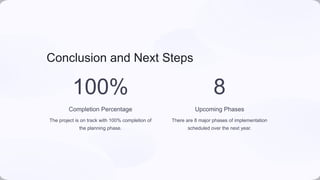
The document outlines TechCorp's implementation plan for an Identity and Access Management (IAM) platform aimed at enhancing security, user experience, and scalability. It details the scope, including user onboarding and role management, with an eight-phase timeline for execution. The plan includes roles, technical requirements, and risk management strategies to ensure a secure and efficient rollout across the organization.