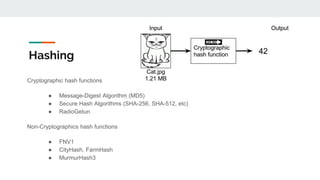
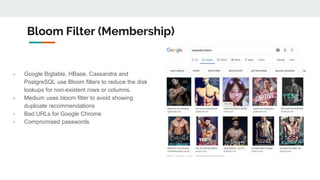
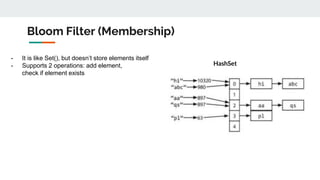
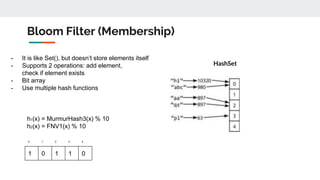
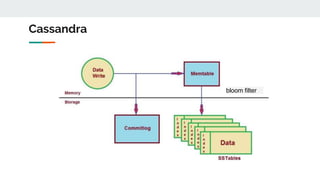
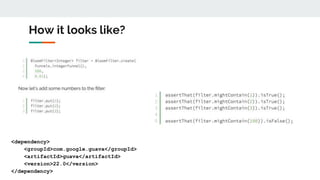
The document discusses various probabilistic data structures, including Bloom filters, count-min sketches, and hashing techniques, highlighting their use cases in data engineering. It outlines their applications in membership checking, frequency counting, cardinality estimation, and similarity detection, showing how they optimize performance and resource usage. The document serves as an introduction to these structures, emphasizing their importance in managing large datasets effectively.





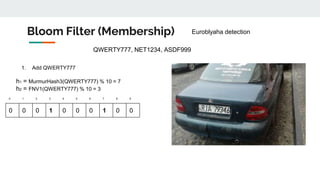
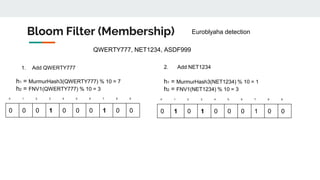
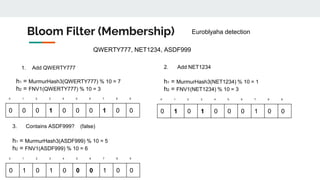
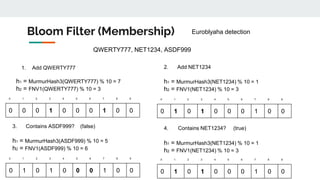







![{ #quarantine, #quarantine, #brexit, #brexit, #alyonalyona, #quarantine, #tesla, #tesla, #quarantine,
#brexit, #oscar, #quarantine -> }
Count-Min Sketch (Frequency)
0 1 2 3 4 5 6 7 8 9
h1 0 0 0 0 6 0 1 0 5 0
h2 0 0 3 0 0 1 0 6 0 2
How many times #tesla?
h1(x) = MurmurHash3(tesla) % 10 = 8
h2(x) = FNV1(tesla) % 10 = 9
Final answer = min(h1[8], h2[9]) = min(5, 2) = 2](https://image.slidesharecdn.com/datamonstersprobablisticdatastructures-200430091550/85/Data-monsters-probablistic-data-structures-27-320.jpg)