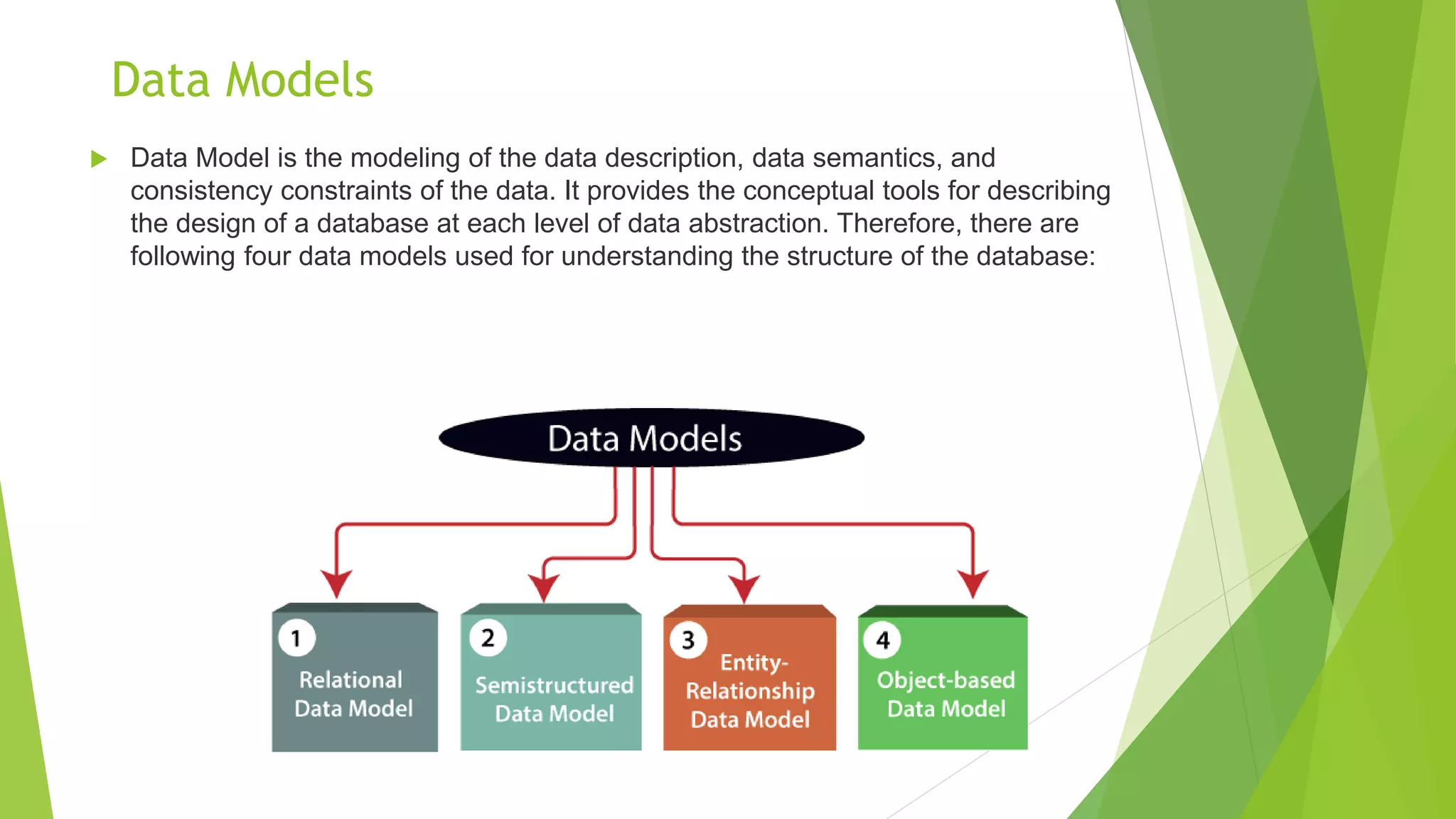
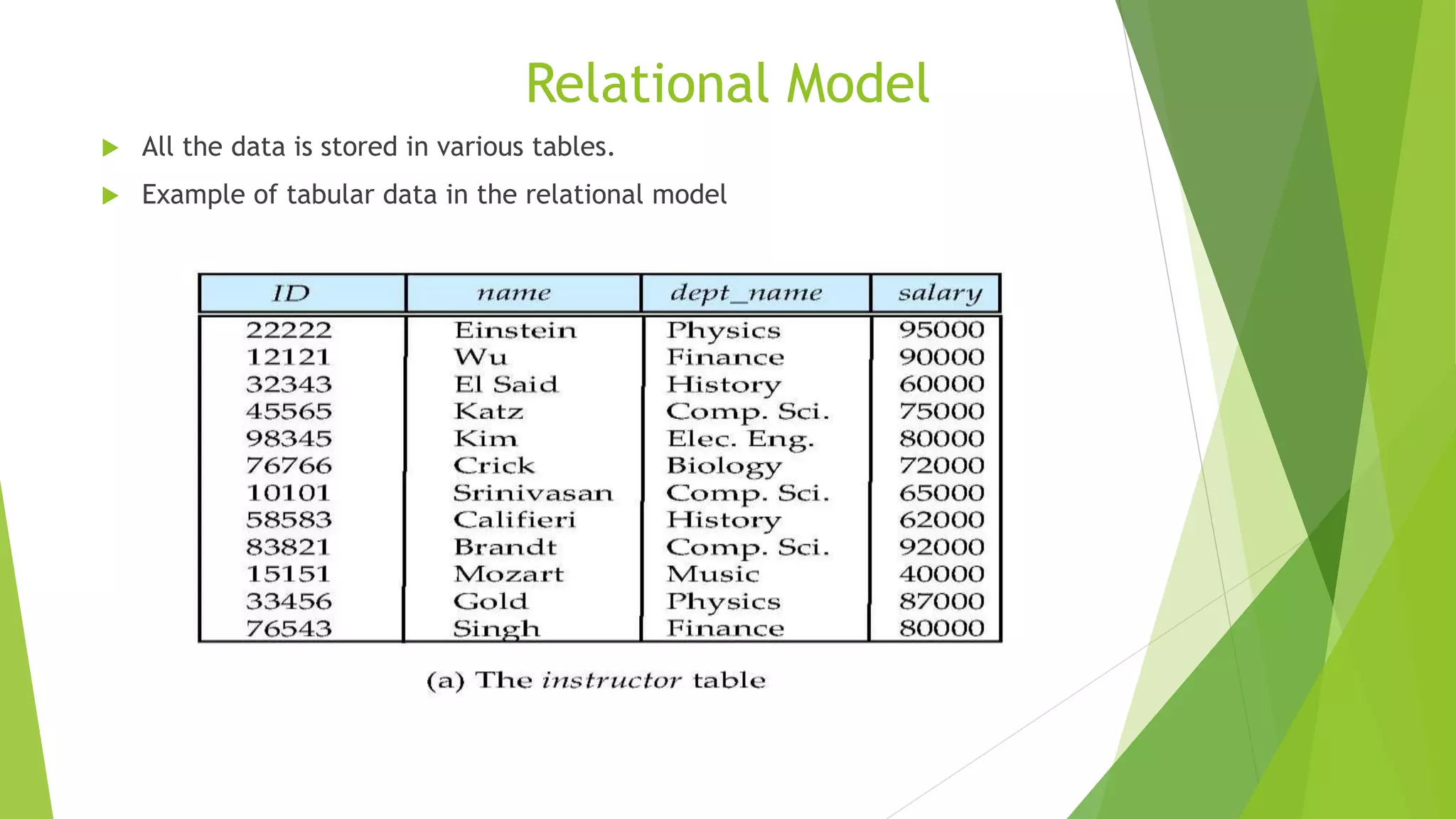
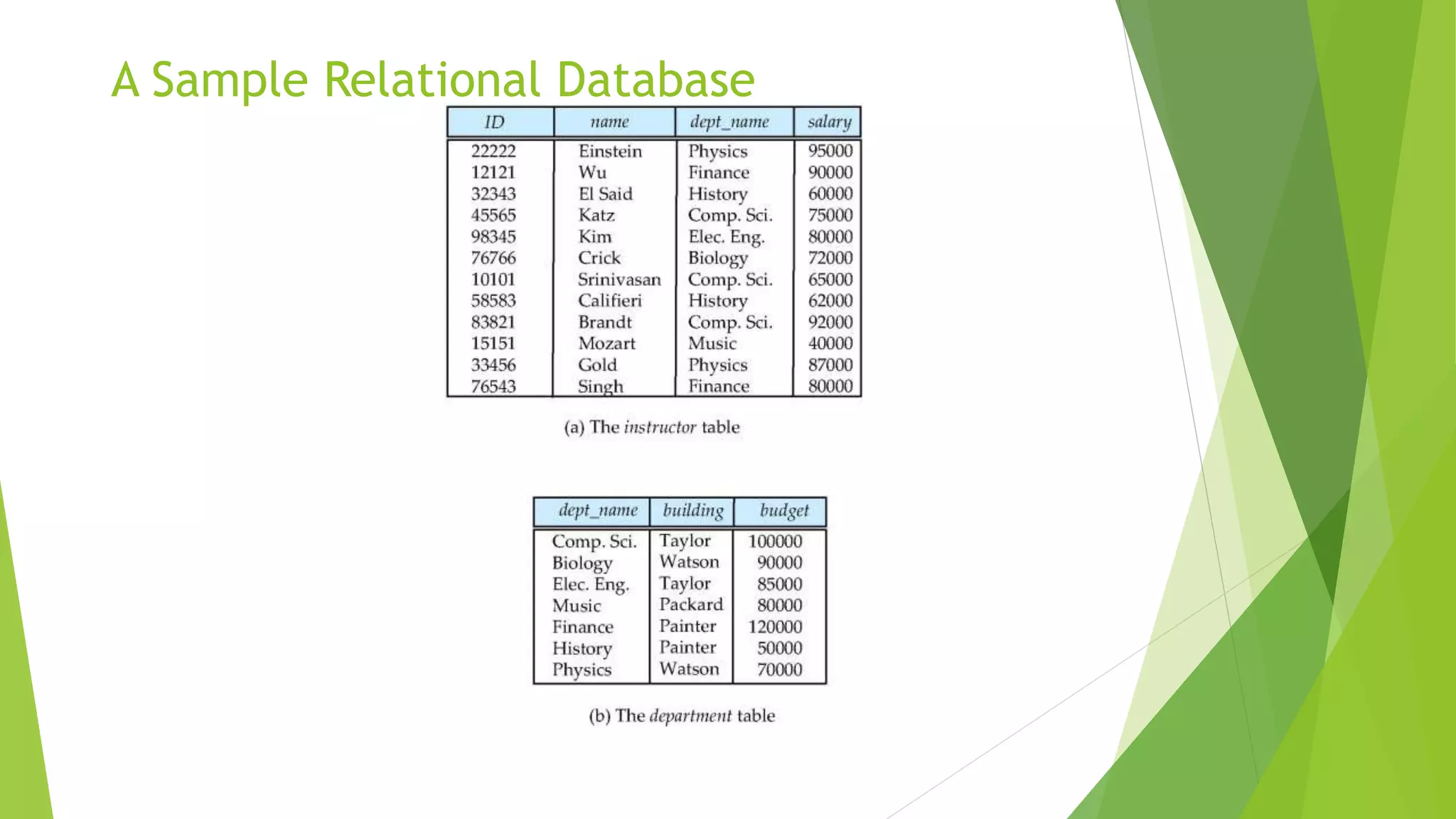
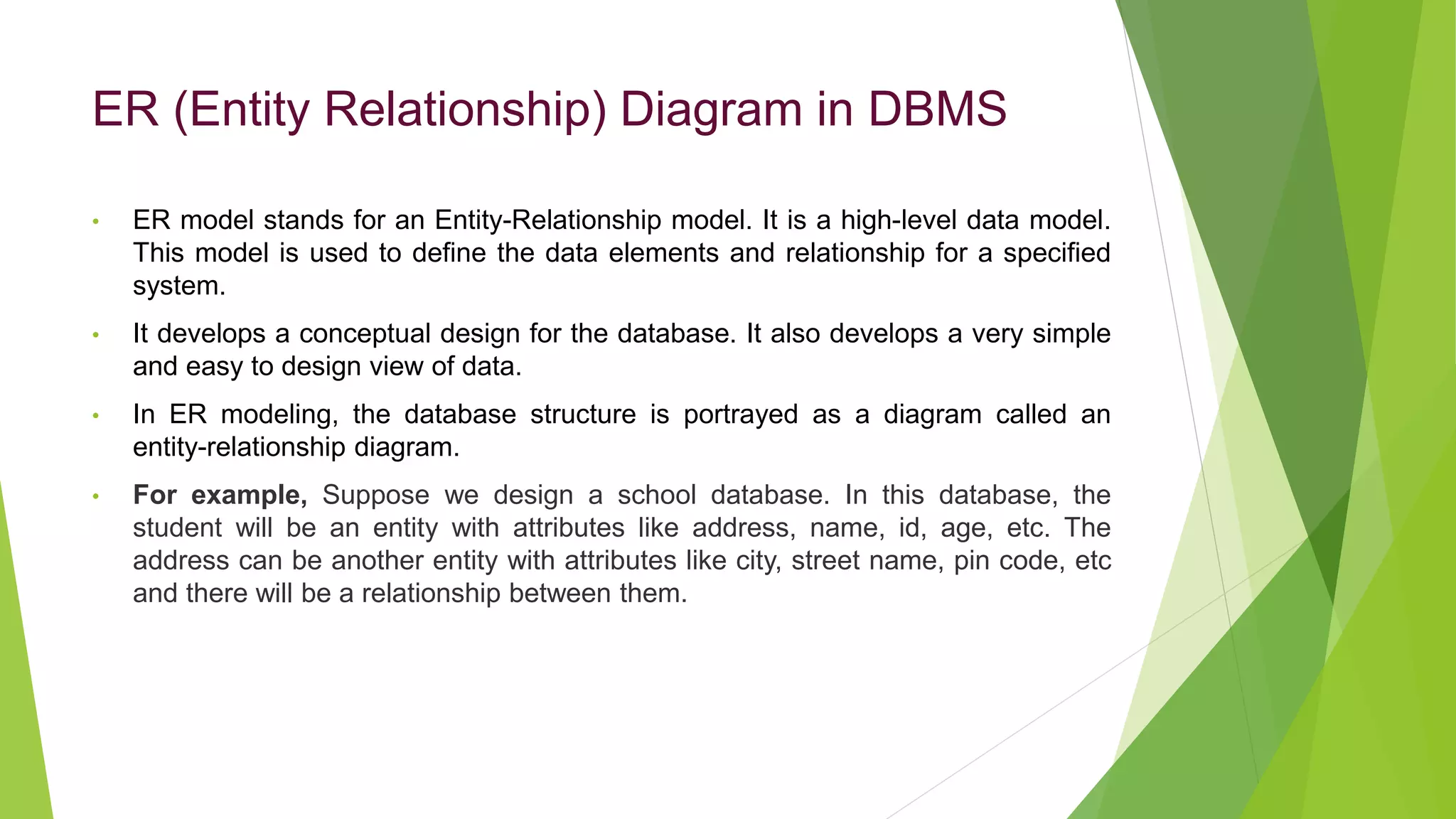
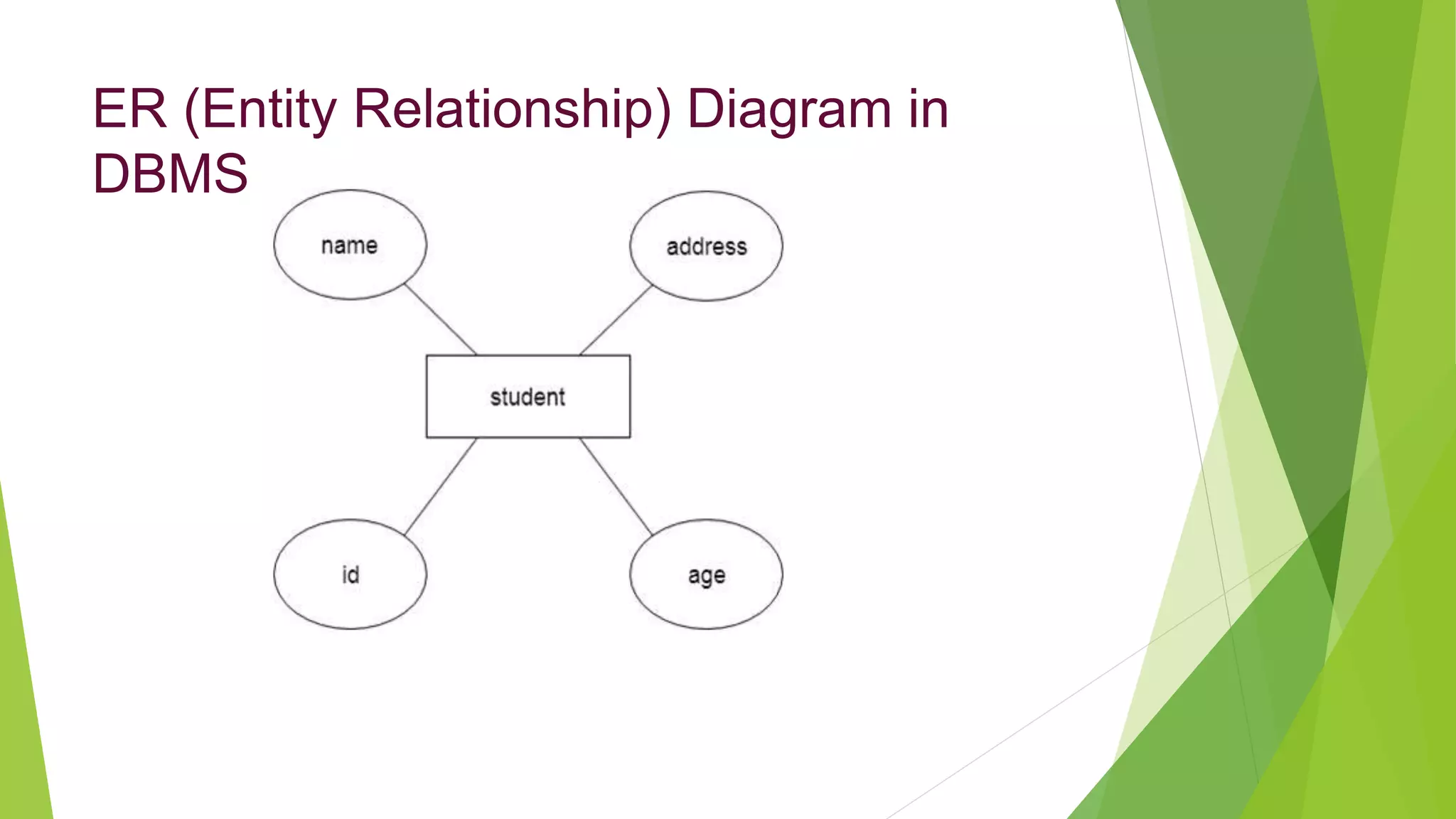
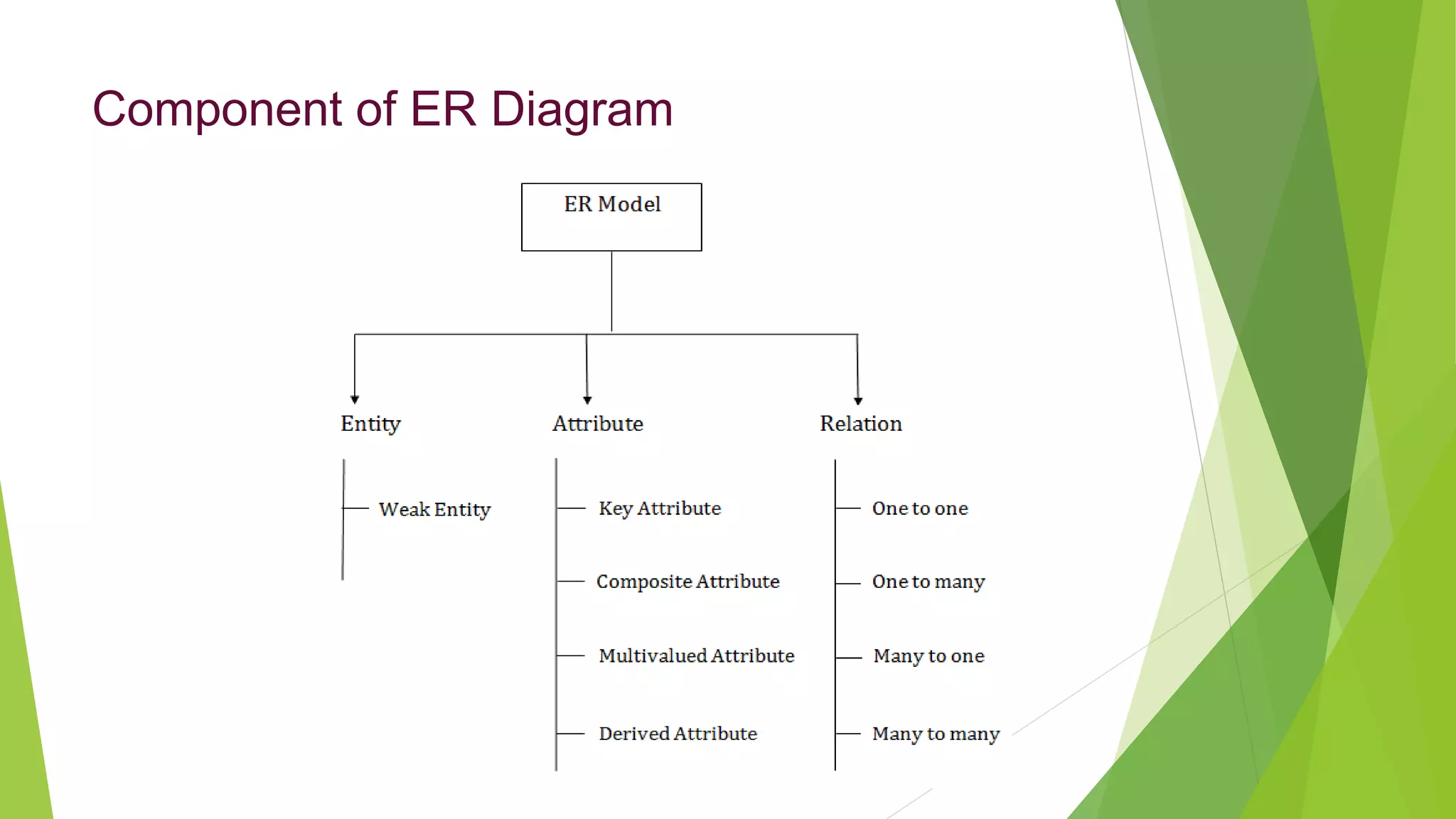
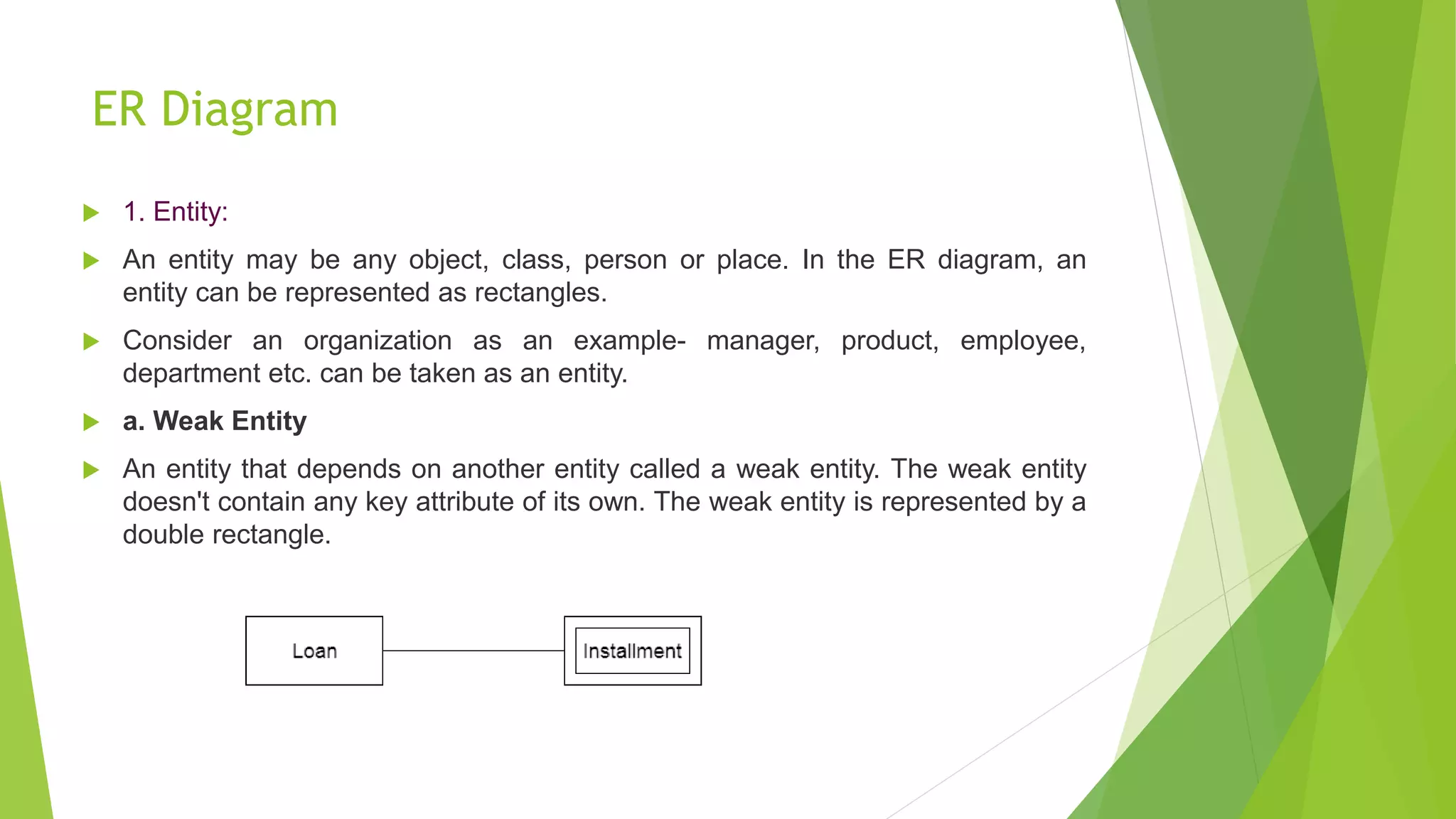
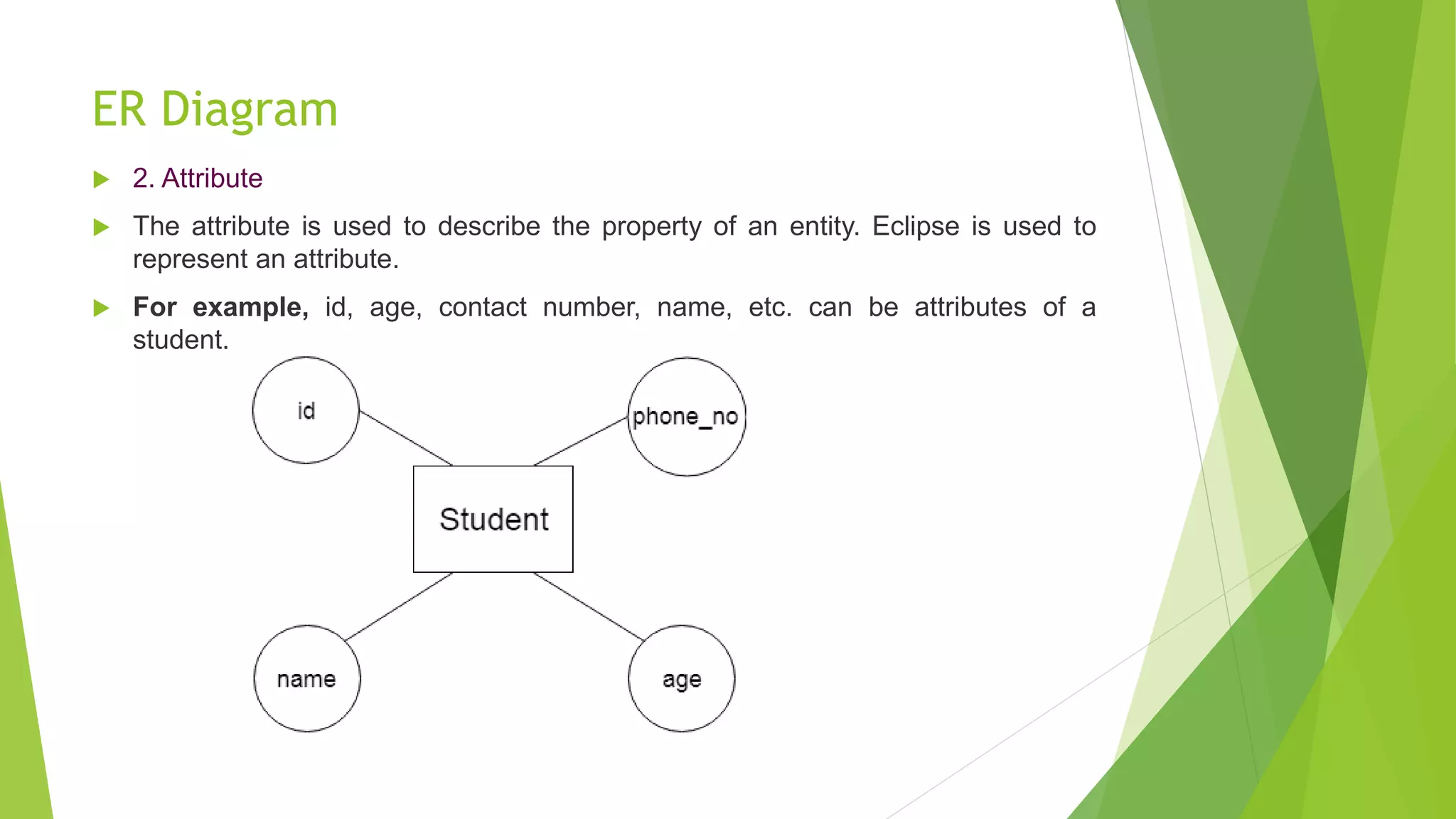
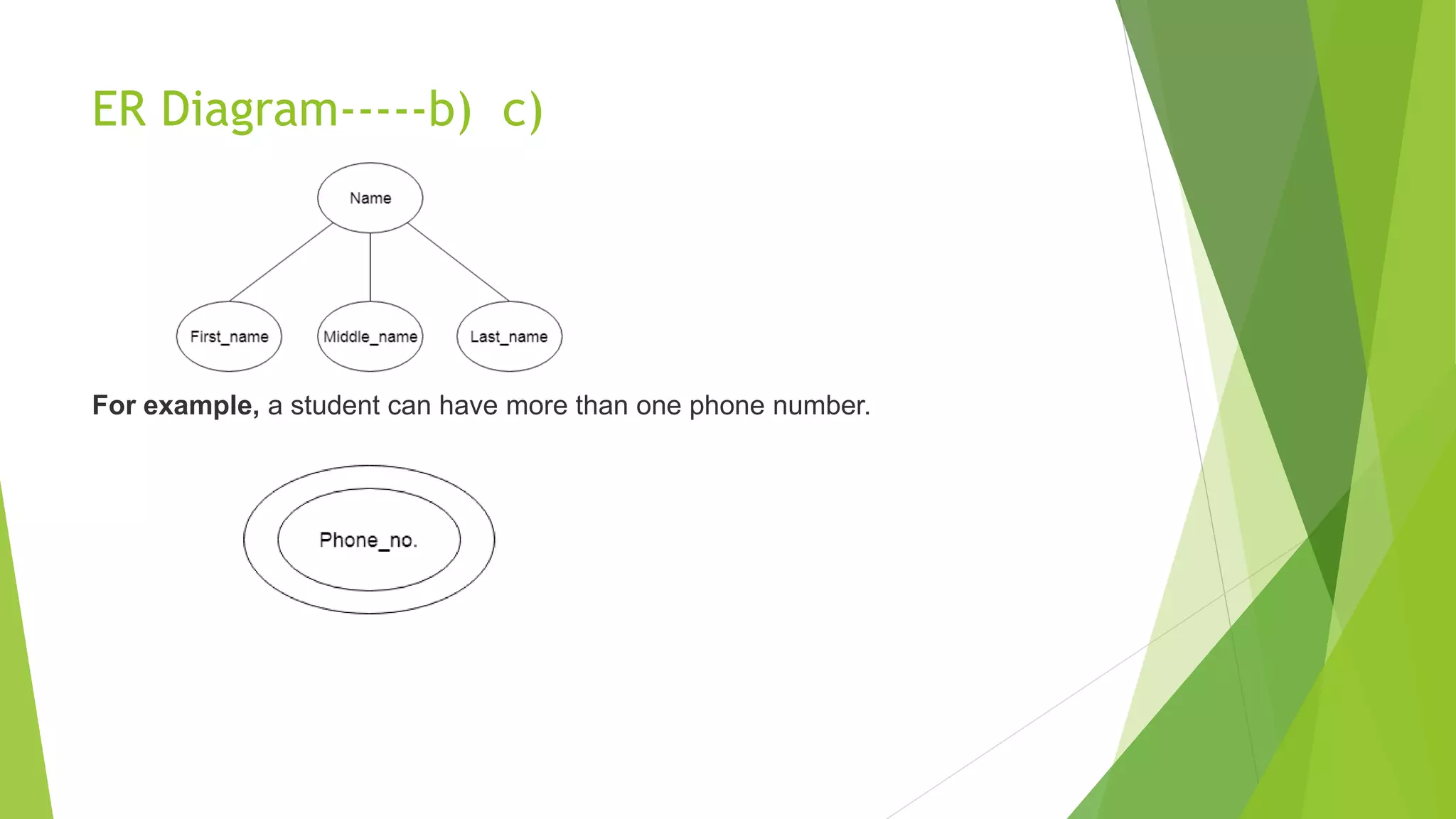
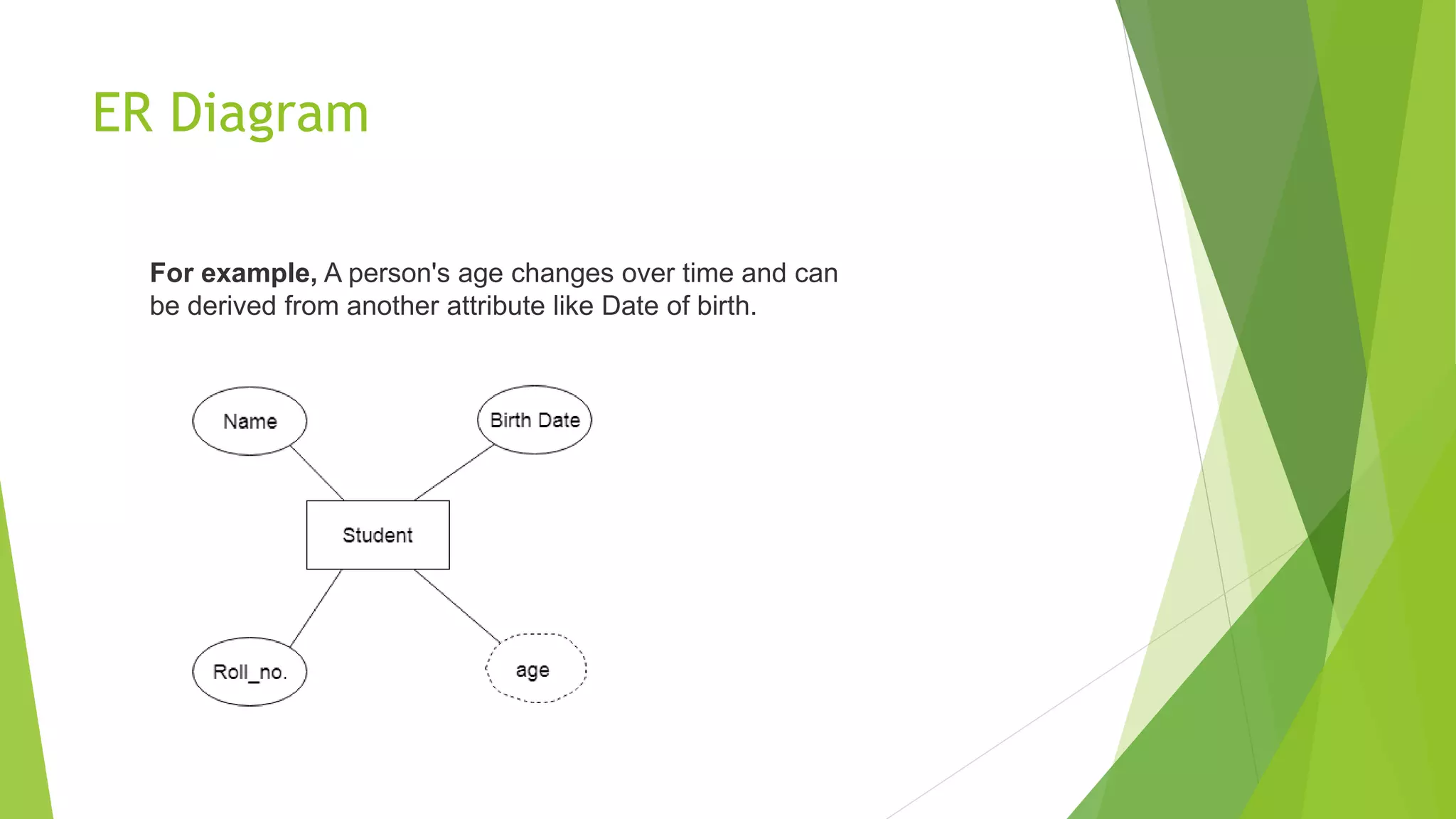
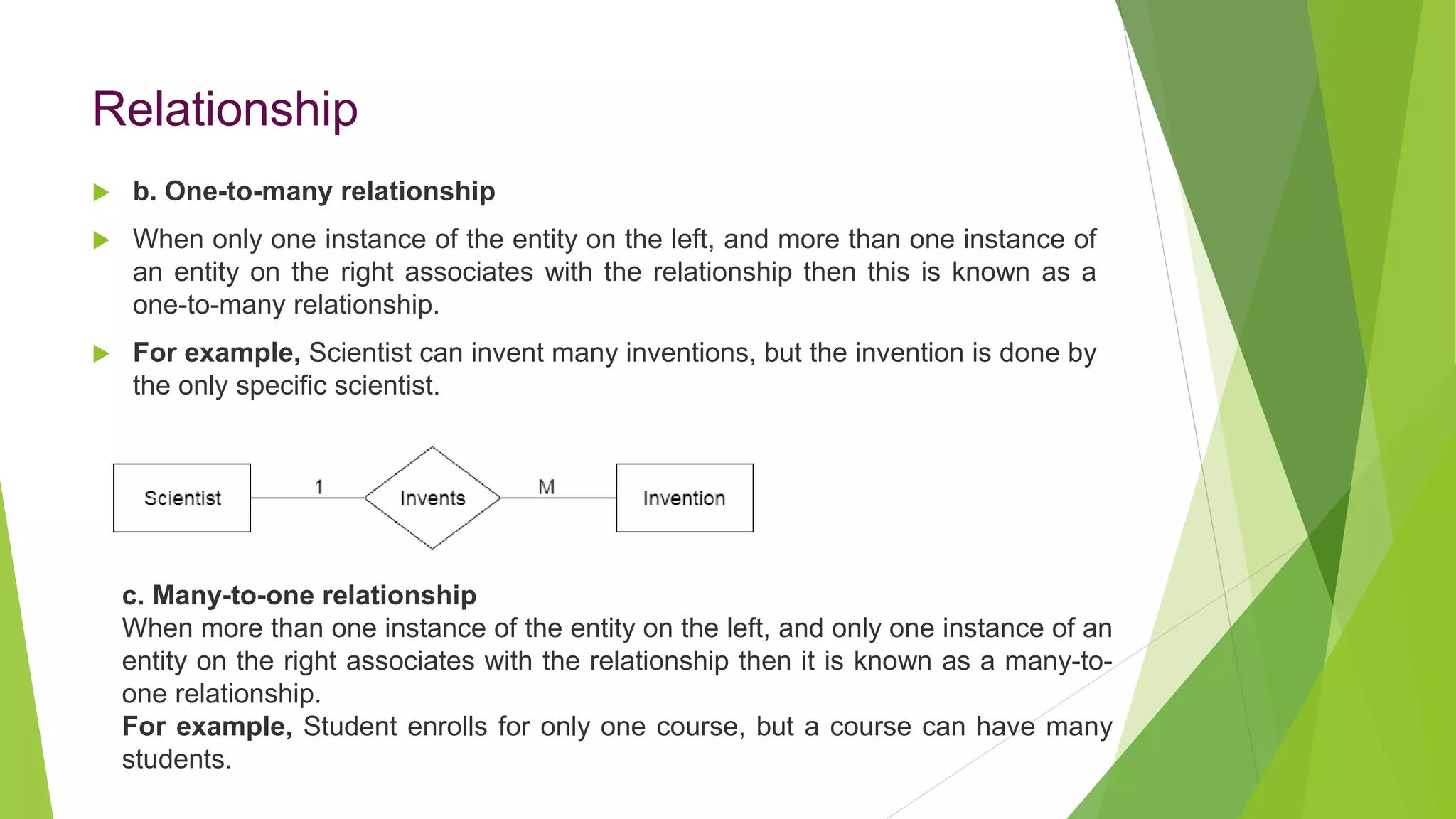
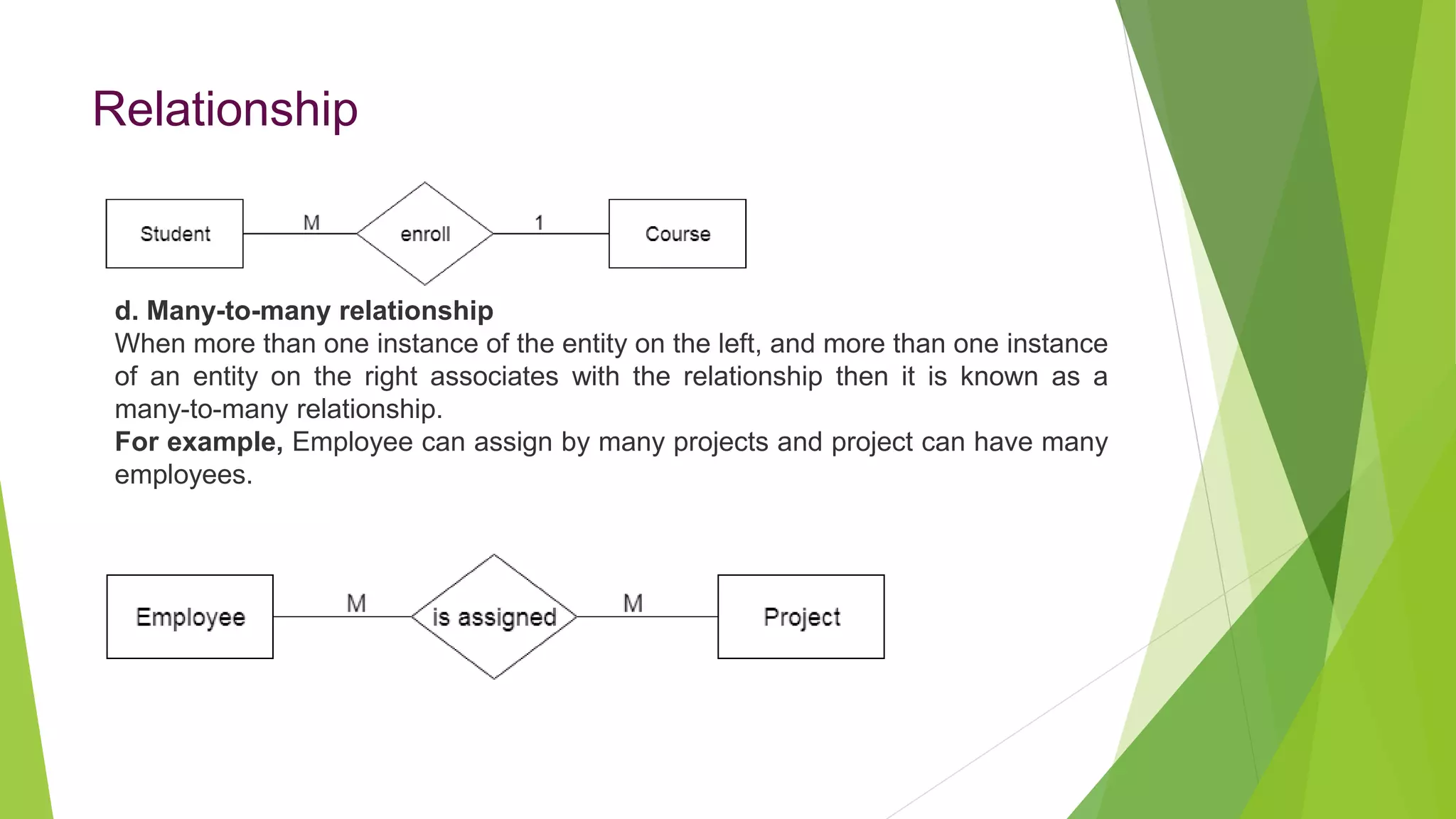
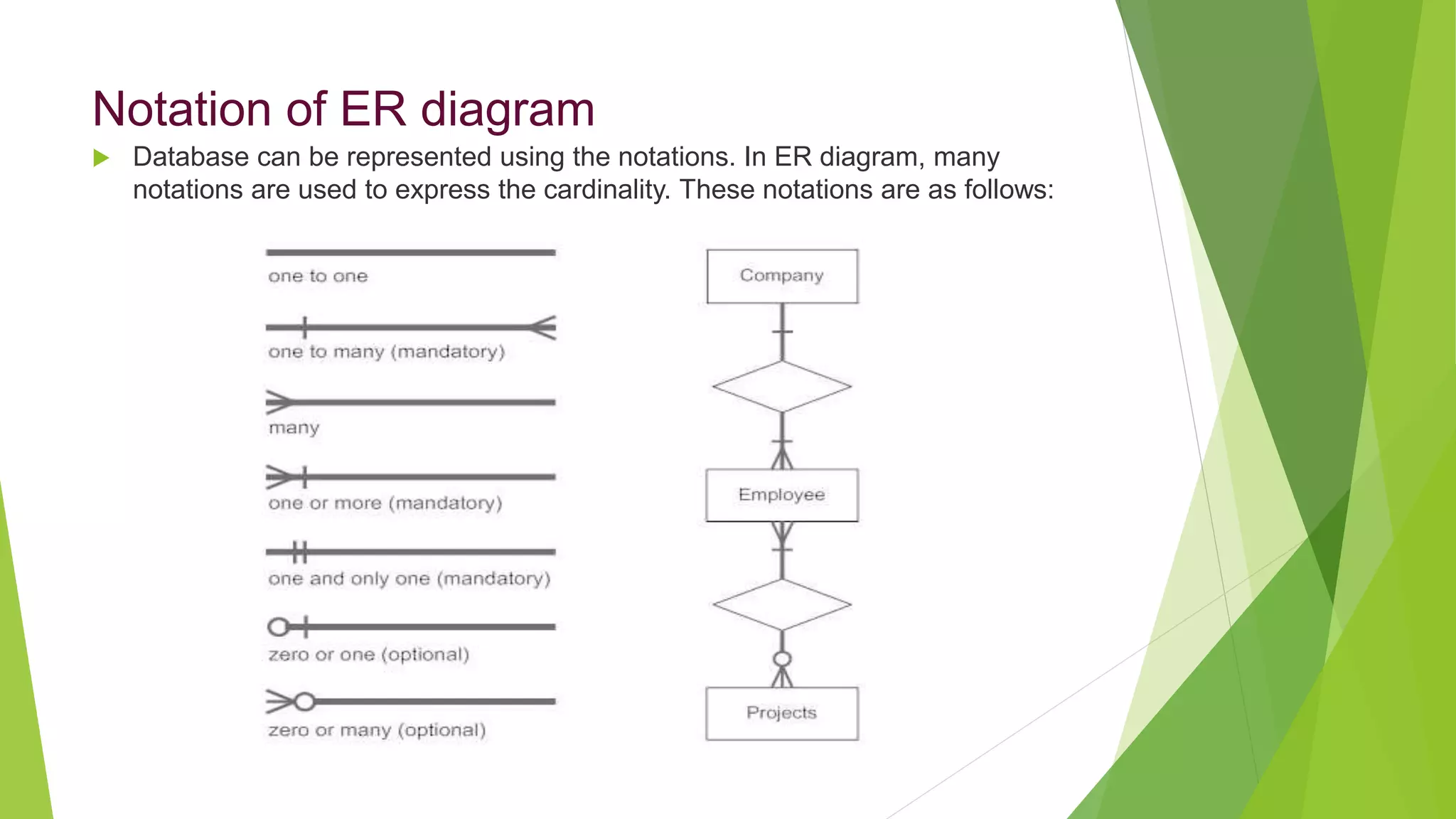
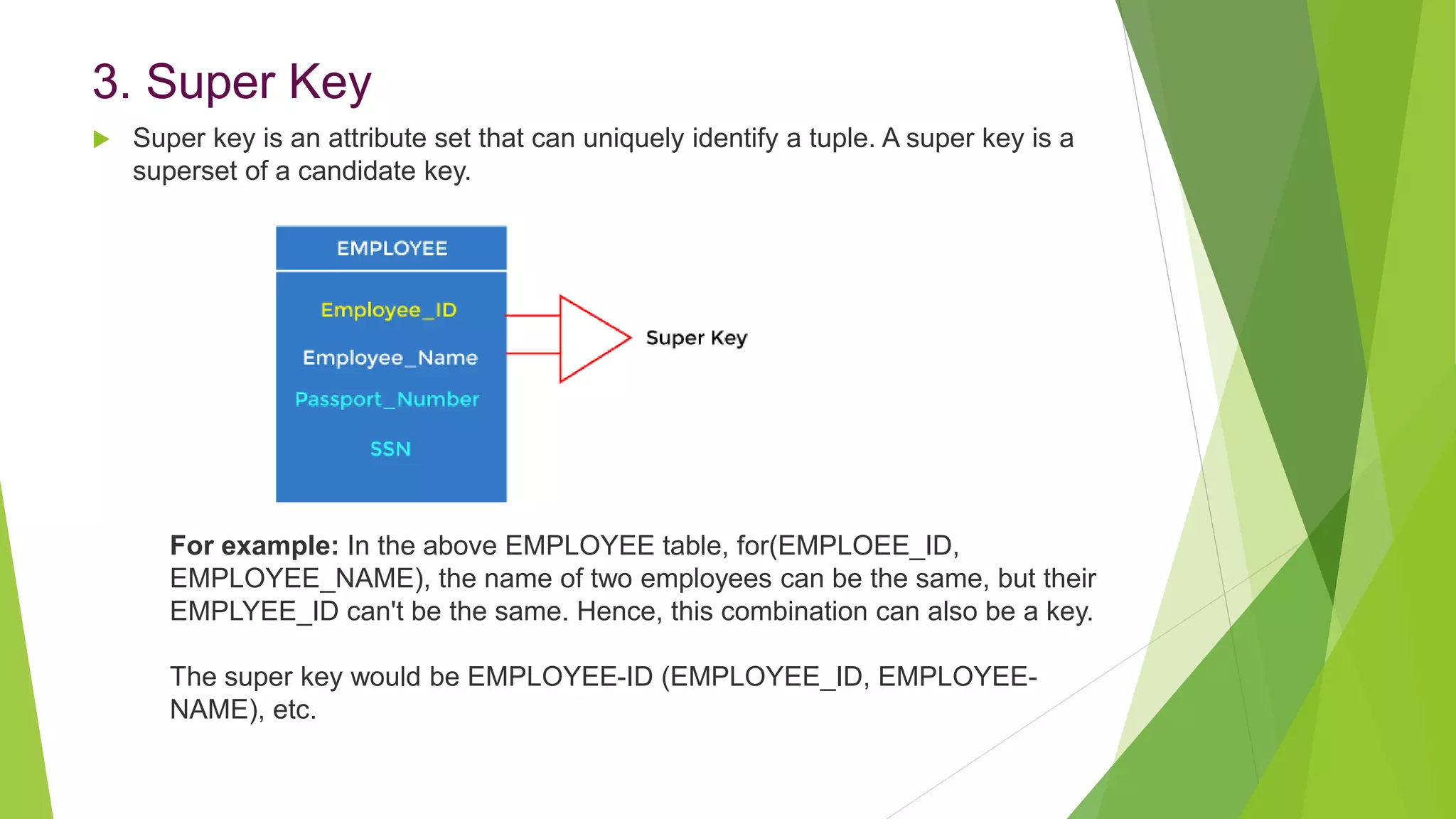
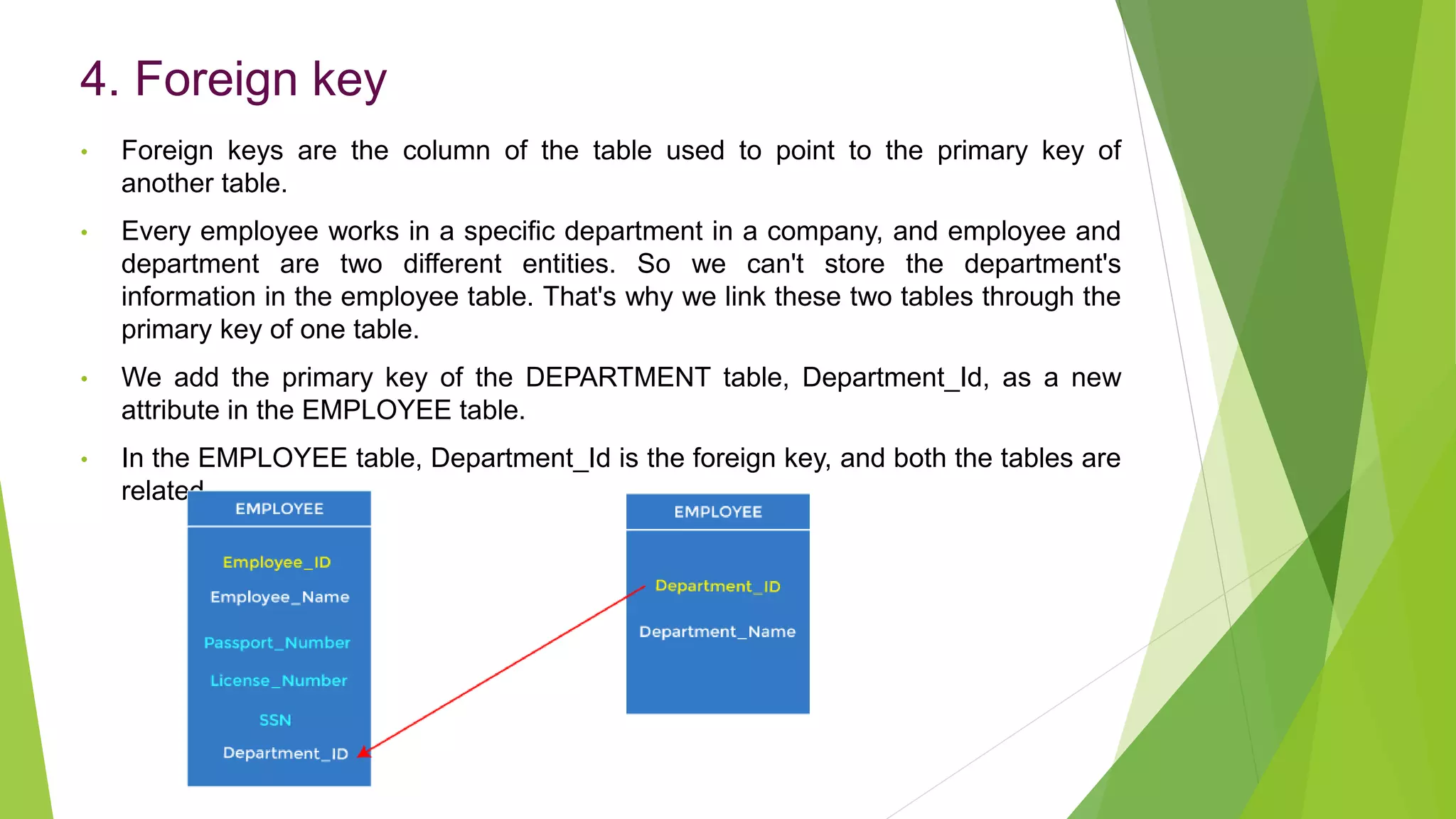
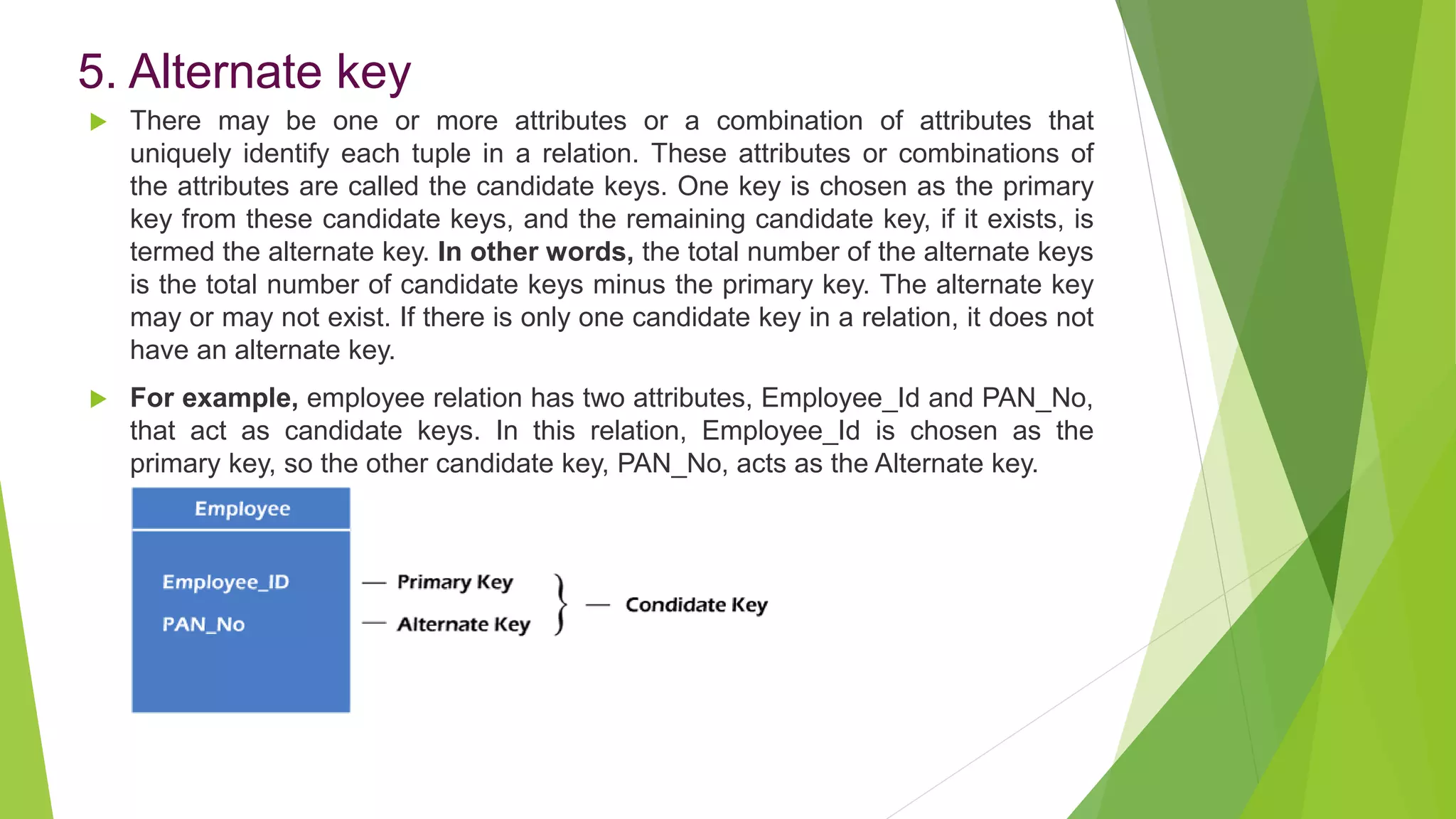
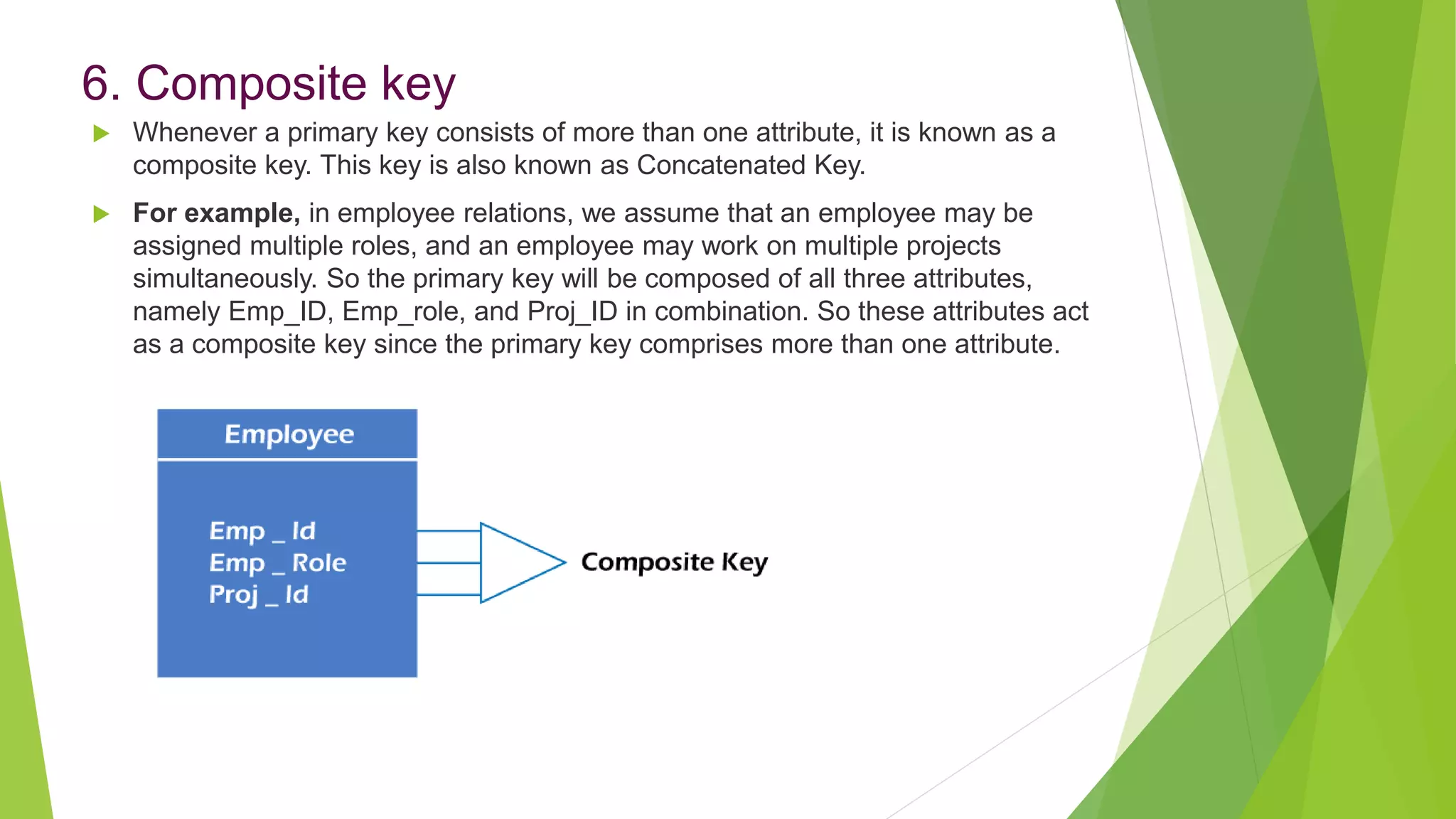
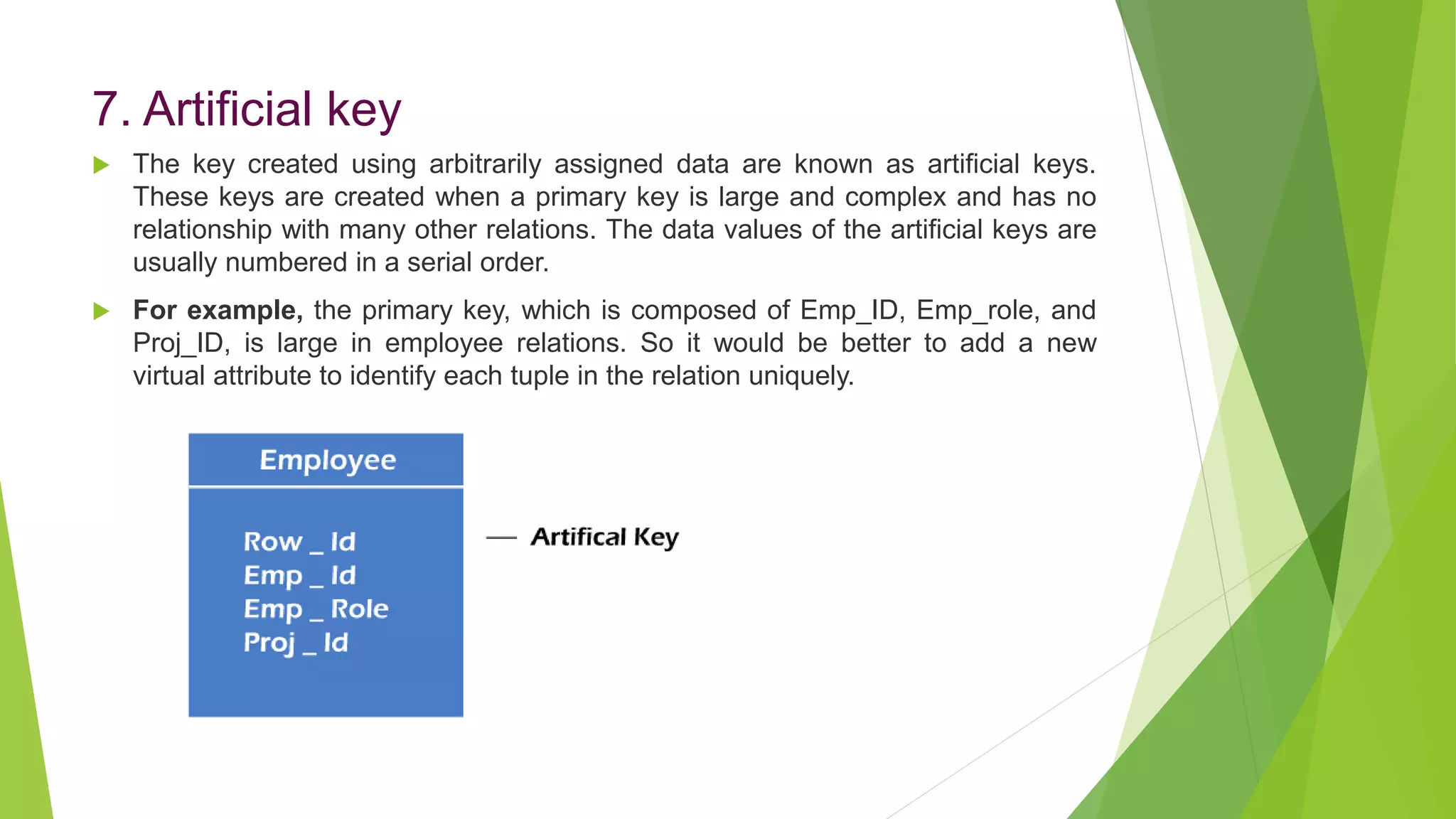
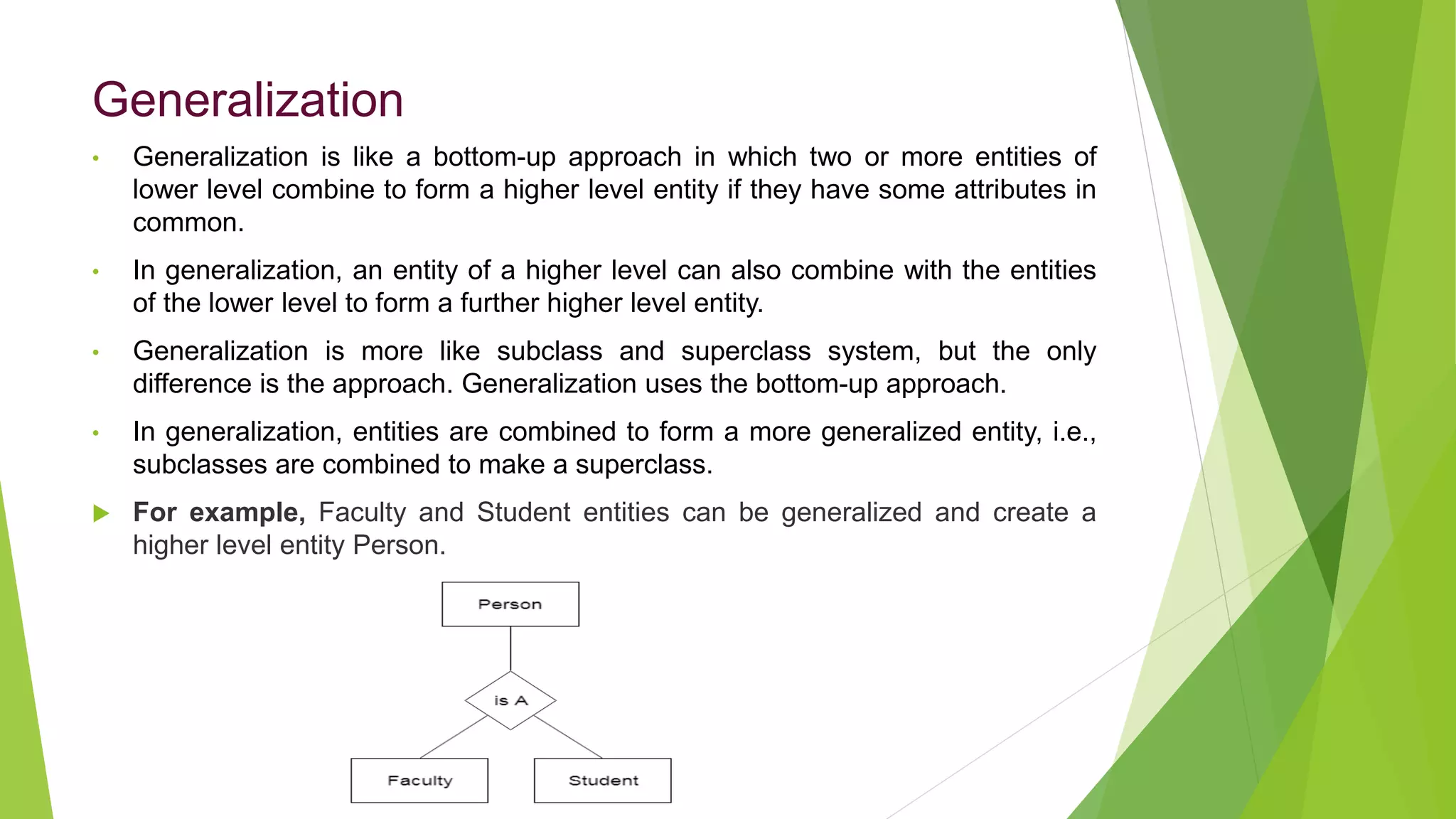
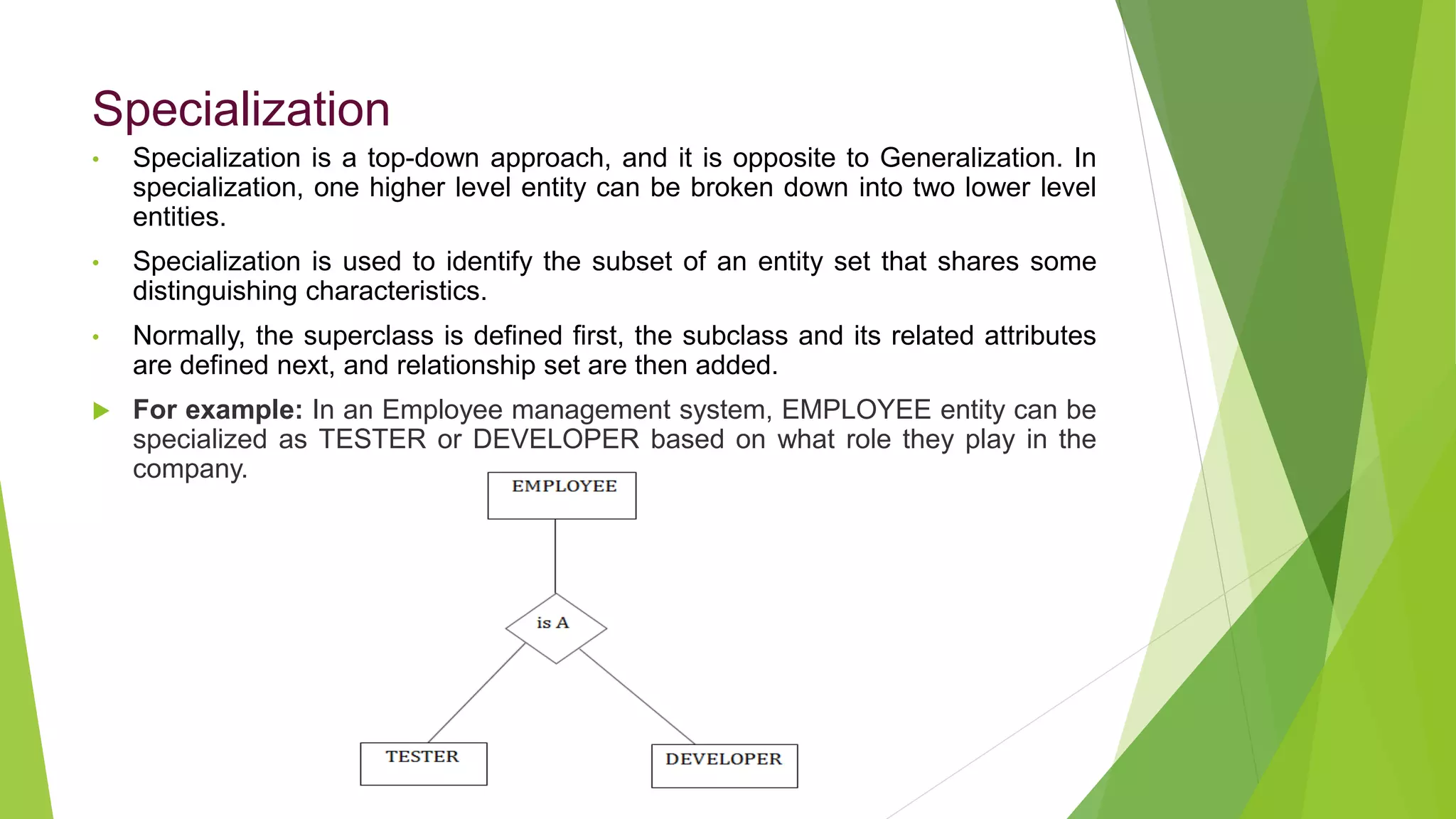
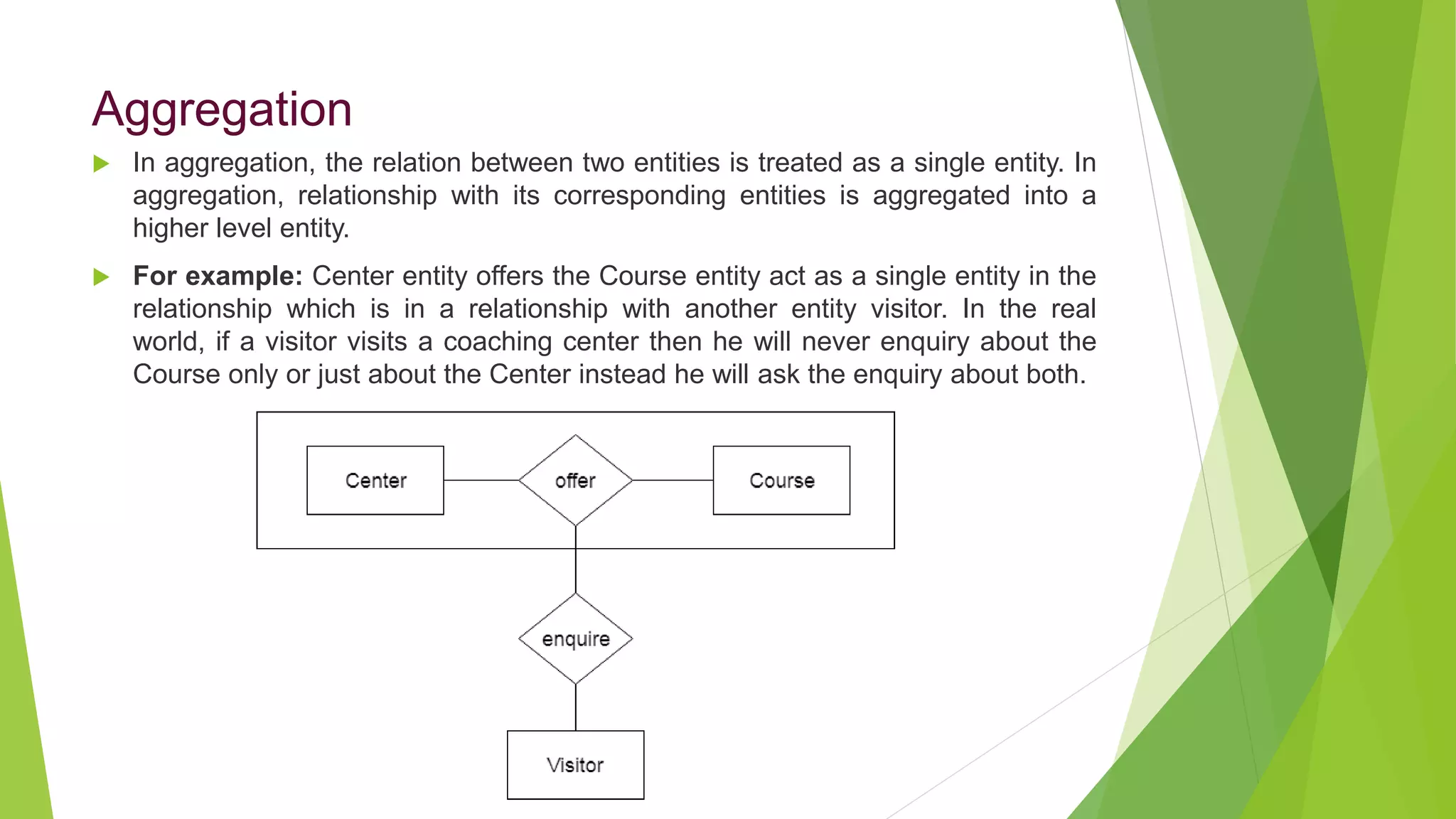
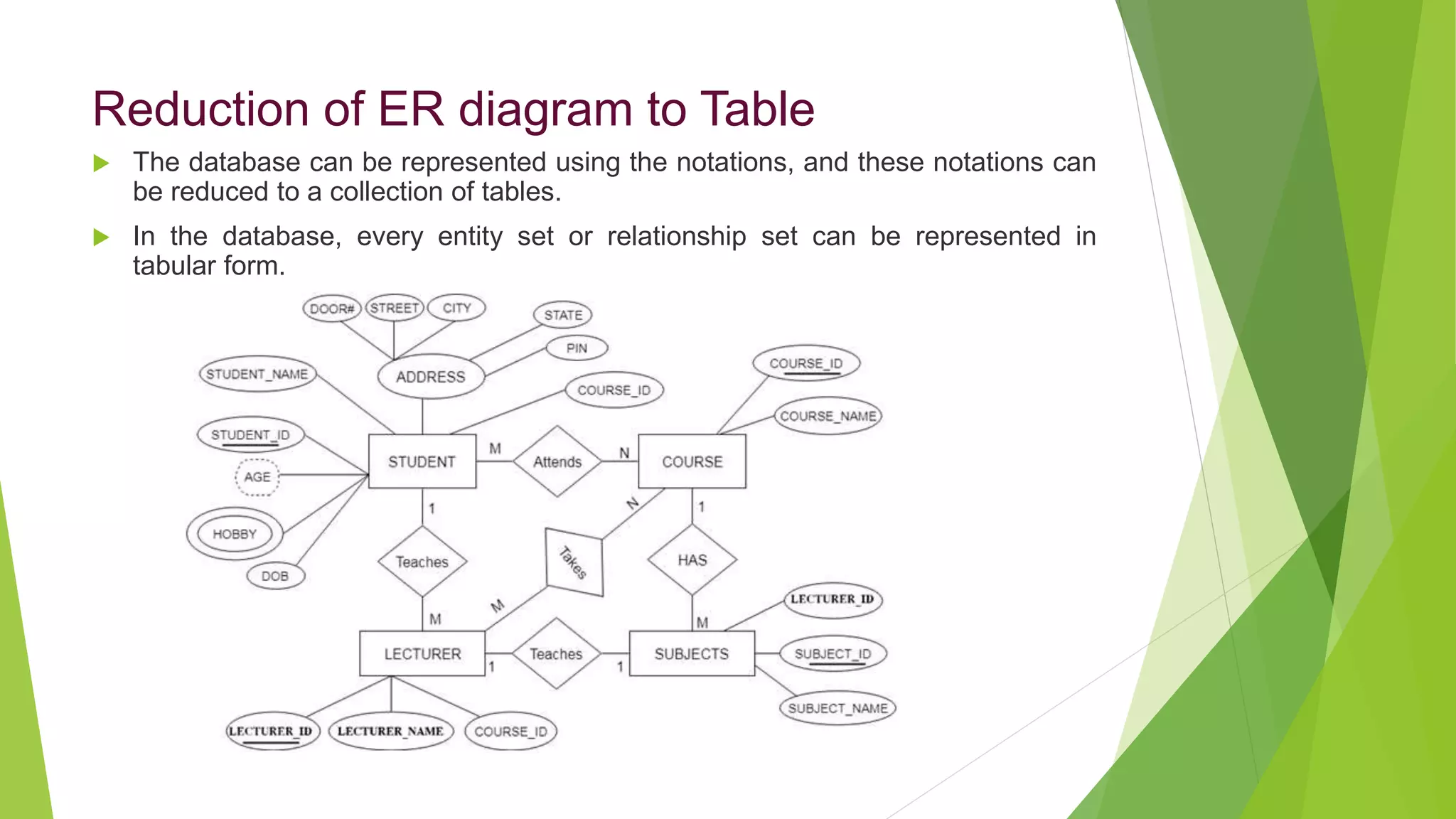
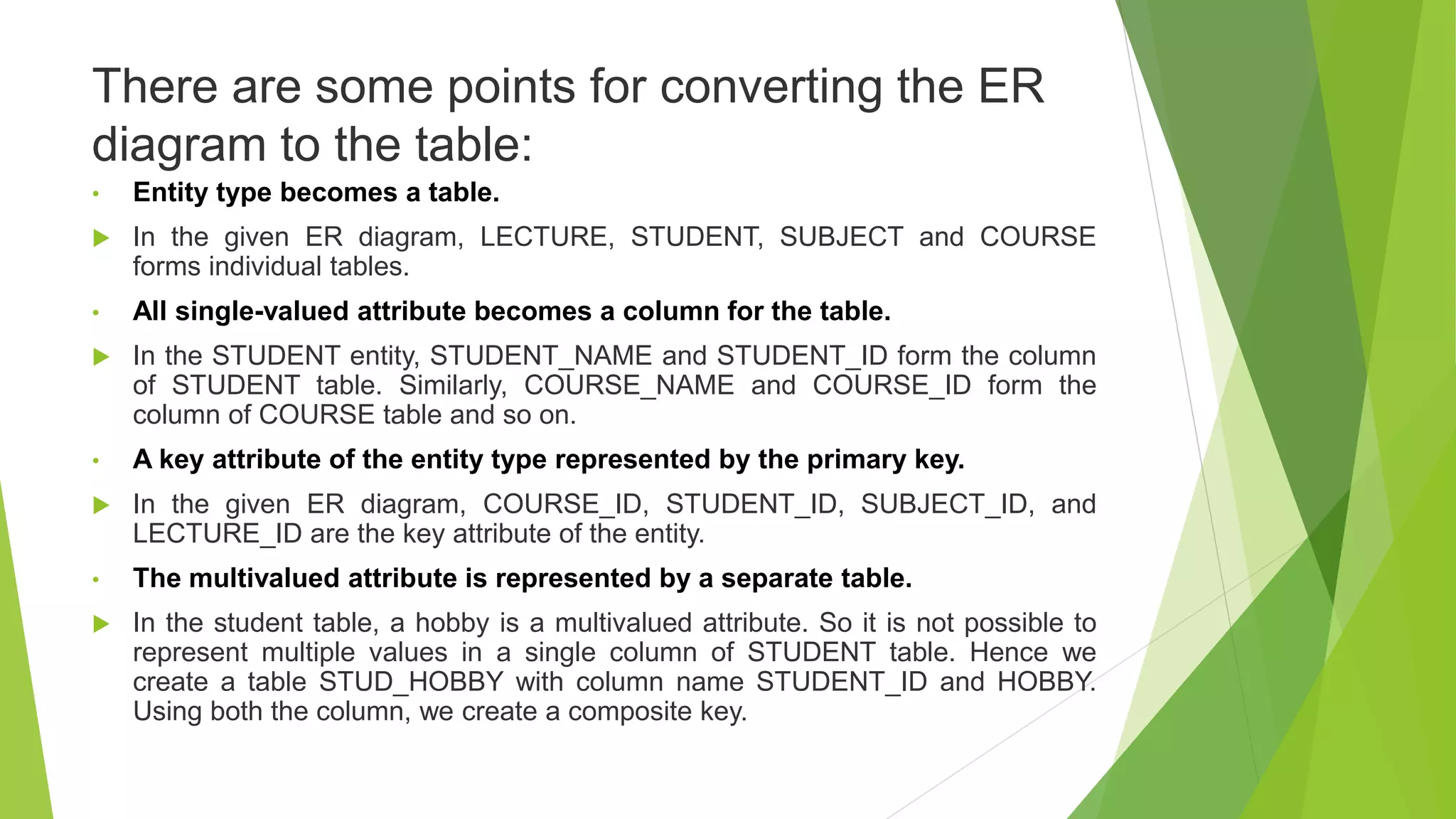
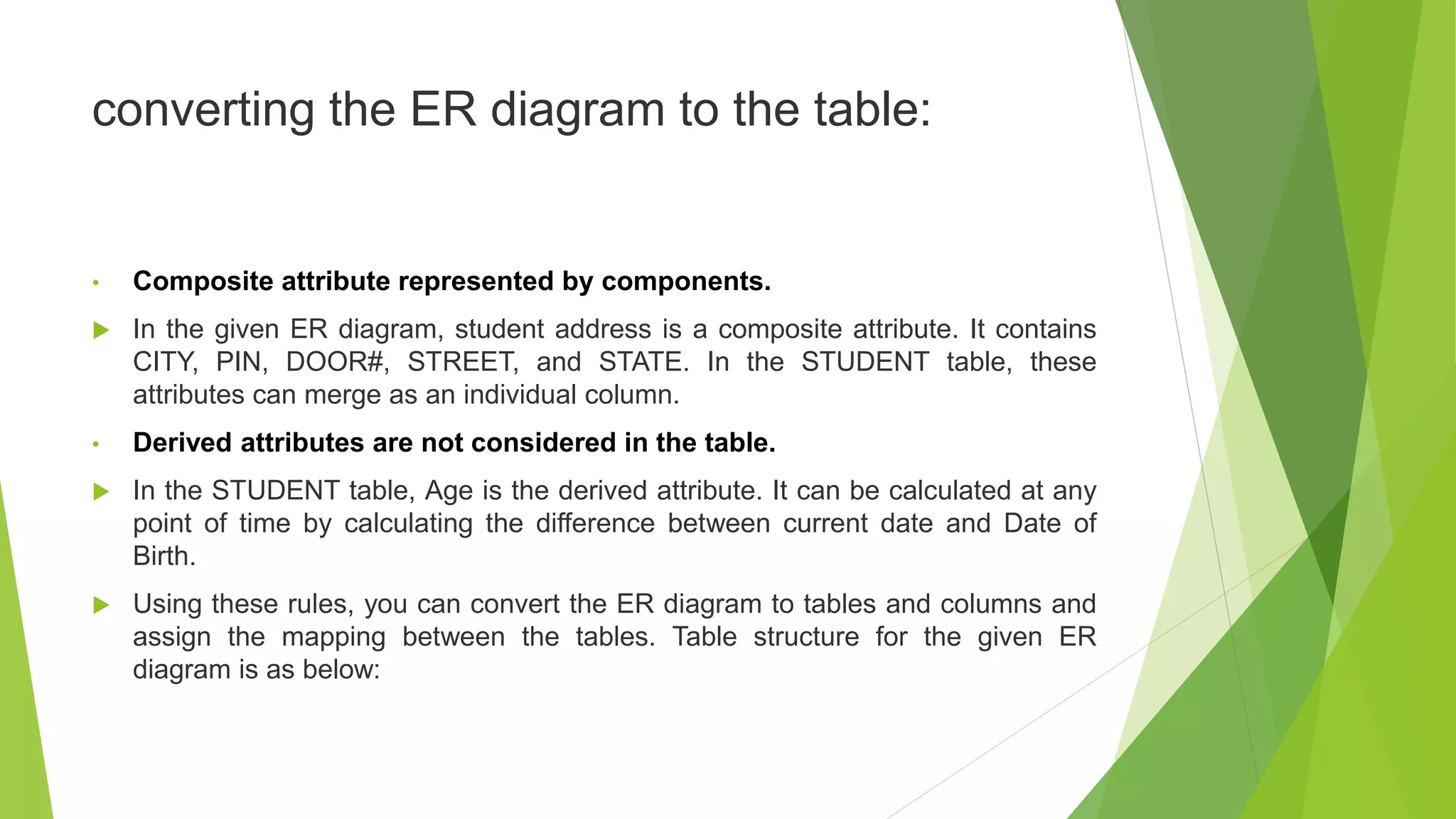
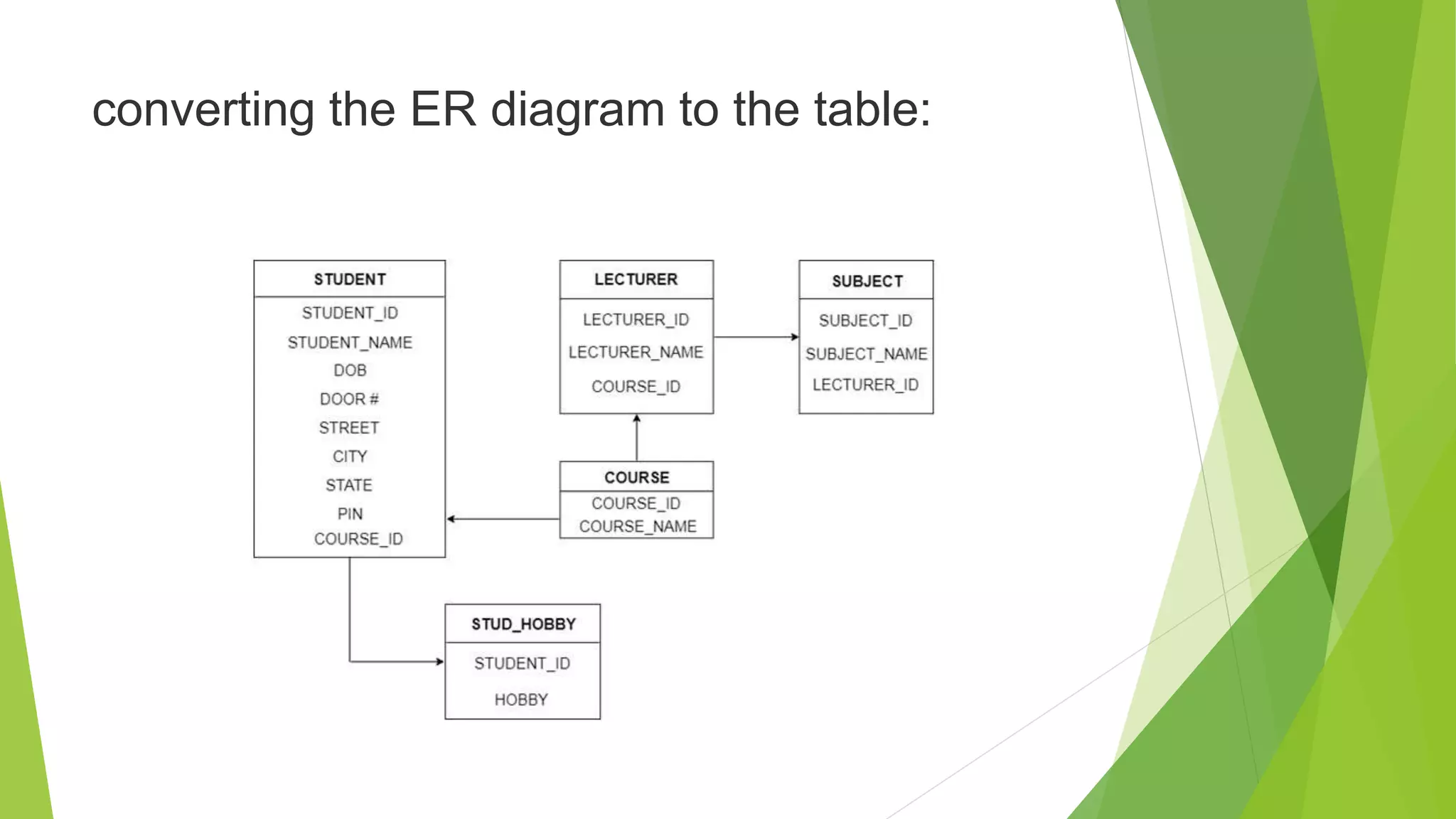
The document provides an overview of database management systems (DBMS). It discusses the need for DBMS, different database architectures including centralized, client-server and distributed. It also covers data models, ER diagrams, relational models, and SQL. Key advantages of DBMS over file systems include reducing data redundancy, improving data integrity and security, and enabling concurrent access.