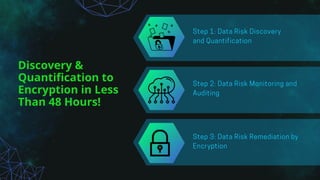
Actifile offers a unique real-time data risk assessment process designed to meet privacy regulations and quantify risks in local currencies. The software provides a three-step approach: discovering and quantifying data risk, monitoring data flows in real-time, and automated remediation through encryption. Actifile's method is presented as superior to traditional data loss prevention strategies, emphasizing quick deployment and minimal workflow disruption.