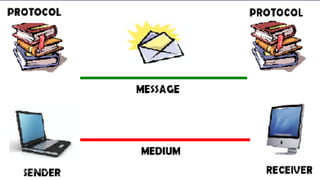
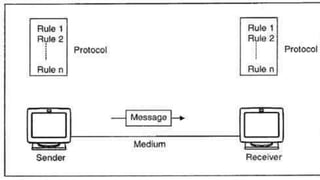
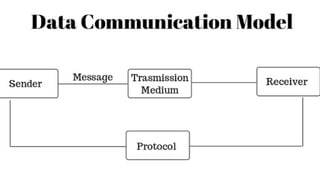
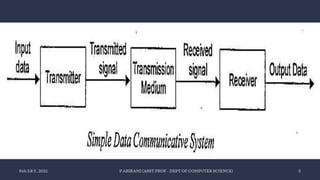
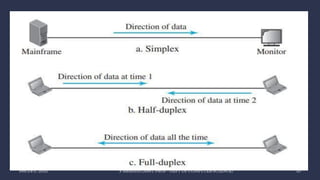
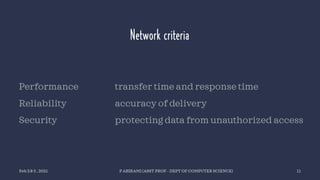
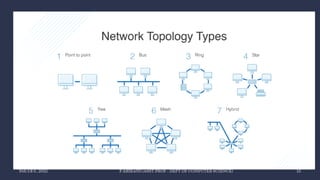
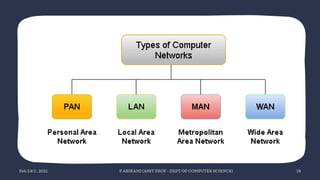
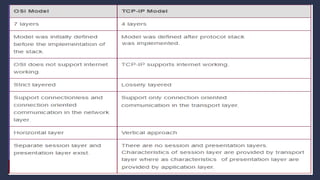
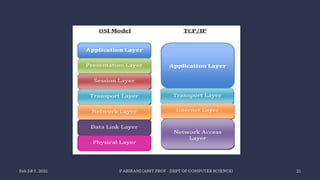
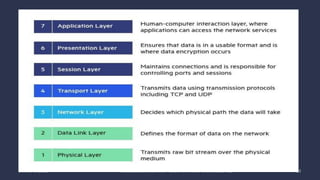
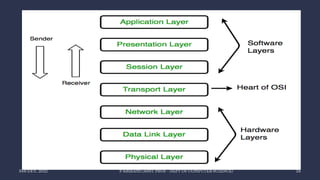
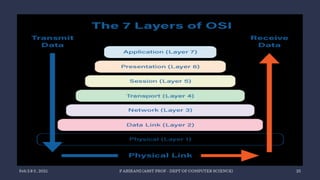
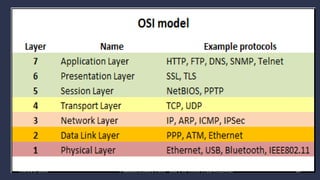
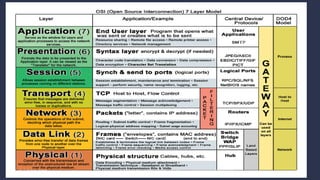
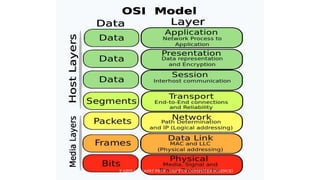
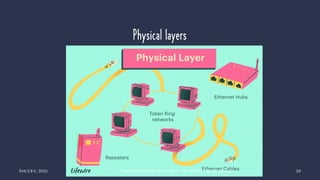
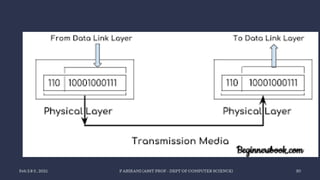
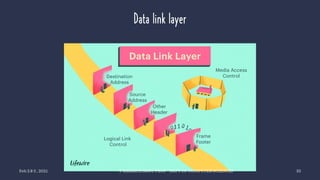
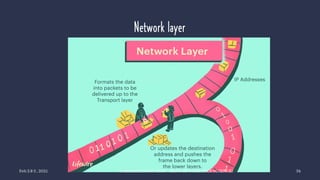
The document discusses data communication and networking concepts, emphasizing the characteristics, protocols, and standards involved. It highlights the Open Systems Interconnection (OSI) model, which describes seven layers used in network communication, and details the role of the physical layer in converting digital data to signals for transmission. Additional topics include network criteria, identifiers, and the methods of digital transmission such as line and block coding.