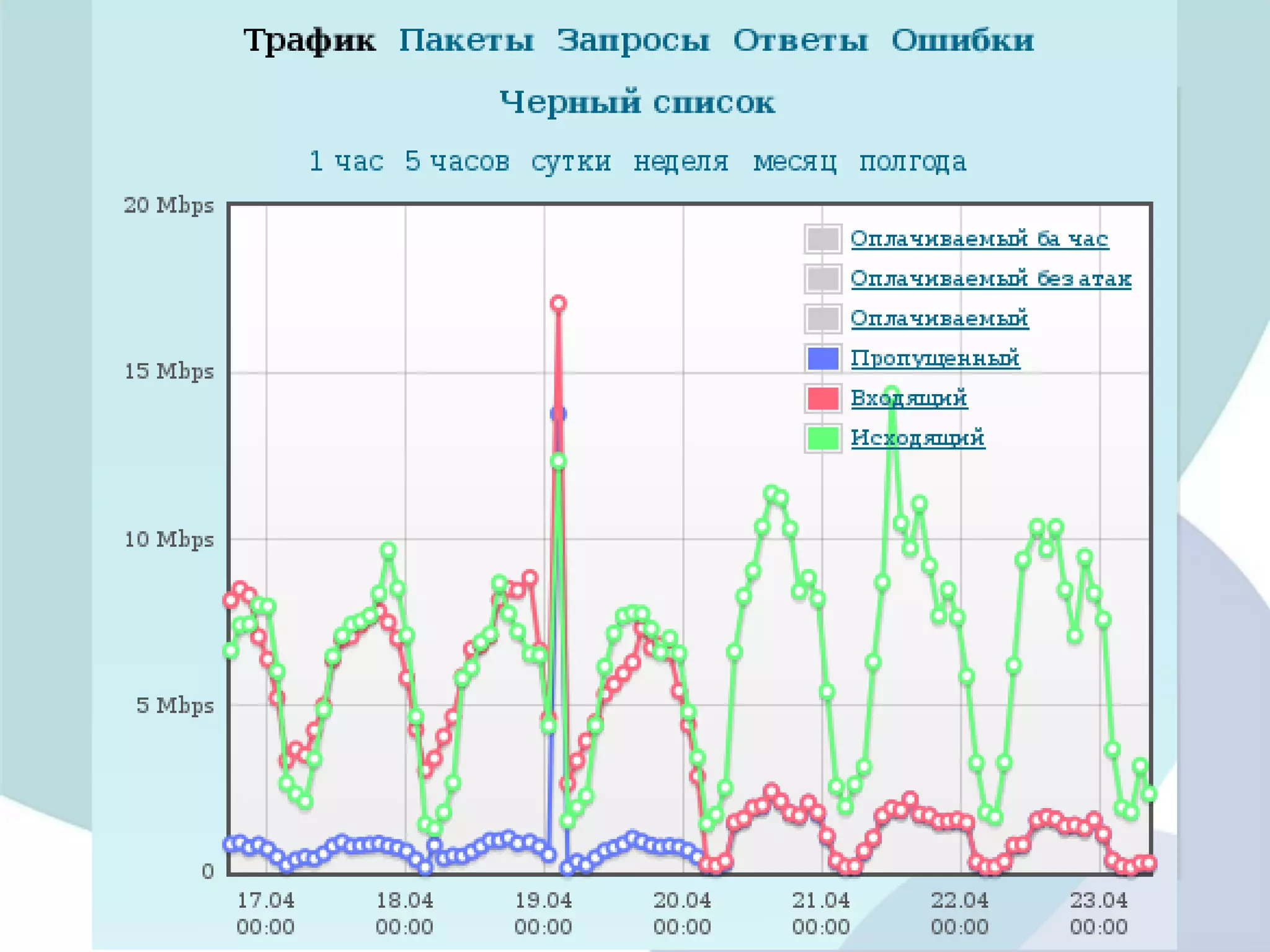
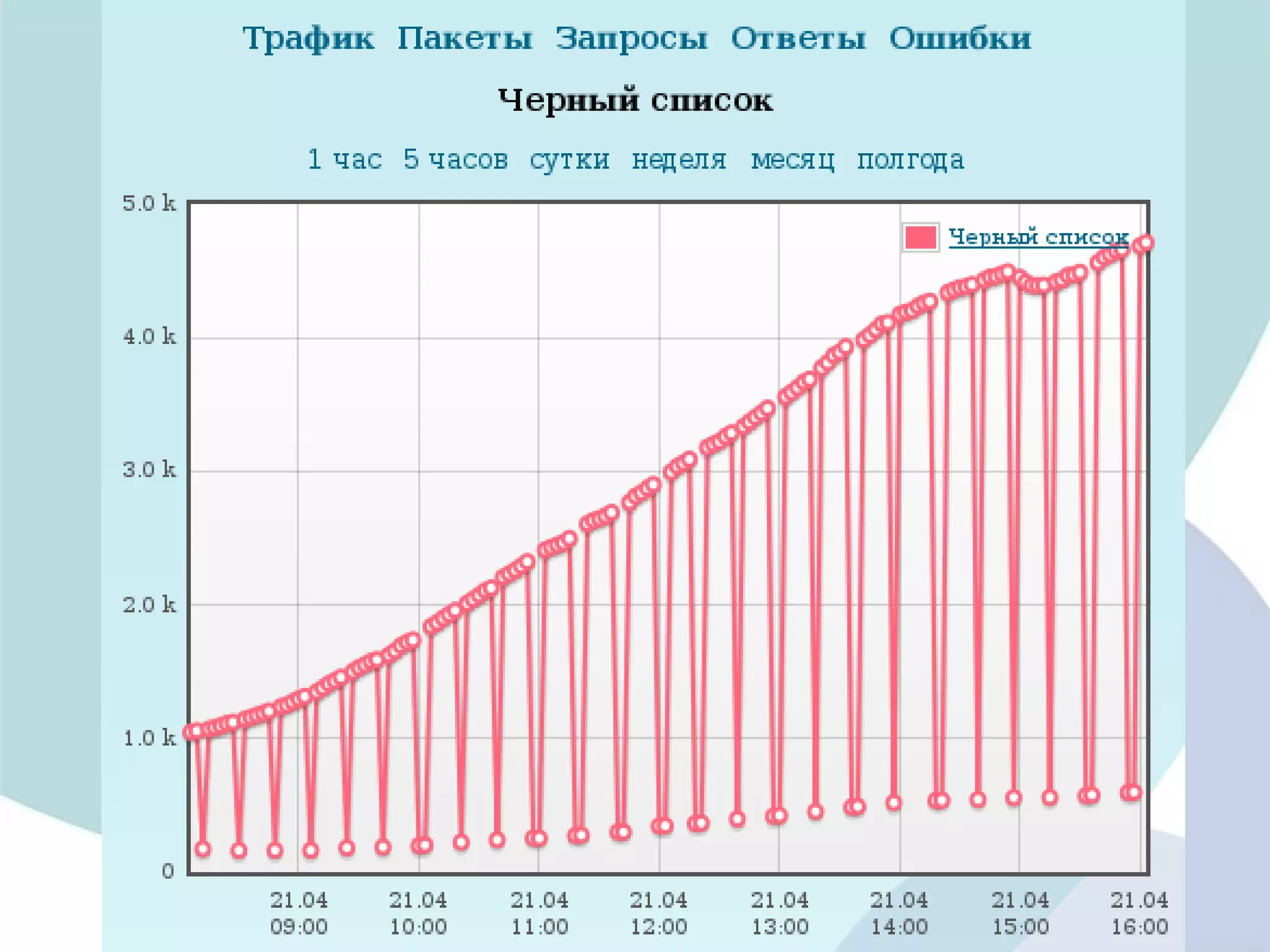
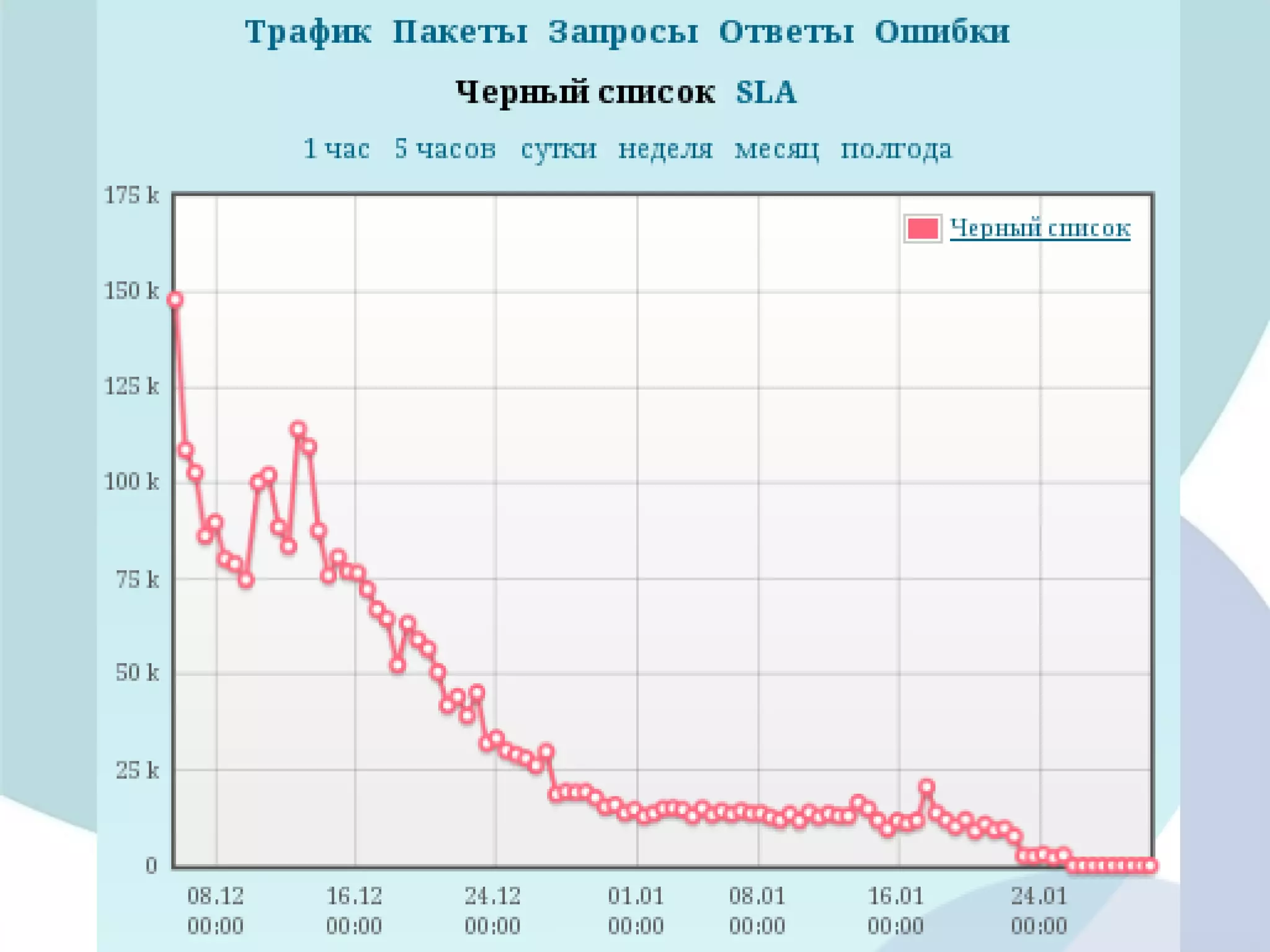
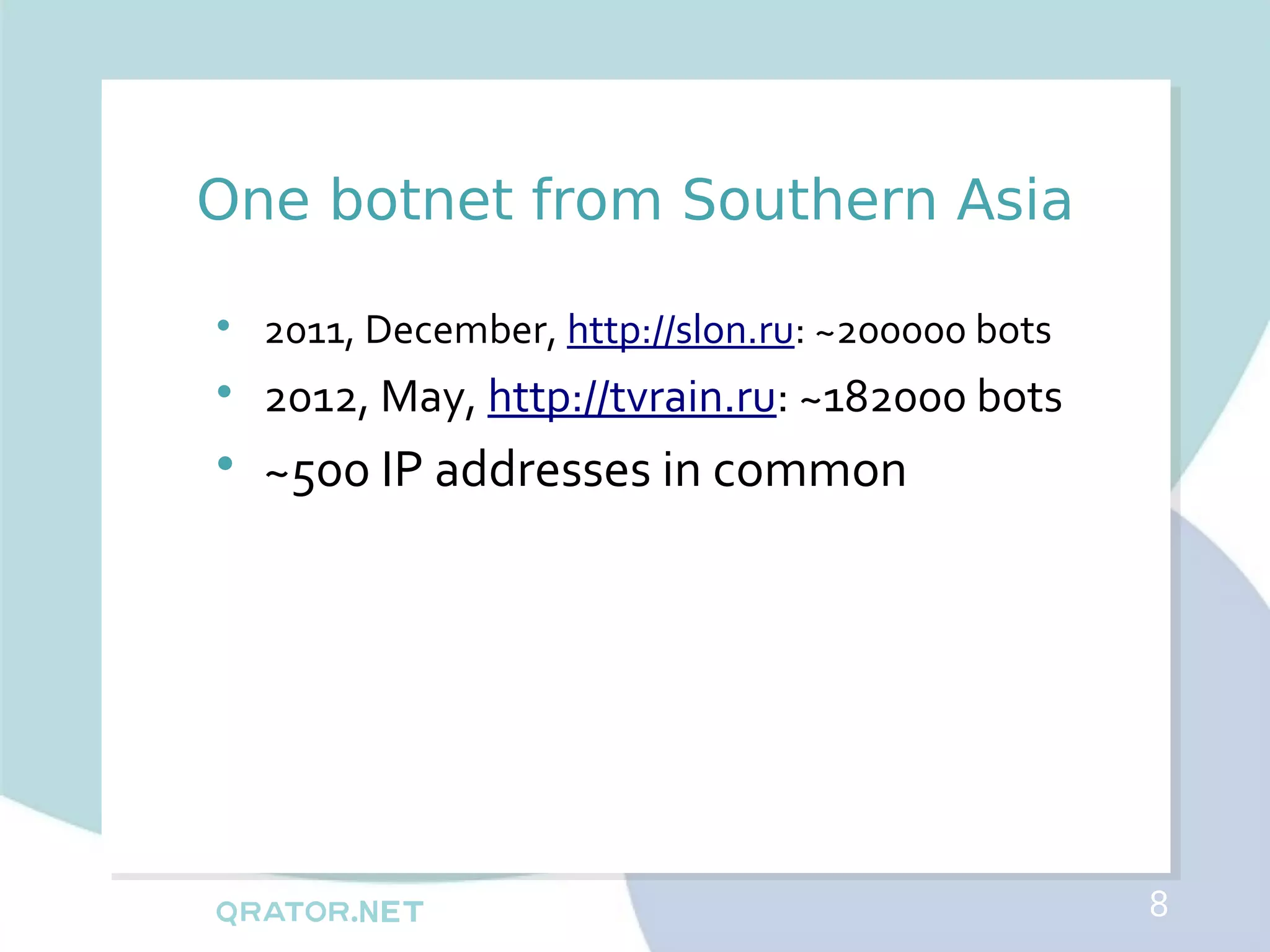
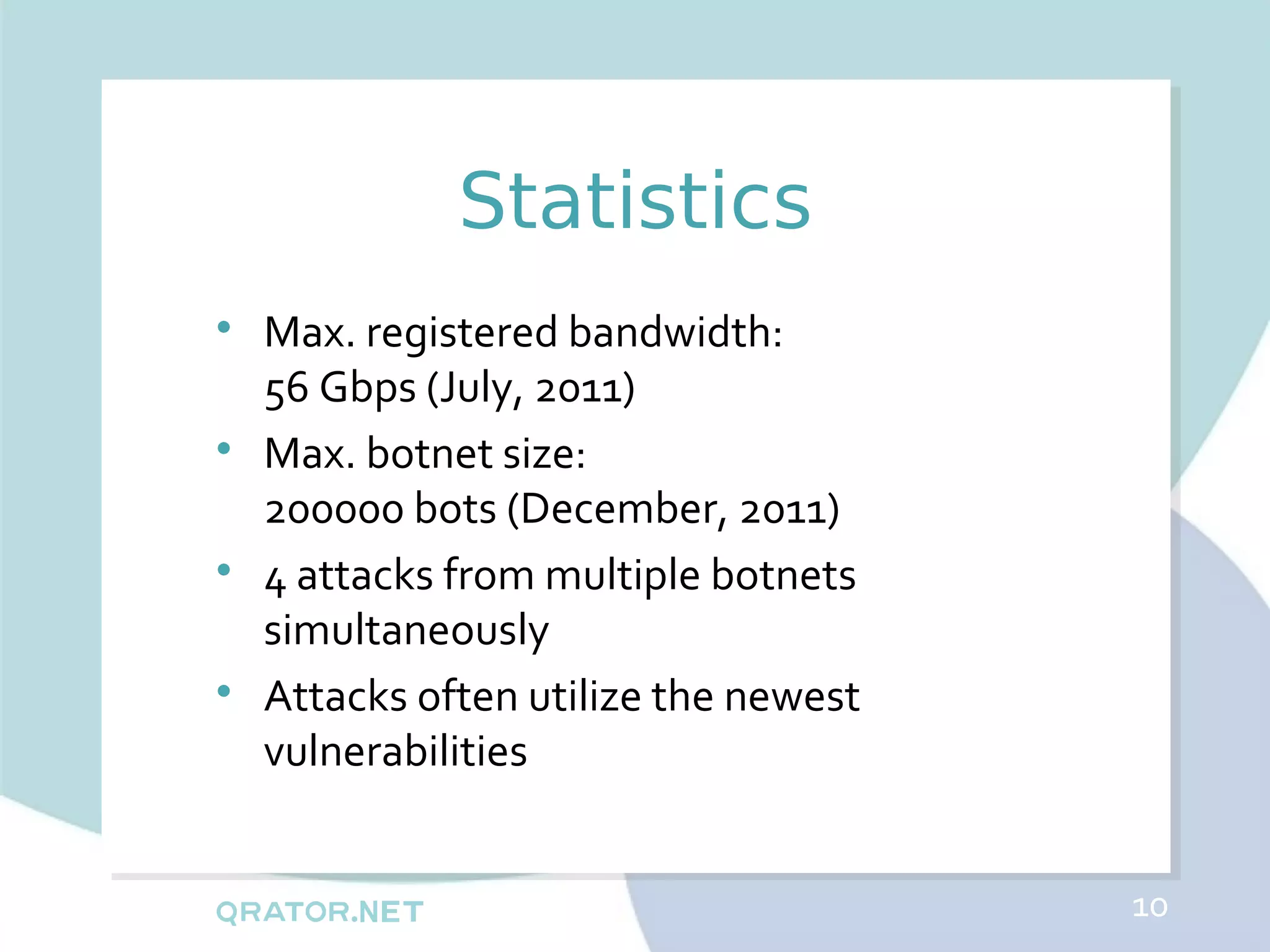
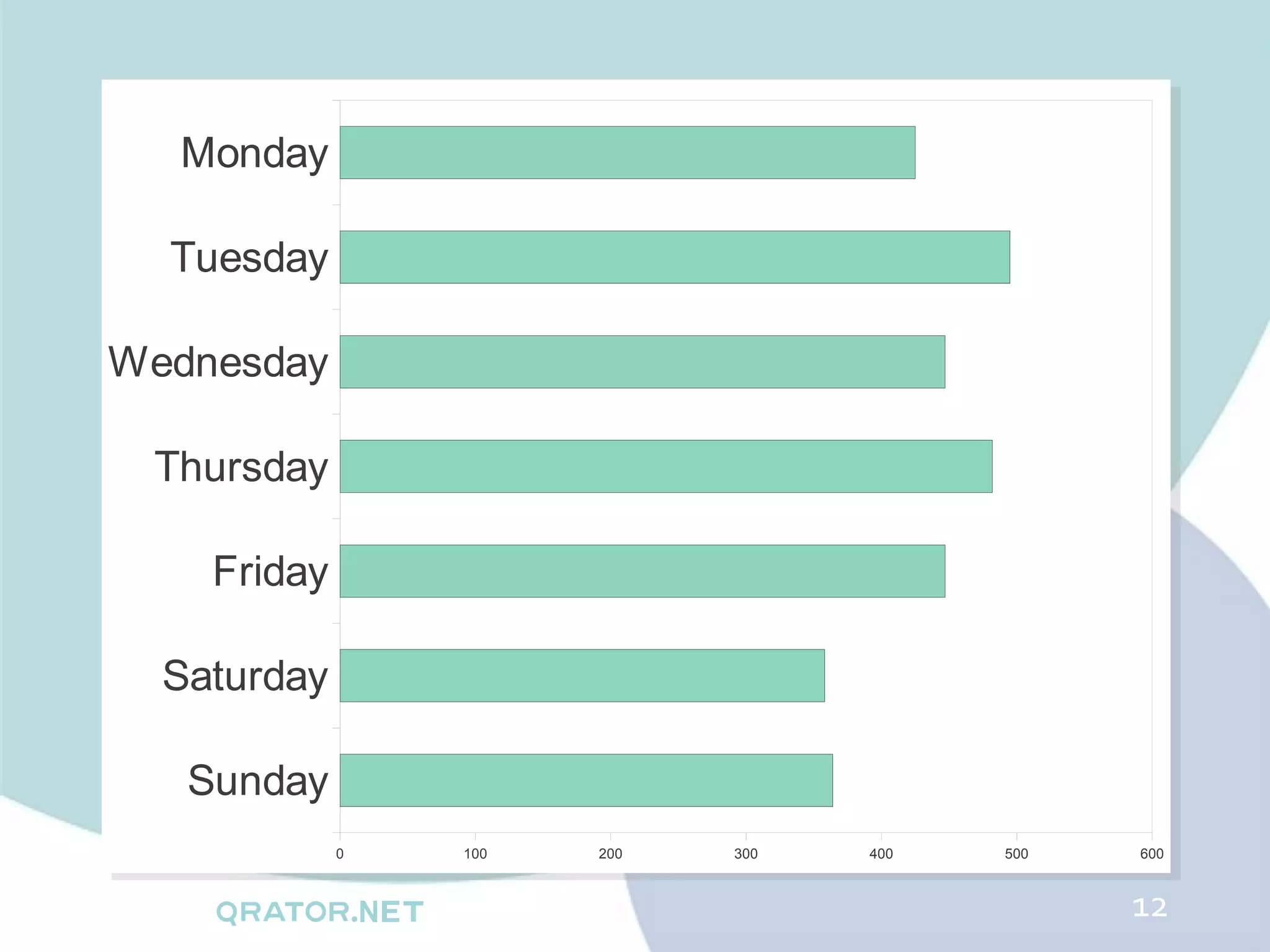
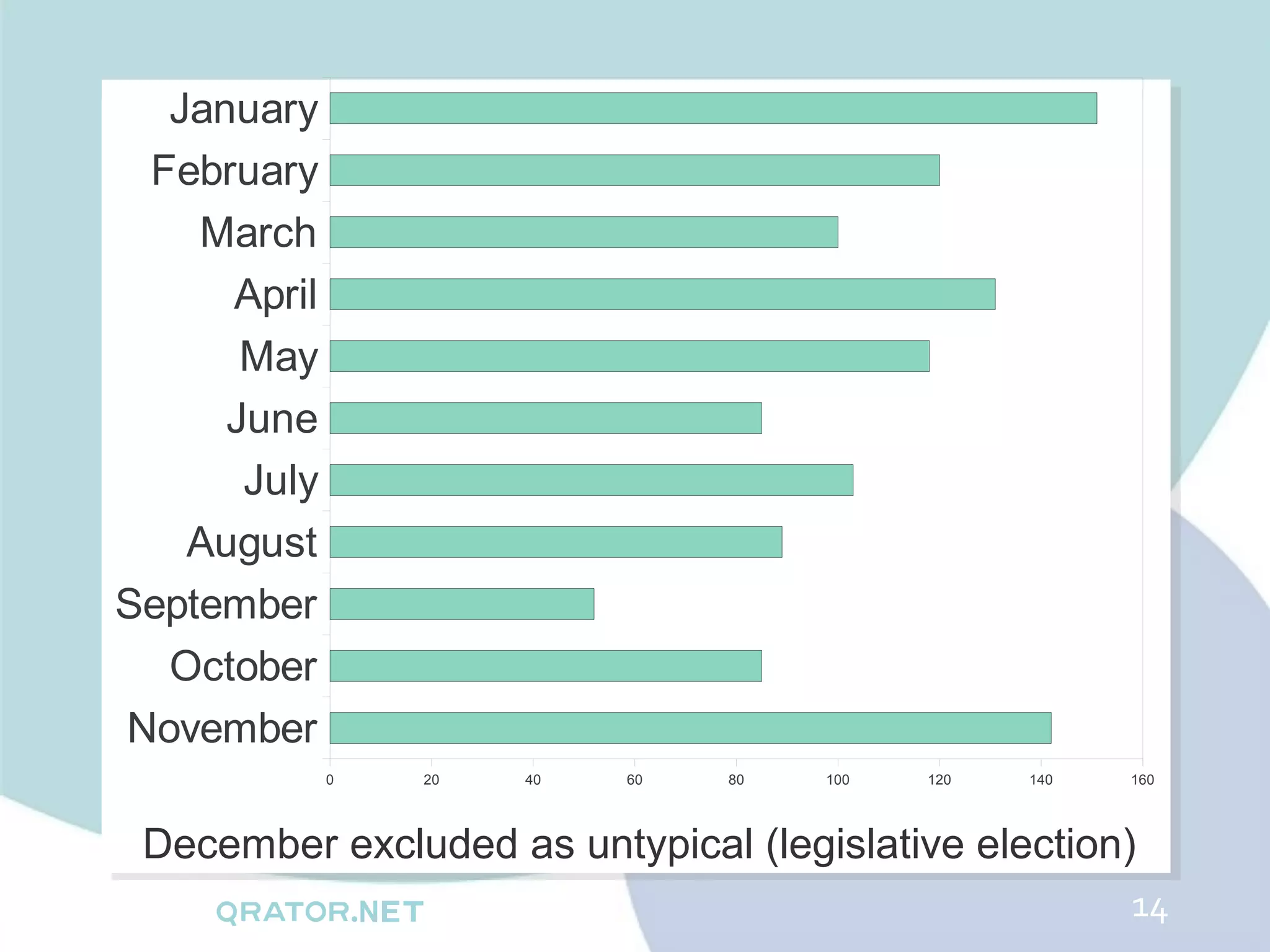
The document analyzes DDoS attack patterns and trends in Russia from 2011 to 2012, reporting over 2,500 attacks with peaks in intensity and duration. Key statistics include a maximum attack bandwidth of 56 Gbps and a botnet size reaching 200,000 bots. It highlights that attacks are often motivated by financial gain, political purposes, or botnet promotion, with a notable increase in attack frequency during weekends.