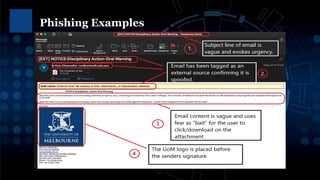
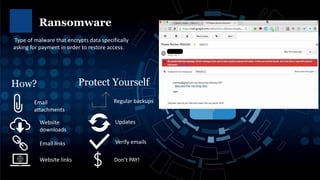
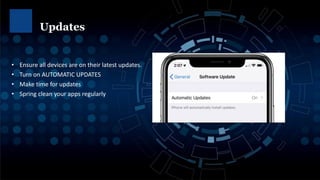
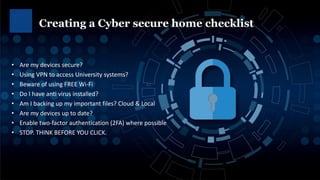
Phishing attacks, ransomware, and social engineering scams are ongoing cybersecurity threats. Ransomware encrypts user data and demands payment for access restoration. Phishing occurs through emails, texts, and phone calls attempting to steal personal or financial information. Users can protect themselves using strong and unique passwords, enabling two-factor authentication, updating devices and software, avoiding suspicious links and attachments, and backing up important files. Regular cybersecurity awareness training helps users identify and avoid common cyber attacks.