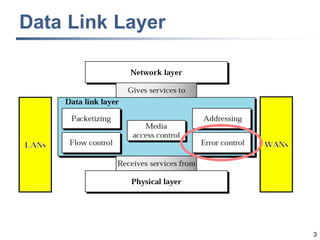
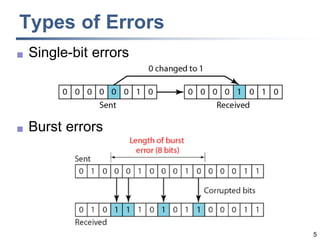
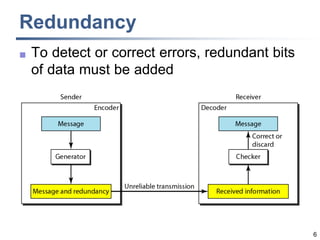
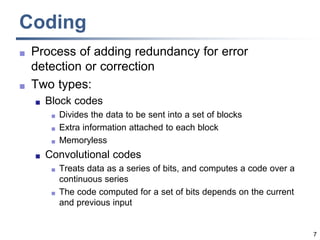
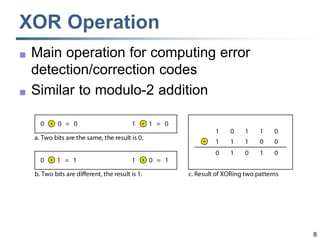
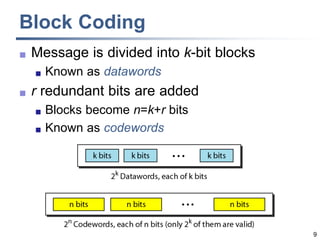
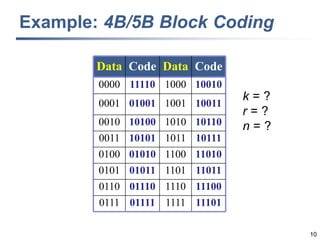
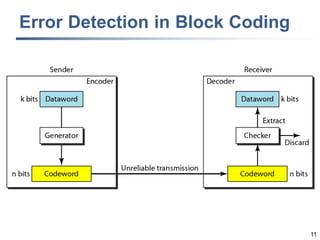
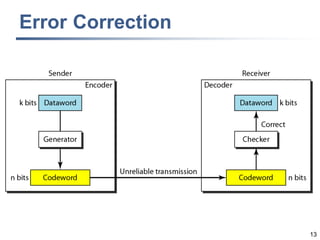
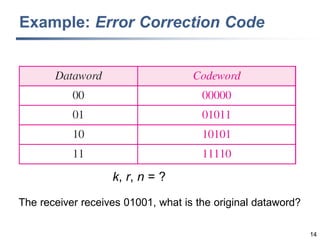
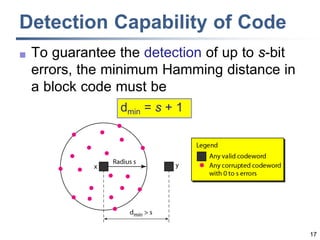
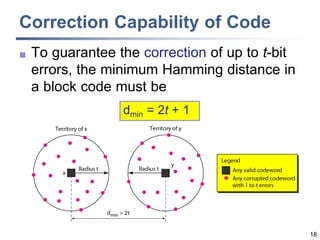
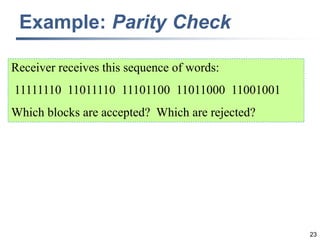
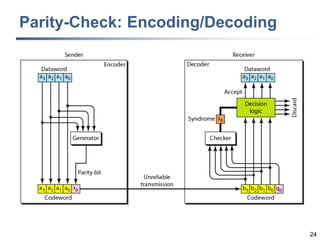
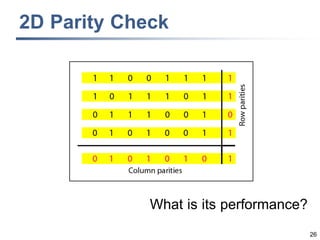
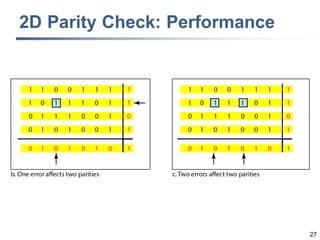
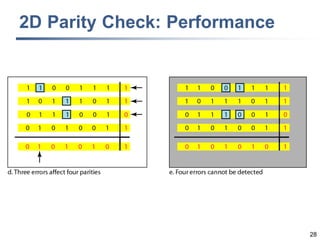
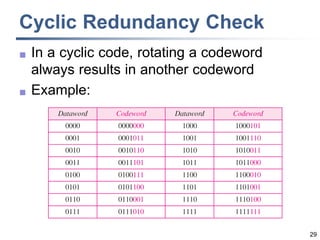
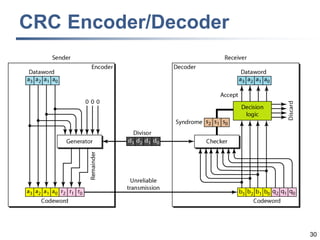
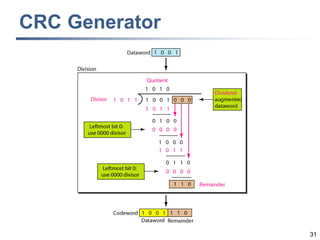
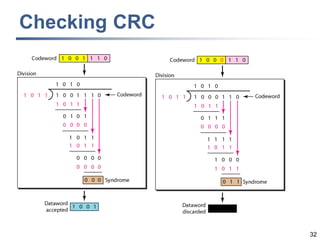
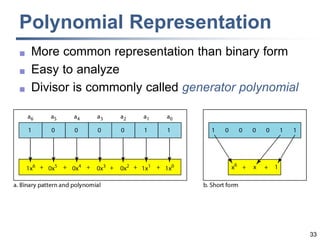
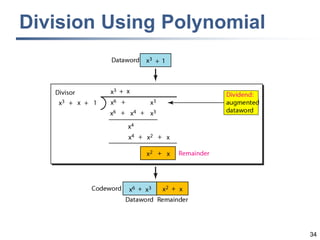
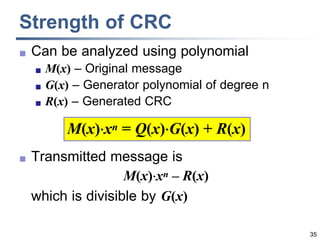
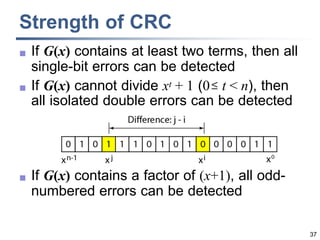
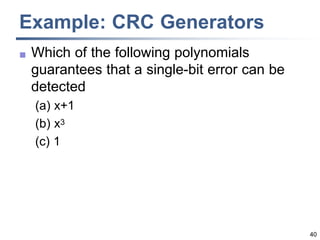
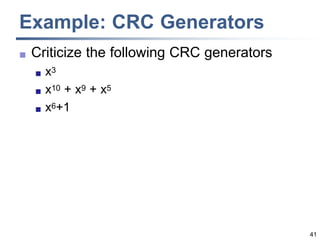
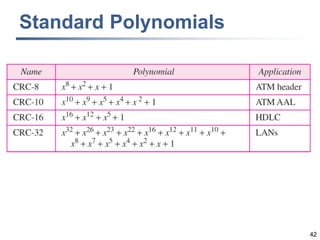
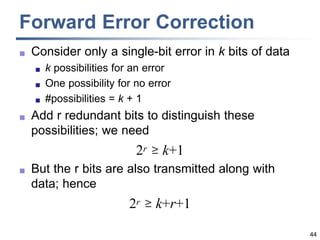
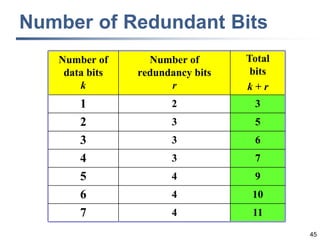
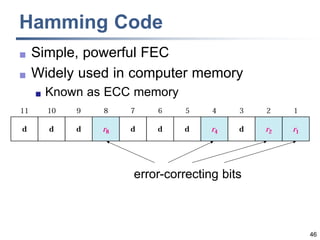
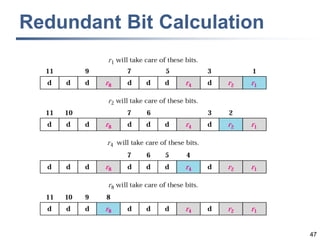
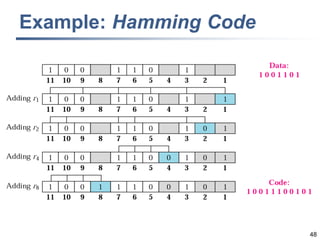
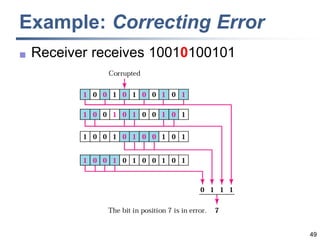
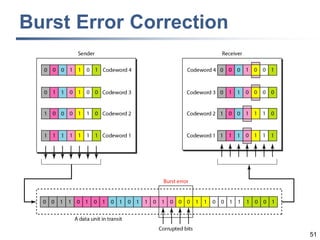
This document discusses error detection and correction techniques at the data link layer. It covers different types of errors, the use of redundancy to detect or correct errors, block coding and convolutional coding approaches. Specific coding schemes like parity checks, cyclic redundancy checks (CRC), and Hamming codes are explained in detail. The key aspects covered are the use of redundant bits, minimum Hamming distance requirements for detection and correction capabilities, and how techniques like CRC and Hamming codes function to detect and correct single-bit errors. Assignments and example problems are also listed.