Embed presentation
Download to read offline
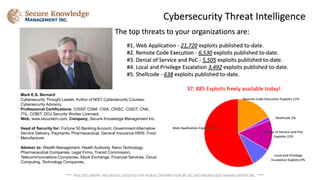
The document identifies the top cybersecurity threats to organizations, with web application exploits being the most common at 21,720, followed by remote code execution and denial of service exploits. A total of 37,885 exploits are currently available, emphasizing the urgent need for cybersecurity awareness. The document is publicly distributed and authored by Mark E.S. Bernard, a cybersecurity expert with numerous professional certifications.
