The document discusses an efficient digital watermarking system based on the discrete cosine transform (DCT) to protect the integrity of digital content such as images. It outlines the theoretical foundations, implementation techniques, and future work needed to enhance the watermarking process against various attacks like noise and compression. The conclusion emphasizes that DCT domain watermarking offers more robustness than spatial domain methods, making it a critical approach for safeguarding digital media.





![Theoretical Understanding
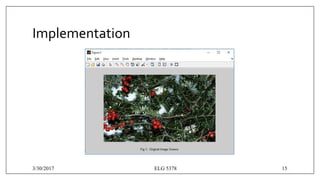
Fig 3:- Co-relation between image before and after DCT [11]
3/30/2017 ELG 5378 10](https://image.slidesharecdn.com/finalipicppt-170422000132/85/DCT-based-Image-Watermarking-10-320.jpg)
![Theoretical Understanding
Fig 4 :- Energy Compactness of different transformation[7]
3/30/2017 ELG 5378 11](https://image.slidesharecdn.com/finalipicppt-170422000132/85/DCT-based-Image-Watermarking-11-320.jpg)
![Theoretical Understanding
Fig 5 :- Comparison of DCT vs DFT[8]
• DFT assumes that each block is repeated having the same value n pixel away.
• DCT assumes that the pixel is identical just next to it with periodicity 2N with
mirror symmetry3/30/2017 ELG 5378 12](https://image.slidesharecdn.com/finalipicppt-170422000132/85/DCT-based-Image-Watermarking-12-320.jpg)

![Theoretical Understanding
• Truncation of higher spectral coefficients results in blurring when the details are high.
• Variance from block to block lead in artifacts creating checker board effect.[9]
• Coarse quantization of some of the low spectral coefficients introduces graininess in the smooth
portions of the images.
• So beyond a bit rate we can’t use DCT.
3/30/2017 ELG 5378 14](https://image.slidesharecdn.com/finalipicppt-170422000132/85/DCT-based-Image-Watermarking-14-320.jpg)
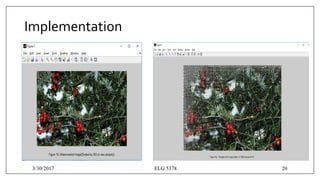
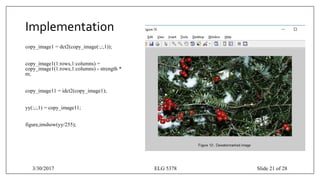
![Implementation
matrix = zeros(300,500);%[Height=300,Width=500]
matrix(100:250,100:350)=1;
figure,imshow(matrix);
3/30/2017 ELG 5378 Slide 16 of 28](https://image.slidesharecdn.com/finalipicppt-170422000132/85/DCT-based-Image-Watermarking-16-320.jpg)

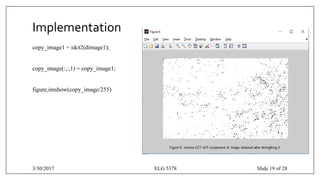
![Implementation
• Strength is defined as maximum allowable weight for an invisible conversion to the (i,j) DCT co-
efficient.[4]
• Fi & Fj are the vertical and horizontal spatial frequency.
• R is set to .7
• Tmin is the minimum value for a given fmin .
3/30/2017 ELG 5378 18](https://image.slidesharecdn.com/finalipicppt-170422000132/85/DCT-based-Image-Watermarking-18-320.jpg)



![References
[1]. Potdar, Vidyasagar M., Song Han, and Elizabeth Chang. "A survey of digital image watermarking
techniques." Industrial Informatics, 2005. INDIN'05. 2005 3rd IEEE International Conference on. IEEE, 2005.
[2]. Barni, Mauro, et al. "A DCT-domain system for robust image watermarking." Signal processing 66.3
(1998): 357-372.
[3]. Lee, Sin-Joo, and Sung-Hwan Jung. "A survey of watermarking techniques applied to
multimedia." Industrial Electronics, 2001. Proceedings. ISIE 2001. IEEE International Symposium on. Vol. 1.
IEEE, 2001.
[4]. Hernandez, Juan R., Martin Amado, and Fernando Perez-Gonzalez. "DCT-domain watermarking
techniques for still images: Detector performance analysis and a new structure." IEEE transactions on image
processing 9.1 (2000): 55-68.
3/30/2017 ELG 5378 25](https://image.slidesharecdn.com/finalipicppt-170422000132/85/DCT-based-Image-Watermarking-25-320.jpg)
![Reference
[5]. Wong, Ping Wah, and Nasir Memon. "Secret and public key image watermarking schemes for image
authentication and ownership verification." IEEE transactions on image processing 10.10 (2001): 1593-
1601.
[6]. Al-Haj, Ali. "Combined DWT-DCT digital image watermarking." Journal of computer science 3.9
(2007): 740-746.
[7] Nptelhrd. "Lecture - 15 Discrete Cosine Transform." YouTube. YouTube, 15 Oct. 2008. Web. 28 Mar.
2017. <https://www.youtube.com/watch?v=S8FkaEWfCOg&t=449s>.
[8] Alfred936. "Digital image processing: p010 - The Discrete Cosine Transform (DCT)." YouTube.
YouTube, 15 Mar. 2013. Web. 12 Mar. 2017.
3/30/2017 ELG 5378 26](https://image.slidesharecdn.com/finalipicppt-170422000132/85/DCT-based-Image-Watermarking-26-320.jpg)
![Reference
[9] "Compression artifact." Wikipedia. Wikimedia Foundation, 21 Mar. 2017. Web. 23 Mar. 2017.
[10] "Discrete Cosine Transform." Discrete Cosine Transform. N.p., 12 Jan. 2014. Web. 28 Mar. 2017.
[11] "The Discrete Cosine Transform (DCT) | Mathematics of the DFT." DSPRelated.com | DSP. N.p.,
26 May 2013. Web. 28 Mar. 2017.
3/30/2017 ELG 5378 27](https://image.slidesharecdn.com/finalipicppt-170422000132/85/DCT-based-Image-Watermarking-27-320.jpg)
