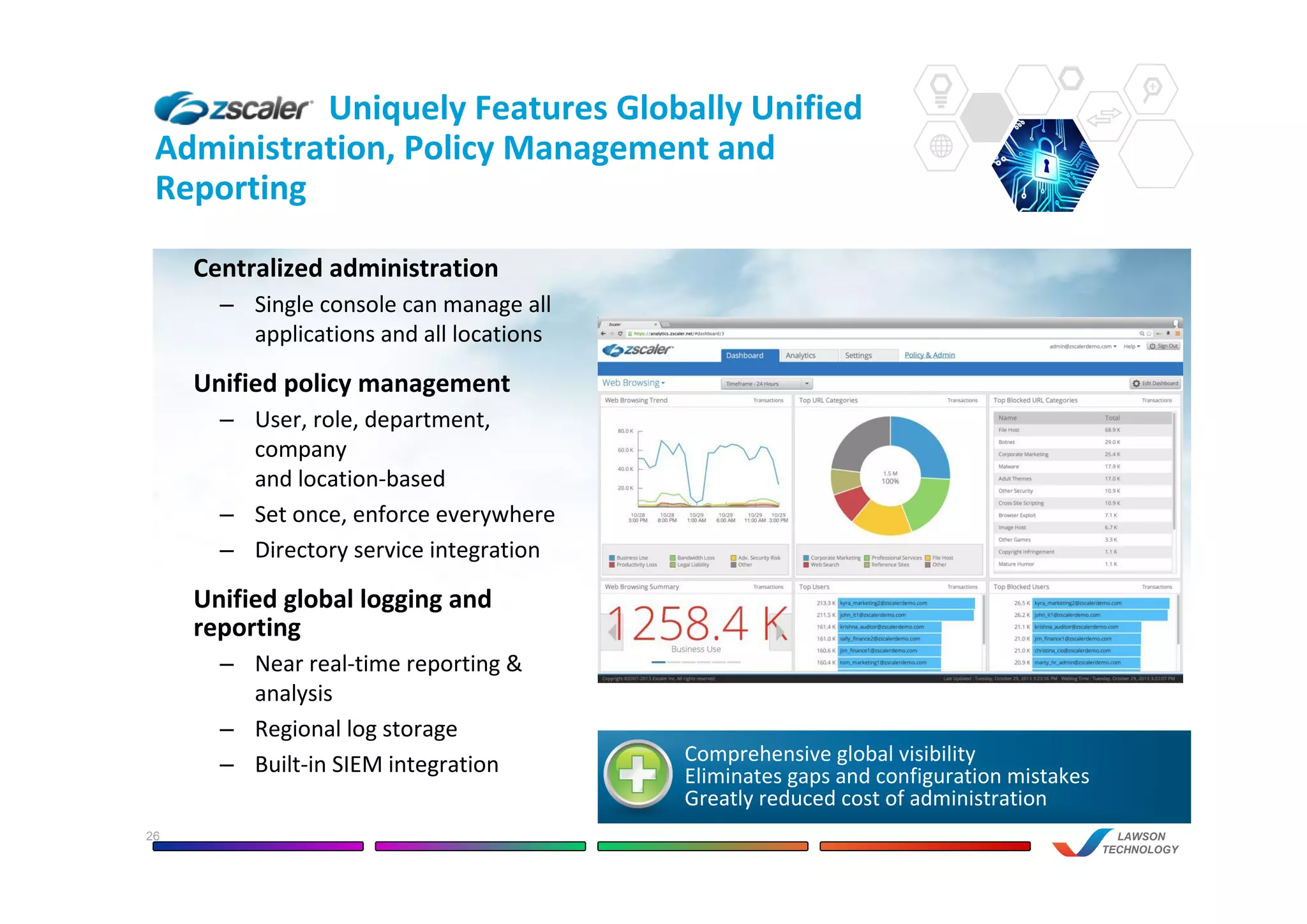
This document discusses the benefits of using Zscaler's cloud-based network and internet security solution over traditional on-premise appliance solutions. It summarizes that Zscaler provides comprehensive security across multiple threat vectors through a single cloud platform. It is more cost effective than appliance solutions and improves performance and user experience while reducing complexity and management overhead. The document also highlights key capabilities of Zscaler such as real-time inspection of all traffic including SSL, global policy management, and unified reporting and administration.

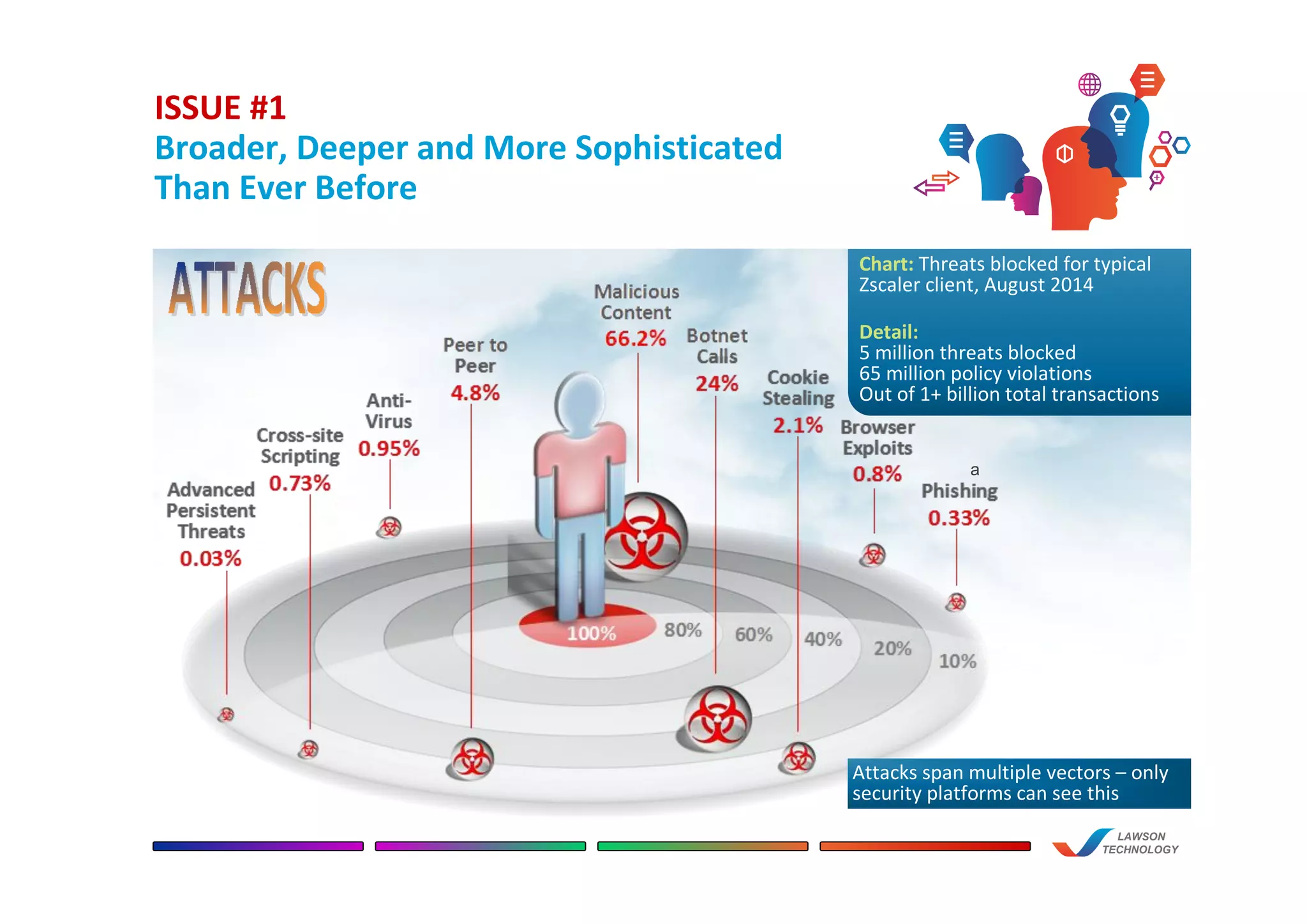
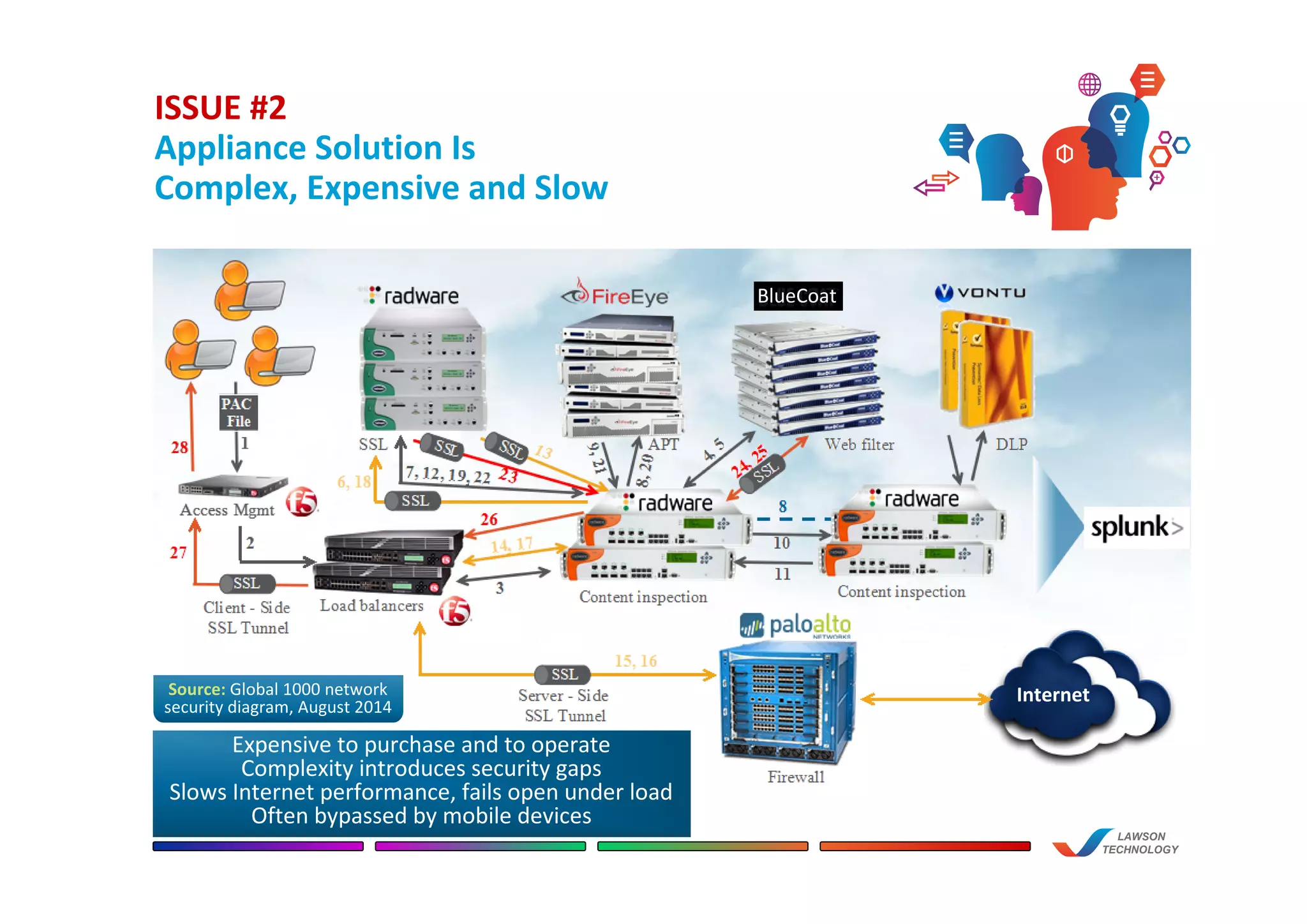
![ISSUE #2
Appliance Solution Is
Complex, Expensive and Slow
a
LAWSON
TECHNOLOGY
“We [spent] at least 4 days each
month just on malware
remediation and hours
on maintenance of appliances.”
– BIG 4 ACCOUNTING FIRM
Data Loss Prevention
Zero Day
Advanced Persistent Threat
Intrusion Prevention Systems
Anti-Virus
URL Filtering
Caching
Proxies
Rate Limiting](https://image.slidesharecdn.com/lpqreyg5t5updved50wu-signature-f8d2148933412ba65bec485769c094f000a62694e870dac31a7204a1e790007d-poli-150507230044-lva1-app6891/75/Streamline-and-Secure-Your-Network-and-Users-3-2048.jpg)